Read on for the Multilogin Antidetect Browser review.
Facing constant frustration with slow and error-prone manual processes, many users struggle to bypass platform detections, especially when security concerns loom large over profile storage and access.
Add to this the frustration of downtime, sluggish support, and the challenge of navigating security during multi-project team collaborations, and the need for a reliable solution becomes glaringly clear.
Meet Multilogin, an antidetect browser to tackle the above problems. It is a specialized tool designed to help users manage multiple online identities across various platforms. It offers advanced features that enable businesses to operate with greater security and flexibility, particularly when managing browser profiles and online accounts.
Through sophisticated browser fingerprint masking and secure proxy integration, Multilogin allows users to mimic human behavior and avoid detection on platforms with strict anti-fraud measures.
Now, the latest version, Multilogin X, takes the capabilities further. With enhanced features for team collaboration, improved cloud-based profile storage, and advanced automation capabilities, Multilogin X offers a seamless experience for businesses dealing with multiple projects or requiring better collaboration between teams.
Its innovative approach helps businesses bypass platform detections effortlessly, safeguard their online identities, and streamline digital operations.
Table of Contents
Two solutions offered for different problems by the Multilogin X are as follows:
Web Scraping and Automation:
- Single API Calls: Multilogin X supports single API calls, simplifying the process of integrating the tool into your automated workflows. This allows you to automate tasks efficiently and scale operations seamlessly.
- Prompt Launching with Local Profiles: Users can swiftly launch browser profiles with local configurations, reducing setup time and enabling rapid task execution. This flexibility improves efficiency, particularly for projects that involve repetitive scraping tasks.
- ‘Headful' Browsers for Efficient Scraping: Multilogin X allows users to launch ‘headful' browser instances that replicate typical user behavior, making it easier to scrape websites while remaining undetected. These instances offer greater efficiency by mimicking human interactions, bypassing anti-bot measures.
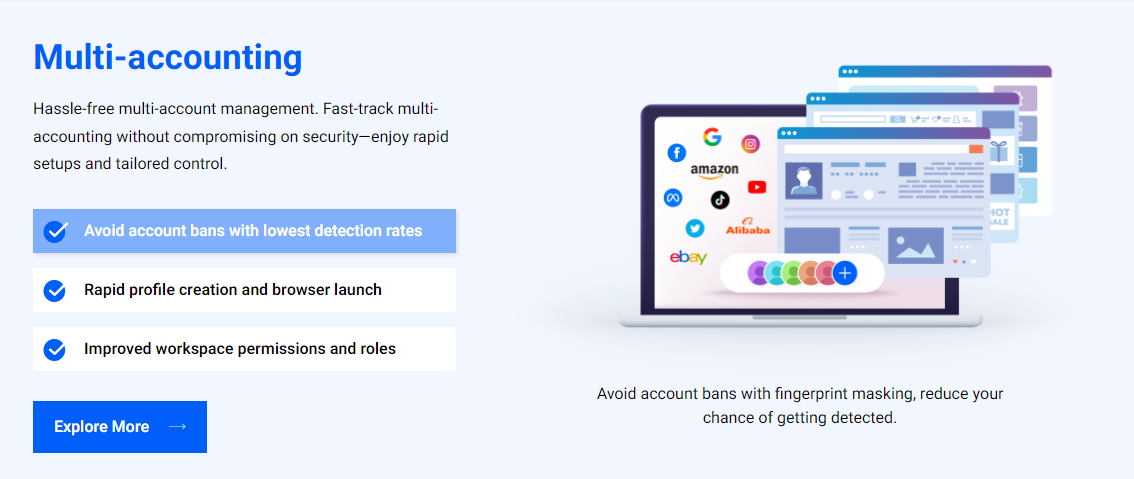
Multi-Accounting:
- Maximize Your Chances for Staying Undetected: Multilogin X leverages advanced fingerprint masking and anti-detection technology to minimize detection risks across multiple accounts. Users can confidently operate on platforms implementing strict anti-fraud measures, ensuring each browser profile appears unique.
- Ready-to-Use, Customizable Fingerprints: The platform provides an extensive range of fingerprints, enabling users to fine-tune profiles for different applications. This helps in creating distinct browser profiles that look genuine and individualized.
- Rapid Account Creation: Multilogin X simplifies setting up new accounts across various platforms, allowing users to quickly create and manage multiple accounts. This feature's efficiency is valuable for businesses that rely on multi-account setups for marketing, sales, or other digital operations.
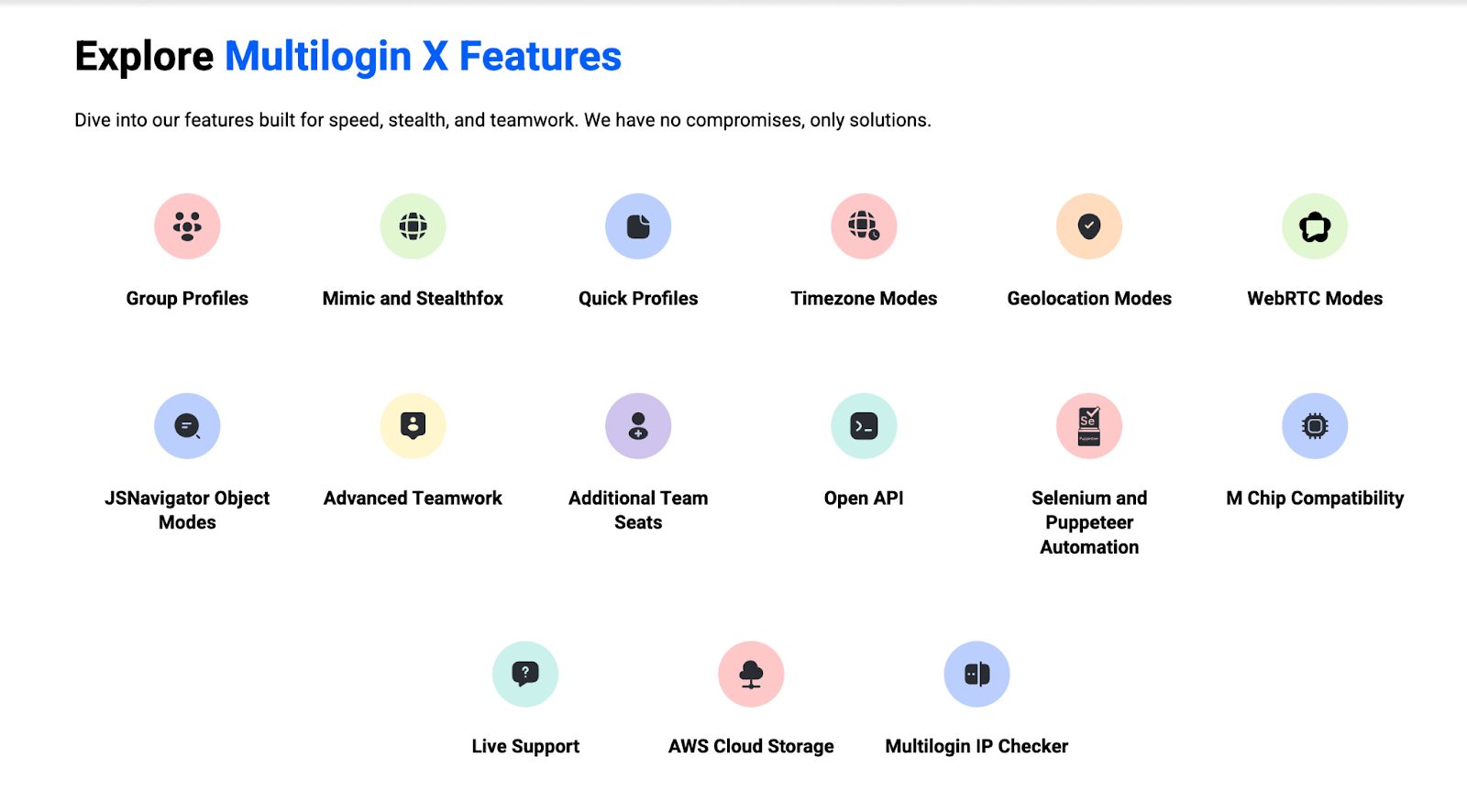
Multilogin X Features and Benefits
Account Bans and Detection, Gone:
- Advanced Anti-Detection Technology: Multilogin employs pioneering anti-detect technology to ensure website browser fingerprints appear unique and consistent. This reduces the likelihood of detection and account bans by simulating realistic browsing patterns and hiding identifiable data points. It's particularly useful for digital marketers, e-commerce sellers, and anyone needing multiple accounts that bypass platform restrictions.
Create Browser Profiles in a Flash:
- Quick Profile Generation: The Quick Profile feature allows users to generate single-use browser profiles within seconds. This feature is designed for temporary tasks where quick setup and tear-down are crucial. Once the task is complete, profiles automatically delete themselves, eliminating manual cleanup and enabling more efficient completion.
Teamwork Makes the Dream Work, Securely:
- Multi-Level Role Management: Multilogin provides comprehensive collaboration features through multi-level role management. Users can securely organize their teams by assigning different roles, from Owner to Launcher, each with distinct access levels. This promotes effective task delegation, protects sensitive data, and prevents redundancy and overlap in operations, making it ideal for large teams managing multiple projects.
Light as a Feather, Fits Like a Glove:
- Lightweight Platform: Designed to be resource-efficient, Multilogin X provides smooth navigation and performance on high-end and older devices. Users can benefit from its powerful features without compromising system performance, making it versatile for various environments.
