Read on as I show you the OmniWatch Online Identity Protection review.
Identity theft is a growing concern, and many platforms exist to help you fight it. OmniWatch is one such solution. The platform offers a solution to protect against its impacts.
With a range of services like breach monitoring and insurance, OmniWatch promises to help safeguard your property and limit the damages that hackers can inflict.
In this OmniWatch Online Identity Protection review, we’ll explore what the platform offers, how it works, and its benefits. So, if you want to sign up and use the platform, read on to find all the details you need.
Table of Contents
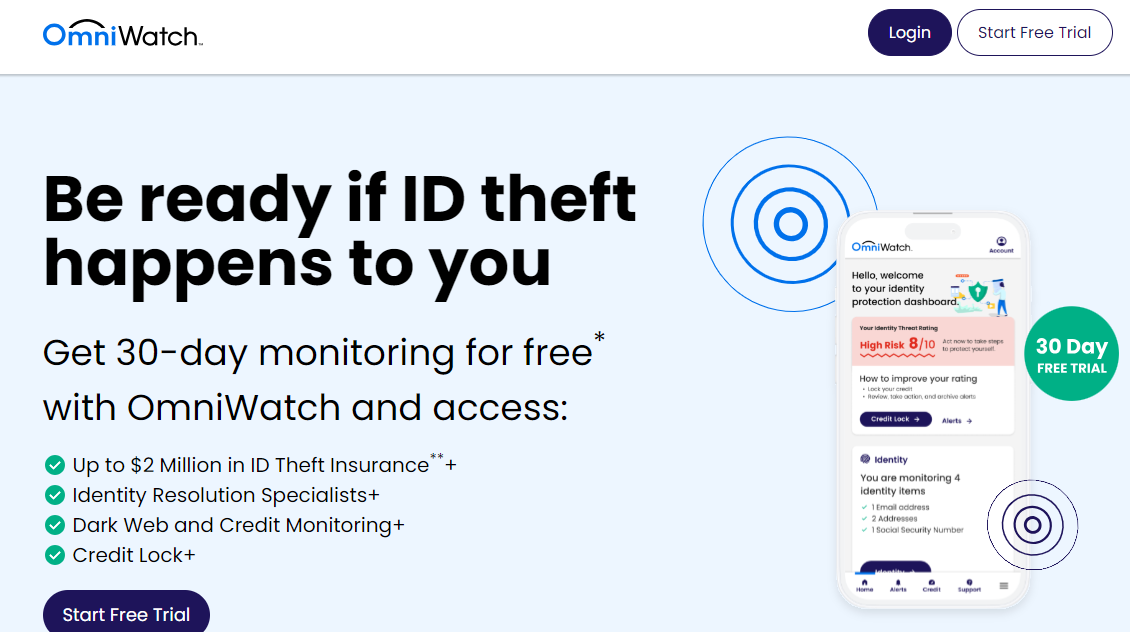
What is OmniWatch Online Identity Protection?
OmniWatch Online Identity Protection provides a service designed to shield your assets. It provides up to $2 million in insurance to cover financial losses, legal fees, and lost wages from identity theft incidents.
The service also includes a credit lock feature that secures your credit files across major bureaus, preventing unauthorized openings of new accounts. One of the best features yet is that OmniWatch monitors your credit and alerts you to potential exporters on the dark web.
The platform assigns an Identity Risk Score reflecting your exposure level based on breached data and advises mitigating risks.
Furthermore, US-based identity resolution experts are on standby 24/7, offering hands-on assistance. These include paperwork and guidance through recovery should your identity be compromised.
Overall, OmniWatch services aim to mitigate identity theft and offer recovery support. Hence, it’s a comprehensive platform to protect against such risks.
🔐 Get Started with OmniWatch’s Free Trial in 4 Easy Steps:
- 🔍 Step 1: Head over to the OmniWatch homepage and click the inviting “Start Your Free Trial” button.
- 📋 Step 2: Select the plan that best suits your needs. OmniWatch offers various plans with different features and durations.
- ✏️ Step 3: Fill in your name, email address, and preferred payment method. Don’t worry; you won’t be charged during the free trial period.
