In this post, I will show you 5 reliable ways to backup your Android Device and tips to secure it.
Last summer, while on a family vacation to the beach, I clicked hundreds of photos on my phone to capture those moments. However, one day, my phone stopped working, and when it was repaired, I realized all my precious data was gone. It was a total disaster as I lost all important data on that device, including my special memories of our beach trip, forever. – Mary Acqulin
Reading about common data loss incidents on user forums has changed many perspectives on data security and made us realize the importance of regularly creating backups for Android devices.
If there is a technical issue or damage to our Android device, everything on it is lost. In this article, we’ll explore five easy ways to back up an Android smartphone and discuss methods to secure data, as well as tools to recover lost Android data without a backup. So, let’s get started!
Table of Contents
Why do we Need to Backup Our Android Devices?
We all store a lot of important information, including personal and sensitive data, on our phones these days – whether it’s photos, messages, contacts, or more. This makes it extremely crucial to back up our Android devices on a regular basis.
Here are some important reasons that explain why backing up your smartphone is so important:
Protect yourself from accidental data loss
Accidents can happen anytime! Smartphones are portable devices; hence, they can also get lost, stolen, or damaged in the course of usage. Without properly secured backups, you risk losing all your photos, messages, contacts, and other valuable data. Regular backups ensure you don’t lose anything, even if something goes wrong.
Avoid resource exhaustion during upgrades.
Whenever you upgrade to a new phone or perform a factory reset, transferring your smartphone data can be a troublesome task and needs to be done manually. Additionally, although the chance of data loss is low, it may still occur during the creation of a factory reset. Having backups offers you peace of mind in case of data loss and helps you restore everything from your backup. This saves a lot of time and hassle.
Secure your private photos and videos.
Our phones contain some of our most private and personal memories, like photos of family vacations. Without backups, there is a risk of losing these forever if the phone is compromised. Regular backups to the cloud or computer help secure these special memories.
Protect important documents and messages.
In addition to photos and videos, our phones often contain important documents, such as data spreadsheets, invoices, bills, and important messages, as well as notes. Regular backups ensure these documents don’t get lost, even if the phone is damaged or lost. This also helps avoid any trouble related to important conversations, legal docs, paperwork, and finances.
READ ALSO: Why Is Data Backup And Recovery So Important?
How to Backup Up Your Android Device safely?
In an increasingly digital world, our devices hold years of memories, contacts, and documents stored in hundreds of gigabytes. If your phone is lost or damaged, all that data could disappear without backups. This guide will show you easy yet effective backup solutions to ensure your data is protected.
Therefore, it’s essential to back up all your data, including contacts, photos, files, and app data, to a secure location, such as a storage device, cloud storage, or Google Drive. While backing up data is a necessity, adding encryption and an extra layer of security to your data protects it from external threats, data leakage, and unethical hackers. But how do we do so?
We are here to discuss 5 ways to back up your Android data and tips to securely safeguard and protect your data from being compromised on the internet. Let’s embark on this journey together as pro-Android users and manage your data across devices.
1. Manual Backup to a Computer
Manual backup is a process that involves manually backing up your Android device’s data, rather than relying on automatic cloud backups. This involves creating a backup of your Android device to your computer or an external storage drive.
This easy and convenient way to back up your Android device involves a few steps. However, it’s an outdated way and cannot help with data segregation or arrangement.
Steps to backup your device manually are provided here:
- Connect your Android phone to your Windows desktop with a USB cable.
- Look for your smartphone on my computer; it will get detected as an external storage device by the computer. For example, David’s Samsung Galaxy S24, John’s Nothing Phone 2 external drive.
- Now, open the detected external storage device to locate the folders on your computer, such as Downloads, Pictures, Audio, App Data, Documents, Videos, etc.
- Copy all the important folders you wish to backup and save them in a safe location.
How do you secure backed-up data on your computer?
With the increasing prevalence of data theft and cybercrimes, securing your backed-up Android device data has become necessary these days, and the process to ensure it is really easy. To encrypt your files, follow the steps below. This will password-protect your files and lock them against any unwanted intrusions.
- Right-click the file you want to encrypt, then select Properties.
- Under the General menu, click on Advanced to open the Advanced Attributes window.
- Next, select “Encrypt contents to secure data” from the options and hit the OK button.
- Now, click on the Apply button. A pop-up encryption warning will appear; select one of the provided options and then click OK.
- Your file will be secured. Hence, anybody without a password will not be able to delete, modify, or view the files or folders.
READ ALSO: What You Need To Know About Android Application Security
2. Back up to an SD card
Smartphone users can also back up their data directly to an external SD card inserted into their devices. This portable backup facility ensures data availability even when an active internet connection is not available.
This helps retrieve data in case your device experiences data loss due to a factory reset, hardware malfunction, or software issue.
If your Android phone supports an external microSD card, you can copy all the important folders to the SD card and create a handy backup.
- On your Android device, locate the folders with data you want to back up on your SD card, such as “DCIM” for internal camera photos.
- Select and copy the folders.
- Go to the SD card directory and paste the copied folders.
When required, you can restore all the backed-up data from the SD card to your device. This works as offline backup storage without needing a computer. However, the only drawback of having an SD card backup is that it will consume a significant amount of free space on your SD Card.
I lost my Android Device Data and don’t have a backup – What’s next?
Losing your Android device data can be heartbreaking, especially if you do not have backups and you have something really important in your device, be it your personal, professional, or legal documents. But do not lose hope; there’s still a way.
Stellar Data Recovery for Android can help scan and restore data from Android devices even without backups. With its simple and intuitive interface, you can easily connect any damaged, corrupted, or non-booting Android device to a computer running the software and regain access to files that were lost or accidentally deleted.
Best of all, it offers a free trial to scan and preview files before purchasing a license for the paid version. If you have lost your Android data without backups, the first step is to stop using your device. Without any delay, download Stellar Data Recovery for Android from the official website to recover all your precious files with its powerful data recovery engine.
Here is the step-by-step guide to using Stellar Data Recovery for Android and recovering lost Android data.
- Download and install the latest version of Stellar Data Recovery for Android from the official website on your computer.
- Connect your Android smartphone to your computer via a USB cable.
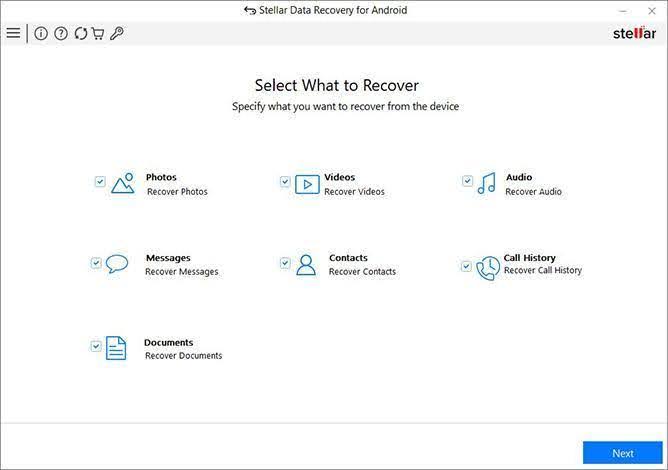
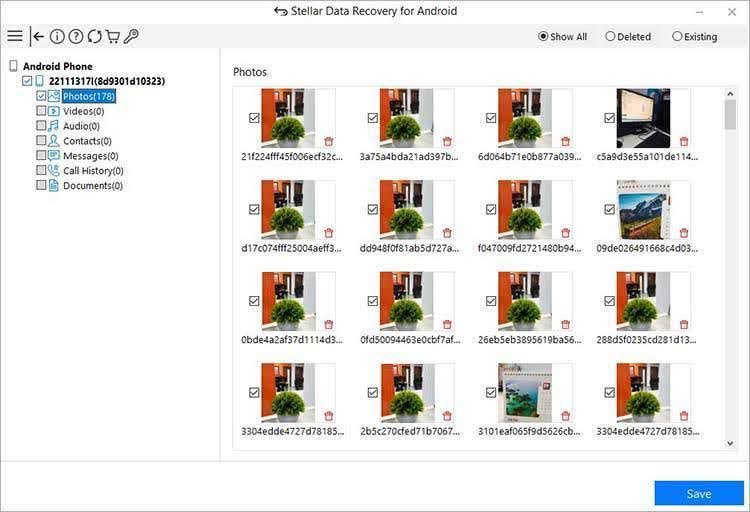
- Launch the application, and on the “Select What To Recover” page, select the file types you want to recover, as shown in the image below.

