In this post, we will show you the methods for increasing the availability of your app. Read on.
App availability is essential for upholding the desired user experience and functionality that defines your software. And if your app is taken out of action due to backend issues, previously loyal users could be put off it for good.
As a result, you should do everything possible to increase and maintain the availability of your app. To help you with this, here are a few methods to try yourself.
Table of Contents
Methods For Increasing The Availability Of Your App
#1 Make The Most Of Monitoring Tools
Although you may plan for outages and take steps to prevent them, the reality is that no solution is entirely resilient. This is why you need to harness monitoring tools to track how resources are being used and identify potential issues so they can be addressed before they cause chaos.
For example, if you always use Availability Groups (AGs), assuming they will function flawlessly without being monitored is incorrect.
Instead, you should keep track of the AGs that power your app so you are always attuned to its performance and if any problems are looming large.
READ ALSO: The Increasing Importance Of Cybersecurity In 2024
#2 Consider Scalability As Soon As Possible
When building an app, you likely have a specific use case in mind and an intended number of users you expect to serve simultaneously.
This is all good in the short term, but if your app becomes more popular and needs to support the added influx of simultaneous users, it could crumble under the strain.
Because of this, it makes sense to design your app with future usage scenarios in mind and implement as much scalability as possible early on, rather than having to add it in a panic when the app is overwhelmed by traffic further down the line.
Of course, that does not mean you need to over-allocate resources upfront. Still, that built-in scalability should allow additional servers to be added to the mix without causing performance issues, unexpected bugs, or security vulnerabilities.
#3 Plan Your Responses To App Availability Issues In Advance
We have already touched on the impossibility of building a perfectly available and functional app. Therefore, if you anticipate that outages will occur at some point, it makes sense to plan ahead for how to address them.
This is all about establishing processes to codify your response to availability dilemmas. You should know who is responsible for what aspect of the reaction and which tools they will be called to use in such circumstances.
Standardizing your response will make it faster and more efficient and will also give you a means of diagnosing the causes of downtime rather than being baffled when they crop up.
Preparations like these are also advantageous because they will help you overcome some of the pitfalls usually associated with troubleshooting apps in an emergency. So, rather than staff being overwhelmed, they will be empowered and ready to act effectively.
READ ALSO: Top Factors to Consider Before Switching to Cable Internet
Strategies to Bolster Your App’s Defenses: The Cybersecurity Fortress
In today’s digital world, applications are the lifeblood of many businesses. They connect us to customers, streamline operations, and drive revenue.
However, just like a physical castle needs strong defences to withstand attack, your app requires robust cybersecurity measures to ensure availability and protect sensitive data.
Here’s how to fortify your app against the ever-present threats in the cybersecurity landscape:
1. Code with Security in Mind
Secure Coding Practices: Implement secure coding practices from the get-go. This includes techniques like input validation to prevent injection attacks, proper data sanitization to avoid vulnerabilities, and secure password hashing to safeguard user credentials.
Regular Security Audits: Don’t Rely Solely on Initial Secure Coding. Conduct regular security audits by internal teams or external security experts to identify and address potential vulnerabilities in your codebase.
2. Secure Your Infrastructure
Robust Authentication and Authorization: Implement strong authentication and authorization protocols to control access to your app and its data. Multi-factor authentication (MFA) adds an extra layer of security, while role-based access control (RBAC) ensures that only authorized users have access to specific functionalities.
Vulnerability Management: Maintain an up-to-date inventory of all software components used in your app development stack. Regularly patch and update these components to address known vulnerabilities and prevent attackers from exploiting them.
3. Continuous Monitoring and Threat Detection
Proactive Security Monitoring: Don’t wait for a breach to happen. Implement continuous security monitoring tools to detect suspicious activity, identify potential threats in real time, and enable a prompt response.
Incident Response Plan: Develop a well-defined incident response plan that outlines the steps to take in the event of a security breach. This plan should include procedures for containment, eradication, recovery, and communication with stakeholders.