- 📧 Step 4: Check your email for a verification link. Click it to activate your account and unlock the full potential of OmniWatch’s free trial.
🎉 Congratulations! OmniWatch’s powerful features will now protect you!
Features of OmniWatch Online Identity Protection
There’s a lot to leverage when you register for OmniWatch.
Below, we discuss each of the features in detail as I tested for this OmniWatch review:
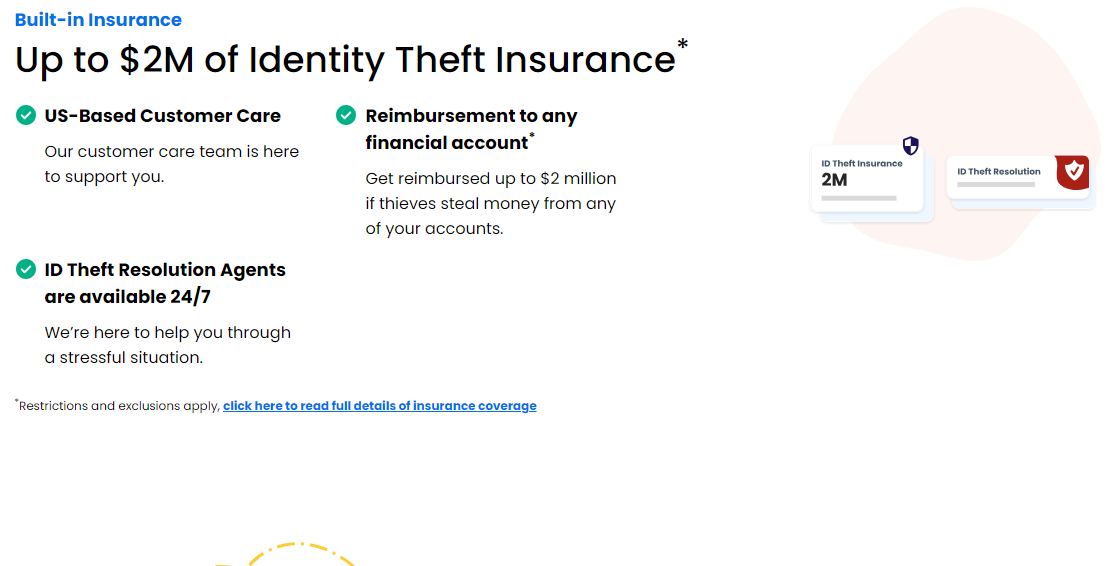
Up to $2 Million in Identity Theft Insurance
OmniWatch stands out with its substantial identity theft insurance offering, which promises to deliver significant financial reassurance. If you fall prey to identity theft, this feature provides up to $2 million in insurance coverage. That’ll reduce the financial impact on you.
The broad coverage extends beyond reimbursement for stolen funds from your bank accounts. It also encompasses potential legal fees, should you need to seek legal counsel or take legal action against fraudsters. Additionally, if restoring your identity requires time off work, the insurance aims to cover lost wages.
This safety feature aims to give you the confidence that you will not have to bear the full loss alone in the face of identity theft. It’s important to note that such a comprehensive insurance package comes with certain terms and restrictions.
Nevertheless, OmniWatch provides detailed information on the extent of the coverage, ensuring you are fully aware of the conditions that apply. This feature underscores OmniWatch’s commitment to providing robust support in the event of identity theft.
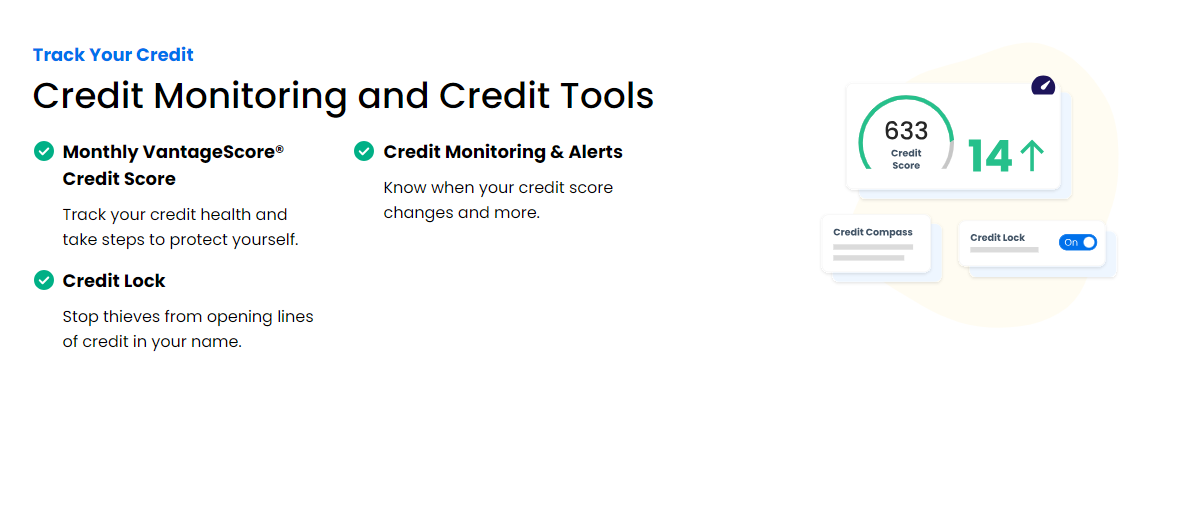
Credit Lock+
The Credit Lock+ feature OmniWatch provides is a pivotal security measure designed to empower you with direct control over your credit profile. This option is crucial today, where credit-related fraud is a common target for identity thieves.
With OmniWatch’s assistance, managing the security of your credit files becomes simple, giving you a vital edge in personal information security.
By locking your TransUnion credit file through OmniWatch, you take a significant step in preventing fraudulent accounts from being opened in your name. Identity thieves often attempt to exploit credit profiles to open unauthorized accounts.
However, this feature blocks such actions as lenders cannot access your locked credit files to approve new applications.
OmniWatch Protection extends this protective measure by assisting you with securing your credit information across all major credit bureaus. This includes helping you to lock your Equifax credit files and freeze your Experian credit files. All these ensure your credit standing is shielded on all fronts.
The comprehensive nature of this feature means that you are protected against identity theft at the primary points of financial inquiry.
So, by utilizing the Credit Lock+ feature, maintain the peace of mind that comes with knowing your credit files are inaccessible to unauthorized parties.
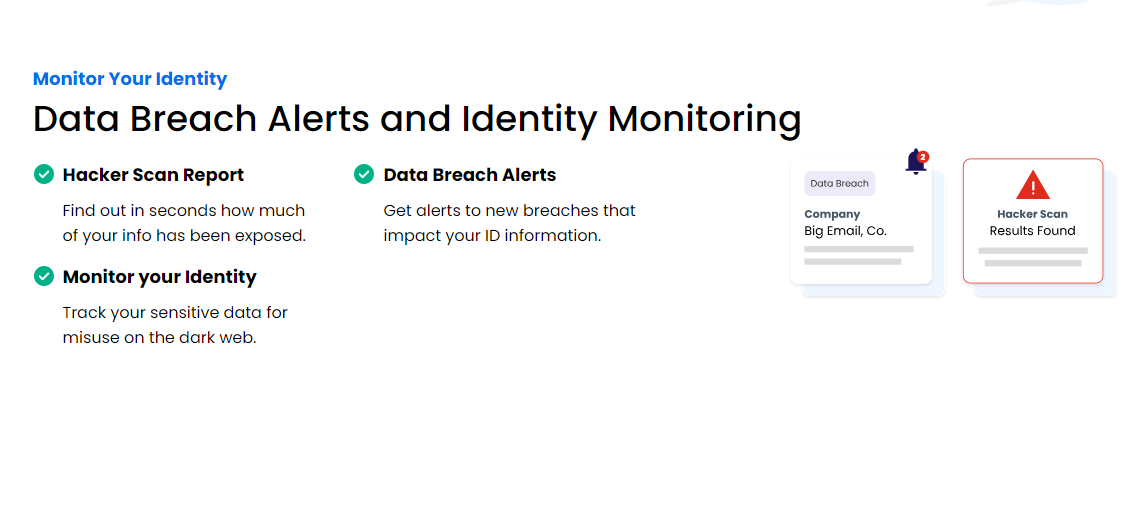
Dark Web & Credit Monitoring
OmniWatch Online Identity Protection provides a vigilant eye with its dark web & credit monitoring feature. It’s designed to alert you to potential threats to your personal and financial information. This dual-aspect monitoring is crucial in an online space where data breaches are increasingly common.
The credit monitoring aspect of this feature keeps a close watch on your credit report. Should there be any changes—such as inquiries from lenders, new accounts being opened, or changes to your credit limit—you will receive timely alerts. This immediate notification system allows you to act quickly if the changes are unauthorized, helping to prevent further fraudulent activity.
Simultaneously, OmniWatch scans the dark web—a part of the internet notorious for illicit activities, including the buying and selling stolen personal information. If OmniWatch detects your personal details, such as social security numbers or bank account information, on the dark web, you will get an alert.
Such early warning is vital, as it can often be the first sign that your information has been compromised. Hence, you can secure your accounts before they can be used fraudulently. Together, these monitoring services provide a comprehensive shield, helping to secure your identity from two critical angles.
Particularly, this feature serves not only as a detection mechanism but as a preventative strategy. This function enables you to respond proactively to threats before they escalate into identity theft.
Overall, with OmniWatch’s Dark Web & Credit Monitoring, you gain a valuable ally in the ongoing effort to protect your identity online.
Identity Risk Score
You’ll find the OmniWatch’s Identity Risk Score really valuable. It’s a personalized metric that assesses your vulnerability to identity theft based on your online exposure. This feature analyzes various types of your personal data that may have been compromised or breached on the internet.
Note that the score is not static. Rather, it updates as new data breaches are detected, providing a dynamic and current assessment of your risk level. With each reported breach, OmniWatch doesn’t just leave you with a number; it offers actionable insights.
The service breaks down the breached information and guides you on specific steps to help mitigate the damage. For example, if your email address has been found on compromised lists, OmniWatch may suggest changing passwords or setting up two-factor authentication for affected accounts.
Regardless of your online activities, the Identity Risk Score is a crucial tool in your digital defense strategy. It offers both awareness and guidance. That’s because OmniWatch educates you about your digital footprint’s security status and empowers you with the knowledge to reinforce your defences.
By understanding your Identity Risk Score and following OmniWatch’s recommendations, you can proactively lower your chances of further losses. That means you maintain a stronger stance against identity theft.
Identity Resolution Experts+
OmniWatch provides around-the-clock access to U.S.-based Identity Resolution Experts, ensuring that you have expert assistance available anytime your identity is at risk. This service is a critical component of the platform’s comprehensive approach to identity protection.
When you face the challenge of identity theft, the recovery process can be daunting. OmniWatch’s specialists step in to ease this burden. They are trained to act promptly and efficiently, guiding you through the necessary steps to reclaim your identity.
The steps include filing reports, contacting financial institutions, and handling paperwork that may be complex and time-consuming. Having a dedicated agent means personalized support tailored to your specific situation.
These experts help in the immediate response following identity theft and provide ongoing support throughout the recovery process.
Furthermore, they work on your behalf to ensure that every resolution aspect is managed properly. It covers initiating fraud alerts, freezing credit files, and interfacing with law enforcement if necessary.
With OmniWatch’s Identity Resolution Experts, you are not alone in facing the repercussions of identity theft. Instead, you have professional help to restore your identity and secure your personal information.