- Now, follow the steps shown in the application to enable USB debugging on your Android smartphone.
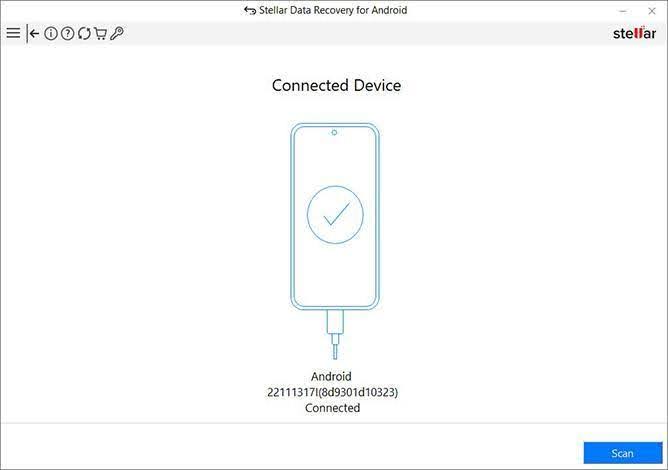
- Now, on the next screen, select the Android device from which you want to recover files, and then click on “Scan”.

- Wait for the application to scan your device and recover data.
- Once the scan is complete, you can see all recoverable files listed by type – images, videos, audio, call history, etc., and preview them as well.

- Click “Save” and then browse to the location where you want to restore the recovered data.
3. Backup to Google Drive
Google Drive is Google’s cloud storage service, allowing you to store and access files from any device. Your Android phone uses this feature to automatically back up important data. You must be signed in to your Google account on the phone to use it.
This will automatically and periodically back up data, including documents, contacts, calendar events, photos, and more.
- Go to Settings > System > Backup and Restore and ensure your smartphone’s backup setting is turned on.
- Under the Google Drive account, choose which account you want to back up to.
- You can select to back up Call history, Device Settings, Contacts, Apps and app data, Messages, Photos, and videos.
- Tap Backup now and wait for the backup process to complete.
- You can check the backup progress by going to Settings > System > Backup and Restore.
However, Google’s drive comes with a data limit, allowing backup of only up to 15GB of data in some regions.
Note: The above settings and steps may vary depending on your device and region.
4. Backup to Cloud
Major smartphone manufacturers, such as Samsung, Vivo, Oppo, and OnePlus, offer free cloud backup services to help back up your data to the cloud.
These free cloud storage services are easily accessible from the phone Settings. Similar to Google OneDrive, all Cloud backups offer ease of access, all-around accessibility, and data security.
For example, on a Vivo phone, go to Settings, then select Backup and Restore, and access Vivocloud. Sign in using your Vivo ID credentials to start the backup. Similarly, every manufacturer-backed cloud service has its specific settings, though you need login credentials for each.
Follow the steps to log in and back up data to your Android smartphone’s cloud service.
- You can select to back up Call history, Device Settings, Contacts, Apps and app data, Messages, Photos, and videos.
- Tap Backup now and wait for the backup process to complete.
- You can check the backup progress by going to Settings > System > Backup and Restore.
READ ALSO: What is Data Recovery: Its Importance and Application?
5. Backup to Dropbox
Dropbox is a file hosting service that offers cloud storage and file synchronization. It allows users to create a folder on their devices, and with the drag-and-drop feature, it automatically syncs files placed there to Dropbox’s servers and other computers and devices.
It offers up to 2GB free storage, is easy to use and can be accessed from anywhere with the help of an active internet.
Here are the steps to use Dropbox:
- Sign up for a Dropbox account on the official website.
- Install the Dropbox app from the Play Store and sign in using your account credentials.
- This will automatically create a Dropbox folder; drag the files into this folder that you want to backup.
- This will automatically back up the files to the Dropbox cloud and sync data between your devices.
- You can access the backed-up files from any device by simply logging in or using the Dropbox website.
Conclusion
While all the above data backup options are of great help, it is essential to understand that relying on any one of them may be risky.
While cloud backup options offer convenient access and regular automatic backups, manual backups provide increased control of your data with secure encryption and huge storage. Based on your needs, you must choose two ways to back up and secure your Android data.
However, if your data is lost accidentally without a backup in place, you can rely on Stellar Data Recovery for Android to get back your lost Android device data.
INTERESTING POSTS
















![Is Carbonite Safe To Use? [Unbiased ANSWER] Is Carbonite Safe To Use? [Unbiased ANSWER]](https://secureblitz.com/wp-content/uploads/2024/01/Is-Carbonite-Safe-To-Use-Unbiased-ANSWER-768x402.jpg)






























![Hacker leaks over 23 million user data on Webkinz World [OLD NEWS] Hacker leaks over 23 million user data on Webkinz World [OLD NEWS]](https://secureblitz.com/wp-content/uploads/2020/05/webkinz-world-hack-768x432.jpg)