Is Surfshark Antivirus for Mac worth it? Read on to find out…
Mac computers are famous for having solid protections, stronger than Windows in particular. As a result, most Mac users conclude their device cannot suffer a virus or malware attack. But that’s a wrong consensus.
More than 60% of Mac computers suffer a virus infection. On average, each user has five infected files. Also, about 6,000 new malware, capable of infecting Mac systems, are released monthly. These stats confirm that, if you own a Mac laptop, investing in a quality antivirus is worthwhile.
We’ve found many antivirus solutions optimized for Mac computers. But the Surfshark Antivirus is one of interest. So, we took our time to register and try the app to see if it’s worth your money. Read on to uncover our findings.
Now, let me answer the question – Is Surfshark Antivirus for Mac worth it?
Table of Contents
Is Surfshark Antivirus For Mac Worth It?
Yes, Surfshark Antivirus for Mac is worth it. It is reliable in fighting off viruses and malware, including zero-day threats. Yet, it doesn’t slow down your device in any way.
The software allows multiple options for scanning, including real-time, scheduled, and manual. This ensures you can protect your device in various ways. To add, there’s cloud scanning that guarantees in-depth analysis of unknown files.
How about the downsides? Some users don’t appreciate that you can’t get the antivirus as a standalone software. It comes with Surfshark One. Typically, the pricing would be lower if it were a standalone solution.
However, in a way, it’s an advantage if the pricing doesn’t inconvenience you. The other solutions in the Surfshark One bundle are also helpful regarding cybersecurity. Since the upsides carry more weight than the downsides, we conclude that Surfshark Antivirus for Mac is worth it.
An Overview of Surfshark Antivirus For Mac
Surfshark Antivirus supports three primary devices: Windows, Android, and Mac. Typically, it’s more popular among Windows and Android users.
However, Mac computer owners who tried the solution confirm its dependable. That’s what drew our interest to review the software.
From the homepage, Surfshark promises a lightweight antivirus. An antivirus that can halt vast viruses and malware types, both old and new. Also, the software is described as “easy to use.”
The thing is, many antivirus solutions promise all these and turn out to be unreliable. So, we couldn’t just take Surfshark’s word for it. We had to use the tool first-hand and record our experience.
Before registering to try out the antivirus, we first analyzed ratings on top review websites. On G2, Surfshark scores 4.1 out of 5 stars:
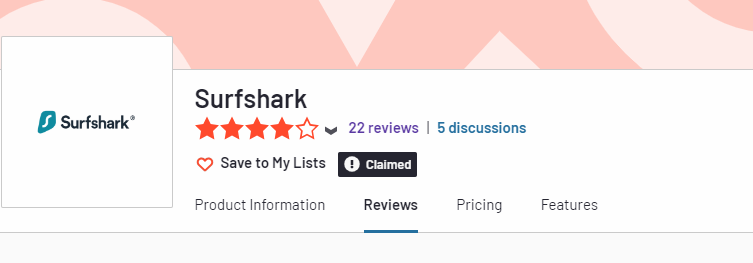
However, the count is just 22 reviews, so we weren’t completely convinced.
Next, we checked Trustpilot – arguably the number one software review platform on the web. Surfshark scores 4.5 stars out of 5 on Trustpilot, which is much more impressive:
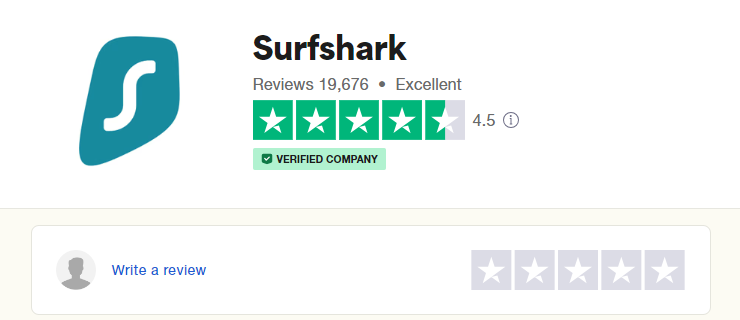
And the ratings were from over 19,600 users, a more significant number than on G2. If close to 20,000 users attest a solution is “Excellent” on Trustpilot, such a solution definitely needs attention.
How to Install Surfshark Antivirus For Mac
Downloading and installing the software is the first step to using Surfshark Antivirus. And from our experience, it’s simple to complete.
Downloading Surfshark Antivirus For Mac
You can’t download the software from the official Apple Store. So, visit the official Surfshark Antivirus website. Then, click on the “Available for macOS” option:
Select a location to store the file on your Mac computer and download it. Note that you’re downloading a DMG file. Click on the file and install it.
After installation, launch the Surfshark Antivirus software. The app will ask you to log in, which means you must have an active subscription.
If you don’t, follow the prompts to create one and subscribe. Surfshark requires payment as a new user, as there’s no free trial. However, there’s a money-back guarantee, so your funds are safe.
Activating Surfshark Antivirus for Mac
Typically, an antivirus needs authentication to scan your computer. So, as you launch the Surfshark software, navigate to the Antivirus tab, and select “Open System Preferences:”
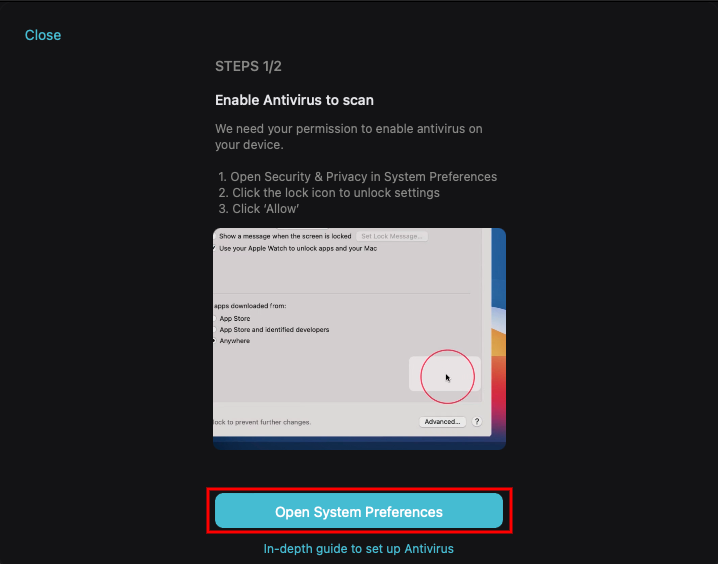
Next, select “Security & Privacy. Switch to the Privacy tab and click on “Full Disk Access.” Then click the Lock icon, which you’ll find at the bottom left:
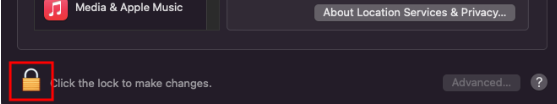
Your system will prompt you to enter your username and password. Once done, the final step is to tick the Surfshark Antivirus option, then click the Lock icon again to apply the changes:
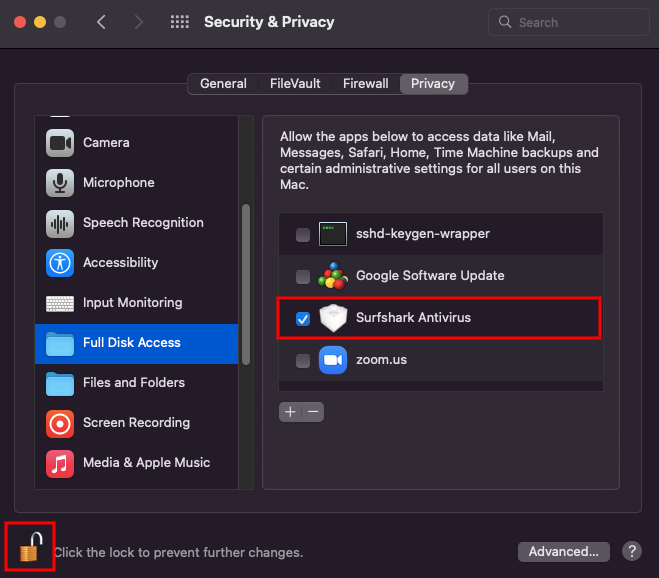
That’s all. Surfshark Antivirus now has full access to protect your Mac device from viruses and malware.
READ ALSO: Is Surfshark One Worth It? [Honest ANSWER]
Surfshark Antivirus For Mac Features
Check out a review of the features we found while using Surfshark Antivirus for Mac below:
Intuitive Interface
Surfshark doesn’t feature a complex dashboard in any of its tools. And this trend exists with the Antivirus solution for Mac devices. The interface is intuitive, such that you can navigate it even if it’s your first time using an antivirus.
Here’s a screenshot of what it looks like:
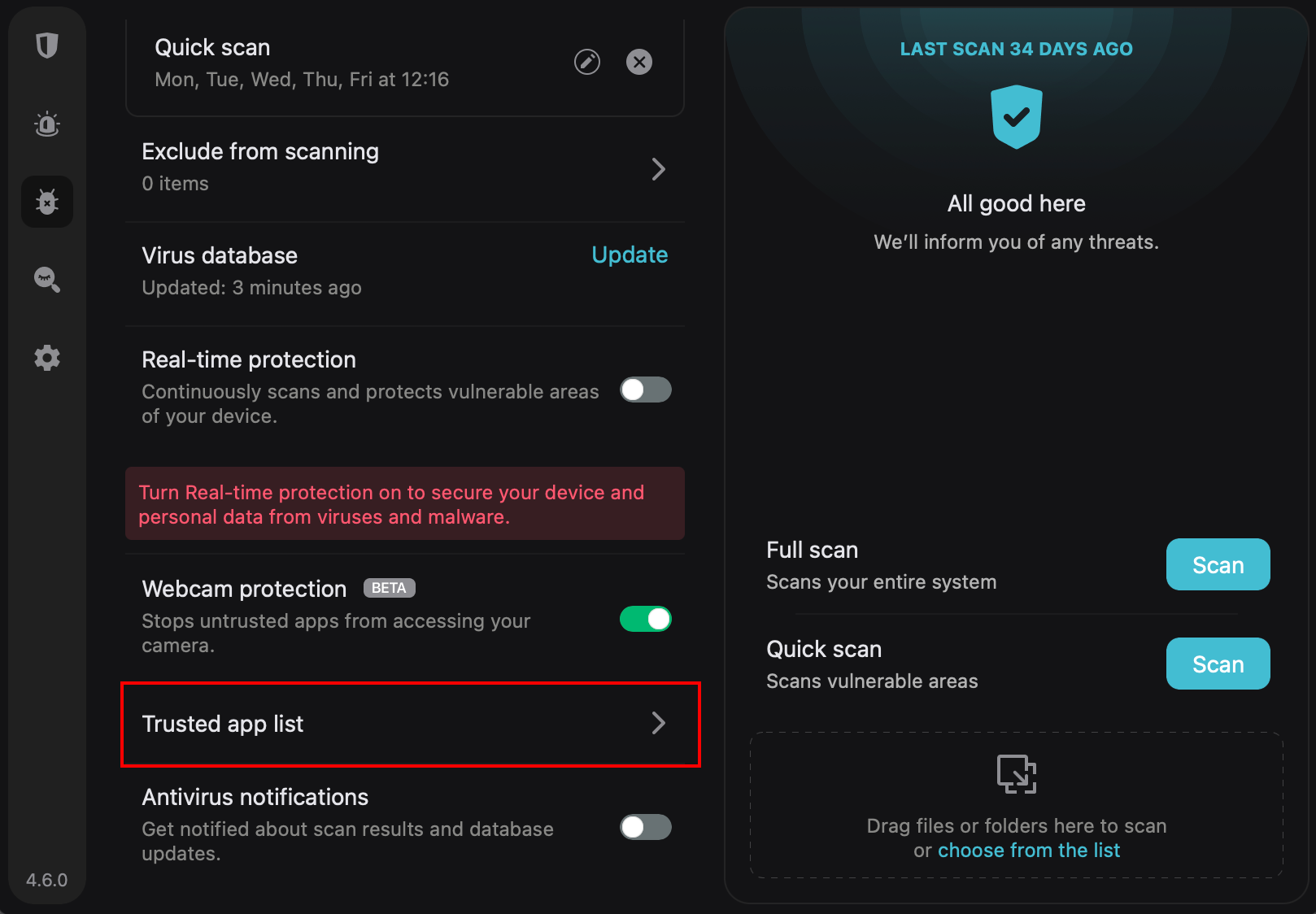
Note that the background conforms to your Mac’s display settings. In other words, you get a dark background — as in the above image — when using dark mode. Otherwise, it’s light.
If you want to perform a scan, you only need to click a corresponding button in the right section of the dashboard. You also get a rundown of your previous scans from the same section.
In addition, you can click the “choose from list option” to scan a particular file or folder. It’s also possible to drag the file and folder into the dashboard. All these confirm the fact that the Surfshark Antivirus is easy to use.
Multiple Protection Options
Different scanning options are available within the Surfshark Antivirus app on Mac. You either initiate a manual, scheduled, or real-time scan. In addition, there’s the Cloud Protect system. Let’s rundown each one.
Manual Scan
This feature lets you check your Mac device for viruses and malware anytime. Launch the tool and select either Full Scan or Quick Scan from the right section:
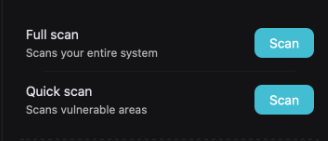
A full scan will check every part of your device. As a result, it’ll usually take time, but from our observations, it’s the most efficient manual scanning option.
Conversely, a quick scan will only check for common vulnerabilities. It doesn’t last more than a few minutes.
Scheduled Scan
Scheduled scans can be full or quick. The difference is that you set it to occur at a future time. You’ll find it at the top of the dashboard:
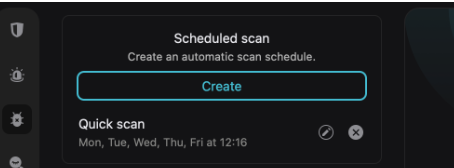
Click Create and select when you want the Antivirus to take action. The save.
We recommend this feature for recurring scanning. For instance, you can schedule Surfshark Antivirus to scan your computer every Monday, Wednesday, or Friday. That way, you’re protected week in and week out.
Real-Time Scans
You can set Surfshark Antivirus to protect your device round the clock with real-time scans. We advise that you activate this option if you use the software. It’s as easy as toggling a bar from your dashboard:
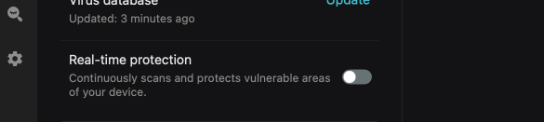
Once activated, the antivirus will scan your device whenever there’s a file change.
For instance, if you download a doc from your email, Surfshark will check for viruses in real time. If it’s vulnerable, the file won’t get into your device.
Cloud Protect Systems
Cloud Protect Systems work mainly for online vulnerabilities. In particular, it keeps you safe from zero-day threats – new malware, which most antivirus software don’t know.
By staying connected to the cloud, Surfshark Antivirus is always informed of the latest vulnerabilities and can shield your device against them.
READ ALSO: Surfshark One vs Surfshark VPN Comparison
Lightweight
The last thing you need is antivirus software lagging your Mac device. You’ll most likely uninstall it, even if it’s the most powerful.
But with Surfshark Antivirus, our tests confirm you don’t have to worry about such. The app is lightweight and doesn’t consume much system resources.
First, the file you install is only 173 MB:
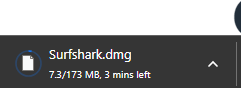
Our checks showed that the Windows version is more lightweight at around 66 MB. Nevertheless, this is expected, considering Mac software files are usually larger than Windows versions.
While we used the Surfshark Antivirus for manual, scheduled, or real-time scans, the Mac PC was never slow. And from the Activity Monitor, we found that the software consumed less than 20% of resources for the most intense scans.
Webcam Protection
Antiviruses often focus only on files and folders. But hackers can skip these elements and attack your Mac device via your camera, your webcam. The risk here is that you become a victim of spies.
As a result, we rate Surfshark Antivirus highly for supporting webcam protection. The feature, like the others, sits in the dashboard:
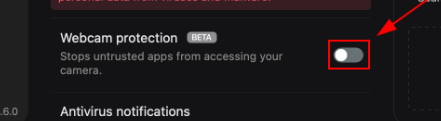
Toggle on the button, and you’re good to go.
