This post will show you 9 ways to secure your mobile devices.
In today’s digital age, our mobile devices have become an extension of ourselves. We rely on them for communication, banking, entertainment, and storing sensitive personal information.

However, with the increasing prevalence of cyber threats, it’s crucial to take proactive measures to secure our mobile devices.
This comprehensive guide will provide you with the essential steps and best practices to ensure the security of your smartphones and tablets.
Table of Contents
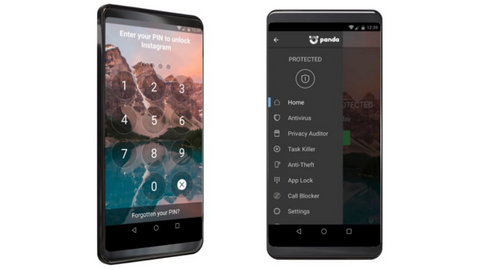
Step 1: Lock Your Device for Maximum Security

1.1 Set Up a Strong Password or PIN
One of the first and most fundamental steps to secure your mobile device is to set up a strong password or PIN. Avoid using easily guessable combinations such as “1234” or “password.”
Instead, use a unique alphanumeric password with a minimum length of eight characters. Consider incorporating a mix of uppercase and lowercase letters, numbers, and special characters.
1.2 Utilize Biometric Authentication
Take advantage of the advanced biometric authentication features available on most modern smartphones and tablets. Enable either fingerprint recognition or facial recognition to add an extra layer of security.
Biometric authentication ensures that only you can unlock your device, making it significantly more difficult for unauthorized individuals to access your sensitive information.
1.3 Enable Auto-Lock and Timeout
To further enhance the security of your mobile device, enable the auto-lock feature. This setting automatically locks your device after a specified period of inactivity, ensuring that even if you forget to lock it manually, your device will be secure.
Additionally, adjust the timeout duration to a shorter interval so that your device locks quickly when not in use.
Step 2: Keep Your Software Up to Date
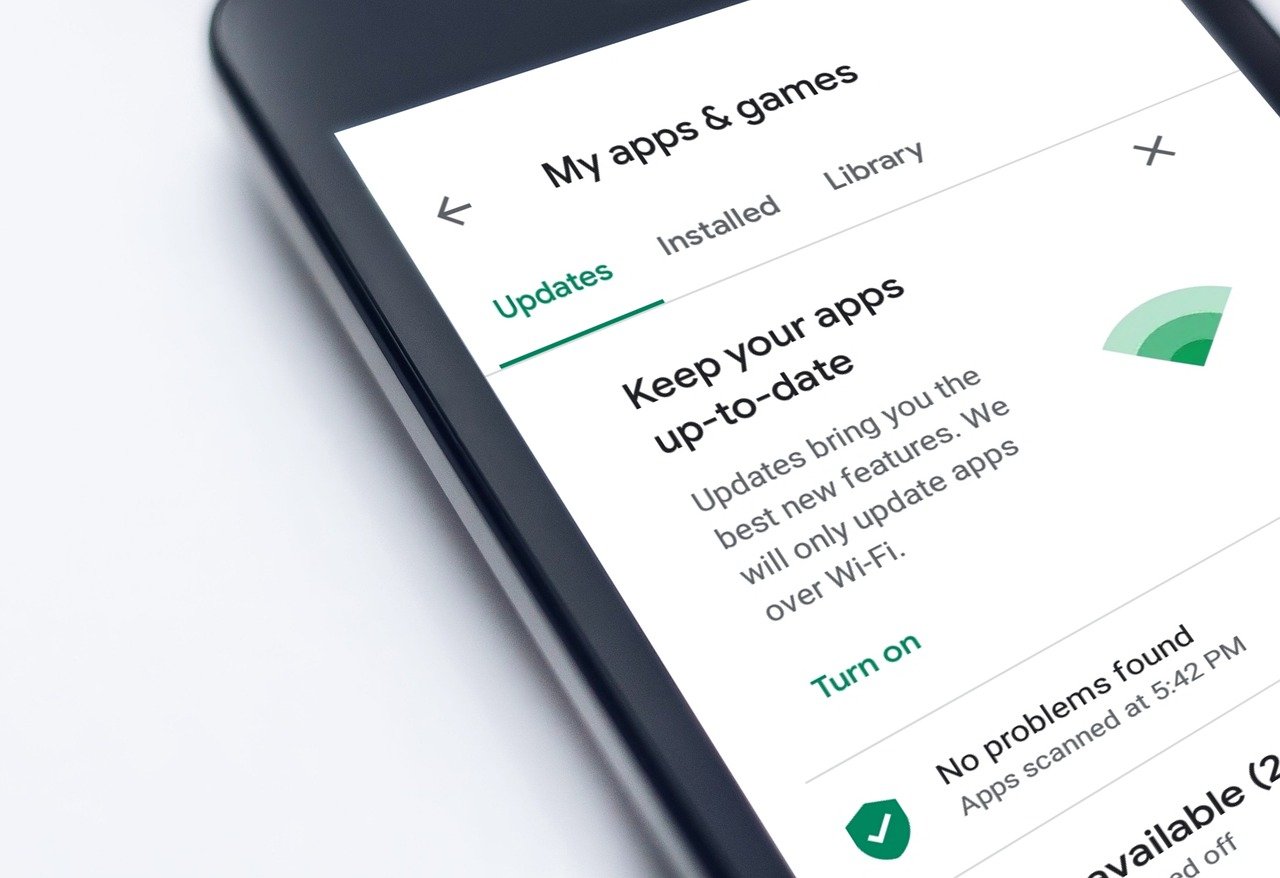
2.1 Update Your Operating System Regularly
Operating system updates often include critical security patches and bug fixes. Keeping your mobile device’s operating system up to date ensures that you have the latest security measures in place.
Enable automatic updates if available, or regularly check for updates manually and install them promptly.
2.2 Update Your Apps
In addition to updating your operating system, it’s essential to keep your apps up to date. Developers frequently release updates that address vulnerabilities and enhance security.
Enable automatic app updates or regularly check for updates in your device’s app store and install them as soon as they become available.
2.3 Remove Unnecessary Apps
Periodically review the apps installed on your mobile device and uninstall any that you no longer use or trust.
Unused apps can pose security risks, as outdated or vulnerable apps may become targets for malicious actors.
By removing unnecessary apps, you reduce the potential attack surface and minimize the risk of compromise.
Step 3: Protect Your Data with Backups
3.1 Regularly Backup Your Device
Backing up your mobile device’s data is crucial in case of loss, theft, or hardware failure. Regularly create backups of your important files, photos, and documents to ensure that you can restore them if needed.
Use cloud-based backup services or connect your device to a computer and transfer the data to a secure location.
3.2 Encrypt Your Backups
When creating backups, ensure that they are encrypted to protect your data from unauthorized access. Encryption converts your data into an unreadable format, making it inaccessible without the decryption key.
Both iOS and Android devices offer built-in encryption options for backups, which you should enable for maximum security.
Step 4: Be Vigilant of App Security

4.1 Download Apps from Trusted Sources Only
When installing apps on your mobile device, only download them from official and trusted sources such as the Google Play Store for Android or the App Store for iOS.
Third-party app stores or unofficial websites can host malicious apps that may compromise the security of your device. Check app reviews and ratings before downloading to ensure their legitimacy.
4.2 Review App Permissions
Before installing an app, carefully review the permissions it requests. Be cautious of apps that ask for excessive permissions that seem unrelated to their functionality.
Granting unnecessary permissions may expose your personal information and compromise your privacy.
If an app’s permissions raise concerns, consider looking for an alternative or contacting the app developer for clarification.
4.3 Remove Unused or Suspicious Apps
Regularly review the apps installed on your mobile device and remove any that you no longer use or suspect to be malicious. Cybercriminals may disguise malware as legitimate apps, so it’s essential to be vigilant.
If you encounter an app that exhibits suspicious behavior or consumes excessive resources, uninstall it immediately to mitigate potential security risks.
Step 5: Protect Your Device on Public Networks

5.1 Avoid Unsecured Wi-Fi Networks
When connecting to public Wi-Fi networks, exercise caution as they may lack proper security measures.
Avoid accessing sensitive information such as online banking or making purchases when connected to unsecured Wi-Fi networks. Instead, use a virtual private network (VPN) to encrypt your internet traffic and ensure secure communication.
5.2 Disable Automatic Wi-Fi and Bluetooth Connections
To minimize the risk of unauthorized access to your device, disable automatic Wi-Fi and Bluetooth connections. Leaving these features enabled increases the likelihood of connecting to untrusted networks or devices without your knowledge.
Manually connect to trusted networks and devices when necessary, and always disable the connections when not in use.
5.3 Utilize Cellular Data for Sensitive Activities
When conducting sensitive activities such as online banking or accessing confidential information, consider using your cellular data instead of public Wi-Fi.
Cellular networks are typically more secure than public Wi-Fi networks, reducing the risk of eavesdropping or interception of your data.
Step 6: Exercise Caution with Emails, Links, and Messages

6.1 Beware of Phishing Attempts
Phishing is a common method used by hackers to deceive users into revealing sensitive information. Be cautious of suspicious emails, links, and messages that prompt you to provide personal information or login credentials.
Avoid clicking on unfamiliar links or downloading attachments from unknown senders. Verify the legitimacy of emails and messages before taking any action.
6.2 Be Wary of Social Engineering Tactics
Cybercriminals often employ social engineering tactics to trick users into divulging confidential information.
Be skeptical of unsolicited requests for personal or financial information, even if they appear to come from reputable sources. Legitimate organizations will never request sensitive information via email or text message.
6.3 Use Antivirus Software for Added Protection
To enhance the security of your mobile device, consider installing reputable antivirus software.
Antivirus apps can detect and remove malicious software, protect against phishing attempts, and provide real-time scanning for potential threats. Regularly update your antivirus software to ensure it remains effective against emerging threats.
Step 7: Secure Your Mobile Device Physically

7.1 Keep Your Device in Sight
When in public spaces, always keep your mobile device within sight to prevent theft. Avoid leaving your device unattended or placing it in easily accessible locations.
By maintaining physical control over your device, you minimize the risk of unauthorized access and potential security breaches.
7.2 Enable Remote Tracking and Wiping
In the event your mobile device is lost or stolen, having remote tracking and wiping capabilities can be invaluable.
Both iOS and Android devices offer built-in features that allow you to locate your device, lock it remotely, and even erase its data.
Enable these features and familiarize yourself with the necessary steps to utilize them effectively.
7.3 Use a Secure Locking Case or Screen Protector
Protect your device from physical damage and unauthorized access by using a secure locking case or a screen protector with a privacy filter.
These accessories provide an additional layer of security by preventing prying eyes from viewing your screen and protecting your device from accidental drops or scratches.
Step 8: Educate Yourself and Practice Safe Habits

8.1 Stay Informed About Mobile Security Best Practices
Stay updated on the latest mobile security best practices and emerging threats. You can check out a smartphone blog like mobiletechify.
Regularly educate yourself about new vulnerabilities, scams, and security measures to ensure you are well-informed and prepared to protect your mobile devices effectively.
8.2 Use Strong and Unique Passwords
Create strong and unique passwords for all your accounts, including your device’s lock screen, email, social media, and online banking.
Avoid using easily guessable passwords and consider utilizing a password manager to securely store and manage your passwords.
8.3 Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password.
Enable two-factor authentication whenever possible to enhance the security of your accounts.
8.4 Be Mindful of App Permissions and Privacy Settings
Review and manage app permissions and privacy settings regularly. Be cautious of apps that request excessive permissions or access to sensitive data.
Adjust your privacy settings to limit the information apps can collect and ensure that your personal data remains protected.
Now, let me show you one of the ways to secure your mobile devices.
Step 9: Seek Professional Assistance

9.1 Consider Using Antivirus Software
In addition to following the best practices on the ways to secure your mobile devices mentioned above, consider using reputable antivirus software to provide an additional layer of protection for your mobile device.
Antivirus software can detect and remove malware, block malicious websites, and safeguard your device against various threats.
9.2 Consult with Security Professionals
If you require expert guidance or assistance in securing your mobile devices, consider consulting with security professionals or seeking the advice of IT specialists.
They can provide personalized recommendations and tailor security measures to meet your specific needs.
Mobile Security Deals
Conclusion
There you go! 9 ways to secure your mobile devices.
Securing your mobile devices is essential in today’s digital landscape. By following the steps and best practices outlined in this comprehensive guide, you can significantly reduce the risk of unauthorized access, data breaches, and other security threats.
Remember to stay vigilant, keep your software up to date, practice safe habits, and seek professional assistance when needed.
With a proactive approach to mobile device security, you can enjoy the benefits of your devices while keeping your personal information safe and secure.
INTERESTING POSTS
- How to Protect Yourself from Online Fraud [6 Surefire Internet Safety Tips]
- How To Stay Secure: 5 Top Tips When Betting Online To Implement And Follow!
- How To Secure Your WhatsApp Group From Hackers
- Why Should Startups Use A VPN? [#4 ANSWERS]
- How To Start An Insurance Business
- Ultimate Digital Privacy Guide: Protect Your Data Today
- Website Speed Optimization Tips for Windows Hosting
About the Author:
Meet Angela Daniel, an esteemed cybersecurity expert and the Associate Editor at SecureBlitz. With a profound understanding of the digital security landscape, Angela is dedicated to sharing her wealth of knowledge with readers. Her insightful articles delve into the intricacies of cybersecurity, offering a beacon of understanding in the ever-evolving realm of online safety.
Angela's expertise is grounded in a passion for staying at the forefront of emerging threats and protective measures. Her commitment to empowering individuals and organizations with the tools and insights to safeguard their digital presence is unwavering.