We Speak Your Language, Literally:
- Comprehensive Multilingual Support: Multilogin's team of experts offers 24/7 support in multiple languages, ensuring that users, regardless of their expertise level, receive assistance tailored to their needs. Whether troubleshooting or seeking optimization advice, the support team is ready to assist with any issue, big or small.
How does Multilogin X work?
Multilogin X works by creating and managing unique browser profiles that mimic real user behavior, providing each profile with distinct fingerprints to evade detection by platform algorithms.
It uses advanced anti-detect technology to make each profile appear as a separate, genuine user, enabling activities like multi-account management, web scraping, and automation.
Users can quickly create profiles with customizable settings for different tasks, while the cloud-based storage ensures profiles are securely saved and accessible across devices.
Collaboration tools allow teams to share profiles efficiently, and automated workflows streamline repetitive tasks, helping businesses scale their digital operations smoothly and securely.
It is based on the three below-mentioned pillars:
- Browser Fingerprint Masking: Generates unique browser fingerprints for each profile, simulating human-like behavior and avoiding detection by anti-bot algorithms.
- Proxy Integration: Assign different proxies to each profile, routing internet traffic through different IP addresses to mask the user's location.
- Profile Encryption: Encrypts all browser data for each profile, ensuring secure storage and transit of cookies, login details, and browsing history and protecting sensitive information from unauthorized access.
How to use Multilogin X?
Step 1: Register an account
- Fill out the registration form and click “Create account“
- Enter the verification code from your email (be sure to check your Social, Promo, and Spam folders)
Step 2: Get a subscription
- Click “View plans”
- Choose a subscription that fits your needs
- Choose a payment method: Multilogin platform accept card*, PayPal, and crypto payments
- Pay the invoice: The platform has this handy guide that will help if you get stuck
- Click “Open Multilogin X” in the top-right corner
Step 3: Connect the agent
- Download the agent for your OS
- On a Mac, make sure your OS is 12 (Monterey) or newer
- Click the downloaded file to open the installer
- On Windows, right-click the file and choose “Run as administrator”
- Follow the on-screen instructions to complete the installation
- Click “Connect agent” and wait while Multilogin downloads all components and establishes the connection (wait time can be longer with slower connection speeds)
Step 4: Create a profile
- Click “New profile” and enter its name in the top field
- Operating system: choose your device's OS for best results
- Browser: Mimic is built on Chrome and Stealthfox – on Firefox
- Storage type: choose cloud storage for seamless multi-device access and synchronization, and local storage for exceptional speed and saving data on your device
- Click “Next” at the bottom and fill in your proxy details, or take advantage of your welcome bonus: 5 GB of free premium residential proxy traffic!
- Click “Create” at the bottom of the screen and then “Launch”
- Wait while Multilogin downloads your browser cores: it only needs to do it once for every core release (wait time can be longer with slower connection speeds)
Bonus step: Elevate your strategy
- Check out API documentation and knowledge base articles to discover how you can automate and scale your business effectively (we support Selenium, Puppeteer, and Playwright)
- Take control of your team's access to browser profiles with four new roles designed to meet your needs (not available in the Solo plan)
- Explore the best tips and tricks for managing multiple accounts
Use Cases of Multilogin X
Let’s explore some of the great across various industries cases offered by Multiulogin X:
Use Cases of Multilogin X In Different Sector
| Sector | Uses Cases of Multilogin X |
| E-commerce |
|
| Affiliate |
|
| Ads |
|
| Agency |
|
| Arbitrage |
|
| Betting |
|
| Ticketing |
|
| Crypto |
|
Improvements in Multilogin X compared to Multilogin
Let’s compare it with the current version of Multilogin. i.e., Multilogin X with Multilogin's earlier version:
Multilogin X vs. Multilogin
| Capabilities | Multilogin X | Multilogin |
API and Automation |
|
|
| Profile Management |
|
|
| Team Collaboration |
|
|
| Workspace and Recovery |
|
|
| Interface |
|
|
Conclusion
In conclusion, Multilogin X is a powerful tool for addressing the critical needs of businesses and individuals who require secure and efficient online identity management.
Its advanced browser fingerprint masking, seamless proxy integration, and robust profile encryption offer unparalleled security and anonymity. It is ideal for various applications, from e-commerce and advertising to affiliate marketing and web scraping.
Multilogin X empowers users to expand their digital operations confidently and efficiently by enabling streamlined automation, team collaboration, and scalable multi-account management.
Whether safeguarding brands, enhancing ad campaigns, or exploring global markets, Multilogin X provides a reliable solution to these challenges.
INTERESTING POSTS










![Lightsail VPN Review: Is Lightsail VPN Safe? [+Best Alternatives] Lightsail VPN Review: Is Lightsail VPN Safe? [+Best Alternatives]](https://secureblitz.com/wp-content/uploads/2022/03/Is-Daily-VPN-Safe-1-768x345.png)