Learn why NAKIVO is the best virtual machine (VM) backup software for modern IT in this post.
Virtual machines have become the backbone of modern IT, powering everything from small business systems to enterprise-scale data centers. As infrastructures expand and threats evolve, even a single instance of data loss can result in costly downtime, regulatory penalties or lasting reputational damage. Reliable backup is no longer optional; it’s critical for business continuity and data protection.
Yet, not every solution can deliver the needed speed, efficiency and multiplatform support. To minimize risks and ensure fast, dependable recovery, choosing the best virtual machine backup software is essential. Read this post to discover why NAKIVO is the leading VM backup solution.
Table of Contents
Modern IT Backup Challenges
IT specialists and technical departments can encounter challenges when configuring virtual machine backup. General requirements include application-aware and incremental backups for running VMs to ensure data consistency. Inconsistent data cannot be recovered.
Legacy backup methods that are used for physical servers are not effective for backing up virtual machines. Physical machine backup solutions install an agent on the physical machine to transfer data to the repository. In the case of virtual machines, this legacy method is inefficient and consumes more resources. Instead of using backups at the guest operating system level, it is better to use a host-level, image-based backup.
There are multiple popular virtualization platforms and each of them uses its own virtual machine formats and APIs to interact with the hypervisor and virtual machines. It is necessary to use a virtual machine backup solution that supports different platforms, including VMware vSphere, Hyper-V, Proxmox VE and Nutanix on a host level using their native APIs. There is a demand for a unified VM backup solution across all major hypervisors.
NAKIVO’s Superior Multi-Platform Features
NAKIVO Backup & Replication supports the most popular virtualization platforms. The solution uses vSphere APIs for data protection and a native mechanism for agentless VMware VM backup. This allows users to benefit from the advanced functionalities with application-aware backup (using VM queiscing and VSS) and incremental backup (using VMware Changed Block Tracking). Backing up VMs in a cluster is supported without additional configurations.
The NAKIVO solution also provides comprehensive support for Hyper-V, including standalone hosts and clusters. There is no need to identify a host in a cluster where a protected VM is running since it is performed automatically once the VM is added to the backup job. Using native Hyper-V APIs for agentless backup allows customers to back up virtual machines effectively.
Proxmox VE is on the rise as an open-source virtualization platform and the NAKIVO solution already supports agentless Proxmox VM backup. NAKIVO Backup & Replication includes enterprise-grade features while remaining cost-effective.
Nutanix is a hyper-converged virtualization platform that is also supported by NAKIVO Backup & Replication. Seamless backup and recovery ensure reliable data protection for Nutanix virtual machines.
The unified virtual machine disaster recovery functionality allows administrators to perform physical-to-virtual and virtual-to-virtual recoveries, restoring machines from one hypervisor to another.
Performance and Cost Advantages
Speed, cost-effectiveness and efficiency make NAKIVO Backup & Replication the preferred virtual machine backup solution for organizations working in one or multiple virtual environments. The perpetual and subscription licensing models and the multiple editions are suitable for all organizations. In addition, NAKIVO offers a fully featured free trial that allows users to test the solution in their environment.
Real-World Success and Implementation
PT Pertani (Persero) is an agricultural company that uses the NAKIVO solution to back up physical servers, VMware VMs and Hyper-V VMs. Previously, the company used two solutions to back up different platforms, which complicated administration. After switching to NAKIVO Backup & Replication, PT Pertani saved administration time, improved the backup speed and obtained an effective solution at an affordable price.
Another example is GCS International, a fintech company that wanted to back up virtual machines in VMware vSphere and Nutanix AHV and physical servers located on two sites in different regions. Backing up virtual machines and physical servers with NAKIVO is fast and convenient.
Getting Started: VM Backup with NAKIVO
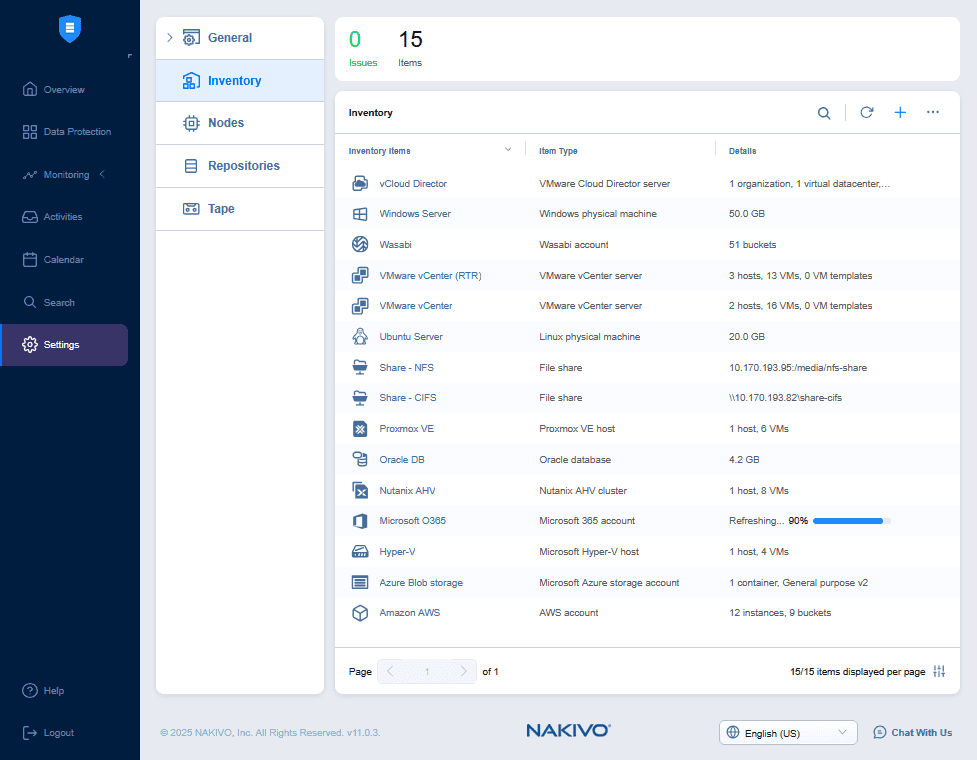
To start backing up virtual machines in VMware vSphere, Microsoft Hyper-V, Proxmox VE and Nutanix, you have to add each platform to the inventory.
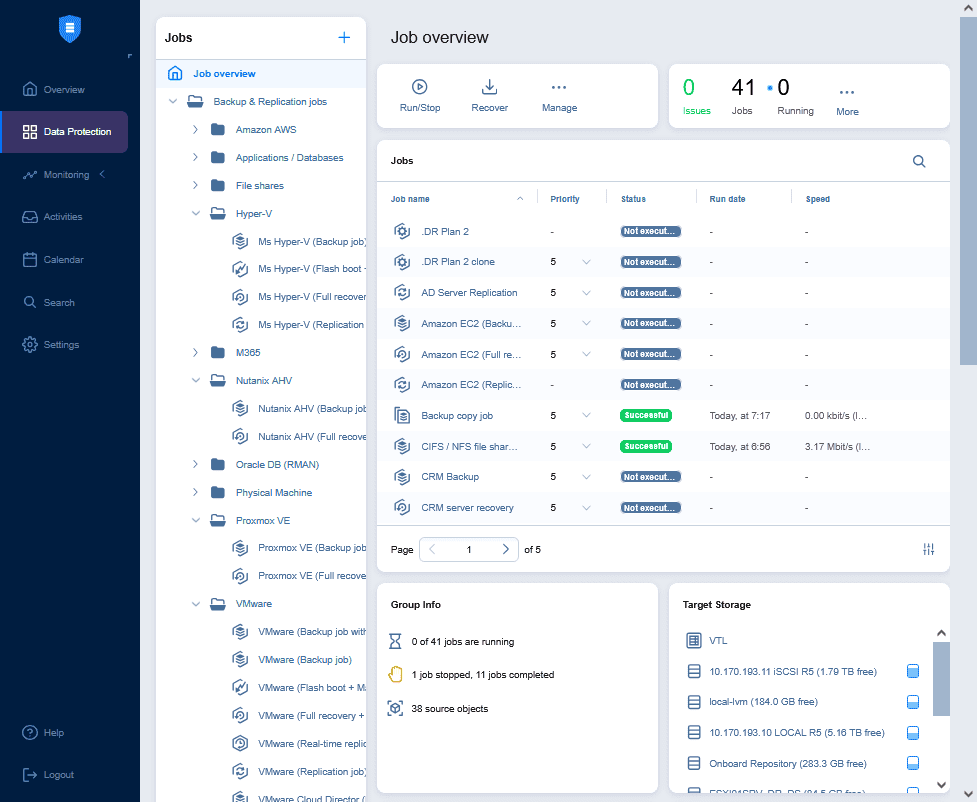
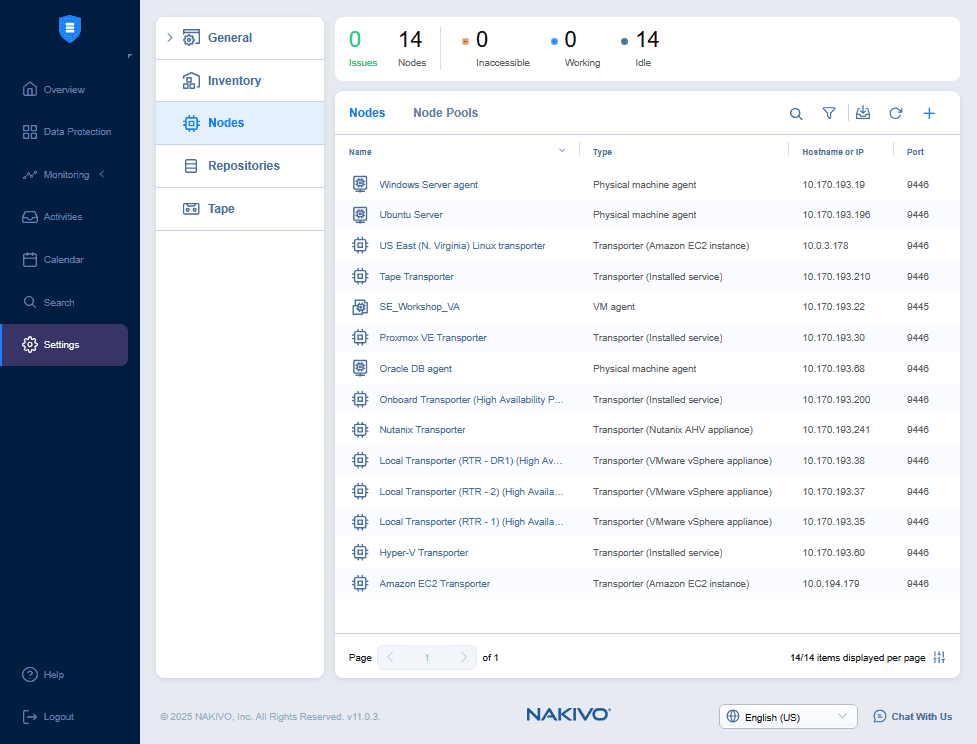
You can create multiple backup jobs for virtual machines and other supported items and configure a schedule to run them automatically. Backup jobs are displayed in the Data Protection section.
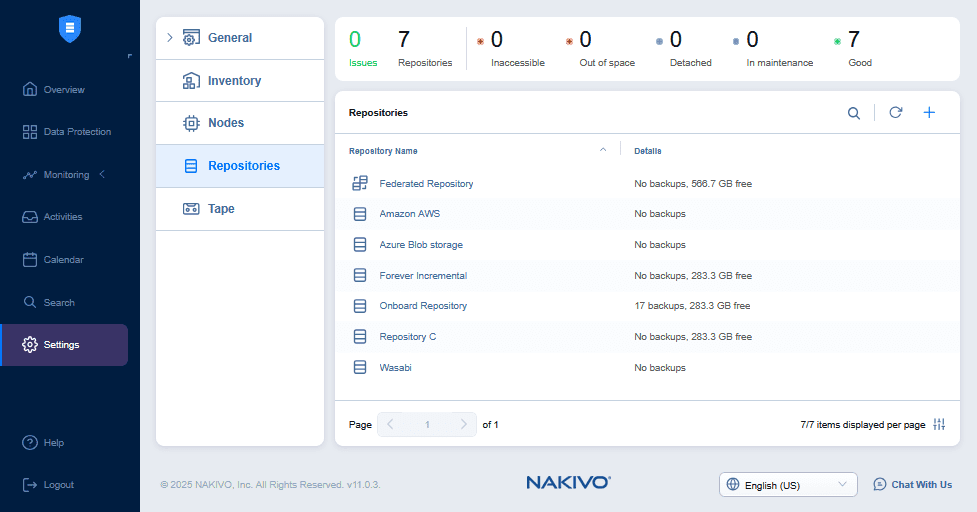
You can create multiple backup repositories in different locations: Onsite, offsite and in the cloud. Saving backups and backup copies to multiple backup repositories is a reliable backup strategy. Backup repository settings are located in Settings > Repositories.
For better scalability, backup speed and security, you can deploy additional NAKIVO Transporters. You can configure Transporters in Settings > Nodes.
NAKIVO Backup & Replication includes a wide range of data protection features, including:
- Backup various platforms: Virtual machines (VMware vSphere, Microsoft Hyper-V, Proxmox VE, Nutanix AHV), physical machines (Windows and Linux servers and workstations), Amazon EC2 instances, Microsoft 365 and Oracle databases via RMAN.
- Backup to multiple locations: Backup repositories on local machines, SMB/NFS shares, tape, private and public clouds like (Amazon S3, Azure Blob, Backblaze B2, Wasabi), and S3-compatible cloud storage.
- Incremental backup: Copy only the changed blocks of data to save backup time and storage space. You can use native or proprietary change tracking technologies.
- Immutable backup: Ensure ransomware resilience with backup immutability. Once data is written to a backup repository, it cannot be deleted or altered during the specified period.
- Backup encryption: Apply powerful encryption to data at the source, in transit when transferring over the network or at rest in the repository.
- Application-aware backup: Even if a source machine is running, the NAKIVO solution can back it up without any data loss. As a result, backups are consistent and data can be recovered successfully.
- Cross-platform recovery: With the backup export feature, you can quickly recover physical machines to virtual machines and recover virtual machines to another virtualization platform.
- VM disaster recovery: The Site Recovery feature allows you to create complex VM recovery workflows and orchestrate the recovery process. The disaster recovery testing functionality helps ensure that recovery is possible within the RTO framework. Virtual server disaster recovery becomes faster and easier.
Download the 15-Day Free Trial of NAKIVO Backup & Replication and try this comprehensive data protection solution within your environment.
Conclusion
NAKIVO has proven itself as a unified, high-performance virtual machine backup software trusted across reputable environments like VMware, Hyper-V, Proxmox and Nutanix.
Its speed, reliability and cost-effectiveness make it the ideal choice for businesses seeking robust data protection and seamless disaster recovery.
By consolidating virtualization backup into one powerful solution, organizations can reduce complexity, minimize risks and maximize ROI.
INTERESTING POSTS

































![How to Play DVD on Windows 10: 4 Methods [Free Included] How to Play DVD on Windows 10: 4 Methods [Free Included]](https://secureblitz.com/wp-content/uploads/2025/09/How-to-Play-DVD-on-Windows-10-4-Methods-Free-Included-768x475.jpg)