Read on for the eyeZy review. Phone monitoring software makes it easy to keep an eye on children, spouses, employers, and aged parents.
In the age of digital information, the demand for phone monitoring solutions has skyrocketed. EyeZy is one such solution that strives to offer a comprehensive and versatile platform for monitoring and tracking mobile devices.
There are several phone monitoring apps, but eyeZy review stands out as a parental control app with much emphasis on social media monitoring.
In this eyeZy review, we’ll take a deep dive into EyeZy’s capabilities, ethical considerations, as well as its potential pros and cons. Our aim is to provide an in-depth analysis that will help you decide whether EyeZy is the right choice for your monitoring needs.
Table of Contents
What Is eyeZy?
 eyeZy is a phone monitoring app that empowers you to remotely monitor target phones, providing you with the ability to oversee your children, spouse, or employees even when you are not physically present.
eyeZy is a phone monitoring app that empowers you to remotely monitor target phones, providing you with the ability to oversee your children, spouse, or employees even when you are not physically present.
With EyeZy, you can effectively monitor incoming and outgoing calls, keep tabs on social media interactions, track the physical location, scrutinize visited websites, and gain insights into various other activities.
EyeZy operates surreptitiously in the background after installation, discreetly recording all activities on the phone, encompassing call logs and physical location data. Notably, it also captures keystrokes entered on the target device, offering access to accounts associated with the target, thereby providing a comprehensive view of the digital world of the monitored individual.
This versatile phone monitoring tool serves as a valuable resource for parents and employers, addressing concerns related to safety, security, and responsible device usage.
eyeZy Review 2025: Facts & Figures
| Feature | Details |
|---|---|
| Monitoring Capabilities | Tracks calls, texts, social media (25+ platforms), location (GPS), apps, browsing history (limited), and more. |
| Device Compatibility | Works on Android (4.0+) and iOS (7.0+) devices. |
| Supported Languages | 10 languages, including English, Spanish, French, German, and Portuguese. |
| Data Storage & Security | Claims 256-bit AES encryption and no user data storage on their servers. |
| Remote Management | Web-based dashboard and mobile app for on-the-go monitoring. |
| Geofencing | Set virtual boundaries and receive alerts when entered or exited. |
| App Blocking | Restrict access to specific applications on monitored devices. |
| Website Blocking | Block access to inappropriate or distracting websites. |
| Keylogging (Android only) | Monitor keystrokes typed on the device. |
| Customer Support | Email support and online resources are available. |
| Pricing | Starts at $29.99 per month for 1 device, with discounts for multiple devices and longer plans. |
| Free Trial | A 3-day free trial is available. |
READ ALSO: 16 Best Protection Tools Against Hackers [100% WORKING]
Benefits Of Using eyeZy Phone Monitoring App
The EyeZy Phone Monitoring App offers an array of compelling benefits that cater to the needs of parents, employers, and individuals who want to maintain a watchful eye over their loved ones or employees. Let’s explore these advantages in greater detail:
Real-Time Location Tracking
EyeZy’s standout feature is its ability to provide real-time location tracking. Parents can use this to keep a close eye on their children’s whereabouts, particularly when they’re constantly on the move or if they have elderly family members who may require assistance.
Geofencing alerts enable users to receive notifications when a loved one enters or exits a specified area, thereby enhancing peace of mind and safety.
Phone Calls and Messages Monitoring
EyeZy’s capability to monitor phone calls and messages is invaluable for both parents and employers.
Parents can use it to ensure their children are not engaging with strangers or getting involved in potentially risky situations. Employers, on the other hand, can monitor employee communications to safeguard sensitive information and maintain professional conduct.
Protection Against Cyberbullying
In an era marked by the growth of cyberbullying, EyeZy steps in as a protector. It enables parents to closely monitor their children’s social media activity and receive alerts if any signs of bullying or online harassment arise.
This proactive approach allows parents to intervene and prevent further harm to their children’s well-being.
Prevention of Data Theft
For employers, data theft is a top concern, and EyeZy serves as a valuable deterrent. The app enables employers to monitor employee emails and instant messaging conversations, ensuring that confidential information remains within the organization.
Additionally, tracking internet activity helps ensure employees do not visit potentially hazardous websites that could lead to a data breach.
Improved Productivity
EyeZy’s comprehensive monitoring capabilities contribute to enhanced workplace productivity. It enables employers to closely monitor employee activities, making it easier to identify areas where improvements can be made.
For example, if an employee spends an excessive amount of time on social media, EyeZy promptly alerts employers, enabling them to take corrective action. This can lead to a more efficient and focused work environment.
How To Get Started With eyeZy
Getting started with EyeZy is a straightforward process that enables you to access its comprehensive monitoring capabilities. Here’s a step-by-step guide to help you get started:
1. Visit the Official EyeZy Website
To initiate the process, visit the official EyeZy website. You can do this from any web browser on your computer or mobile device.
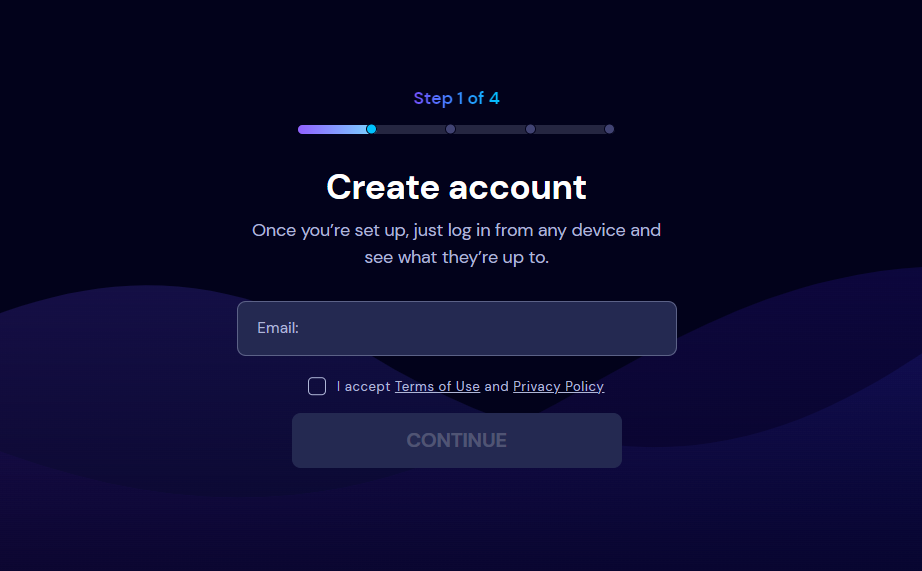
2. Create an Account
Once on the website, create your EyeZy account by signing up. This typically involves providing your email address and setting up a secure password.
3. Download and Install EyeZy
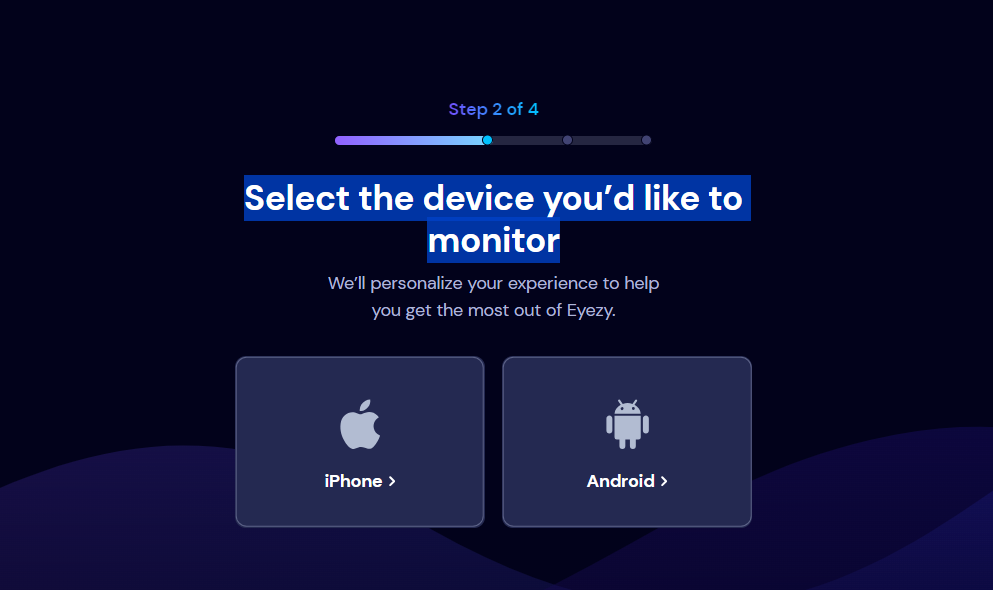
EyeZy allows you to monitor either iPhone or Android devices. So, select the device you’d like to monitor.
If you are targeting an Android device, you will need to download and install the EyeZy app directly onto the target device. You can usually find the download link on the official website.
For iOS users, you can connect to the target device by logging in to the user’s iCloud account. This typically involves obtaining the user’s iCloud credentials, and it is crucial to respect privacy and legal considerations during this process.
4. Select the Plan That Suits You
EyeZy offers various subscription plans to cater to different needs. Select the plan that best suits your needs and proceed to the payment page.
5. Make Payment
Complete the payment process according to your chosen plan. EyeZy often accepts various payment methods to make the process as convenient as possible for users.
6. Access Your Dashboard
After successfully setting up EyeZy on the target device, you can start monitoring its activities. Access your dashboard from anywhere in the world using your login credentials. This dashboard serves as your control center, providing you with insights into the activities and data of the monitored device.
By following these steps, you can seamlessly start using EyeZy to monitor the target device and gain a comprehensive view of its phone activities. Remember to always use monitoring software responsibly and in compliance with legal and ethical considerations, including obtaining the necessary consent when monitoring someone else’s device.
eyeZy Features
EyeZy offers a comprehensive suite of features designed to provide you with in-depth insights into the activities of the target device.
Let’s explore these EyeZy features in detail:
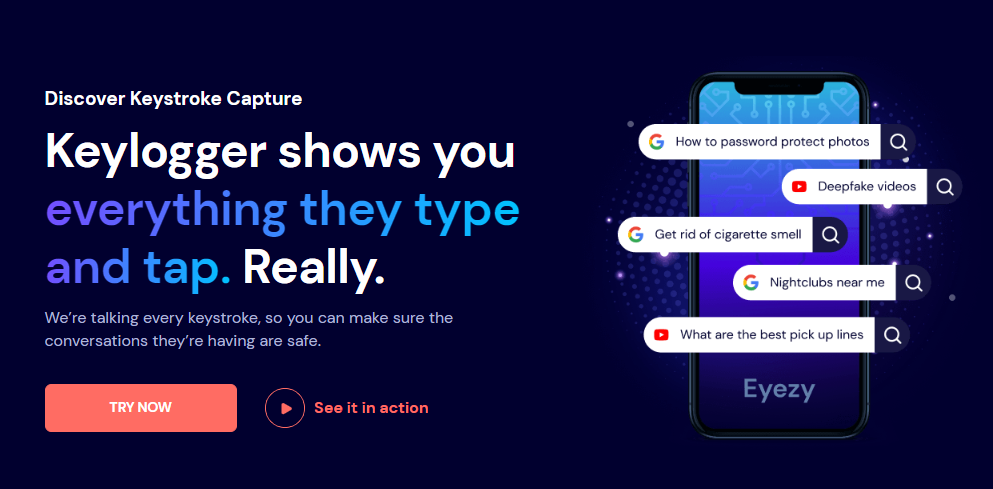
Keystroke Capture
This feature unveils every keystroke made on the phone, exposing passwords, sensitive information, and even private thoughts. It provides a window into the user’s mind, revealing their innermost thoughts and intentions.