Primarily, the feature will block unauthorized Mac apps from accessing your camera. So, it’s up to you to select which apps to grant access to. And you do this via the Trusted app list:
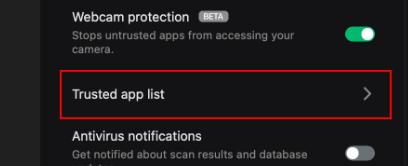
Click the option and select the “Manage app list” option to add trusted software:
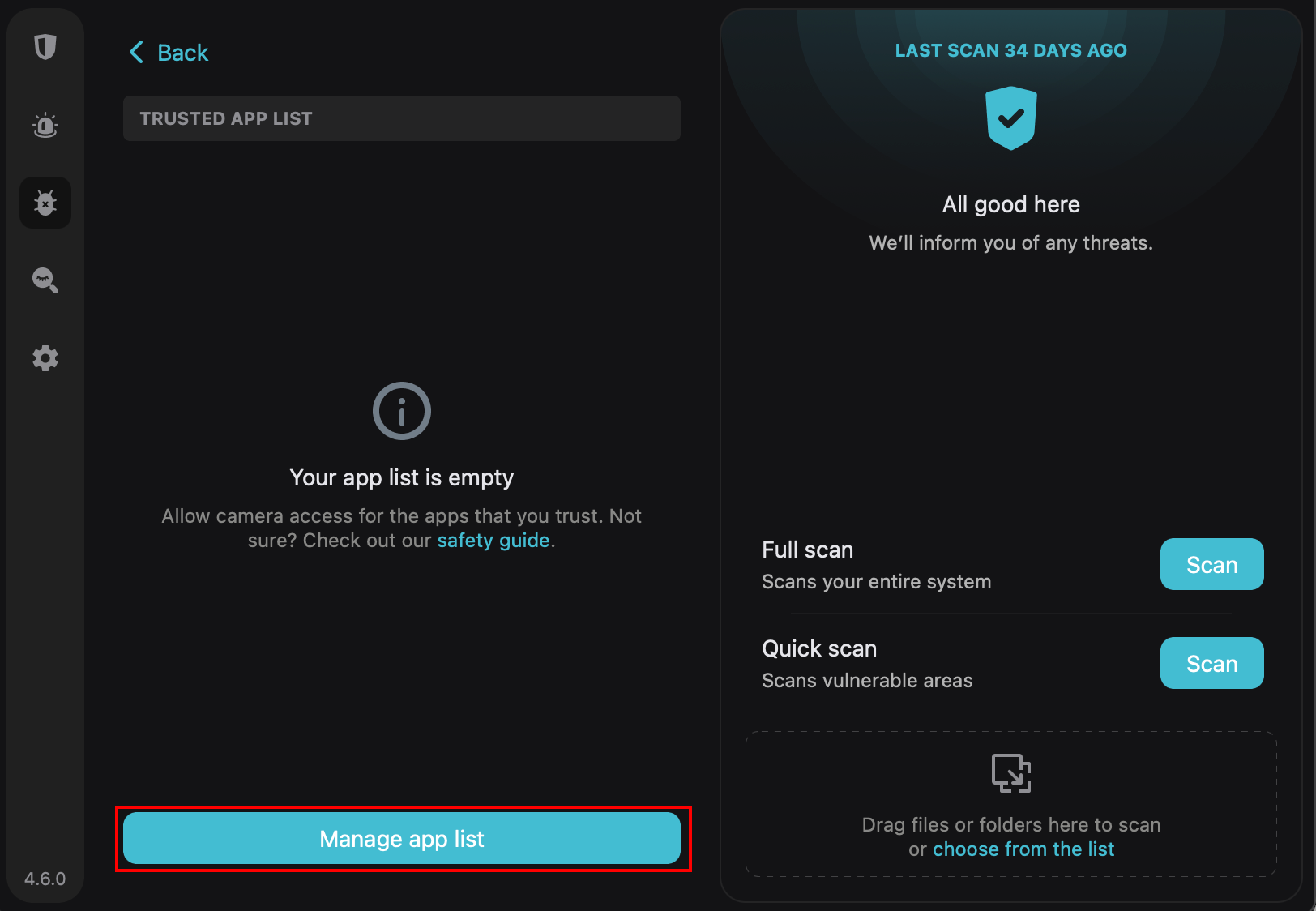
Once done, only programs in the list will be able to activate your camera. You can always edit and update the list when you want.
24/7 Customer Support
We didn’t face many issues using the Surfshark Antivirus for Mac. If there was any unclear feature, we quickly visited the Help Center for an explanation:
