Here is the Blooket review. Read on.
As a teacher, I am always seeking new and innovative ways to engage my students and make learning more enjoyable. That’s why I was excited to discover Blooket, a learning platform that is built in a gamified way.
In this comprehensive Blooket review, I will share my experience with Blooket and explain how it can unlock the potential of your classroom.
Table of Contents
What Is Blooket?

Are you seeking a fun and engaging way to make learning exciting for your students? This innovative platform offers a wide variety of review games that are sure to engage and motivate your students.
Blooket is the ultimate learning experience, providing a fun and engaging way for students to review and reinforce their knowledge.
One of the standout features of Blooket is its game ID system. Each game has a unique ID that can be shared with students, allowing them to easily access and join the game.
This makes it easy to incorporate it into your classroom routine, and students will love the excitement and competition that comes with playing these educational games.
But Blooket is more than just a game platform – it’s a comprehensive tool for teachers. With Blooket, you can create your own review games, customize questions to fit your curriculum, and track student progress with ease.
Whether you’re looking to reinforce basic concepts or challenge your students with advanced material, Blooket has something for you.
In addition to the customizable games, Blooket also offers a wide variety of pre-made games covering a range of subjects, including math, science, social studies, and language arts. These games are designed to be both fun and educational, providing students with a well-rounded review experience.
Overall, Blooket is an excellent choice for teachers seeking to make learning a fun and engaging experience.
With its innovative game ID system, customizable games, and extensive library of pre-made games, Blooket offers the ultimate learning experience for students of all ages.
How Blooket Works
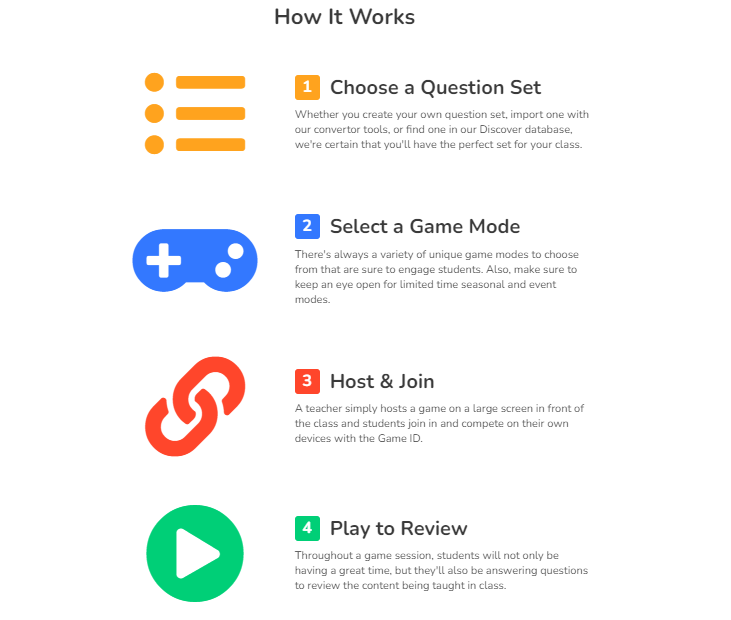
Blooket is an online platform that allows teachers to create and customize game-based learning activities for their students.
The platform incorporates a variety of game modes, including flashcards, quizzes, and team games, to keep students engaged and motivated.
To get started with Blooket, teachers can create an account and begin building their own games or use pre-made games created by other educators.
While preparing this Blooket review, I observed that the platform is user-friendly and intuitive, making it easy for even novice users to get started.
Blooket Features
Blooket is an interactive and engaging online game platform designed for both educators and students.
It offers a diverse range of features that make learning fun and enjoyable. One of the key features of Blooket is its game mode, which allows students to play games in a competitive and collaborative environment.
This mode is perfect for classroom settings where educators can create games tailored to the specific needs and interests of their students. With Blooket’s game mode, students can learn new concepts and skills while having fun.
Another great feature is its ability to allow students to join games using their own devices. This feature ensures that every student can participate in the game regardless of their location and device.
The platform is designed to be device-agnostic, meaning it works seamlessly on desktops, laptops, tablets, and even smartphones. This feature is particularly useful as it allows students to join games from anywhere in the world, at any time.
It also offers a wide range of game options that cater to different learning styles and preferences.
Students can choose from various game modes, including classic, team, and timed modes. These modes enable students to compete with one another or collaborate towards a common goal, fostering critical thinking and problem-solving skills. Students can answer questions based on their question set or class.
Additionally, Blooket provides customizable options for educators to create their own games, making the platform an excellent tool for creating personalized learning experiences.
Blooket also offers a wide range of question sets, which are designed to cater to different age groups and learning levels. This makes it easy for parents and teachers to find the right content for their kids, and ensures that the games remain challenging and engaging.
To start playing, users must enter a code provided by the game creator. This code ensures that only authorized users can access the game and helps to keep the game safe and secure.
Not to mention, it is a fantastic platform that offers numerous features to make learning fun and interactive.
With its game mode, students join the platform to play games in a competitive and collaborative environment. The ability to join games using their own devices ensures that every student can participate.
The diverse range of game options and customizable features make it an ideal tool for educators looking to create personalized learning experiences for their students.
Overall, Blooket is an excellent platform that combines education and entertainment in a fun and engaging way.
READ ALSO: The Hidden Threats in EdTech: What Teachers Need to Know About Classroom Cybersecurity
Benefits of Using Blooket in the Classroom
One of the biggest benefits of using Blooket in the classroom is its ability to engage students in a fun and interactive way. By incorporating game-based learning, teachers can create a more dynamic and engaging learning experience that encourages students to be active participants in their own education.
Another benefit is its ability to personalize learning for each student. Teachers can create different games for different skill levels or learning styles, allowing students to learn at their own pace and in a way that best suits them.
READ ALSO: How to Take Your First Step into Cybersecurity
Blooket Game Modes
Blooket offers a variety of game modes to choose from, including flashcards, quizzes, and team games. Each game mode is designed to keep students engaged and motivated while reinforcing key concepts and skills.
Flashcards are an excellent way to reinforce vocabulary and memorization skills. Quizzes can be used to test students’ knowledge of a particular subject or to review material before an exam.
Team games, such as “Battle Royale” and “Tower Defense,” encourage collaboration and teamwork among students.
Creating and Customizing Your Own Blooket Game
One of the best features of Blooket is its ability to customize games to fit your specific needs. Teachers can create their own games from scratch or modify pre-made games to better suit their lesson plans.
Customization options include adding or removing questions, rearranging the question order, and adjusting the difficulty level. Teachers can also add images or videos to their games to make them more engaging and interactive.
Strategies for Incorporating Blooket into Lesson Plans
To get the most out of Blooket, it’s important to incorporate it into your lesson plans in a strategic way. One effective strategy is to use this learning app as a review tool before an exam or quiz. By creating a quiz game that covers key concepts or vocabulary, students can review material in a fun and engaging way.
Another strategy is to use Blooket as a formative assessment tool. By creating a game that covers material students have just learned, teachers can quickly and easily assess their understanding and adjust their lesson plans accordingly.
Student Engagement and Learning Outcomes with Blooket
In my experience, Blooket has proven to be a highly effective tool for engaging students and enhancing learning outcomes. By incorporating game-based learning, students become more motivated and engaged, resulting in better retention of material and improved academic performance.
Additionally, Blooket’s ability to personalize learning for each student enables a more individualized approach to education. By creating games that align with each student’s learning style and skill level, teachers can ensure that all students are challenged and supported in their learning journey.
Blooket Pricing
One of the key features of this gamified learning tool is its pricing model. Blooket is completely free to use, with no hidden costs or fees associated with the site.
This makes it an ideal choice for parents and teachers seeking an affordable way to educate and entertain their children.
Overall, Blooket is a fun and engaging educational tool that provides kids with an exciting way to learn.
Its free pricing model, time limits, question sets, and code system all work together to create a safe and entertaining gaming experience for kids of all ages.
READ ALSO: Student Cybersecurity: 5 Simple Tips for Safety
Best Practices for Using Blooket in the Classroom
To get the most out of this tool, it’s important to follow some best practices.
First, ensure that you create games that align with your lesson plans and learning objectives. This will help ensure that students are learning the material they need to succeed.
Second, be sure to vary the game modes you use to keep students engaged and motivated. Flashcards and quizzes are great, but incorporating team games and other interactive activities can make for a more dynamic and engaging learning experience.
Finally, be sure to provide feedback to students on their performance in Blooket games. This can help students identify areas where they need improvement and enable teachers to adjust their lesson plans as needed.
Conclusion: The Future of Educational Gaming with Blooket
In conclusion, Blooket is a powerful tool for engaging students in a fun and interactive way. By incorporating game-based learning into your lesson plans, you can unlock the potential of your classroom and help your students achieve academic success.
Whether you’re looking to review material before an exam or provide personalized learning opportunities for each student, Blooket offers a variety of game modes and customization options to fit your needs.
So why not give Blooket a try and see how it can transform your classroom engagement?
Leave a comment below regarding this Blooket review.
INTERESTING POSTS
















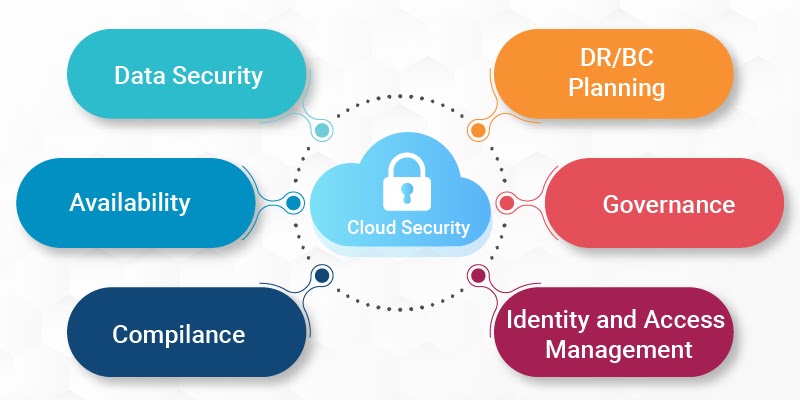 These are the following components that come under cloud security and protection:
These are the following components that come under cloud security and protection: