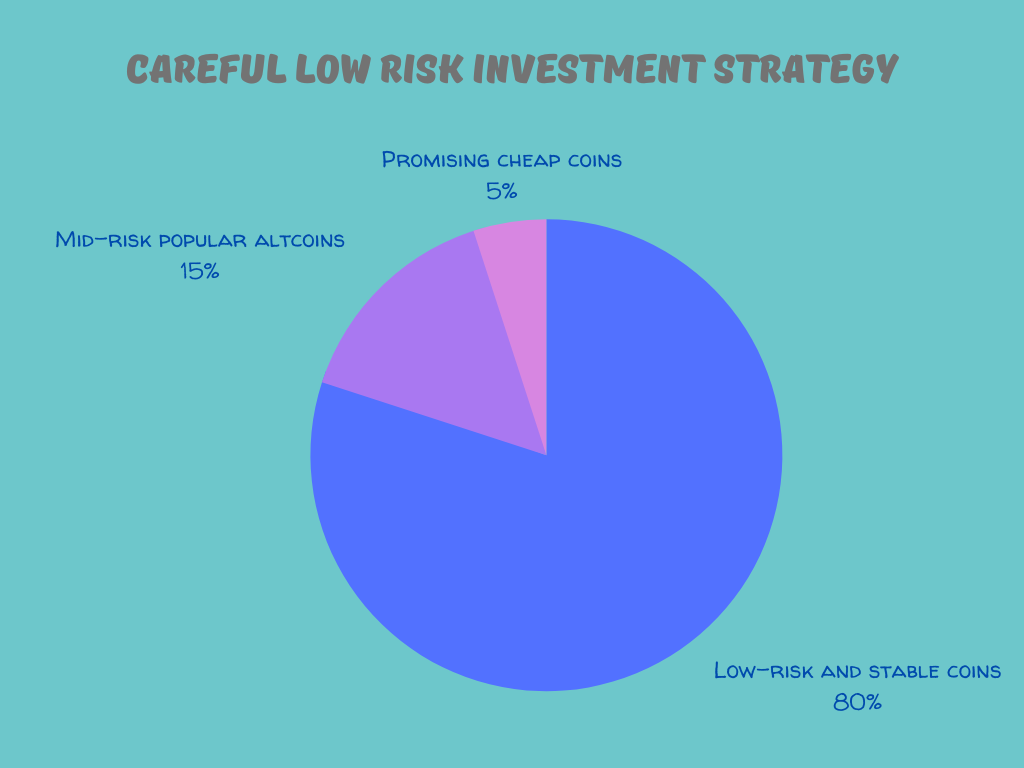
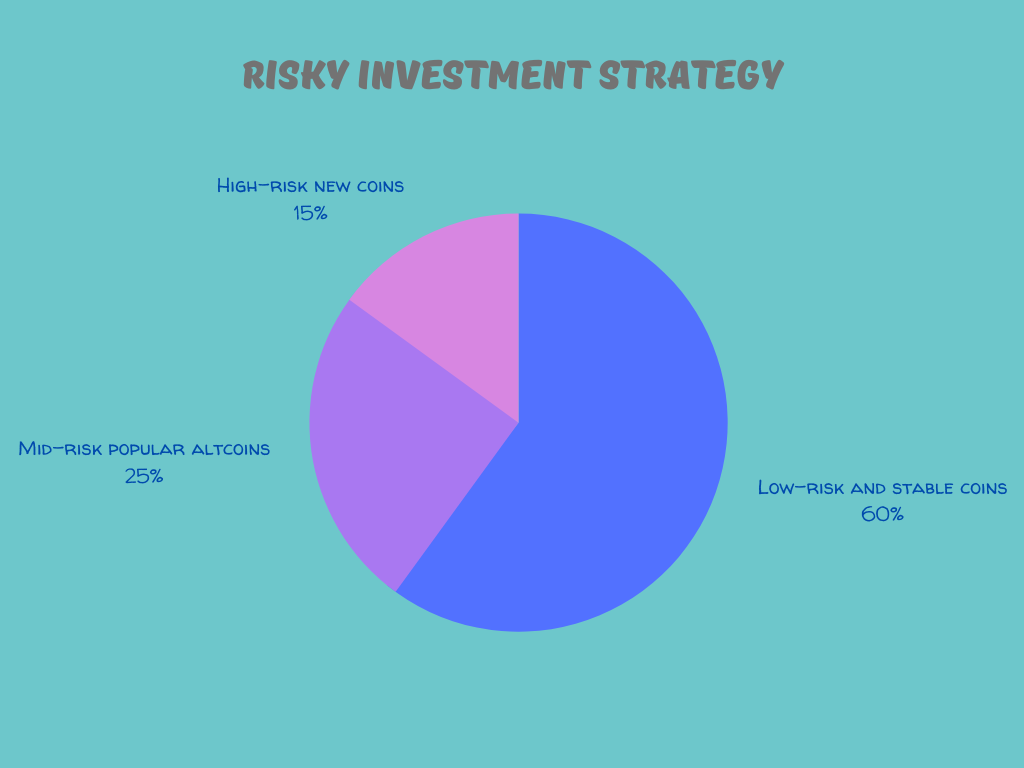
Reassure your audience that their information is safe and that it is built on an exceptional customer experience. Here, I will demonstrate why security in online forms is crucial to delivering exceptional customer experiences.
Customer journeys and delivery have been challenging, and delivering an awesome customer experience is extremely important for the success of any business’s online strategy.
Securing your online form and using it on your website will continue to deliver a positive customer experience, as customers are, and always will be, concerned about their privacy and aware of the risks associated with interacting with a form on your website.
Your website visitors have different ways to ensure their comfort and privacy wherever they’re online. They are always overprotective and will do their best to be cautious as much as possible, based on their knowledge, before providing any information on your contact form.
Also, in the latest generation of digital forms, rules can be applied to validate data when it’s collected. In this way, employees and customers can receive real-time notifications on data collection and its value.
The significance of “customer is always right” is no less relevant in today’s world than when the phrase was first coined. Currently, customer expectations are at an all-time high, yet some surveys show that more than half feel companies they interact with fall short when it comes to delivering a great experience.
Once the information is collected, it can be automatically and instantly processed in real-time. Any necessary calculations can be performed by the system, and the submission can be assigned to the relevant parties. All this can be achieved using Headlessforms form backend solution
Table of Contents
The Expectation Of Privacy And Safety
Global organizations want to acquire customers faster while delivering and securing great customer experiences. Customers should be able to move securely and seamlessly across the digital customer journey,
Remember that there is an expectation from the customer that the information that they’re submitting on an online form is going to be submitted safely and their information will be kept secure, far away from the group of people that they don’t want to see that information.
Users are hearing about data breaches in the news, compromised passwords and other horror stories. You have to pay attention to this. Here are a couple of things you can do.
Use Encryption and SSL Certificates Correctly
Ensure your website utilises some form of encryption. Set up SSL correctly and verify that the lock symbol is visible to users just before the URL in the browser to give them confidence.
Headlessforms adheres to the General Data Protection Regulation (GDPR) and other compliance regulations through its privacy and consent capabilities, including multi-tenancy, data isolation, and encryption.
Headlessforms has add-on features.
- Manage Who Has Access to Data!
- Use Permissions and Roles Effectively
- Protect Against Data Loss
- Phone avoidance
- Better data collection and processing
- Speeding up customer support cases
READ ALSO: A Look at New Forms of Marketing and How to Implement Them
Secure Your Forms
Ensure the forms you’re using are secure. Headlessform solutions are powering your forms to ensure they’re protected against hackers or malware intercepting the data being transmitted between the user and your website.
Headlessforms is designed to be easy to use, allowing you to deploy secure forms with minimal coding and development expertise. To discover more about how this works for your business, check out Headlessforms, which can help you ensure security in online forms.
Frequently Asked Questions
Why is security so important in online forms?
Data breaches and security vulnerabilities can have severe consequences for both businesses and customers:
- Financial losses: Stolen credit card information, identity theft, and fraudulent transactions can result in significant financial costs for businesses.
- Reputational damage: Data breaches erode customer trust and damage brand image, potentially leading to customer churn and legal repercussions.
- Compliance issues: Failing to comply with data privacy regulations can result in hefty fines and legal action.
- Operational disruptions: Cyberattacks can disrupt operations, impacting business continuity and service delivery.
What are the biggest security risks associated with online forms?
Several vulnerabilities can make online forms susceptible to attacks:
- Unsecured data transmission: Sensitive information, such as passwords and credit card details, can be intercepted if not transmitted using encryption methods like HTTPS.
- Weak authentication: Inadequate password requirements and a lack of multi-factor authentication can make it easier for attackers to gain unauthorised access.
- Exploitable vulnerabilities: Forms themselves can have coding errors or outdated software, creating entry points for hackers.
- Phishing and social engineering: Deceptive practices can trick users into submitting personal information to fake forms.
READ ALSO: AI Revolution: Protecting Your Cyber Future
How can businesses ensure secure online forms for a positive customer experience?
Here are some key steps to prioritize security and deliver a smooth experience:
- Implement strong encryption: Ensure all data transmission is protected with HTTPS and secure protocols.
- Enforce strong passwords and multi-factor authentication: Make password creation complex and implement additional verification steps for sensitive actions.
- Regularly update and patch software: Keep all software used for forms up to date to address known vulnerabilities.
- Validate user input: Minimize the risk of malicious code injection by validating data entered into forms.
- Be transparent about data collection and usage: Clearly communicate what data is collected and how it’s used, building trust with customers.
- Regularly conduct security audits and penetration testing to proactively identify and address security weaknesses before attackers can exploit them.
- Offer secure payment options: Ensure online payments are processed through secure gateways with industry-standard security measures.
How can prioritizing security benefit customer experience?
By prioritizing security, businesses gain several advantages:
- Increased customer trust: Customers feel confident that their information is protected, leading to increased loyalty and satisfaction.
- Reduced risk of data breaches: Fewer security incidents translate to lower customer churn and potential legal issues.
- Improved brand reputation: A secure online environment demonstrates your commitment to protecting customer data, enhancing brand image.
- Streamlined customer interactions: Secure and user-friendly forms simplify the experience, reducing friction for customers.
Bottom Line
Remember, security is not a one-time thing but an ongoing process. By taking proactive steps to secure your online forms, you can create a seamless and trustworthy experience for your customers while protecting your business from potential threats.
INTERESTING POSTS
- Why SSL Certificate Is An Essential Cybersecurity Tool?
- What Is An SSL Certificate?[MUST READ]
- 5 Features Of A Good Manufacturing Company
- What Is A Certificate Authority (CA) And What Do They Do?
- Website Security Check: How Secure Is Your Website?
- 4 Tips on How to Reach Your Target Audience More Effectively