Here is the ZoogVPN review; read on.
With hundreds of VPN options to choose from, it can be confusing. Which is the best? That’s what everyone wants to know. Reading this means you have ZoogVPN among your options. So, if you want to know if the VPN service is worth your money, you’re on the right page.
We carried out an in-depth ZoogVPN review to evaluate the service’s performance. From the results, both the upsides and downsides of the VPN solution are worth noting.
Read on as we explain everything about the service you should know before subscribing. Let’s kick off by having an overview.
Table of Contents
What Is ZoogVPN?
ZoogVPN is a virtual private network (VPN) service launched in 2013 and headquartered in Greece. As a tool to enhance online privacy and security, ZoogVPN comes with various features to safeguard digital activities.
Notably, the VPN uses AES-256 encryption – a standard adopted by the US military – to protect your online data.
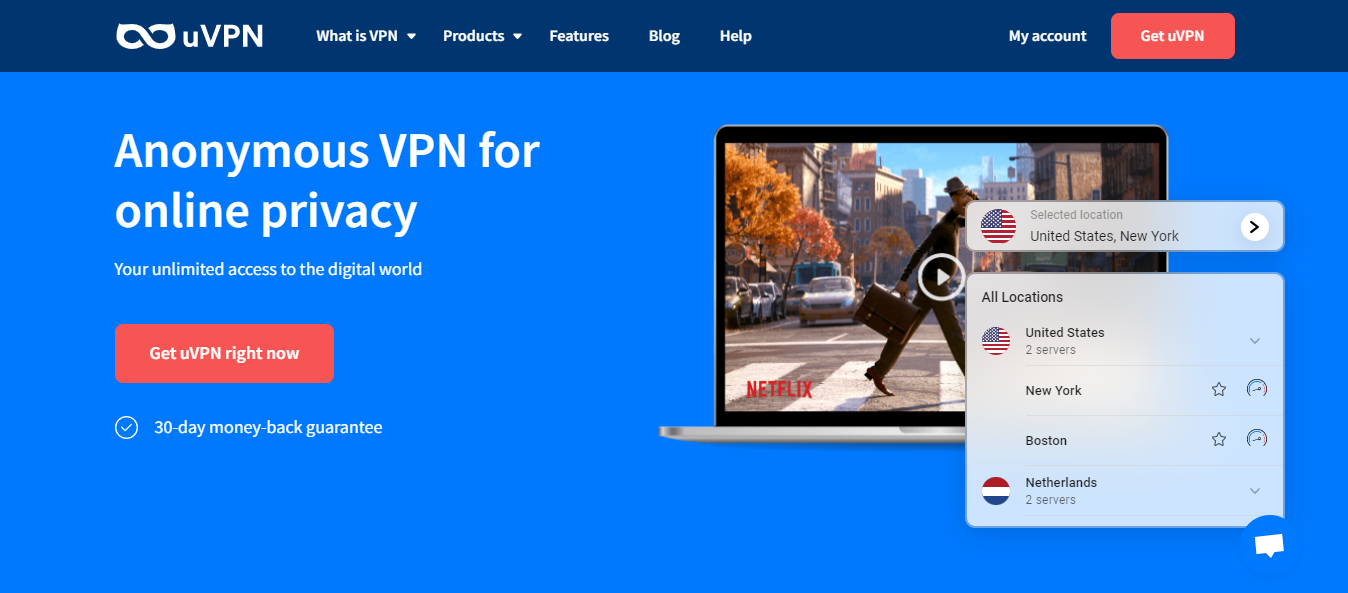
One notable aspect of ZoogVPN is its expansive server network, spanning over 70 countries. This extensive reach enables you to connect with diverse locations. In many ways, it offers enhanced online anonymity and the ability to bypass geo-restrictions, providing unrestricted internet access.
To further prioritize privacy, ZoogVPN adheres to a zero-logs policy. What that means is that they don’t store any records of user activity or browsing history. This commitment enhances the confidentiality of user data. Based on our experience, it aligns with the core principles of a reliable VPN service.
In addition to encryption and server diversity, ZoogVPN introduces extra functionalities. For example, consider split tunneling, which allows you to selectively choose which applications use the VPN.
Then, there’s the kill switch feature that automatically disconnects internet access if the VPN connection drops. These features collectively contribute to ZoogVPN’s offerings in online security and privacy.
