In this interview, we spoke with Matt Davey, COO of 1Password, to learn more about IT roles in remote working, cybersecurity protocols, and 1Password contribution for both SMBs and large enterprises.
On May 21st, the enterprise password manager (EPM) 1Password released fresh data that explores the under-celebrated role that IT has played in the massive shift to extended remote work (from 1% to 89% of U.S. office workers in just a matter of weeks).
Below is a quick preview of 1Password’s findings as it relates to security protocols, which were collected between April 15-23:
Big brother tactics aren’t needed — workers are following the rules: 63% of IT workers said they believe employees are following security protocols and requirements actually better when working from home.
Who’s more likely to relax the rules during COVID-19? 46% of SMB firms report relaxing some security protocols and requirements, compared to just 19% of large firms.
Here are Matt Davey’s responses to our questions.
Table of Contents
1. Question: What major role has IT played in the revolution of remote working?
Matt Davey: IT has led the charge to remote work, which frankly wouldn’t exist without IT. From replicating in-person conversations with Zoom to enabling rapid written communications with Slack, and adding security protections accessible via the cloud, this wholesale transition to working from home wouldn’t have been possible even just a few years ago without strong IT personnel and technologies.
CHECK OUT: Full 1Password Review – Reliable Password Manager
2. Question: Do you agree that employees take cybersecurity protocols at home seriously and even better than they do in the office? If yes, why is it so?
Matt Davey: I do, and our research very clearly backs it up. In our survey, 63% of IT workers believe employees are following security protocols and requirements more effectively when working from home, and 58% of employees report that they are following home security protocols more diligently than they did while in the office.
We feared people would be more relaxed at home and be more likely to slip up, and we were pleasantly surprised to see that employees are taking on the mantle of security themselves.
3. Question: Given how long your company has been in business – about 14 years – how would you describe the progress of remote working from then till now? Have there been any major changes?
Matt Davey: At 1Password, we’ve had an almost entirely remote workforce for 14 years and have learned a great deal along the way.
Keeping communication open and collaboration going can be one of the biggest challenges of working from home – loneliness can creep in, and teams can begin to feel siloed. The major changes for our teams have been the proliferation of fantastic digital collaboration tools, such as Slack, Basecamp, and Google Meet.
Setting expectations from the start has been crucial. The most important expectations to set are those around working hours, availability, processes, and priorities. Whatever the expectations, we communicate them clearly from the start and make sure that everyone fully understands the rules by which we’re now working.
Maintaining team members’ happiness and work-life balance is just as important as laying the structural groundwork for remote work. Difficulty unplugging is one of the top struggles of remote workers, so it’s crucial to encourage people to take proper breaks and time away from their desks – and actually mean it. There are also several ways workers can help themselves, such as dedicating a space for work, considering how they use devices, dressing for work, adhering to a regular schedule, and getting up and moving.
We’re lucky to have the opportunity to meet, work (and then hang out with) folks from diverse backgrounds from all over the world. Yes, this happens while working together, but often, it’s the informal, unstructured chats that hold the most value to team wellbeing. We host happy hour video calls where colleagues can catch up over a beer, play online sessions of Settlers of Catan, and share endless Animal Crossing screenshots in our #topic-gaming chat on Slack.
When connections form naturally, they’re real and long-lasting. And teams that communicate well will work more effectively together, be happier, and enjoy their jobs. We’ve seen lower staff turnover and more engaged team members, and have found it easier to recruit new staff due to our company culture.
4. Question: Lots of online service providers have recorded an increase in service usage as a result of the COVID-19 pandemic, are the statistics the same at your end?
Matt Davey: Online attacks are already on the rise, and new threats targeting remote teams will emerge. Smart businesses will develop robust processes to stay safe in the remote economy, and these processes will be woven into the fabric of their day-to-day operations.
We’ve provided businesses with a free six-month trial of 1Password to support companies during the pandemic. That has helped us see strong service usage over the last few months.
5. Question: Do you think companies should embrace remote working as normal after the COVID-19 pandemic or it should be reversed? How would you weigh the possibility?
Matt Davey: Ultimately, the successful businesses will be those best prepared for uncertainty – those that recognize that flexibility is a virtue – and now, perhaps, the only viable option. Currently, flexibility means adopting remote work as the new standard. We won’t bother to call it “remote” anymore. It’ll just be what we call “work.”
==>> Get 1Password
Note: This was initially published in May 2020, but has been updated for freshness and accuracy.
RELATED INTERVIEWS
- Most Effective Cybersecurity Strategy For A Small Business [We Asked 45+ Experts]
- Exclusive Interview With SpyCloud’s CEO And Co-Founder Ted Ross
- Exclusive Interview With Paul Lipman, CEO Of BullGuard
- Interview With Michael Bruemmer, Vice President Of Experian Data Breach Resolution Group And Consumer Protection
- 20 Online Security Tips For Remote Workers
- Secure Remote Access VPN: Everything You Need to Know
- 4 Essential Cybersecurity Tips To Implement When Working Remotely










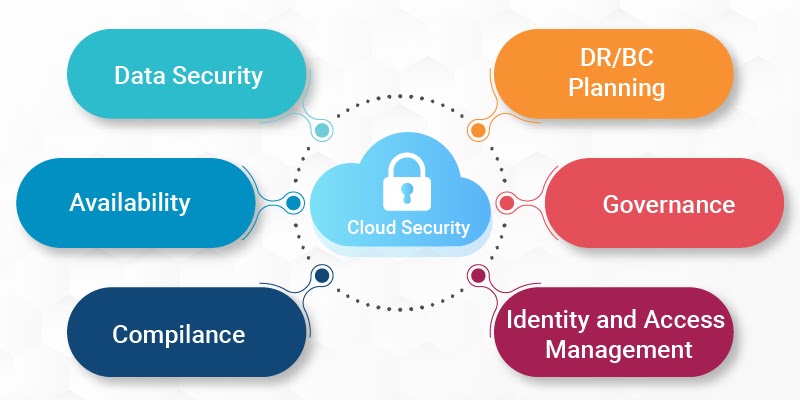 These are the following components that come under cloud security and protection:
These are the following components that come under cloud security and protection: