In this post, I will show you the most secure online payment services. Read on!
A secure online payment service makes transactions between you and your clients possible.
Choosing the right one for your business instills trust in your customers as they make purchases. With so many options online today, you may find it challenging to make the right choice.
So, we’ll be recommending some of the most secure online payment services today.
Let’s dive in;
Table of Contents
Most Secure Online Payment Services
Here’s a list of the most secure online payment services!
1. Payoneer
Payoneer is among the most secure online payment and international money services you can use for your business. With Payoneer, you can send and receive funds with an e-wallet, virtual bank account number, or MasterCard debit card.
This platform is best for individual business owners or freelancers in developing countries having difficulty receiving payments from clients overseas.
It is also the go-to platform for those who need to receive payment from big companies like Amazon and Google Adsense.
Based on the reviews on G2, many users of Payoneer found their service secure and reliable except for a few having issues with stuck funds.
To get started with Payoneer, visit their official website to create an account, create virtual bank accounts and explore its amazing features. The Payoneer app is available on both PlayStore and AppleStore.
==>> Get free $25 with Payoneer
2. Wise (Transferwise)
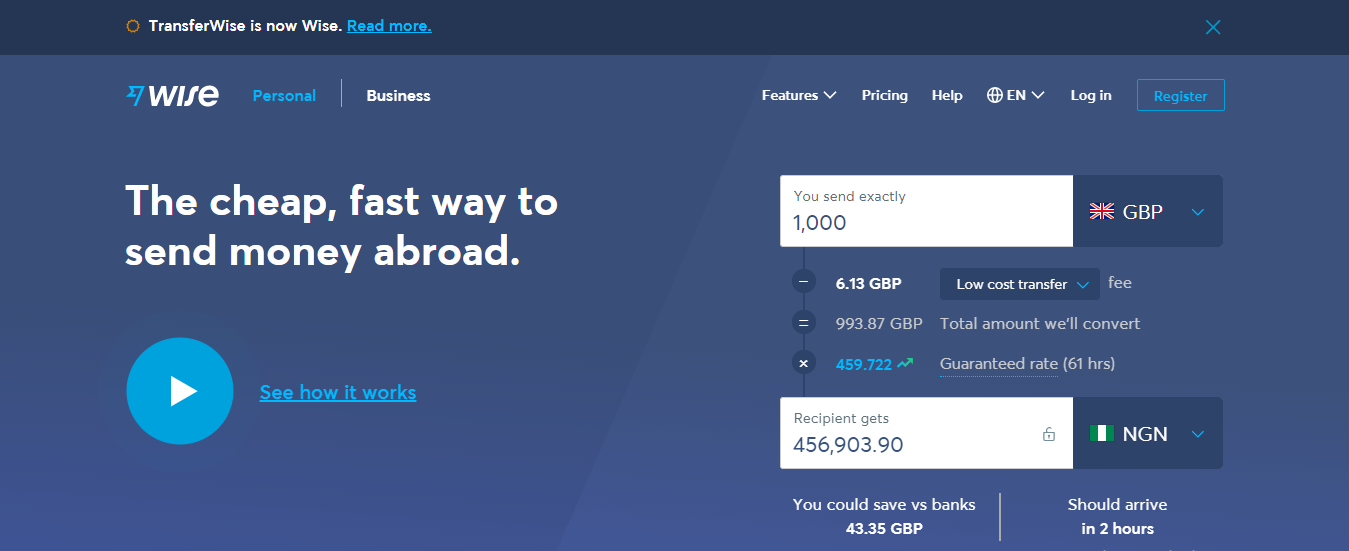
Wise, formerly known as Transferwise is an international money transfer service similar to Payoneer. It is among the cheapest, fastest, and most accessible ways to send and receive money internationally.
Wise operates in over eighty countries, converts up to fifty-three currencies, and receives money like a local in nine currencies.
It is best for any individual or business owner who wants to receive payment from any part of the world. It is also a go-to option to make purchases in foreign online stores. Travelers too can take advantage of the currency converter feature to spend in their preferred currency. For those exploring a Wise alternative, similar platforms offer competitive exchange rates and low transfer fees, making global transactions even more convenient.
Getting started with Wise is as simple as just registering on their official website. Registration is free but you might need to pay little charges for sending money, converting money, receiving USD wire transfers, and more.
==>> Get Wise
3. Amazon Pay
Amazon pay is owned by the giant company ‘Amazon’. This online payment service allows customers to use their Amazon account information to make purchases on eCommerce platforms.