Getting Started With ZoogVPN
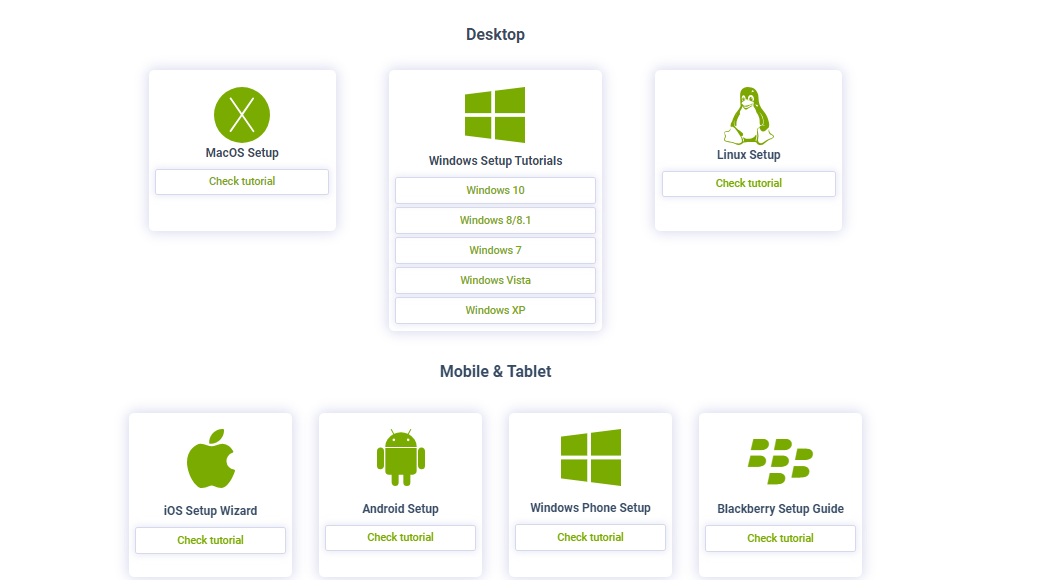
To get started with ZoogVPN, the process is straightforward. You can download the service’s app for your device and register an account.
For instance, you can download the APK from the Google Play Store if you use an Android device. However, here’s the step-by-step procedure if you use the website:
- Visit the official ZoogVPN website and click the “Get ZoogVPN” button at the top right
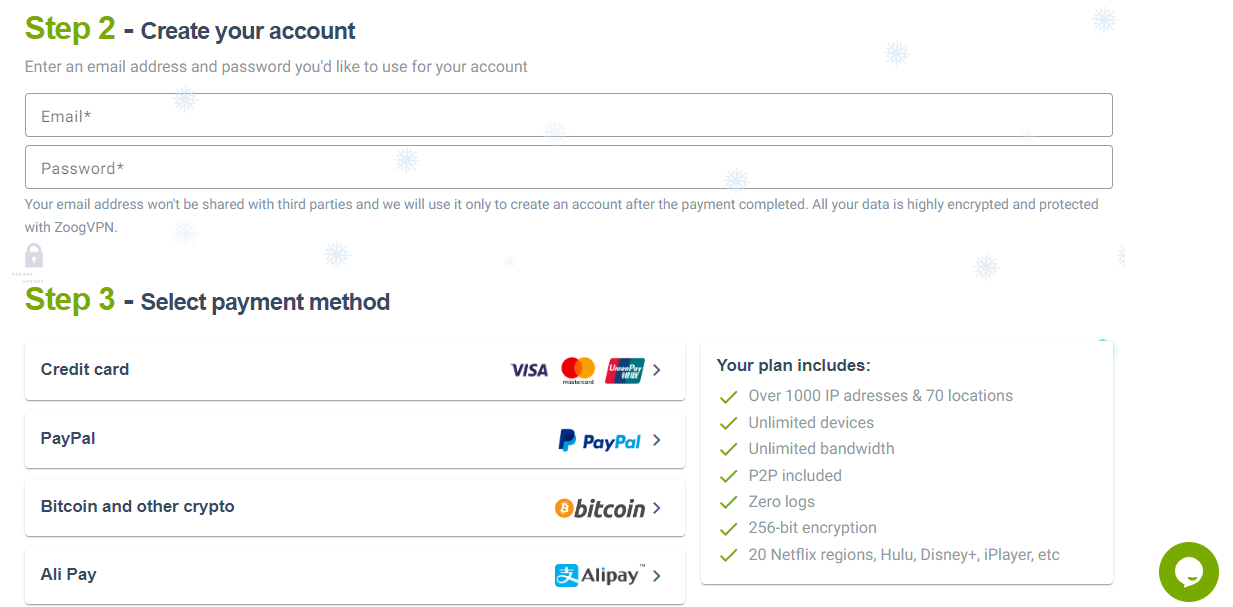
- Choose your preferred payment plan and enter the email and password you want to use
- Select your preferred payment method. You can pay using a credit card, PayPal account, crypto, Ali Pay, Paymentwall, and more.