Indeed, we found the Help Center helpful, and you will. It features an FAQ section as well:
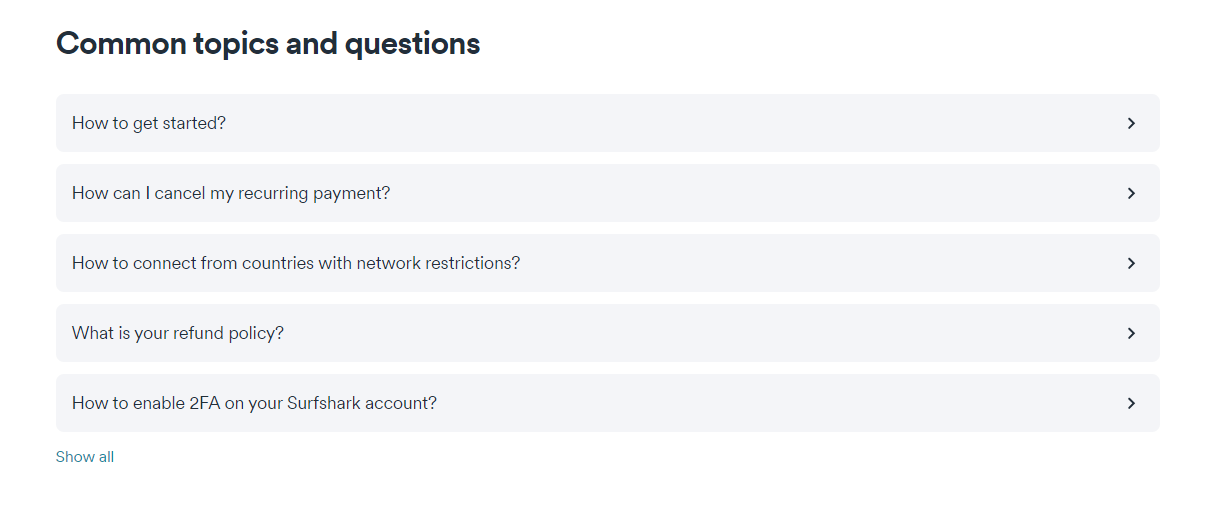
However, if your inquiry demands talking with a support agent, then, you can initiate a live chat. You’ll find the option as you scroll to the bottom in the Help Center:
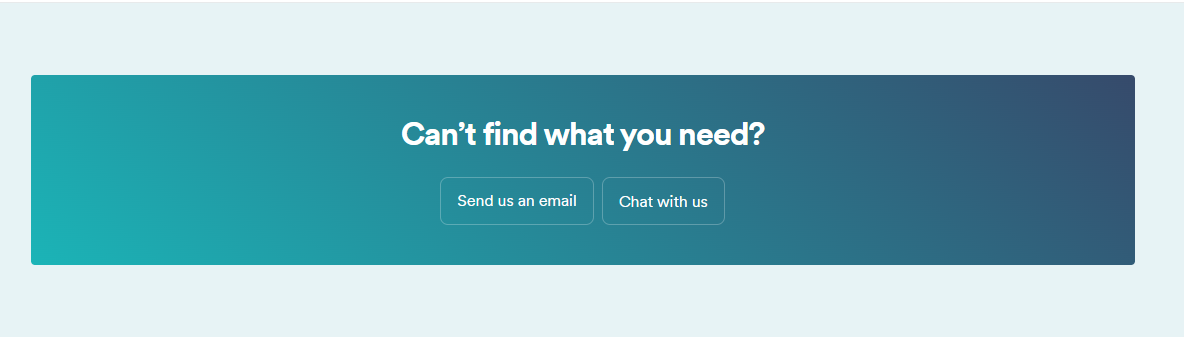
As the image above shows, the Surfshark support team is reachable via email too.
We tested the live chat option to confirm if it’s available 24/7, as Surfshark claims. And it was:
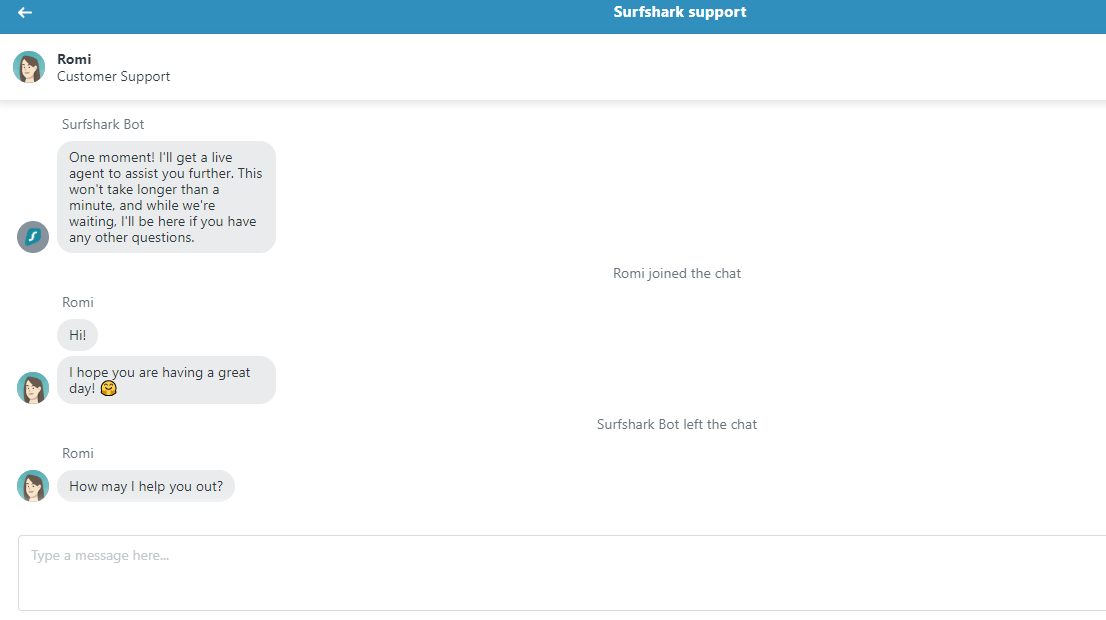
We got connected to a live agent, Romi, within a few minutes.