If you are a merchant, you can use Amazon Pay on your eCommerce store to receive payments from your customers.
Amazon Pay can be integrated with eCommerce platforms like Amazon, Shopify, Magento, BigCommerce, and more.
Just like other Amazon products, Amazon Pay is highly rated by its users. It has a rating of 4.5/5 on G2 with many of its users commending it for its fastness, security, multiple payment options, features, and flexibility.
Unlike Wise which is available for multiple countries, Amazon Pay is said to work best for US residents. To use Amazon Pay on your eCommerce website, you need to create an Amazon seller account and then copy and embed the code on your website.
4. Google Pay
Google Pay is an online payment app developed by Google to enable users to make payments with their mobile devices.
It allows you to send and receive payments from both friends and business partners. Google Pay has amazing features like storing card details for faster access, tracking your spending activities, and more.
If you own an app or a website, you can use Google Pay to receive payments from your customers.
You can also use it to accept donations, subscriptions, and more. It is free to use, easy to implement, and provides a great shopping experience for your customers.
5. Verifone (fka 2CheckOut)
2CheckOut is another great addition to this list. It was founded in 2006 by Verifone and has over twenty thousand active users worldwide.
It operates in over one hundred and eighty countries and is trusted by top companies like myFICO, Advisera, Malwarebytes, and more.
Many companies integrate 2checkout on their website because it makes it easier for them to receive payments from their customers. Aside from receiving payments, you’ll enjoy other features like subscription billing, risk management, and compliance; and more.
Integrating 2CheckOut into your eCommerce website will help you do the following;
- Receive payment globally.
- Maximize your customer lifetime value through a good user experience.
- Growth recurring revenue.
- Accelerate time to market.
If we continue with the benefits of using 2CheckOut, we might make a whole post. So, let’s move to Apple Pay.
6. Apple Pay

This is one of the many Apple products which works like Google Pay. But trust Apple to always make their products exclusively for their users. So, you can’t use Apple Pay if you don’t use an Apple device like iPhone, iPad, or Mac.
Apple pay was created to help its users handle money with ease. You can send and receive money, make purchases, and carry all sorts of transactions without moving about with physical cards or cash.
One of the major advantages of using Apple Pay is the level of security – it is very high. Since Apple Pay is accepted by many apps and online stores, you can make purchases in just one click as long as you are using an Apple device.
If you own a business and wish to accept payment using Apple pay, then you should visit Apple Pay for developers.
7. Stripe
Stripe is one of the most popular online payment services. It is used by millions of companies of different sizes to send out and receive payments.
With the Stripe API, you can integrate a payment gateway to your website so that you collect payments from your customers faster and easier. Freelancers too can use stripe to receive payments from their clients around the world.
Getting started with stripe only requires you to create an account with them.
8. PayPal
PayPal is arguably the most used secure online payment service worldwide. It is one of the fastest ways to send and receive money locally and internationally.
Paypal has so many features that make it the right choice for many individuals and business owners. According to them, there are over 200 million active Paypal accounts worldwide to show how popular they are.
Paypal is the people’s choice because it is available in almost all countries, is fast, reliable, and highly protected. Paypal will refund you if you don’t get the value for any payment made using the platform.
Business owners too can integrate Paypal on their website to accept payment from their customers around the world.
9. Braintree
Braintree is a PayPal partner that allows you to integrate other payment services like PayPal, Venmo, Apple Pay, Google Pay, and more in a single integration.
This platform is best for eCommerce store owners who wish to have multiple payment options on their websites. They can create custom payment plugins for their customers to process once-off payments, recurring payments, or donations/payments.
Braintree supports web and Android devices. It comes with features like reporting/analytics, billing and invoicing, data security, API, and more. Its ideal users include; freelancers, SMBs, and large enterprises.
10. WePay
WePay is a secure payment gateway similar to Braintree. It provides online payment services through its APIs to platforms like eCommerce, apps, crowdfunding sites, or some online marketplaces.
WePay unlocks new growth opportunities for your business through a seamless payment experience for your customers.
This SaaS solution offers fraud and risk protection and has been rated high by its users. Some popular brands using WePay include; BigCommerce, FreshBooks, Constant Contact, and Buildertrend.
Benefits of Using Secure Online Payment Services

Online payment services have helped eCommerce store owners, freelancers, publishers, and individuals across the world receive send and receive payments with a minimal barrier.
Here are some benefits of using them.
1. Build trust with customers
Secure online payment service is visual. It displays confirmation messages, sends receipts, and guides customers during the payment – this encourages customers to always come back.
Also, visual cues like the green button to proceed and the grey button to return make your customers feel like they are in control.
2. Secure and reliable
The advancement in digital technology has made online payment safer than ever. The SSL protocol found on websites encrypts all sensitive information like bank and card details. This helps you to complete transactions without fear of leaking customers’ data.
3. Attracts more customers
Using a secure online payment service adds up to improving customer experience. When customers have a good experience, they refer your products or services to other potential customers.
Another way to attract more customers is the flexibility and accessibility that comes with online payment services.
4. Recurring payment
Some online payment services allow you to set up a recurring payment. This is particularly beneficial to SaaS or subscription-based businesses.
Setting up recurring payments allows you to automatically bill your customers based on what they subscribed for.
5. Easy setup
Most of the secure online payment services recommended in this article today are easy to integrate into your website.
You don’t need to write a single line of code to get them running. Most times, all you do is register and follow the instructions on their official website.
READ ALSO: Cryptocurrency Payment: Pros And Cons
Most Secure Online Payment Services: Frequently Asked Questions
What are the most secure online payment services?
Some of the most secure online payment services include Payoneer, Wise (formerly Transferwise), Amazon Pay, Google Pay, Verifone (2CheckOut), Apple Pay, Stripe, PayPal, Braintree, and WePay. These platforms are trusted globally for fast, secure, and reliable transactions.
Which online payment service is best for freelancers?
Wise, Payoneer and Stripe are highly recommended for freelancers. Payoneer is ideal for receiving payments from international clients and platforms like Amazon and Google, while Stripe allows freelancers to integrate payment gateways for direct client payments.
Is PayPal safer than other online payment services?
PayPal is considered one of the safest and most popular payment services worldwide. It offers purchase protection, fraud prevention, and refunds if transactions go wrong, making it highly reliable for both buyers and sellers.
Can I use Wise (Transferwise) for international payments?
Yes. Wise is specifically designed for international money transfers. It supports over 80 countries and 53 currencies, making it one of the most affordable and efficient ways to send and receive money globally.
How do Amazon Pay and Google Pay differ?
Amazon Pay lets customers use their Amazon account details to pay on eCommerce sites, making it best for merchants in the U.S. Google Pay, on the other hand, is a mobile wallet app that enables peer-to-peer payments and can be integrated into websites and apps worldwide.
READ ALSO: Amazon Scraper API: Best Tools To Extract Data From Amazon At Scale
Is Apple Pay only for Apple device users?
Yes. Apple Pay is exclusive to Apple users. It allows iPhone, iPad, and Mac owners to send, receive, and manage money securely without using physical cards. Businesses can also integrate Apple Pay as a checkout option for Apple customers.
Which online payment service is best for eCommerce websites?
Stripe, Braintree, and WePay are excellent for eCommerce stores. They support multiple payment options, recurring billing, fraud protection, and seamless integration with platforms like Shopify, Magento, and BigCommerce.
Do online payment services support recurring payments?
Yes. Payment gateway services like Stripe, Braintree, and Verifone (2CheckOut) allow businesses to set up recurring billing. This is especially useful for subscription-based services and SaaS businesses.
Are secure online payment services easy to set up?
Most secure payment services are easy to integrate into websites without coding. Platforms like PayPal, Stripe, and Payoneer provide step-by-step instructions for setup, making them accessible even to beginners.
What are the main benefits of using secure online payment services?
The benefits include building customer trust, protecting sensitive data, enabling recurring payments, attracting more customers through convenience, and offering easy setup for both individuals and businesses.
Conclusion
Utilizing the right online payment service will expand customer reach, enable unlimited operating hours, facilitate targeted marketing, and increase the customer base.
We have recommended the 10 most secure online payment services in this post, but Payoneer and Transferwise seem to be our favorites because of their flexibility, affordability, and features, making them standout choices among the best international money transfer platforms today.
INTERESTING POSTS
- Things To Look Out For When Making Payments Online
- Mobile Payment Security Concerns – Four Big Things To Consider
- Are PayPal’s Executives Looking Towards Re-Inventing the Product’s Identity?
- Benefits Of Core Banking Solutions
- 13 Best And Most Secure Web Hosting Services [Tested & Ranked]
- 6 Most Secure Email Service Providers























![Cybersecurity Tips From Squid Game TV Series [MUST READ] Cybersecurity Tips From Squid Game TV Series [MUST READ]](https://secureblitz.com/wp-content/uploads/2021/10/Cybersecurity-Tips-From-Squid-Game-TV-Series-768x402.png)