- Follow the onscreen instructions and complete the transaction.
Please note that to use ZoogVPN for free, you’ll need to download the app directly. You can only complete the on-site registration by paying for a subscription.
Key Features of ZoogVPN
We already hinted at some of ZoogVPN’s key features in the overview. Now, let’s discuss each one in more detail for this ZoogVPN review. Check them out below.
Military-Grade Encryption
ZoogVPN prioritizes user data security by implementing AES-256 encryption. As stated before, it’s a standard trusted by the US military. This robust encryption ensures that transmitted data remains private and secure from any breach.
The choice of such a highly reliable encryption standard reflects ZoogVPN’s commitment to providing users with a secure and confidential online experience.
Notably, you’ll appreciate the encryption when working with sensitive information or using unsecured networks.
No-Logs Policy
One of the primary proofs of ZoogVPN’s commitment to user privacy is its stringent no-logs policy. According to this policy, the service does not store any records or logs of your online activities and browsing history.
It’s pretty standard in the VPN industry, as it’s the basis of privacy. Based on our ratings, implementing a no-logs policy remains critical for those seeking a VPN with a robust data retention strategy.
Kill Switch Feature
ZoogVPN enhances your security by integrating a kill switch feature into its service. Simply put, the feature ensures that in the event of a VPN connection drop, the service automatically ends the internet connection.
By doing so, the kill switch prevents any accidental data exposure whenever the VPN is unstable.
This feature is particularly valuable in maintaining a secure online environment. The last thing you want is data leakage when navigating sensitive tasks or information that requires continuous protection.
IP Leak Protection
According to our ZoogVPN review, preserving user anonymity is a paramount concern for the service. The IP leak protection plays a vital role in achieving this goal. This feature is designed to prevent any accidental disclosure of your actual IP address.
In other words, ZoogVPN actively blocks potential leaks. So, you can confidently browse the internet without risking the exposure of your real location or other critical private details.
ZoogShadowing
Here’s one of ZoogVPN’s most exclusive features. Tailored for users facing online restrictions in certain regions, ZoogShadowing introduces an additional layer of obfuscation to VPN traffic.
This feature makes it more challenging for network monitoring systems to detect and block VPN connections.
Notably, it’ll be helpful in countries with heavy online restrictions like China, Turkey, Iran, the UAE, and Qatar.
From our analysis while crafting this ZoogVPN review, it appears that the feature doesn’t provide absolute invisibility. However, for the most part, ZoogShadowing is a valuable tool for navigating the internet with increased privacy and bypassing censorship measures.
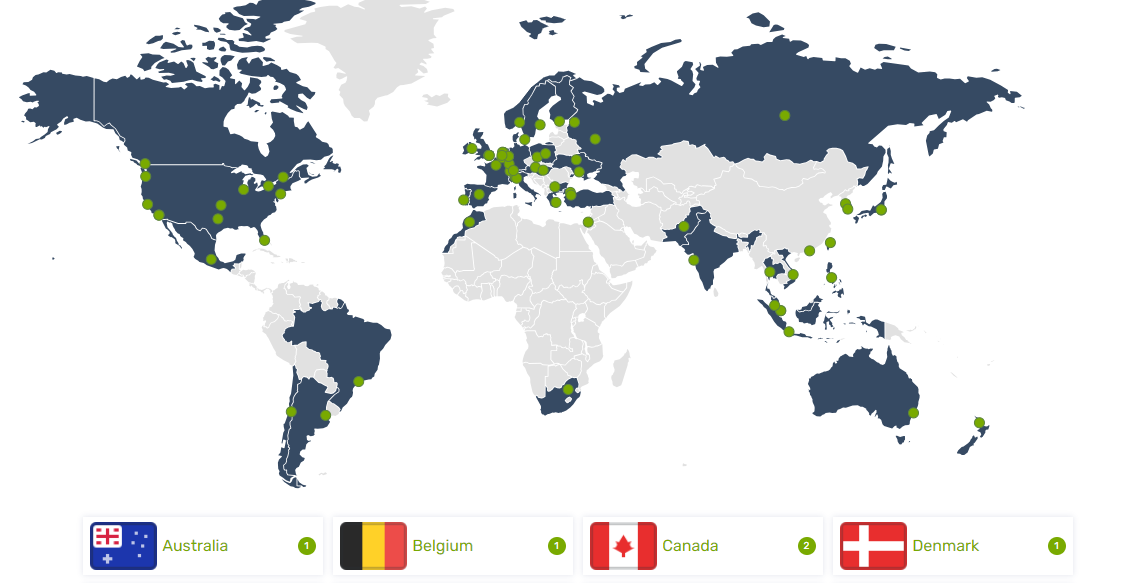
Global Server Network
ZoogVPN boasts a comprehensive global server network spanning over 70 countries and providing access to more than 1,000 IP addresses. This expansive coverage offers you the flexibility to connect to servers worldwide. Additionally, it allows you to bypass geo-restrictions on content.
In addition to the regular servers, ZoogVPN offers dedicated bare-metal VPN servers in key locations. These include the US, UK, Australia, India, Hong Kong, and France at the moment of writing this ZoogVPN review.
With thousands of IPs in 37+ countries, you can choose from a diverse range of servers to optimize your online experience. All the same, the service helps maintain a secure, anonymous connection.
Streaming-Optimized Servers
Recognizing the importance of seamless streaming, ZoogVPN offers specific servers optimized for streaming content. These servers are specifically designed to enhance the performance of popular streaming platforms, including Netflix, Hulu, and BBC iPlayer.
Using these streaming-optimized servers, you enjoy unrestricted access to region-locked content, as we tested for this ZoogVPN review.
To give a verdict, we consider it a convenient solution if you’re seeking an enhanced streaming experience with added privacy and security.
Torrenting-Friendly
Do you download and work with torrents? If yes, you can count on ZoogVPN. It caters to users engaged in secure file-sharing activities by providing servers that are friendly to torrenting. This means that if you engage in torrenting, you can do so on the specialized servers without compromising their privacy or security.
It supports full P2P without any risk of DMCA notices or abuse. Such a tailored approach acknowledges the diverse online activities of users.
However, you shouldn’t abuse the service by engaging in illegal torrents. It’s exclusively for users involved in legal and secure torrenting for a safe and efficient file-sharing experience.
Split Tunneling
ZoogVPN provides the flexibility and control to optimize bandwidth usage with the split tunneling feature. With split tunneling, you can specify which applications use the VPN for secure connections and which can access the internet directly.
In our view, it’s a level of control that ensures efficient bandwidth utilization. That’s because it allows you to tailor your VPN usage to your needs and preferences.
User-Friendly Apps
To ensure accessibility across various devices and operating systems, ZoogVPN offers user-friendly applications.
These apps are compatible with Windows, macOS, Android, iOS, and Linux operating systems. Additionally, it supports a diverse range of platforms, including Fire TV, Android TV, BlackBerry, Windows Phone, Kindle Fire, Chromebook, and routers.
This broad compatibility extends ZoogVPN’s reach. So, irrespective of your device type and preferences, you can install the service and enjoy seamless and safe private browsing.
Simultaneous Connections
ZoogVPN understands the modern user’s need for connectivity across multiple devices. Depending on your subscription plan, ZoogVPN allows for up to 10 simultaneous connections.
Thanks to this feature, you can secure multiple devices simultaneously. It’s accommodating if your digital life includes multiple devices.
Therefore, it doesn’t matter whether you have a laptop, smartphone, tablet, or any other supported device. ZoogVPN provides a versatile solution for protecting your online presence across multiple platforms.
VPN Extension for Chrome
You can enjoy a seamless VPN experience within your Google Chrome browser thanks to the ZoogVPN extension. Designed for simplicity and efficiency, this extension ensures easy access to a secure, unrestricted online environment.
All it takes to get started is just two clicks. By integrating seamlessly into Chrome, ZoogVPN’s extension simplifies the process of unblocking websites, delivering uninterrupted browsing.
This minimalist approach allows you to enjoy the benefits of a VPN without needing to install any software on your laptop or computer.
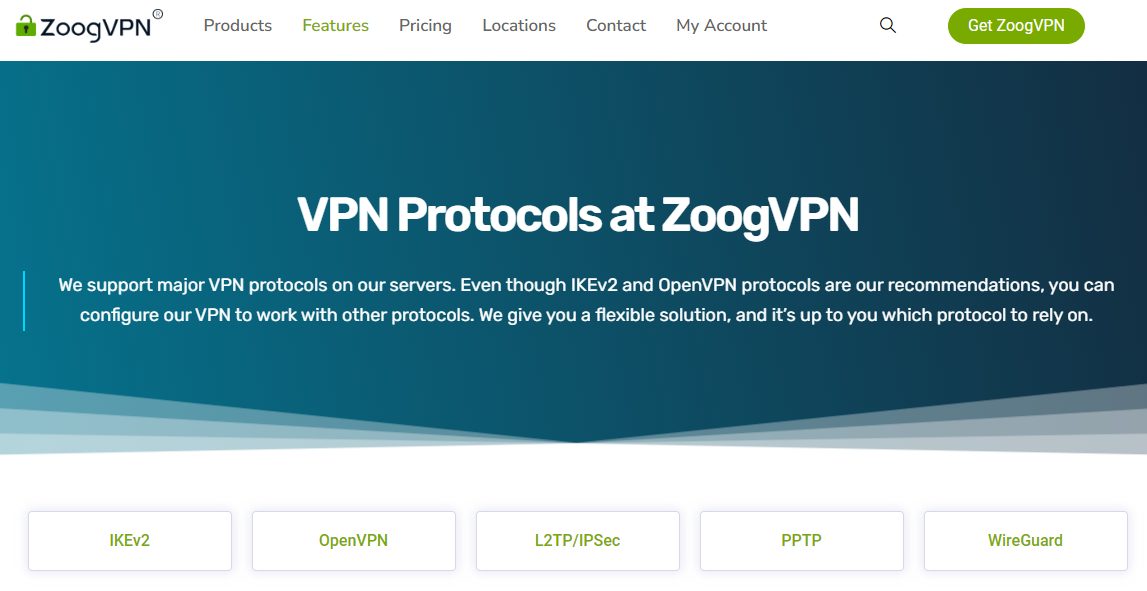
ZoogVPN Protocols
When talking about VPNs, you can’t skip protocols. Some solutions will have one, two, or three supported protocols. However, ZoogVPN switches things up by featuring an impressive five. Let’s discuss each and what to expect as you use the service.
- IKEv2: IKEv2, or Internet Key Exchange version 2, stands out for its robust security features and ability to swiftly reconnect during network changes. This makes it an excellent choice for mobile users, as it seamlessly adapts to switching between Wi-Fi and mobile networks. If you prioritize security and adaptability on mobile devices, IKEv2 could be the preferred protocol for you.
- OpenVPN: Known for its open-source nature and robust security measures, OpenVPN is a versatile protocol that ZoogVPN supports. It’s often favoured for its balance between security and speed. We recommend OpenVPN as a suitable choice if you require a comprehensive VPN experience across multiple devices.
- L2TP/IPSec: Layer 2 Tunneling Protocol (L2TP) coupled with Internet Protocol Security (IPSec) provides a reliable and widely supported option for ZoogVPN users. L2TP/IPSec is particularly suitable for users seeking a balance of security and compatibility across various platforms.
- PPTP: Point-to-Point Tunneling Protocol (PPTP) is an older, less secure option. While it offers faster speeds, it lacks the robust security features found in other protocols. ZoogVPN supports PPTP, but it’s generally recommended to opt for more secure protocols unless speed is your utmost priority.
- WireGuard: ZoogVPN also embraces the modern WireGuard protocol, known for its efficiency and simplicity. If you seek a protocol that balances high-speed performance with robust security, WireGuard could be a solid choice.
Generally, note that the best protocol for you depends on your specific needs. If security is paramount, consider IKEv2 or OpenVPN.
L2TP/IPSec may be the go-to choice for compatibility, while WireGuard offers a contemporary alternative that balances speed and security. Always consider the task when selecting a protocol for your ZoogVPN connection.
ZoogVPN Customer Service
If you’re a ZoogVPN user, you can contact the customer service team at any time. They’re available via multiple channels, including live chat, email, and phone. You can find these details on the Contact page of the website.
To use the live chat, simply click the icon at the bottom right section of the site. You don’t have to provide your email or other details. Just type in your message and start chatting.
On the Contact page, you’ll find the official customer service email address: support@zoogvpn.com. You either send your message directly to the address or use the contact form on the same page. Meanwhile, for the phone, the contact number is +306982989576.
Now, for this ZoogVPN review, I’d like to discuss the pricing plans offered by ZoogVPN.
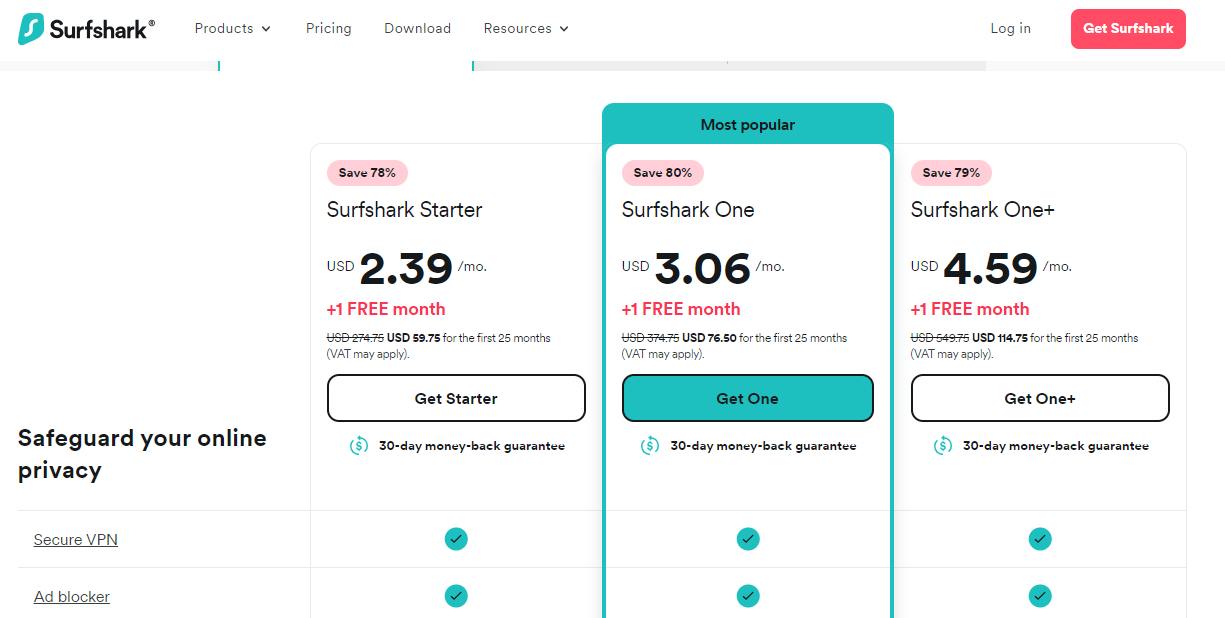
ZoogVPN Pricing Plans
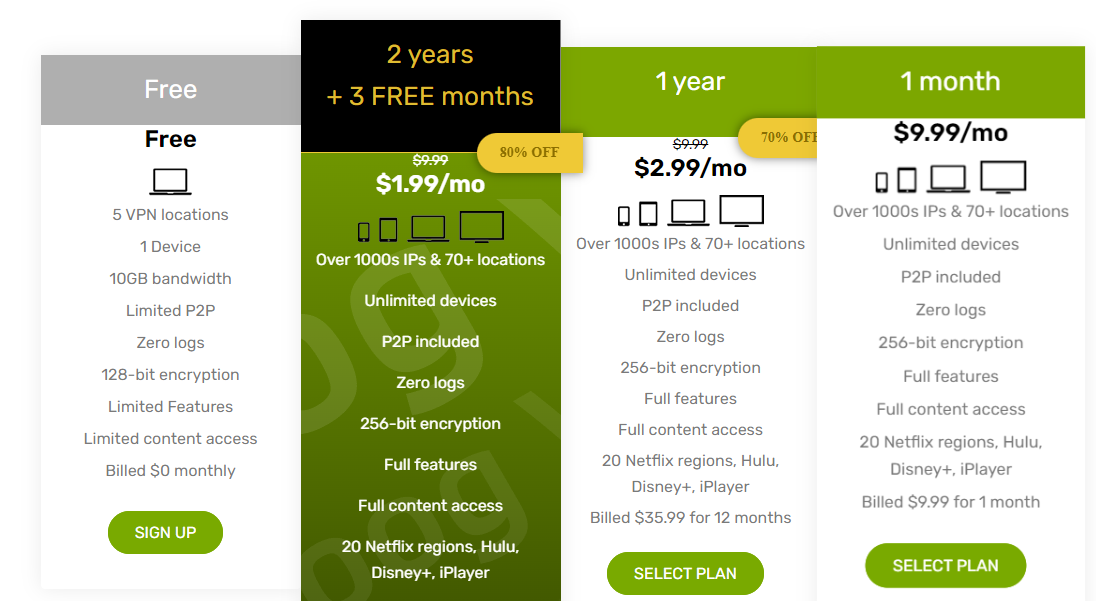
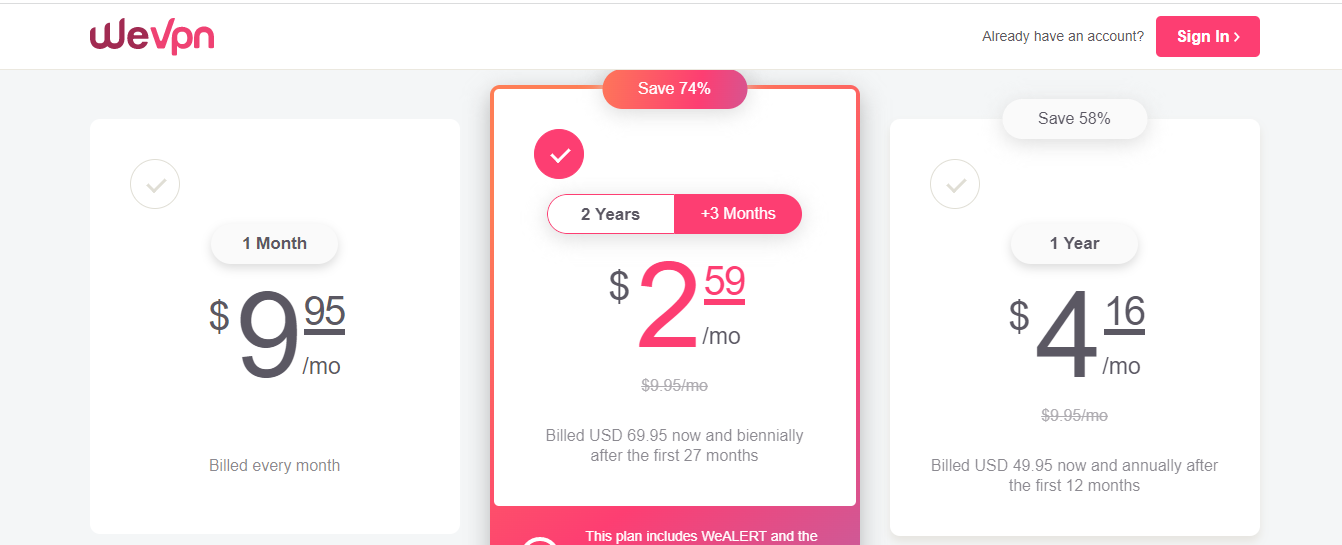
How much does it cost to use ZoogVPN? You can begin using the tool at no cost. There’s a free plan to get you started, but it comes with limited features. For premium, there’s only one plan, but you can pay monthly, annually, or biannually. Here are the prices:
- Monthly Plan: $9.99 per month
- Yearly Plan: $2.99 per month (Billed at $35.99 for 12 months)
- Biannual Plan: $1.99 per month (Billed at $47.76 for two years plus three extra months)
Please note that ZoogVPN offers a 7-day money-back guarantee for its paid plans. So, after subscribing, you can still get a refund if the VPN service doesn’t meet your expectations within the first week.
ZoogVPN Free Version
While paying for a premium plan means you get an advanced VPN service, the ZoogVPN free version can still prove reliable in different aspects. It features notable safeguards designed to protect your online activities without requiring a financial commitment. Let’s look at some of the key features to expect:
- No Credit Card Required: ZoogVPN’s free version does not demand credit card information during sign-up. As a result, you don’t have to worry about unexpected charges.
- No Ads: You won’t encounter disruptive advertisements when you use the ZoogVPN free service. With this, the solution ensures a clean and uninterrupted online experience.
- No Logs: ZoogVPN maintains a no-logs policy, even for its free users. So, although you’re not paying any money, your online activities are still not tracked or stored.
- Lifetime Free VPN Access: Unlike some limited-time trials, ZoogVPN’s free version is available for a lifetime. It’s not one you use for a week or a month. Therefore, you can benefit from VPN services without an expiration date.
- Dedicated Servers: The free version provides access to five dedicated servers. While the server locations are limited to the UK, the US, and the Netherlands, these choices still have some strategic benefits.
Should You Use the ZoogVPN Free Servers?
Features aside, ZoogVPN’s free servers introduce some unskippable advantages. First, you get five servers in diverse locations, which means geographic diversity.
You can explore region-specific content by switching your IP to the UK, US, and Netherlands servers. Without a doubt, that can enhance your online experience.