How to Sign Up For OmniWatch Identity Theft Protection
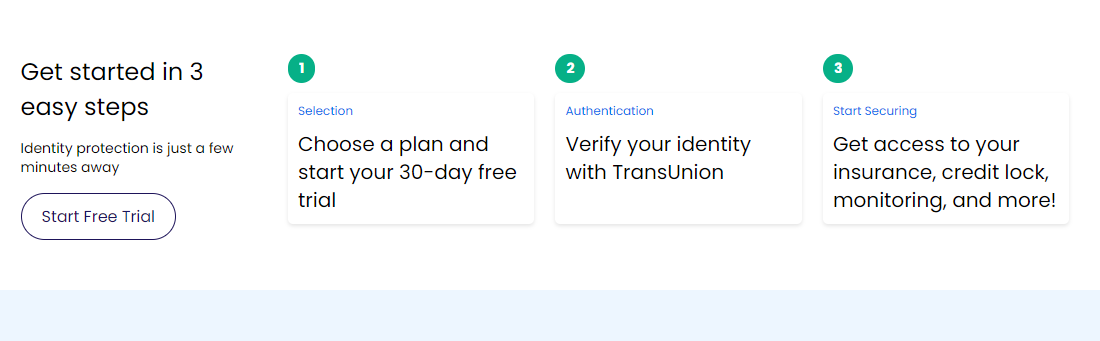
Signing up for OmniWatch’s comprehensive identity protection service is a breeze and can be done in three simple steps. In just a few minutes, you can start your journey to securing your personal information with a robust suite of tools at your fingertips.
Here’s how to get started:
1. Choose your subscription plan
Your first step is to choose the protection plan that fits your needs. OmniWatch offers various plans, each designed to provide the right level of security for different customer requirements. We’ll cover these subsequently.
Once you select the plan that suits you best, you can sign up for a 30-day free trial. This trial period allows you to experience OmniWatch’s services without any commitment. Simply visit the OmniWatch website, browse through the plans, and click ‘Start Free Trial’ for your chosen one.
2. Verify your identity
After you’ve picked a plan, the next step is to verify your identity. OmniWatch partners with TransUnion, a trusted credit bureau, to ensure your identity is protected throughout this process.
You’ll be asked to provide some personal information, and TransUnion will verify your identity to help protect against unauthorized access or fraud. Note that this step is crucial for setting up your account, and it’s handled with the utmost security to ensure your privacy and safety.
3. Start using OmniWatch
Once your identity is verified, you can activate your account. You’ll gain immediate access to OmniWatch’s suite of protection tools. As explained earlier, this includes insurance coverage against identity theft, a credit lock functionality that helps safeguard your credit reports, continuous monitoring of your personal information, and much more.
With OmniWatch Identity Theft Protection, you’ll have the peace of mind of knowing that your identity is being watched around the clock.
Editor’s Note: You can opt for the free trial prior to making a premium commitment to evaluate the OmniWatch features. In my own experience before crafting this OmniWatch review, I evaluated it and I will highly recommend it for its key features like dark web monitoring, credit lock, credit protection, and identity protection.
OmniWatch Customer Support
For this OmniWatch Online Identity Protection review, I will say that as a quality identity theft protection service, OmniWatch’s customer support is designed to provide comprehensive assistance. They ensure you have access to help whenever they need it.
Based in the United States, the support team is described as friendly and is tasked with offering assistance for account issues and alerts.
Here are the details of the customer support options available:
- Email Support: You can contact OmniWatch’s customer care via email for non-urgent inquiries or support needs.
- Phone Support: For immediate assistance, you can call their toll-free phone number (877) 892-8249. The number is active during business hours, Monday through Friday, from 7 a.m. to 4 p.m. PT (10 a.m. to 7 p.m. ET). Note that holiday hours may vary.
- Mailing Address: For correspondence that requires sending or receiving physical documents, you can use the mailing address — OmniWatch, LLC, 3111 Camino Del Rio N, Suite 400, San Diego, CA 92108.
- Live Chat: If you need quick answers to their questions, OmniWatch offers a live chat feature, providing real-time support. I spoke with them before composing this OmniWatch review, and they helped me with the smooth onboarding process.
- Help Center: OmniWatch also has a detailed help center, a valuable resource to help find answers to common questions. You can also learn more about managing your account and the features offered.
This multi-channel support system ensures that you have various ways to get help. You have options whether you prefer self-service options like the help center, real-time assistance via live chat, or direct contact through email or phone.
Now, for this OmniWatch Online Identity Protection review, let me talk about its pricing.
OmniWatch Identity Theft Protection Pricing
OmniWatch provides two pricing tiers for its identity theft protection services. As stated earlier, both feature a 30-day free trial to start.
Check them out below:
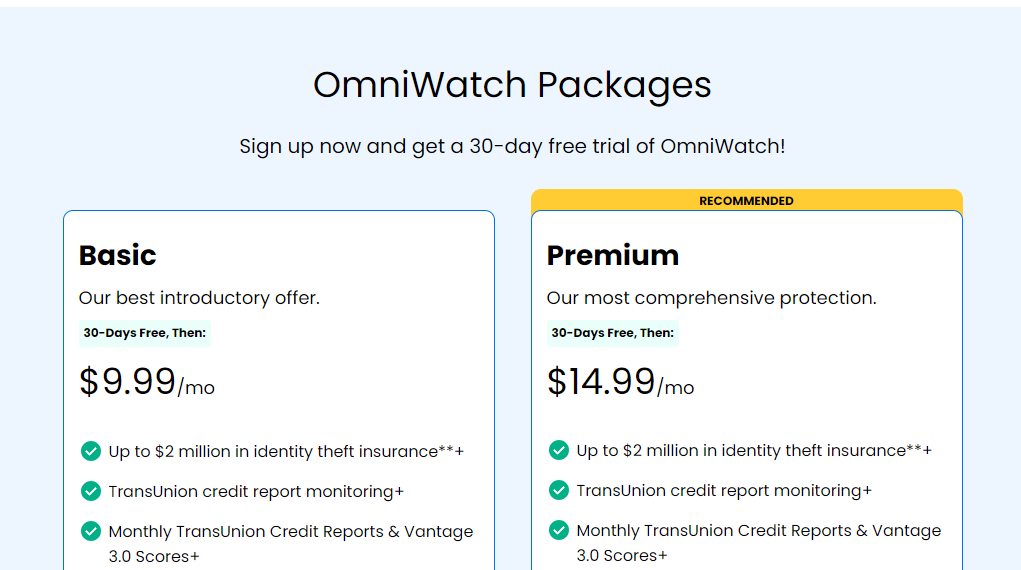
Basic Plan
This plan costs $9.99 per month, and the features include:
- Up to $2 million in identity theft insurance.
- TransUnion credit report monitoring.
- Monthly TransUnion Credit Reports & Vantage 3.0 Scores.
- TransUnion Credit Lock.
- Stolen Funds Reimbursement for any financial account.
- 24/7 U.S.-based dedicated restoration agents.
- Dark Web Monitoring.
Premium Plan
The premium plan costs $14.99 per month, and these are the features you get:
- All the features of the Basic plan
- TransUnion, Experian, & Equifax credit monitoring
- TransUnion, Experian, & Equifax credit reports (1 every 90 days)
- Up to $25,000 in ransomware protection.
The primary distinction between the Basic and Premium plans lies in the ransomware protection. The Premium plan offers this additional safeguard, which is not included in the Basic plan.
However, both plans share comprehensive identity theft protection features after the initial free trial. Also, they renew monthly at their respective prices, but note that costs can change anytime.
Benefits of OmniWatch
With OmniWatch, you benefit from comprehensive services designed to protect you from identity theft.
Here are some benefits of OmniWatch:
- Financial Protection: You’re covered with up to $2 million in identity theft insurance. That offers financial relief if you suffer from stolen funds, legal fees, or lost wages due to identity theft.
- Credit Vigilance: OmniWatch offers continuous monitoring of your credit reports from all three major bureaus and alerts you to any changes. It helps you catch fraud quickly. Also, the monthly reports and scores keep you informed about your credit health.
- Control Over Credit Access: The ability to lock your TransUnion credit file gives you control over who can access your credit information. It prevents unauthorized account openings.
- Recovery Support: If you fall victim to identity theft, you have access to 24/7 U.S.-based dedicated agents. They’ll assist you through the recovery process, handling paperwork and a wide range of complex tasks.
- Dark Web Monitoring: You’re alerted if your personal information surfaces on the dark web. This is often a precursor to identity theft, allowing you to take immediate protective actions.
- Ransomware Safeguard: With the Premium plan, you get additional protection against ransomware threats, with coverage that helps recover your data without paying a ransom.
- Ease of Use: Starting with a free trial lets you explore OmniWatch’s offerings without upfront costs. Also, the subscription process is simple and user-friendly as depicted in this OmniWatch review.
- Knowledge Empowerment: You’re not just protected; you’re also educated on improving your data security and reducing your risk of identity theft.
From all these benefits, one thing is clear. That is, OmniWatch aims to offer you peace of mind with robust protections, ensuring your financial and personal information remains secure.
Omniwatch Review: Omniwatch Pros And Cons
Omniwatch Pros
- Comprehensive features: OmniWatch offers a variety of features for a reasonable price, including dark web monitoring, credit monitoring, credit lock, identity theft insurance, and identity restoration services.
- Affordable: Compared to other identity protection services, OmniWatch offers its features at a competitive price point.
- Good customer service: OmniWatch has a good reputation for providing excellent customer service. They offer various support channels, including phone, email, and chat, and are known for their responsiveness and helpfulness.
- Easy to use: The OmniWatch interface is user-friendly and straightforward, making it easy to navigate and understand even for non-technical users.
- Up to $2 million in identity theft insurance: OmniWatch provides a significant amount of insurance coverage, offering financial peace of mind in case of identity theft.
- $25,000 ransomware protection: This extra layer of protection adds to OmniWatch’s value proposition.
Omniwatch Cons
- Limited monitoring sources: While OmniWatch offers essential monitoring, it lacks coverage in areas like financial activity, home title, and USPS monitoring, which some competitors provide.
- No family plans: OmniWatch currently only offers individual plans, which can be limiting for families seeking comprehensive protection.
Omniwatch Review: Frequently Asked Questions
What features does OmniWatch offer?
OmniWatch offers a comprehensive package of identity protection features, including:
- Dark web monitoring: OmniWatch scans the dark web for any instances of your personal information, such as your Social Security number, address, and email addresses.
- Credit monitoring: OmniWatch tracks your credit report for any suspicious activity like unauthorized credit inquiries or new accounts opened in your name.
- Credit lock: OmniWatch allows you to freeze your credit report, preventing anyone from opening new lines of credit without your approval.
- Identity theft insurance: OmniWatch offers up to $2 million in insurance coverage to help you recover from financial losses incurred due to identity theft.
- Identity restoration services: OmniWatch provides expert assistance to help you restore your identity in case of theft, including contacting creditors and government agencies.
- Ransomware protection: OmniWatch offers up to $25,000 in coverage to help you recover from data breaches and ransomware attacks.
Is OmniWatch Online Identity Protection Legit?
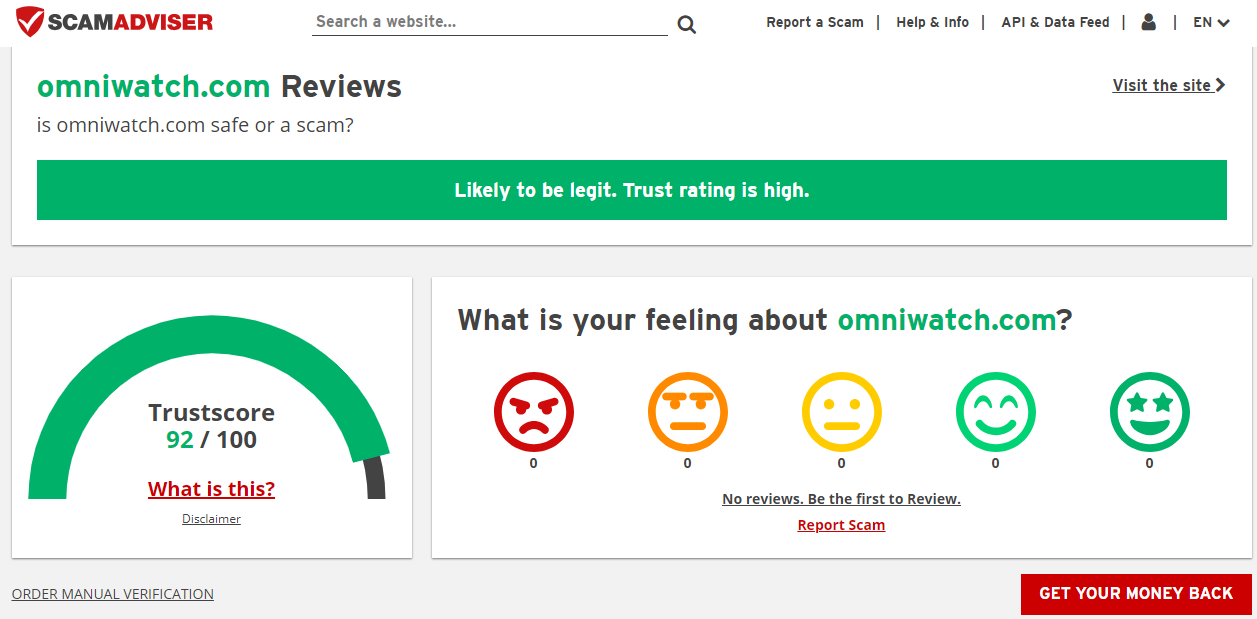
As you can see from this OmniWatch Online Identity Protection review, OmniWatch is relatively new, so there are not many reviews from users. However, the platform has been analyzed by Scamadviser and is considered legit with a high trust rating.
It’s worth noting that Scamadviser’s automated algorithm reviews websites based on 40 different facts found in public sources.
This includes listings on phishing and spam sites, whether it serves malware, the country the company is based in, and the reputation of the domain registrar, among others. Since OmniWatch passes this check, it’s clear the platform is legit.
Is OmniWatch Worth It?
Absolutely! OmniWatch presents a compelling value proposition for several reasons:
- Comprehensive Protection: Offers all essential identity theft protection features at a competitive price.
- Affordable Pricing: Starts at $9.99 per month, making it accessible to most individuals.
- Easy to Use: A User-friendly interface makes managing your protection effortless.
- Mobile App: Monitor your information and take action on the go.
- Additional Protections: Includes up to $2 million in identity theft insurance and $25,000 in ransomware protection.
- Constantly Evolving: OmniWatch regularly adds new features and updates to keep you ahead of the latest threats.
OmniWatch’s core features are unmatched in terms of affordability and ease of use. It’s a fantastic option for individuals seeking comprehensive identity protection without breaking the bank.
A Final Word On The OmniWatch Online Identity Protection Review
To conclude this OmniWatch review, I will say OmniWatch presents itself as a robust identity theft protection service with comprehensive features designed to safeguard your personal and financial information.
With options like credit monitoring, identity theft insurance, credit lock, and a dedicated support team, it’s equipped to provide peace of mind in an increasingly digital world. Also, the U.S.-based customer support and multiple channels, including a live chat, add to the reliability of the service.
Considering the detailed features, the protective measures in place, and the positive trust indicators from online reviews, OmniWatch appears to be a legitimate service worth considering.
If you want to improve your defence against identity theft, sign up for OmniWatch’s free trial. Test the tool, and if it works for you, subscribe and continue protecting your identity online.
RELATED ARTICLES
- Identity Protection Explained in Fewer than 140 Characters
- How To Protect Your Online Identity In 2023
- 5 Certified Benefits of Identity Theft Protection
- Online Privacy Explained: What It Is, Why It’s Important, and How to Protect It
- How To Lock And Unlock Your Windows PC With A Pendrive Like A Pro!
- Importance Of Dark Web Monitoring
- Identity Protection Guide: Safeguarding Your Personal Data
- Identity Theft Is Not A Joke, Jim [MUST READ]
About the Author:
Daniel Segun is the Founder and CEO of SecureBlitz Cybersecurity Media, with a background in Computer Science and Digital Marketing. When not writing, he's probably busy designing graphics or developing websites.