4. Stay Ahead of the Curve
Security Awareness Training: Educate your development team and staff on cybersecurity best practices. Regular training sessions can help them recognize phishing attempts, identify social engineering tactics, and avoid introducing vulnerabilities through human error.
Stay Updated on Emerging Threats: The cybersecurity landscape is constantly evolving. Keep yourself informed about the latest threats and vulnerabilities by following security blogs, attending industry conferences, and subscribing to security advisories from trusted sources.
By remaining vigilant, adapting your defences, and prioritizing security throughout the development lifecycle, you can create a secure environment for your app and safeguard your valuable data and user trust.
Frequently Asked Questions: Keeping Your App Up and Running
A highly available app is essential for ensuring user satisfaction and driving business success. Here are answers to some common questions about ensuring your app’s availability:
How do you ensure application availability?
There’s no single solution, but a layered approach combining:
- Proactive Monitoring: Utilize tools to track resource usage and identify potential issues before they cause outages.
- Scalability: Design your app to handle increasing user loads by quickly adding resources (servers) when needed.
- Secure Coding Practices: Write secure code with input validation and data sanitization to prevent vulnerabilities.
- Regular Security Audits: Conduct audits to identify and address weaknesses in your code and infrastructure.
- Incident Response Plan: Have a well-defined plan that outlines the steps to take in the event of a security breach or outage.
- Redundancy: Implement redundant systems and components to ensure that the failure of one element doesn’t bring down the entire app.
How can we improve availability?
- Focus on preventative measures: It’s more cost-effective and less disruptive to prevent outages than to fix them after they occur.
- Invest in automation: Automate tasks such as backups, updates, and scaling to reduce human error and enhance efficiency.
- Conduct regular testing: Stress-test your app to identify potential bottlenecks and ensure it can handle peak loads.
- Stay updated: Keep your software and libraries up to date with the latest security patches and bug fixes.
What are the tactics that would generally apply to improve availability?
Common tactics include:
- Load balancing: Distributing user traffic across multiple servers to prevent overloading any single server.
- Clustering: Grouping servers together so that if one fails, another can take over its workload seamlessly.
- Disaster recovery: Having a plan to restore your app and data quickly in case of a significant outage.
READ ALSO: Managing Open-Source Vulnerabilities Like A Pro!
What are the measures that can be implemented to improve system availability?
Many measures contribute to availability, including:
- Using reliable hardware and software: Invest in high-quality components with proven track records.
- Proper system configuration: Configure your systems for optimal performance and security.
- Effective logging and monitoring: Track system events and identify potential problems early.
- Regular maintenance: Schedule regular maintenance tasks to keep your systems running smoothly.
What are the major principles to ensure high availability?
The core principles for high availability include:
- Redundancy: Having multiple components that can take over if one fails.
- Scalability: The ability to easily add resources to handle increased load.
- Fault tolerance: Designing your app to continue operating even when some components fail.
- Disaster recovery: Having a plan to recover from significant outages quickly.
What is the high availability method?
High availability isn’t a single method; it’s a philosophy and a set of best practices to maximise your app’s uptime. It involves planning, proactive measures, and building resilience into your system from the ground up.
Addressing these questions and implementing these strategies can significantly increase your app’s availability and deliver a reliable user experience.
Conclusion
By following the tips above, you can increase the availability of your app and minimize the impact of any outages that do occur. This will help to ensure that your users continue to have a positive experience with your software and that your business remains competitive.
In addition to the above, it is also essential to understand your app’s architecture and how its various components interact with one another. This will help you to identify and address potential bottlenecks and vulnerabilities before they cause problems.
It is also essential to regularly test your app’s availability and performance under different conditions. This will help you identify any areas that need improvement and ensure that your app is ready to handle even the most demanding workloads.
INTERESTING POSTS
- 4 Top Cybersecurity Professions In 2024
- Things To Do When In Need Of IT Service
- Difference Between Bitcoin And Bitcoin Cash – Which Is Safer?