Secondly, the free VPN servers still come with stanch security. Thus, you can benefit from a more secure browsing experience with ZoogVPN’s dedicated servers. At zero cost, you get to avoid potential security risks associated with using shared or unsafe networks.
We can also commend the bandwidth allocation. Many free VPNs offer 1, 2, or 5 GB of data per month. However, with ZoogVPN’s free service, you enjoy 10GB of monthly bandwidth. That should work for online activities such as web browsing, emails, or light streaming.
Whether you’re interested in secure browsing or testing the waters with a VPN, ZoogVPN’s free version provides some truly valuable features. However, remember that for advanced capabilities and unlimited access, ZoogVPN’s premium subscription is the best option.
Is ZoogVPN Worth it?
All the many reliable features make ZoogVPN a relatively rich virtual private service. However, at the end of the day, it all boils down to the price. It’s essential to weigh the features against the cost to know if the VPN is worth it. Let’s discuss.
First, consider the free plan. It gives you an introductory taste of security, albeit with limitations. The 10GB and 5 VPN locations you get are enough for casual browsing but not satisfying for streaming or torrenting, among others. Therefore, if you require advanced features, you must pay for a subscription.
Switching to the premium plan provides a robust option for streaming and torrenting. You get dedicated servers and a more comprehensive network for accessing global content and secure file-sharing.
Furthermore, the Premium plan caters to those who demand the absolute best. Blazing speeds, the largest server network, and unlimited simultaneous connections make it the ultimate. Now, without a doubt, this plan is powerful enough for diverse digital needs.
For the Premium plan, you’ll pay $9.99 per month if you want to pay monthly. Based on our experience, it’s neither the cheapest nor the most expensive VPN monthly price. It’s just moderate.
However, things get interesting when you consider the annual and biannual plans. Paying for one year gets you 70% off, while paying for two years comes with an even more substantial 80% off. With such a high discount and considering the rich features, the conclusion is that subscribing to ZoogVPN is a worthwhile investment. Not to mention, the 2-year plan comes with three free months.
ZoogVPN Review: Frequently Asked Questions
Is ZoogVPN free?
ZoogVPN does offer a free plan with limited features, including 2GB of data, one server location, and one simultaneous connection. However, most users prefer the premium plans for their unlimited data, faster speeds, access to all server locations, and additional features, such as streaming and torrenting support.
Is ZoogVPN safe to use?
Yes, the VPN is safe. ZoogVPN employs robust security measures, including military-grade encryption and a no-logs policy, making it a generally secure option. However, any online service has potential risks. Therefore, you should also exercise caution and maintain good online hygiene on your part.
How do I set up ZoogVPN?
Setting up ZoogVPN is relatively straightforward. You can find detailed instructions on their website for your specific device and operating system. Generally, it involves downloading the app, creating an account, choosing a subscription plan, and connecting to a server.
What are the ZoogVPN servers?
ZoogVPN boasts a network of servers in over 60 countries, offering options for various locations and needs. You can choose servers for enhanced privacy, bypassing geo-restrictions, streaming specific platforms, or torrenting safely.
How do I download the ZoogVPN APK?
You can download the ZoogVPN APK directly from their website or from alternative app stores, such as the Google Play Store and APKPure. Ensure you download the latest version from a trusted source to avoid security risks.
Is ZoogVPN Legit?
Yes, ZoogVPN is a legitimate company that offers a virtual private network (VPN) service. They have a website, customer support, and a functioning product.
Is ZoogVPN Reliable?
ZoogVPN’s reliability is a mixed bag. Here’s what you might experience:
- Security: ZoogVPN utilizes industry-standard encryption (AES-256), providing essential security features such as a kill switch. However, some reviewers have reported issues with IP leaks.
- Speed: Connection speeds can be inconsistent and frustrating for activities such as streaming or downloading large files.
- Server Network: ZoogVPN offers a decent number of servers in various locations, but it’s not the most extensive compared to some competitors.
- Customer Support: Reviews on customer support responsiveness are mixed.
READ ALSO: How to Use a VPN to Protect Your Online Privacy
Wrapping Up The ZoogVPN Review
To conclude our ZoogVPN review, we recommend that the solution be considered one of the best VPN services. We’ve highlighted the long list of helpful features, including global servers, a no-logs policy, wide compatibility, split tunneling, Zoogshadowning, and many others.
These are the capabilities you expect from a reliable virtual private network. On the pricing side, the yearly and biannual plans offer significant discounts, up to 80%. What more? You can sign up and start using ZoogVPN now for $0 with the free plan.
Leave a comment below regarding this ZoogVPN review.
INTERESTING POSTS