Is GramFree legit? Is GramFree scam? Read on for the answer.
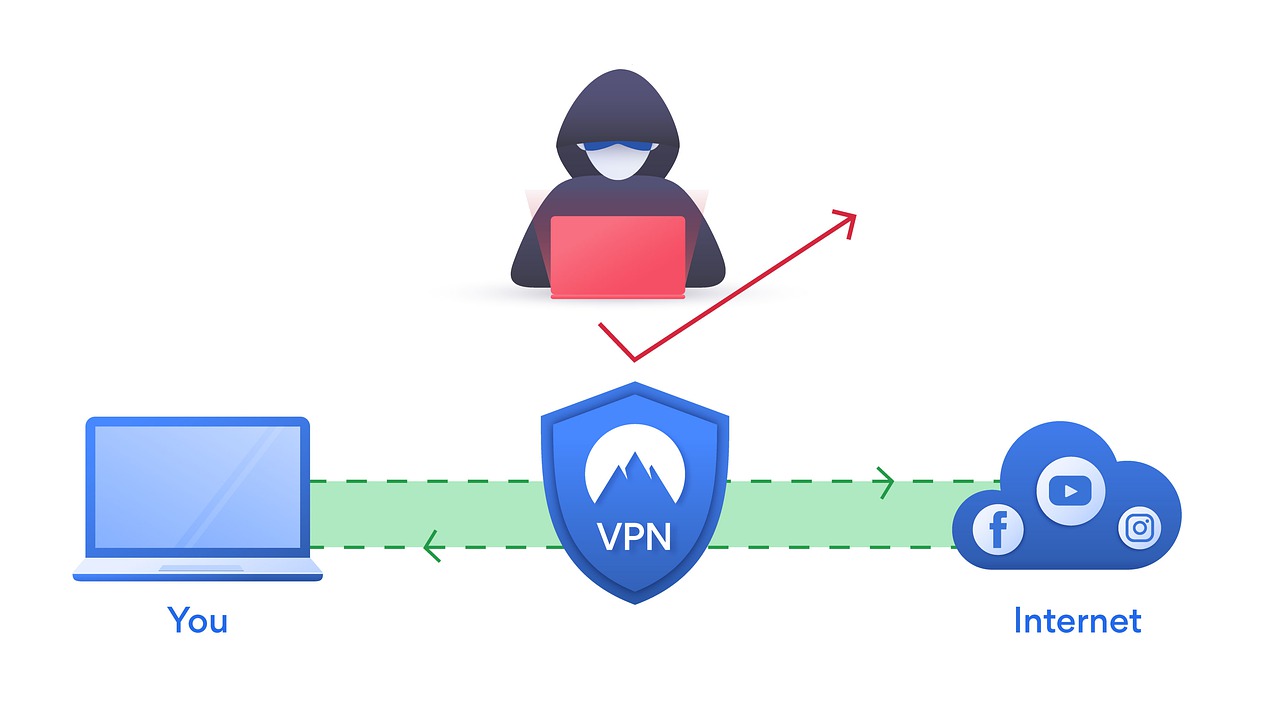
There are many “Get Paid To” websites that claim you can earn cash and other rewards by completing short online tasks, and it is challenging to determine which ones are scams or legitimate. Thankfully, you can use a VPN service like VeePN to access geo-restricted money-making websites.
GramFree is one of these websites, since earning rewards on GramFree is by doing things you would normally do online anyway.
It can be a very attractive platform to earn extra money online.
Therefore, this article will answer the question ‘Is GramFree legit or a scam? So that you can determine if you can participate or not.
Table of Contents
Is GramFree Scam?
No, GramFree is not a legitimate website. It is, in fact, a scam.
GramFree is a website that claims to be a cryptocurrency-based investment platform, offering rewards to users for completing tasks such as watching videos and referring friends.
However, the website is not owned by a registered business and is not a registered financial investment website. This should be your first red flag that something is off about this website.
Aside from not being owned by a registered business, there are several other warning signs indicating that GramFree is a scam.
For example, the website claims that users can earn up to $500 per hour, which is an outrageous amount of money and clearly not achievable in reality. The website also offers referrals and bonuses, which are also very unlikely to be true.
The bottom line is that GramFree is a scam; users should steer clear of it. Not only is it not owned by a registered business, but it also exhibits several other warning signs that indicate it is fraudulent.
Be wary of any website that makes outrageous claims or offers bonuses or referrals.
GramFree offer can be very hard to ignore, but it is a scam.
Some of the positive reviews you see online regarding the website are false. Those who made these reviews are paid in exchange for the positive review.
Another reason it is a 100 percent scam is that no one has been identified as the owner of the website.
READ ALSO: What Is GLI 19 Certification and Why It Matters for iGaming Platforms
Is GramFree Legit?
No, GramFree is not a legitimate website. It is an online scam designed to trick people into believing they can make money by completing tasks on the site.
The website claims to offer users the opportunity to earn money by watching videos, completing surveys, and inviting friends to join.
However, once you sign up for the site and start completing tasks, you quickly realize that you won’t be receiving any money.
From what I’ve heard, some people have even been asked to pay money in order to access certain features on the site.
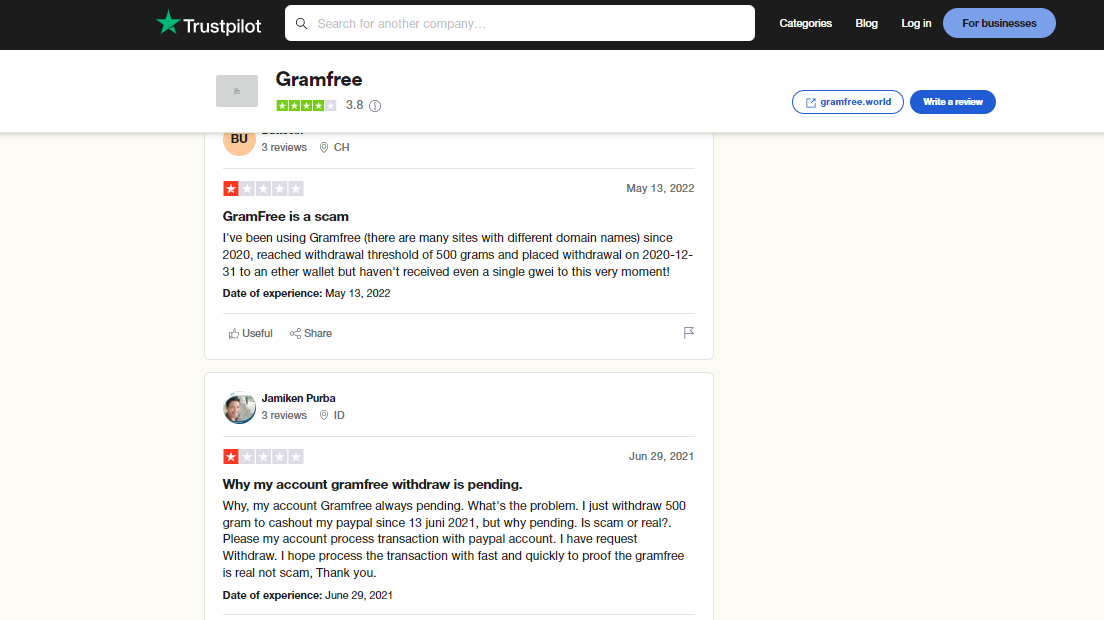
Additionally, many reviews about GramFree are negative, indicating that the site is nothing more than a scam. People have complained that the website is full of misleading information and fraudulent activities.
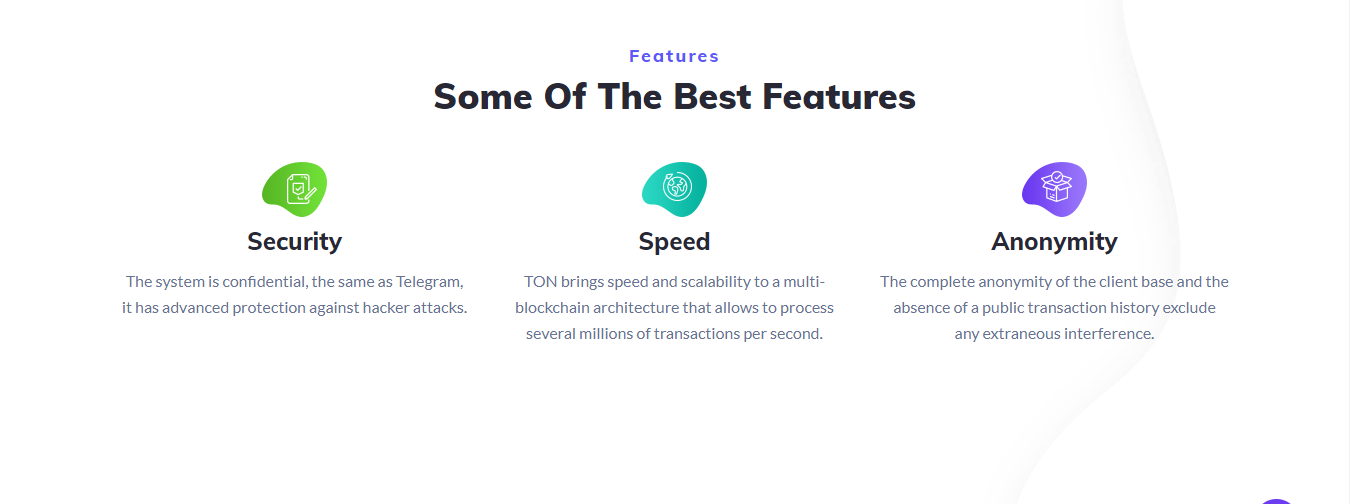
Some people believe GramFree is owned by Telegram. Although they use Telegram Open Network (TON), which anyone can use to create a platform. And they are not in any way related to Telegram
The GramFree website generates a significant amount of revenue from selling grams to its users and through advertising revenue.
Overall, I would advise everyone to stay away from GramFree. It is an online scam that is designed to take advantage of unsuspecting people and should be avoided at all costs.
READ ALSO: How To Identify And Avoid Online Gaming Scams
Discover Legitimate Earning Opportunities
While GramFree may not be a trustworthy option for earning money online, there are plenty of legitimate alternatives that offer genuine earning opportunities. Platforms like Fiverr, Upwork, and Freelancer connect freelancers with clients seeking a wide range of services.
Whether you’re a writer, designer, developer, or have other skills to offer, these platforms provide a secure and regulated environment for freelancers to find rewarding work opportunities.
Ditch the scams and explore reputable platforms that empower you to turn your skills into a source of income.
READ ALSO: Best VPN For Fiverr
What Is GramFree?
GramFree is a blockchain-based digital project with an innovative concept: you can earn money online by signing smart contracts. It is designed to be fast, safe, and scalable, meaning it can process millions of transactions per second.
The way it works is that you sign up on the platform, watch videos, complete tasks, refer friends, and earn money in the form of “Grams”. Grams are a form of cryptocurrency and can be exchanged for real money or other cryptocurrencies.
GramFree is a website that pays its users with Gram by giving them an in-game currency in return for doing simple tasks such as
- Signing smart contracts
- Watching Videos
- Depositing money
- Invitation of new members to the website
- Inputting a daily lottery
The value of one gram (in-game currency) earned by users is worth 1.78USD, as of 2020. They claimed that you can convert this gram into money by working in your comfort zone.
So far, GramFree has received mixed reviews. While some people claim to have made money with it, others report that it’s a scam and not worth their time.
It’s important to remember that with any investment, there’s always risk involved, and you should do your own research to ensure you don’t fall victim to any scams.
Nonetheless, you should note that GramFree is not a legitimate or regulated financial institution, so be sure to do your research before investing any of your hard-earned money.
Additionally, there is no guarantee of success when using GramFree; therefore, always exercise caution when deciding to invest in any online venture.
How Does GramFree Work?
On the GramFree website, you can earn grams through a lot of options, including watching videos, smart contracts, referrals, and the lottery.
Gram is given as a form of currency in which members can exchange for real money. These grams are useless if you don’t cash them out, and for you to cash them out, you must have earned up to 500 grams.
Below is a breakdown of the reward you earn per task.
- Watching videos (0.1 gram per video)
- Entering the Daily lottery (up to 1 gram per entry)
- Inviting other people (Less than 10 grams per person)
- Signing Smart contract(0.5 gram per contract)
Judging from the reward given per task, it will take up to two months to earn 500 grams doing the day-to-day tasks.
Is GramFree Still Paying?
No, GramFree is not paying users who request payment when they reach the minimum amount to cash out. Unfortunately, it appears that GramFree is not a reliable platform that pays its users.
It appears that when users request payment, their accounts are suspended, preventing them from accessing the funds they have earned. This practice is unethical and unacceptable.
It’s essential to remember that before signing up with any online platform, you should always conduct thorough research to ensure they are trustworthy and legitimate. If you come across a platform that promises huge returns, it’s probably too good to be true, and you should steer clear.
The best way to ensure safety with any online platform is to read reviews and check forums before signing up. You should also make sure that the platform is properly regulated and has a good track record of paying its users.
GramFree, unfortunately, does not seem to be a reliable platform, and it’s best to avoid it altogether.
READ ALSO: 12 Common Online Scam Tactics: Shielding Yourself from Digital Deception
How To Identify A Scam
Here are some tips on how to identify a scam:
- Be wary of websites that make outrageous claims. If a website promises you easy money or high returns with little risk, it’s probably a scam.
- Do your research. Before signing up for any online platform, read reviews and check out forums to see what other users have to say.
- Make sure the platform is regulated. Look for signs that the platform is properly regulated, such as a license from a financial authority.
- Be careful about providing personal information. Never give out your personal information, such as your credit card number or Social Security number, to a website you’re unsure about.
Red Flags About GramFree
Here are some red flags about GramFree:
- GramFree is not a registered business or financial institution. This means that there is no guarantee that you will receive a refund if something goes wrong. In the absence of regulatory oversight, your investments and earnings are exposed to higher risks, with no safeguard against potential fraud.
- GramFree makes outrageous claims about how much money you can make. It is simply not possible to make $500 per hour by completing simple tasks online. Such grandiose promises are a telltale sign of deception and should be met with skepticism, as they prey on the desire for quick and easy wealth.
- GramFree offers referrals and bonuses. This is a common tactic used by scammers to lure people in. The promise of referral bonuses often masks the underlying intention of luring in more victims, feeding into a potential pyramid scheme that benefits early participants at the expense of those who join later.
- GramFree has received numerous negative reviews online. Many people have complained that they were unable to withdraw their earnings or that their accounts were suspended without warning. The abundance of negative feedback should serve as a clear warning, highlighting the high probability of facing difficulties and losses if you engage with GramFree.
- Lack of Regulation: The fact that GramFree is not a registered business or financial institution is a significant issue. This lack of official oversight means that there are no legal protections in place for users, making it highly risky to invest time or money into the platform. In the event of any issues or disputes, recourse may not be available.
- Unrealistic Earning Claims: The claims made by GramFree regarding potential earnings are undeniably extravagant. Promises of earning substantial amounts in a short period through simple online tasks should raise immediate suspicion. Making $500 per hour, as suggested, is simply not achievable through legitimate means.
- Referral and Bonus Programs: Offering referral and bonus programs is a classic strategy used by scammers to attract unsuspecting individuals. These tactics often involve encouraging users to recruit friends and family, creating a network effect that benefits the scammers. Such programs can be a key component of pyramid schemes.
- Negative Online Reviews: Numerous negative reviews and complaints about GramFree can be easily found online. Many users have shared their frustrating experiences, citing difficulties in withdrawing their earnings or, in some cases, having their accounts suspended abruptly without prior notice or explanation. These testimonials serve as cautionary tales for potential users.
Protect Your Online Activities With VPN Services
In today’s digital landscape, online security is paramount. To safeguard your personal information and online activities, it’s essential to use a reliable VPN service.
A VPN service not only ensures your privacy but also allows you to access geo-restricted websites and content. Encrypting your internet connection shields your data from prying eyes and potential threats.
Secure your online ventures and explore money-making websites with confidence by using the best VPN, a valuable tool for staying anonymous and secure in the online world.
Check out the recommended VPNs below:
Regulated Investments
If you’re interested in cryptocurrency investments, it’s crucial to choose reputable and regulated platforms to ensure your financial safety.
Coinbase and Binance are two leading cryptocurrency exchanges, recognized for their transparency, security, and adherence to regulatory standards.
By using these platforms, you can invest in cryptocurrencies with confidence, knowing that your assets are protected and your transactions are conducted securely.
Avoid unnecessary risks with unregulated platforms – opt for Coinbase or Binance to make secure and informed investments in the digital currency world.
READ ALSO: 5 Ways To Identify Phishing Or Fake Websites
Are There Better Alternatives To GramFree?
Absolutely, there are many better alternatives to GramFree that offer legitimate ways to earn money online without the risks and red flags associated with it.
Here are a few options to consider:
1. Freelancing Platforms: Sites like Upwork, Fiverr, and Freelancer connect you with clients who need your skills in writing, editing, graphic design, programming, and more. You set your rates and control your workload, providing a flexible and potentially lucrative income stream.
2. Content Creation: If you enjoy writing, blogging, or creating videos, platforms like YouTube, Medium, and Substack allow you to build an audience and monetize your content through advertising, sponsorships, or direct fan support.
3. Online Surveys and Microtasks: Websites like Swagbucks, Prolific, and Amazon Mechanical Turk offer small tasks like completing surveys, transcribing audio, or testing websites for a few cents each. While the earnings might be modest, they can add up over time, especially if you’re diligent.
4. Online Tutoring and Teaching: If you have expertise in a particular subject, platforms like VIPKid, Cambly, and TutorMe connect you with students who need online tutoring or language lessons. This can be a rewarding way to share your knowledge and earn a good income.
Remember, the key is to choose an alternative that aligns with your skills, interests, and available time. Don’t be lured by promises of quick riches; always thoroughly research any platform before investing your time or effort.
READ ALSO: High Risk, High Labor: Why Scaffolders Cannot Pass Over Insurance
Conclusion – Is GramFree Scam? Is GramFree Legit?
Based on the information above, it is clear that GramFree is a scam. I would advise you to avoid this platform and redirect your energy to other online businesses or freelancing opportunities.
Although GramFree is a legitimate website, and you may see numerous positive reviews online, it is ultimately a complete waste of time, energy, and resources.
Making a profit by tricking or exploiting users is GramFree’s main tactic, which is the definition of a scam.
I would advise you to redirect your energy into other online businesses or freelancing opportunities.
Kindly share this article with your colleagues online who might be interested in knowing an answer to the question, ‘Is GramFree legit? Is GramFree scam?’
INTERESTING POSTS
- 7 Business Credit Card Tips For Small Businesses
- Cryptocurrency Payment: Pros And Cons
- Is ZoanCash Legit Or A Scam? [Unbiased ANSWER]
- Difference Between Bitcoin And Bitcoin Cash – Which Is Safer?
- Kinguin Review – Is It Safe, Legit, Or Scam?
- How To Get Started On Forex Trading
- Best Paid Antivirus According To Reddit Users
- Is Africgold Legit Or A Scam? [Here’s The Answer]
- Is CDKeys Legit Or Scam? [Unbiased Answer]
- Is DHgate Legit And Safe? [Here’s The Answer]
- Is Farfetch Legit Or A Scam Website? [Here’s The Answer]


![Is GramFree Legit Or A Scam? [Unbiased Answer] Is GramFree Legit Or A Scam? [Unbiased Answer]](https://secureblitz.com/wp-content/uploads/2022/04/Is-GramFree-Legit-Or-A-Scam-Unbiased-Answer-768x345.webp)


































![Mozilla Firefox Set to Launch a New VPN [OLD NEWS] Mozilla Firefox Set to Launch a New VPN [OLD NEWS]](https://secureblitz.com/wp-content/uploads/2019/12/firefox-new-vpn-768x512.jpg)