- 14 Best Protection Tools Against Hackers [100% WORKING]
- Best Antivirus For 2022
- Best VPN For 2022
- Mastering Mobile Experiences: Unleashing the Potential with a Mobile App Development Company
- 4 Essential Tactics For Increasing Sales Today














































 Furthermore, this program differs slightly from other forms of malware in that it causes little to no harm to the host computer or its inherent files.
Furthermore, this program differs slightly from other forms of malware in that it causes little to no harm to the host computer or its inherent files.

![When Is Hacking Illegal And Legal? [Honest Answer] When Is Hacking Illegal And Legal? [Honest Answer]](https://secureblitz.com/wp-content/uploads/2020/07/when-is-hacking-illegal-and-legal-768x591.jpg)










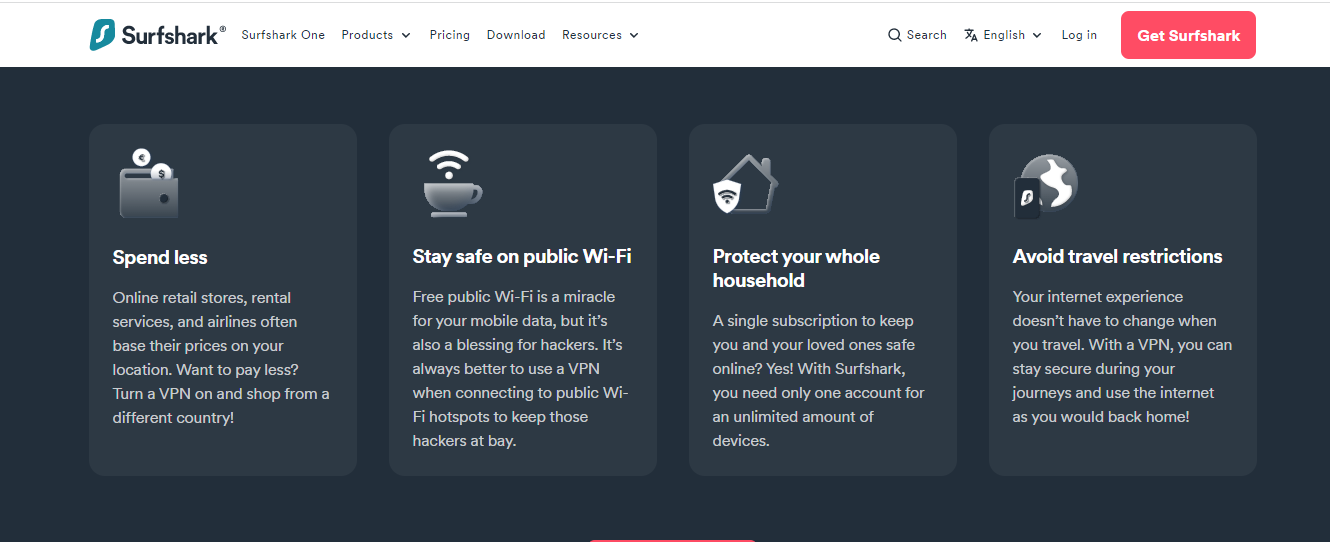 Surfshark works by re-routing incoming and outgoing data pathways from your device through a secure virtual encryption tunnel to any of its secure VPN servers in any country of your choice.
Surfshark works by re-routing incoming and outgoing data pathways from your device through a secure virtual encryption tunnel to any of its secure VPN servers in any country of your choice.