With Keystroke Capture, you can gain a deeper understanding of the user’s motivations and potential actions.
Uncover hidden passwords, sensitive information, and even private thoughts by capturing every keystroke made on the phone.
This comprehensive monitoring tool provides you with unprecedented access to the user’s digital life, enabling you to stay informed and protect them from potential harm.
Social Spotlight
Unveil the user’s private text conversations, including deleted chats. Gain insights into their social media activities on platforms like WhatsApp, KiK, Tinder, Snapchat, Skype, Instagram, and Facebook.
Social Spotlight provides a 360-degree view of the user’s social interactions, revealing their connections, interests, and potential risks.
Delve into the user’s social world by monitoring their private text conversations and social media activities. Uncover deleted chats, hidden connections, and potential risks, ensuring that the user is engaging in safe and appropriate online interactions.
Pinpoint
Track the user’s exact location using GPS and advanced WiFi network analysis. Stay informed about their whereabouts and movements. Pinpoint provides real-time location tracking, allowing you to monitor the user’s movements and ensure their safety.
Stay informed about the user’s whereabouts and movements with real-time location tracking. Pinpoint utilizes GPS and advanced WiFi network analysis to provide accurate location data, giving you peace of mind and the ability to intervene if necessary.
Plans Breaker
Monitor the user’s social calendar to reveal their plans, schedules, and the people they’re interacting with. Proactively prevent them from attending events you disapprove of. Plans Breaker gives you control over the user’s social life, allowing you to guide them towards positive and safe experiences.
Proactively prevent users from attending events you disapprove of by monitoring their social calendars and identifying potential risks. Plans Breaker empowers you with the knowledge and tools to guide users towards safe and enriching social interactions.
Files Finder
Uncover the user’s hidden digital life by accessing their saved photos, videos, and files. Gain insights into their interests, preferences, and activities. Files Finder provides a gateway to the user’s digital world, revealing their hidden thoughts, interests, and activities.
Uncover the user’s hidden digital life by accessing their saved photos, videos, and files. Gain insights into their interests, preferences, and activities, ensuring that they are engaging in safe and appropriate online behaviour.
Web Magnifier
Decipher the user’s online behavior by tracking their internet searches, visited websites, bookmarks, and interests. Understand their online habits and potential risks. Web Magnifier provides a window into the user’s online world, revealing their interests, motivations, and potential risks.
Gain a comprehensive understanding of the user’s online behavior by tracking their internet searches, visited websites, bookmarks, and interests.
Web Magnifier provides valuable insights, enabling you to identify and address potential risks and guide users towards safe and positive online experiences.
Connection Blocker
Take control of the user’s internet access by managing website access, app usage, and usage duration. Set boundaries and prevent them from accessing inappropriate or harmful content.
Connection Blocker enables you to create a safe and controlled online environment for users.
Set boundaries and prevent the user from accessing inappropriate or harmful content by managing website access, app usage, and usage duration. Connection Blocker provides you with the tools to protect the user from online dangers and guide them towards safe and enriching online experiences.
Magic Alerts
Establish virtual fences and receive instant notifications when the user engages in concerning or inappropriate behavior, including controversial searches, chats, or physical movements beyond designated safe zones.
Magic Alerts provides real-time alerts, allowing you to intervene promptly and address potential risks.
Receive instant notifications when the user engages in concerning or inappropriate behavior, including controversial searches, chats, or physical movements beyond designated safe zones.
Magic Alerts provides real-time alerts, empowering you to protect the user from harm and guide them towards safe and positive behavior.
Phone Analyzer
Gain comprehensive insights into the user’s phone calls, including caller ID, call duration, and more. Stay informed about their communication patterns and potential risks.
Phone Analyzer provides a comprehensive overview of the user’s phone calls, allowing you to identify potential risks and ensure their safety.
Stay informed about the user’s communication patterns and potential risks by gaining comprehensive insights into their phone calls.
Phone Analyzer provides caller ID, call duration, and other valuable information, enabling you to protect the user from online dangers and guide them towards safe and responsible communication habits.
Invisible Shield
Operate in stealth mode, monitoring the user’s activities without their knowledge. Stay informed without compromising your privacy. Invisible Shield provides a discreet monitoring solution, allowing you to stay informed without compromising the user’s privacy or trust.
Monitor the user’s activities without their knowledge thanks to Invisible Shield’s stealth mode operation.
This discreet monitoring solution provides valuable insights into the user’s digital life while preserving their privacy and trust, ensuring that you can offer support and guidance without compromising their sense of autonomy.
Friendly Installer
Choose the installation method that suits your needs, whether it’s jailbreak, iCloud Sync, or local WiFi sync. Effortlessly set up Eyezy and start monitoring discreetly.
Friendly Installer provides flexible installation options, making it easy to set up Eyezy and start monitoring discreetly.
Choose the installation method that suits your needs, whether it’s jailbreak, iCloud Sync, or local WiFi sync.
Friendly Installer provides flexible installation options, ensuring that Eyezy can be seamlessly integrated into your monitoring setup, regardless of your technical expertise or device compatibility.
eyeZy Apps
EyeZy is designed to seamlessly integrate with a diverse range of devices, ensuring that you can stay connected and informed about the digital activities of your loved ones. Whether you’re an Android user or prefer the iOS platform, EyeZy has you covered.
EyeZy is compatible with Android devices running Android OS version 4.0 or later, encompassing both rooted and unrooted devices. This extensive compatibility ensures that EyeZy can be used on a wide range of Android devices, providing users with flexibility and convenience.
For iPhone users, EyeZy effortlessly integrates with iOS versions 4 and later. This compatibility extends to both rooted and unrooted devices, allowing you to monitor your loved ones’ iPhone activities regardless of their device’s configurations.
With its extensive device support, EyeZy provides a versatile solution for monitoring and safeguarding your loved ones in today’s interconnected world.
eyeZy Customer Services
EyeZy offers multiple channels for users to access customer support and assistance, ensuring a responsive and helpful experience. Here are the primary ways to get support from EyeZy:
- LiveChat Support: EyeZy provides users with a LiveChat feature that connects them to 24/7 customer support. This real-time chat option enables users to receive immediate assistance with their inquiries or issues, providing a fast and convenient way to get help.
- Helplines: Users can reach out to EyeZy’s customer support team via phone using the helpline number +18446063888. This direct communication channel enables users to receive prompt assistance and have their concerns addressed in a timely manner.
- Email Support: While email response times may vary, EyeZy typically ensures that email queries receive a response within four hours. Email support allows users to provide detailed descriptions of their issues or inquiries, offering a written record of communication.
Depending on your specific needs and preferences, LiveChat and helplines are the fastest means to access EyeZy’s support services.
These channels offer immediate assistance and are ideal for addressing urgent concerns or questions. Email support remains a valuable option for more detailed discussions and documentation of communication.
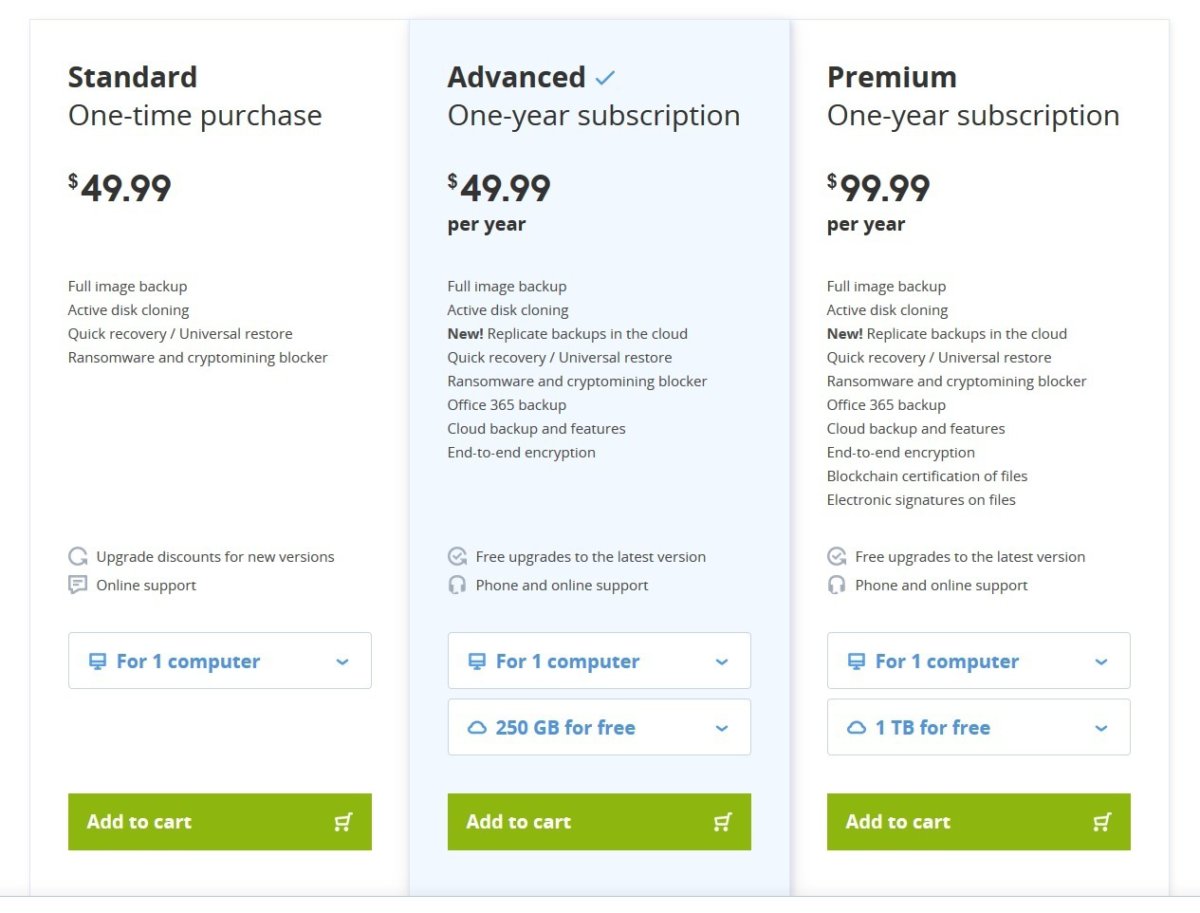
eyeZy Pricing
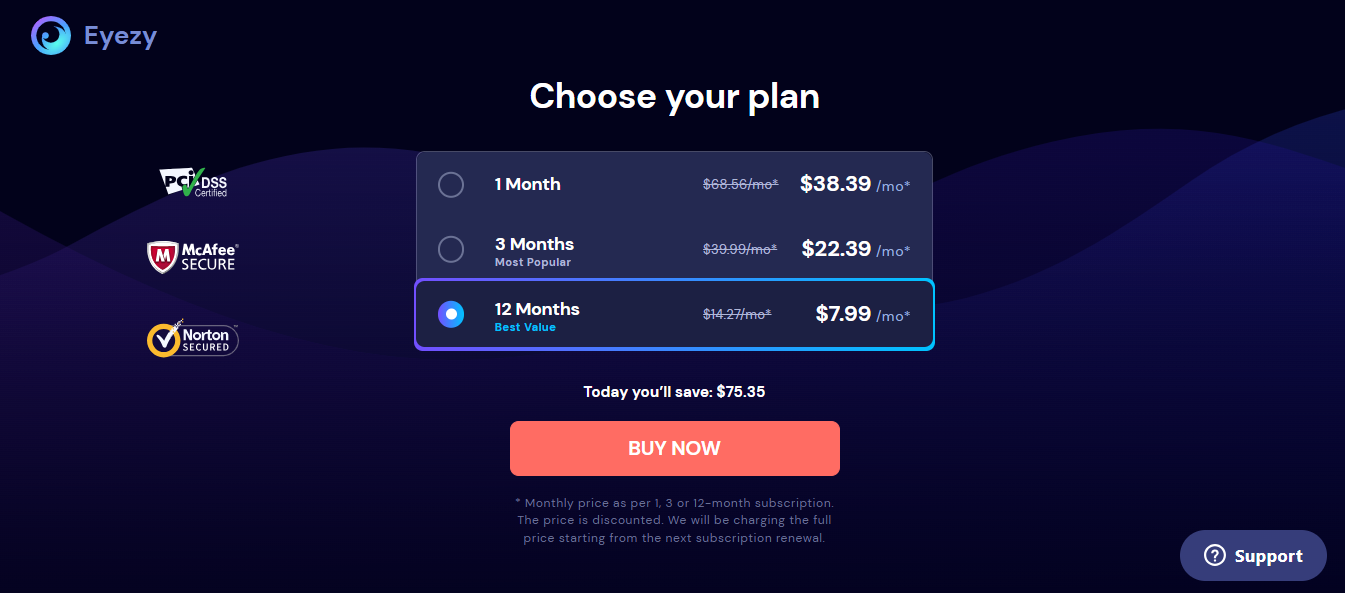
EyeZy offers a straightforward pricing structure with three subscription tiers, making it convenient for users to choose the plan that best suits their needs and budget. Here’s an overview of EyeZy’s pricing options:
1. Monthly Plan
Cost: $38.39 per month
This plan is ideal for users who require short-term monitoring or wish to try the service without a long-term commitment.
2. Quarterly Plan
Cost: $22.99 per month per quarter
The quarterly plan provides a cost-effective option for users seeking a longer monitoring duration, offering the added benefit of lower monthly costs compared to the monthly plan.
3. Yearly Plan
Cost: $7.99 per month per year
The yearly plan provides significant cost savings for users committed to extended monitoring. It offers the lowest monthly cost and ensures continuous monitoring throughout the year.
Note: All EyeZy subscription plans include a 14-day money-back guarantee. This assurance allows users to try the service risk-free and decide if it aligns with their needs and expectations. If you’re not satisfied within the first 14 days, you can request a refund.
EyeZy’s transparent pricing and money-back guarantee reflect the company’s commitment to providing users with flexibility, affordability, and peace of mind when using their phone monitoring software.
Users can select the subscription plan that best fits their specific requirements and enjoy the benefits of EyeZy’s comprehensive monitoring features.
eyeZy Pros And Cons
Pros
- Comprehensive Monitoring: EyeZy offers a diverse array of features, ensuring a holistic view of the target device’s activities. This makes it a versatile tool for parents and employers.
- User-Friendly Interface: The software is designed to be user-friendly, making it accessible to individuals with varying levels of technical expertise.
- Real-Time Alerts: EyeZy enables users to receive real-time alerts for specific activities, such as accessing blocked websites or crossing predefined geographical boundaries.
- Cross-Platform Compatibility: EyeZy is compatible with both Android and iOS devices, providing flexibility to users with a variety of target devices.
- 24/7 Customer Support: The company offers round-the-clock customer support to assist users with any issues they may encounter.
Cons
- Ethical Concerns: The use of monitoring software raises significant ethical questions, particularly regarding consent and privacy. The installation of such software on a device without the user’s knowledge or permission can lead to legal and moral issues.
- Intrusive Keylogger Functionality: While the keylogger feature can be useful, it’s also highly intrusive and can easily cross the line into unethical territory.
- Cost: EyeZy, like many monitoring software solutions, comes with a price tag that may not be accessible to everyone.
- No Free Trial: Unlike some competitors, EyeZy does not offer a free trial, making it difficult for potential users to assess its functionality before purchasing.
eyeZy Review: Ratings
In assessing the efficacy and usability of EyeZy, it’s crucial to consider four key metrics: User Interface, Features, Pricing, and App Compatibility.
These ratings offer valuable insights into the software’s overall performance and user satisfaction, as well as its perception within the online community, including the EyeZy review Reddit discussions.
User Interface (UI)
Rating: 4/5
EyeZy boasts a user-friendly interface that is intuitively designed, making it accessible to individuals with varying levels of technical expertise.
Navigating through the dashboard and accessing various monitoring features is straightforward. However, certain improvements could enhance the overall user experience, which might be discussed in the EyeZy review Reddit threads.
Features
Rating: 4.5/5
EyeZy excels in offering a comprehensive array of features that cater to the needs of parents, employers, and individuals looking to monitor mobile devices.
Features such as real-time GPS tracking, call and message monitoring, and social media tracking are particularly robust. However, the keylogger function may raise ethical concerns and is a point of discussion within the EyeZy review Reddit communities.
Pricing
Rating: 4/5
EyeZy’s pricing structure provides flexibility with monthly, quarterly, and yearly plans. The yearly plan offers significant cost savings, making it a budget-friendly choice for long-term monitoring.
The inclusion of a 14-day money-back guarantee enhances user confidence. However, discussions on the pricing structure, especially in comparison to other similar apps, can be found in EyeZy review Reddit threads.
App Compatibility
Rating: 4/5
For this eyeZy Review, EyeZy demonstrates broad compatibility, working seamlessly with Android devices (both rooted and unrooted) and iOS devices.
This wide range of device support ensures its accessibility to a vast user base. Discussions related to compatibility and any potential limitations may surface in EyeZy review Reddit conversations.
In summary, EyeZy garners favorable ratings across the board, with its comprehensive features and user-friendly interface being significant strengths.
Pricing options cater to various user needs, and the broad compatibility ensures accessibility. However, the ethical considerations of certain features may be raised within the EyeZy review Reddit community.
As with any phone monitoring software, it is crucial to employ EyeZy responsibly and in accordance with legal and ethical standards.
eyeZy Review: 4 Best eyeZy Alternatives
1. Kaspersky Safe Kids
Kaspersky Safe Kids is a reliable parental control and monitoring solution designed to keep children safe while using digital devices.
This software offers robust web filtering to block inappropriate content, application management, and the ability to set screen time limits.
Unlike EyeZy, Kaspersky Safe Kids emphasizes a strong focus on child safety, offering comprehensive features that ensure a secure online environment for your children.
==>> Get Kaspersky Safe Kids
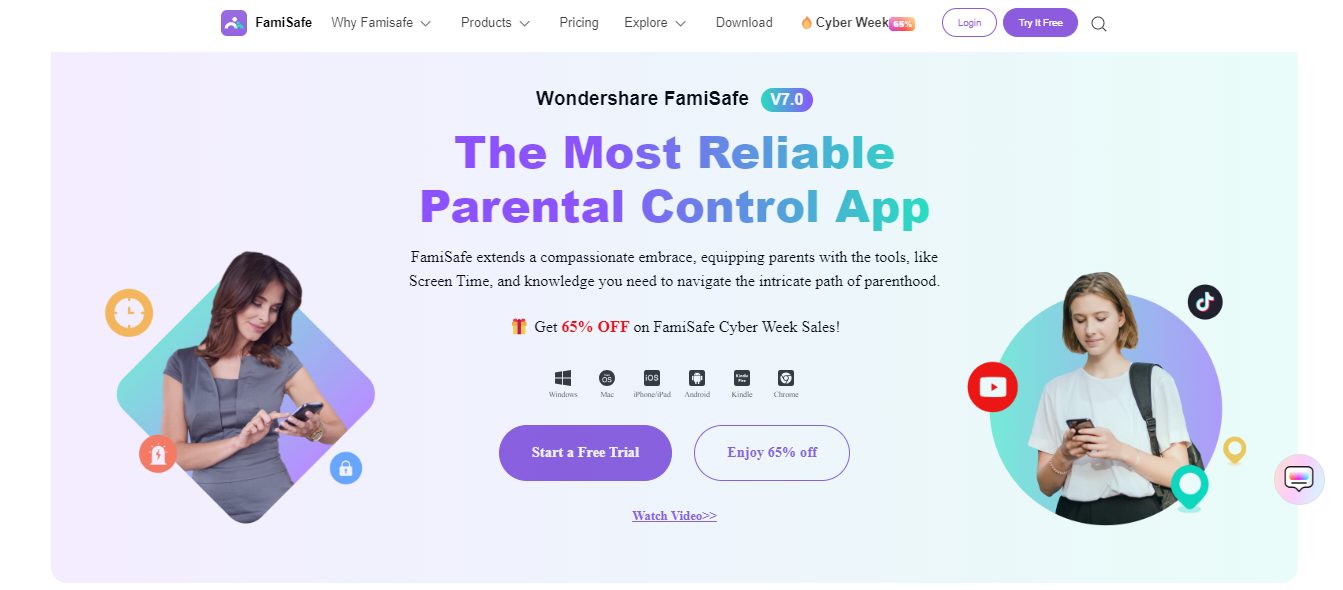
2. FamiSafe
One of the best EyeZy alternatives is FamiSafe. FamiSafe is a versatile and comprehensive parental control application that empowers parents to monitor and protect their children online.
It provides real-time location tracking, geofencing, social media monitoring, and content filtering.
Unlike EyeZy, FamiSafe excels in tracking your child’s physical location, ensuring you’re always aware of their whereabouts in addition to their digital activities.
==>> Get FamiSafe
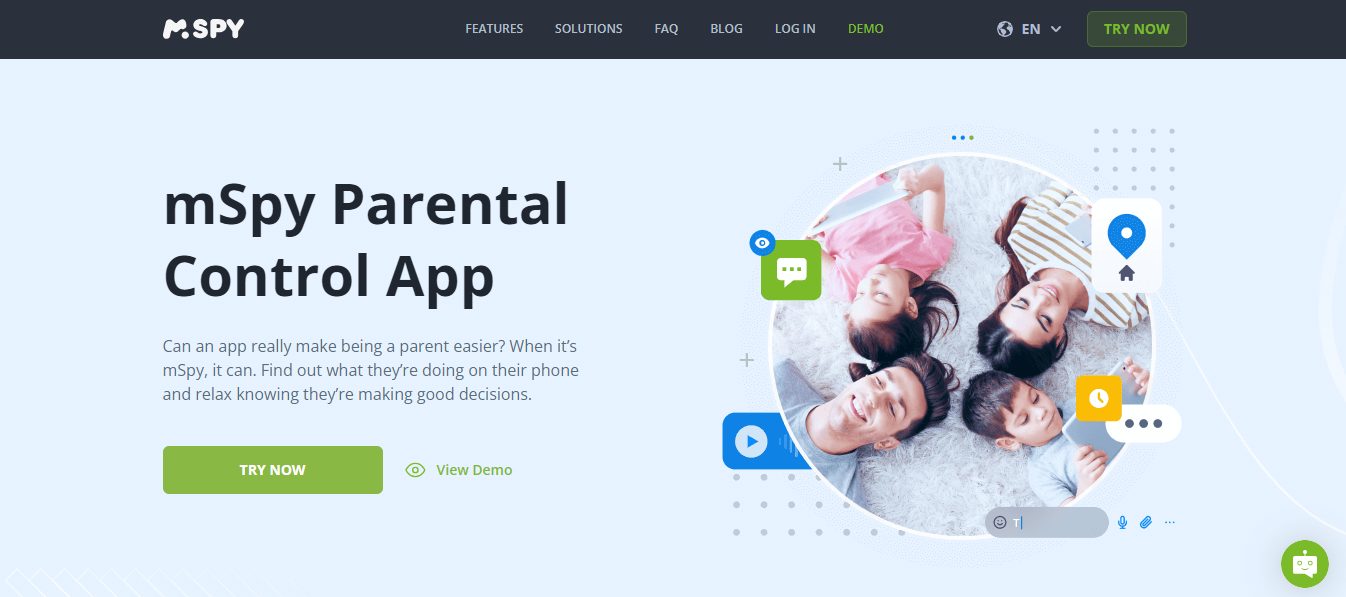
3. mSpy
mSpy is a versatile phone monitoring application suitable for both parents and employers. It offers an array of features, including call and message tracking, GPS location monitoring, and app usage insights.
Unlike EyeZy, mSpy’s keylogger functionality is a unique offering that can provide valuable insights into a monitored device, particularly when it comes to messages and credentials.
==>> Get mSpy
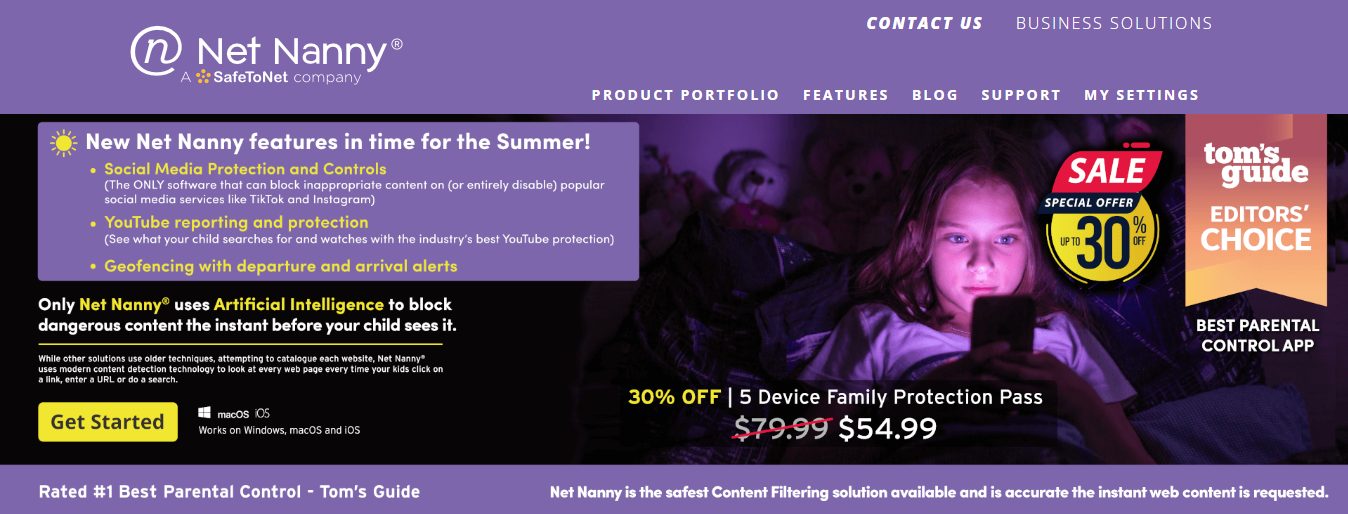
4. Net Nanny
Another best Eyezy alternative is Net Nanny. Net Nanny is a well-established parental control and content filtering software that excels in protecting children from inappropriate online content.
It offers comprehensive web filtering capabilities to restrict access to websites and content that may not be suitable for children.
In contrast to EyeZy, Net Nanny is primarily dedicated to content filtering and ensuring that your child’s online experience remains safe and age-appropriate.
READ ALSO: Full Review Of Qustodio Parental Control Software
Other Spy Apps (Parental Control Software)
Qustodio
Norton Family
ESET Parental Control
eyeZy Review: Frequently Asked Questions
When considering a phone monitoring app like eyeZy, you likely have several questions. Let’s address some of the most common queries to help you make an informed decision:
Is eyeZy legit?
Yes, eyeZy is a licensed software designed for various purposes, including parental control and employee monitoring. As a legitimate app, eyeZy operates within legal and ethical boundaries, empowering users to monitor target phones responsibly.
What can you do with eyeZy?
eyeZy is a spy app powerhouse! It lets you monitor:
- Phone calls and text messages: Stay informed about conversations through remote phone monitoring.
- Social media activity: Monitor social media apps like Facebook Messenger to provide invaluable social media monitoring.
- GPS location: Track your kid’s device whereabouts for peace of mind.
- Browser history: Gain insight into online activity.
- And more! This is just a taste of what eyeZy lets you do.
Do you have to pay for Eyezy?
Yes, eyeZy is a subscription service. Choose from plans depending on your needs and multiple devices you want to monitor. Although no free trials are offered, a 14-day money-back guarantee allows you to try it risk-free.
Is Eyezy undetectable?
Like any phone monitoring software, eyeZy aims to be discreet. However, its detectability can vary depending on factors such as the target device’s operating system (e.g., an Apple ID is required for iOS devices). Generally, newer Android and non-jailbroken iPhones provide better stealth.
Is Eyezy safe?
eyeZy prioritizes security. You can easily uninstall it from the target device. Military-grade encryption protects user data, ensuring safe and responsible monitoring through the eyeZy dashboard.
Can I filter or block content and apps on my kid’s device with eyeZy?
Absolutely! eyeZy goes beyond simply monitoring; it gives you the power to protect your child with app blocking. On Android devices, you can choose specific social media apps or any other apps you find concerning, and restrict access from the target device. For iOS devices, while direct app blocking isn’t available, you can utilize screen time controls and website blocking to manage their online activity.
This granular control lets you customize their digital experience, ensuring they don’t encounter inappropriate content on social media chats, gaming platforms, or other websites. eyeZy even offers a “Magic Alert” feature that notifies you of suspicious keywords or phrases used in phone calls, text messages, or social media app interactions on the target phone.
Personal Experience with EyeZy
As a satisfied user for over a year, I can confidently recommend eyeZy! It’s been a powerful tool for keeping my child safe online. The user-friendly interface makes it easy to navigate, and the advanced features (like Magic Alert for suspicious activity) give me peace of mind. I’ve never had issues with data accuracy, whether it’s tracking phone calls, text messages, or monitoring social media interactions.
Ultimately, eyeZy is a valuable tool for anyone seeking responsible phone monitoring. With its comprehensive features, user-friendly interface, and commitment to security, it stands out among phone monitoring apps, such as KidsGuard Pro, available on the App Store and Google Play Store.
Hopefully, this updated write-up clarifies your doubts and helps you make an informed decision about eyeZy!
Remember: While eyeZy offers powerful features, responsible and ethical use is crucial. Always respect privacy and ensure legal compliance when using any spy app or mobile app for monitoring a child’s phone.
READ ALSO: Ultimate Digital Privacy Guide: Protect Your Data Today
Recommendation for EyeZy
I highly recommend EyeZy to any parent seeking a comprehensive and reliable monitoring app. It’s a great way to stay informed about your child’s online activity and help to keep them safe online.
Here are a few of the reasons I recommend EyeZy:
- Easy to install and use
- User-friendly interface
- Accurate tracking data
- Comprehensive monitoring features
- Reliable customer support
I hope this EyeZy review has been helpful. If you have any questions, please feel free to leave a comment below.
Overall, I give EyeZy a 5 out of 5 star rating.
In addition to the features mentioned above, EyeZy also has a number of other benefits, such as:
- It’s stealth mode, so your child won’t know you’re monitoring them.
- It’s remote access, so you can monitor your child’s phone from anywhere in the world.
- They offer 24/7 customer support, so you can always get help when you need it.
If you’re looking for a way to keep your child safe online, I highly recommend EyeZy.
A Final Word On The eyeZy Review
In wrapping up this comprehensive EyeZy review, it’s evident that EyeZy is a highly commendable choice for individuals seeking an efficient phone monitoring app, whether for parental control or other monitoring purposes.
One standout feature is its user-friendly interface, making it accessible to users of all technical backgrounds. With EyeZy, there’s no need for third-party assistance; its intuitive design ensures that even non-tech-savvy individuals can navigate its features seamlessly.
Furthermore, EyeZy offers exceptional value with its competitive pricing. At just $10 per month for the yearly subscription, it ranks as one of the most budget-friendly phone monitoring solutions on the market. Despite its affordability, it doesn’t compromise on the depth of its advanced features.
For those who prioritize effective monitoring, ease of use, and cost-efficiency, EyeZy emerges as a top-tier choice in the realm of phone monitoring apps. Whether safeguarding your children online or enhancing employee productivity, EyeZy provides a reliable and accessible solution to meet your monitoring needs.
INTERESTING POSTS
- Integrate Your Calls To CRM System
- How To Stop Calls On iPhone Without Blocking Them
- Cybersecurity Professionals Warn About Online Learning Threats For Students
- Tips For Keeping Children Safe Online [Detailed Guide For Parents]
- Importance Of Dark Web Monitoring
- Your Guide For Dealing With MacBook Malware
- The Ultimate Revelation Of Best Apps For Parental Control
- 4 Common VPN Encryption Protocols Explained
- Adware Vs Ransomware Showdown: Decoding the Threat

















![Daily VPN Review: Is Daily VPN Safe? [+Best Alternatives] Daily VPN Review: Is Daily VPN Safe? [+Best Alternatives]](https://secureblitz.com/wp-content/uploads/2022/03/Is-Daily-VPN-Safe-768x345.png)