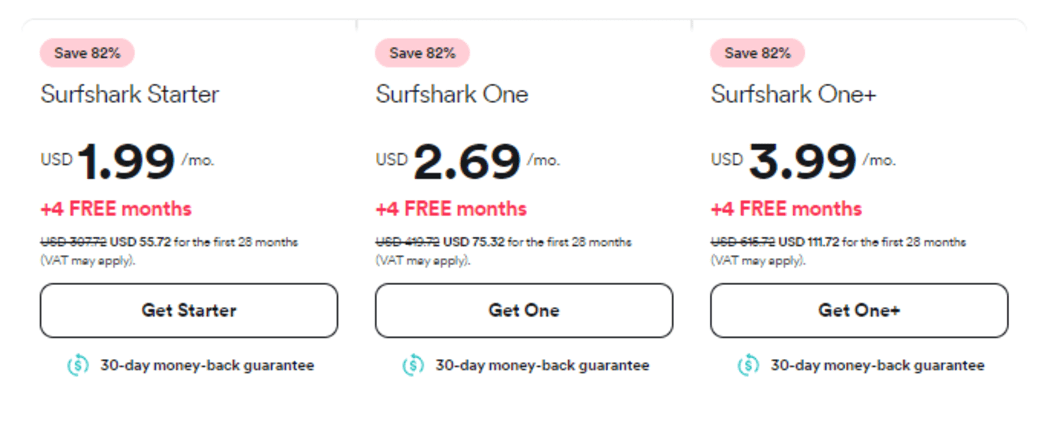
Surfshark Antivirus For Mac Pricing
As mentioned before, Surfshark accommodates no free plan. You have to pay a subscription from the on-set.
Also, the Surfshark Antivirus comes as part of the Surfshark One Suite. This means you can’t purchase the software separately.
You have to get the full suite, and here are the pricing plans:
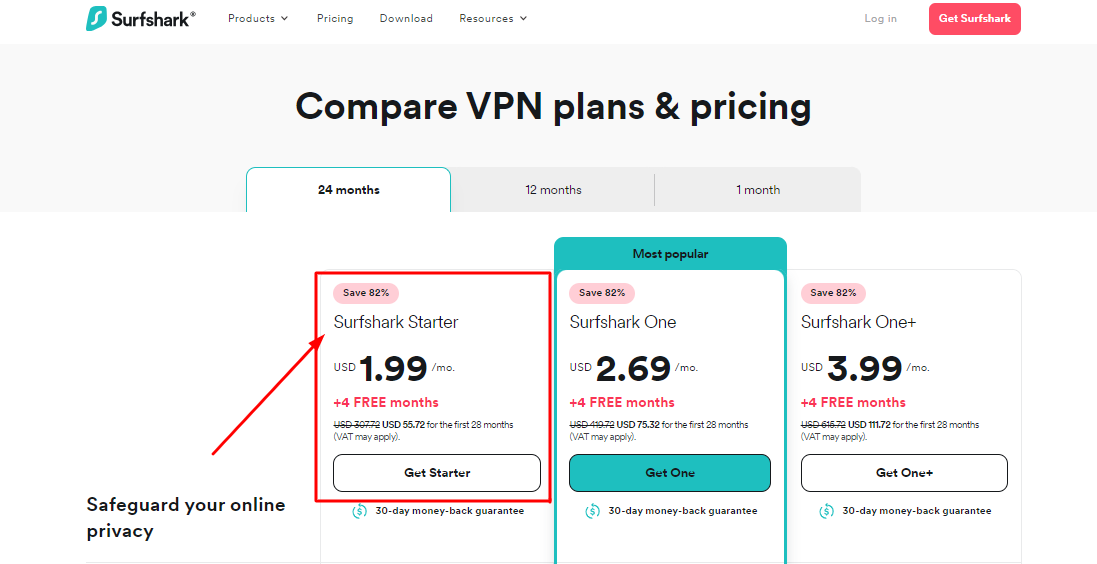
- Monthly Plan: $14.99 per month
- 12-Month Plan: $3.07 per month (plus 4 free months)
- 24 Months Plan: $2.69 per month (plus 4 free months)
If you plan to use the antivirus long term, we recommend the 24-month plan. It’ll run for two years, and you save 82% off the monthly plan. The 12-month option is also ideal, with a 80% discount.
The Surfshark One Connection
Since the Antivirus is a part of the Surfshark One Suite, you’ll get the other programs when you pay. These include the Surfshark Search, Alert, and VPN solutions:
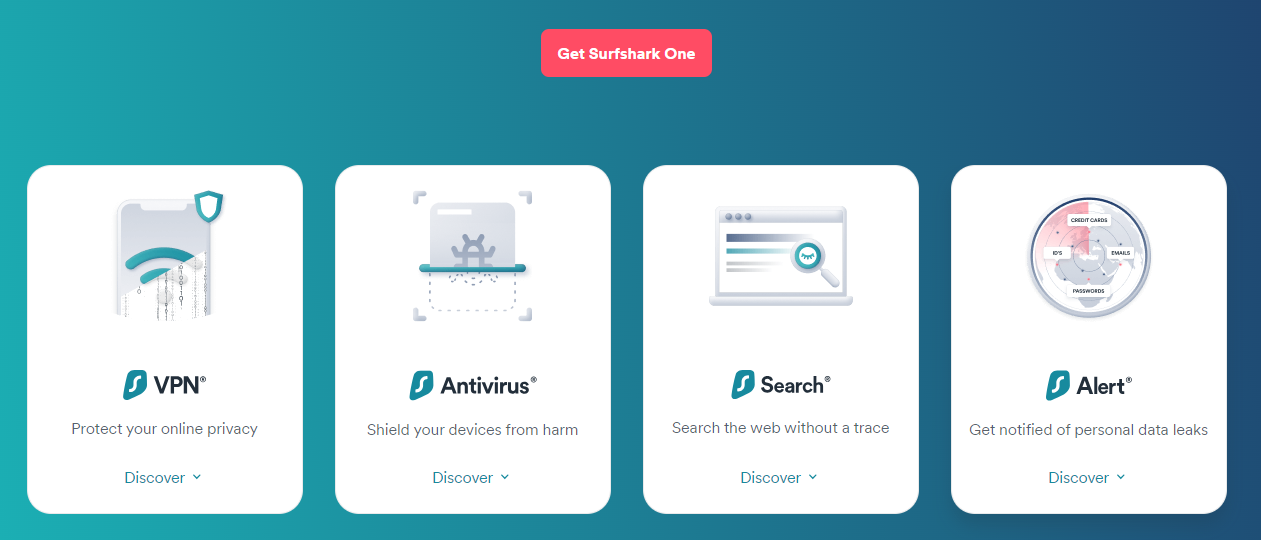
Getting access to these other tools is an advantage, as it means you get more cyber protection. The best part is that each one serves a unique function.
The VPN houses over 3,000 servers, allowing you to surf the web without limitations. You can also stay anonymous online by masking your real IP address. Features like solid encryption, no-logs policy, 2FA, and DNS protection further strengthen the security.
How about the Search tool? Well, it helps you search the web and get authentic results without being subject to trackers and ads. Based on our review, it’s a secure alternative to Google, Bing, Yahoo, and other popular search engines.
Finally, the Alert solution works to prevent data breaches. It’ll notify you if your email, password, credit card details, or ID leaks on the web. Then, you can take action to protect your personal data.
Surfshark Antivirus For Mac Pros
- Intuitive dashboard
- Lightweight software
- Manual and scheduled scans
- Real-time protection
- Webcam protection
- 24/7 customer support
Surfshark Antivirus For Mac Cons
- Not available in the Apple App Store
- Webcam protection is still in beta mode
Bottom Line
Considering the features covered in this post, Surfshark Antivirus offers many benefits for Mac users.
Download the Surfshark Antivirus if you need a solution to safeguard your device from malware. As we answered the question – Is Surfshark Antivirus for Mac worth it? You can see that our review confirms the software is worth purchasing and using.
You can leverage the multiple scanning options to stop all virus traces and employ the other Surfshark tools for optimal protection.
INTERESTING POSTS


![Is Surfshark Antivirus For Mac Worth It? [Here’s the ANSWER] Is Surfshark Antivirus For Mac Worth It? [Here’s the ANSWER]](https://secureblitz.com/wp-content/uploads/2024/01/Is-Surfshark-Antivirus-For-Mac-Worth-It-Heres-the-ANSWER-768x402.jpg)