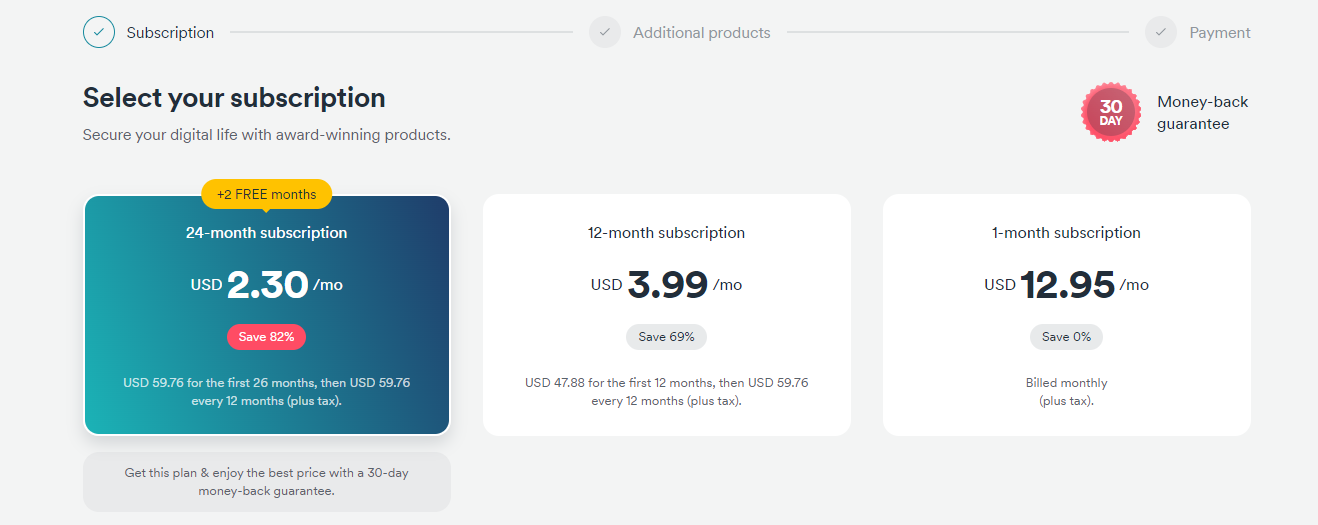
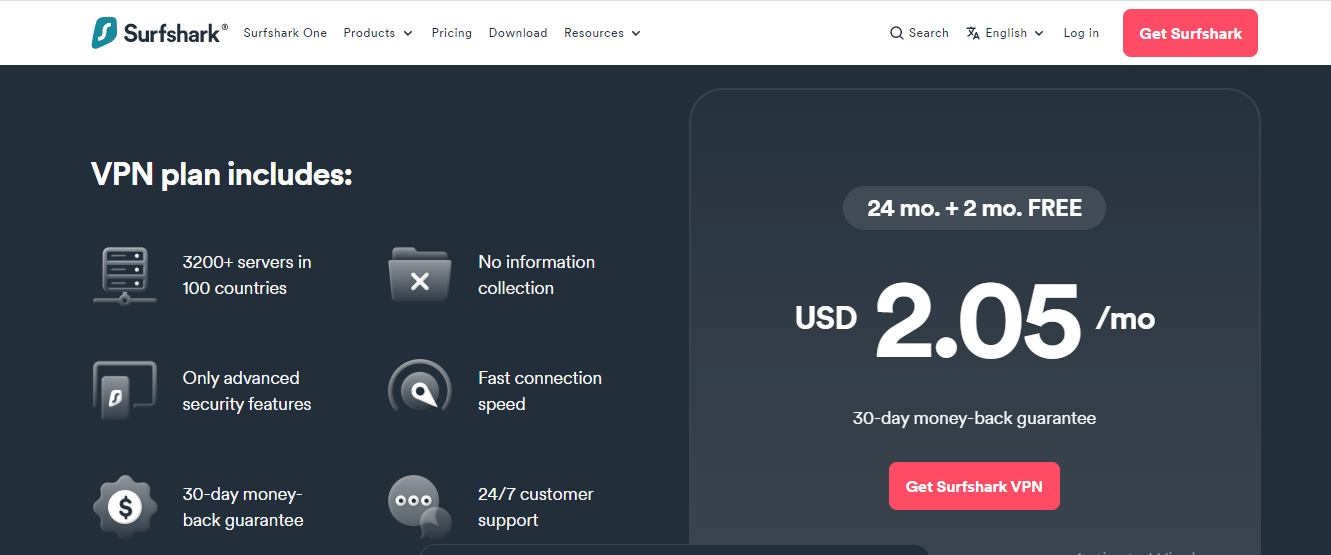
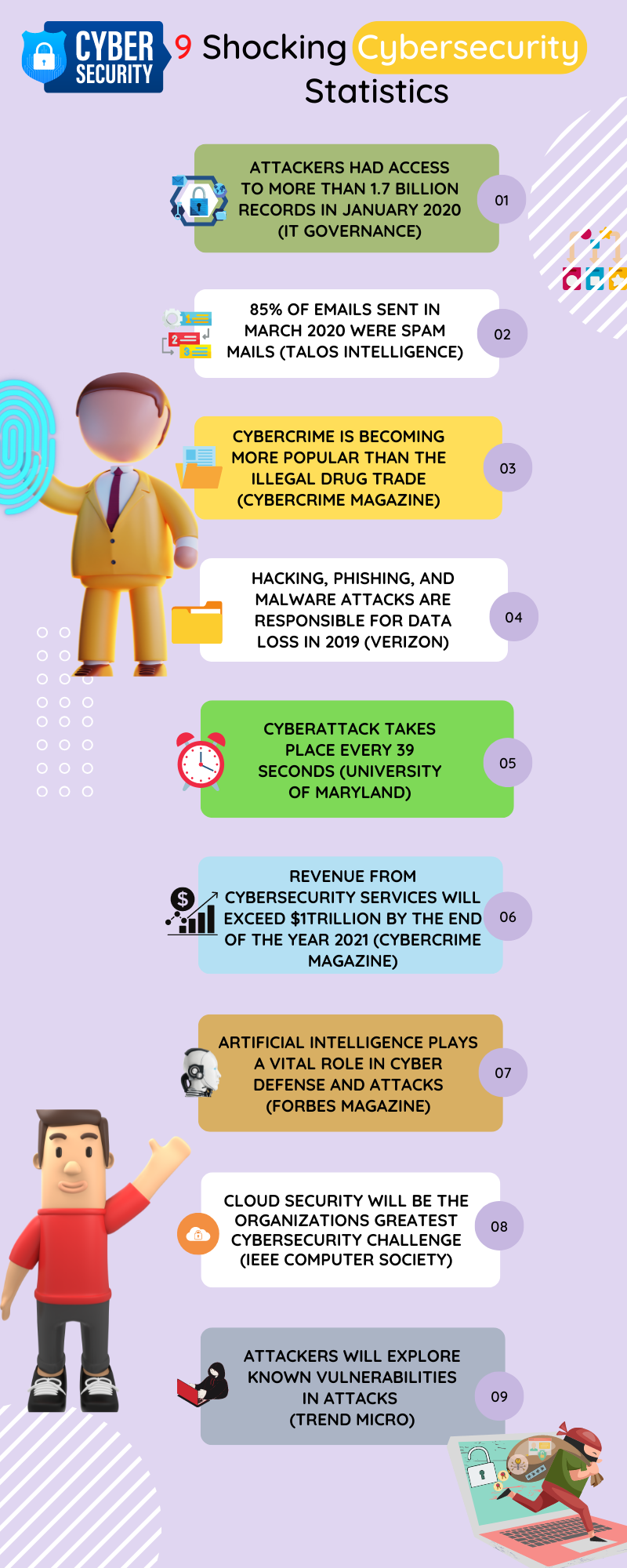
![9 Shocking Cybersecurity Statistics [With Infographics] 9 Shocking Cybersecurity Statistics [With Infographics]](https://secureblitz.com/wp-content/uploads/2021/02/9-Shocking-Cybersecurity-Statistics-1-768x345.png)