Here is the Heimdal Security review. Are you seeking a security solution to safeguard your device against the numerous online threats? I was once in the same position myself. And truthfully, the many solutions available can be overwhelming, making it challenging to settle on one.
After many searches, I came across Heimdal Security and tried the software. The initial interest stemmed from the software’s promise of complete protection from all cybersecurity threats. In this post, I’ll share my first-hand experience using Heimdal Security.
So, if you’re like me and considering a versatile cybersecurity solution, this Heimdal Security review will be helpful. Ultimately, you’ll learn about its features, pricing, and how it compares to some alternatives.
Let’s get into the Heimdal Security review.
Table of Contents
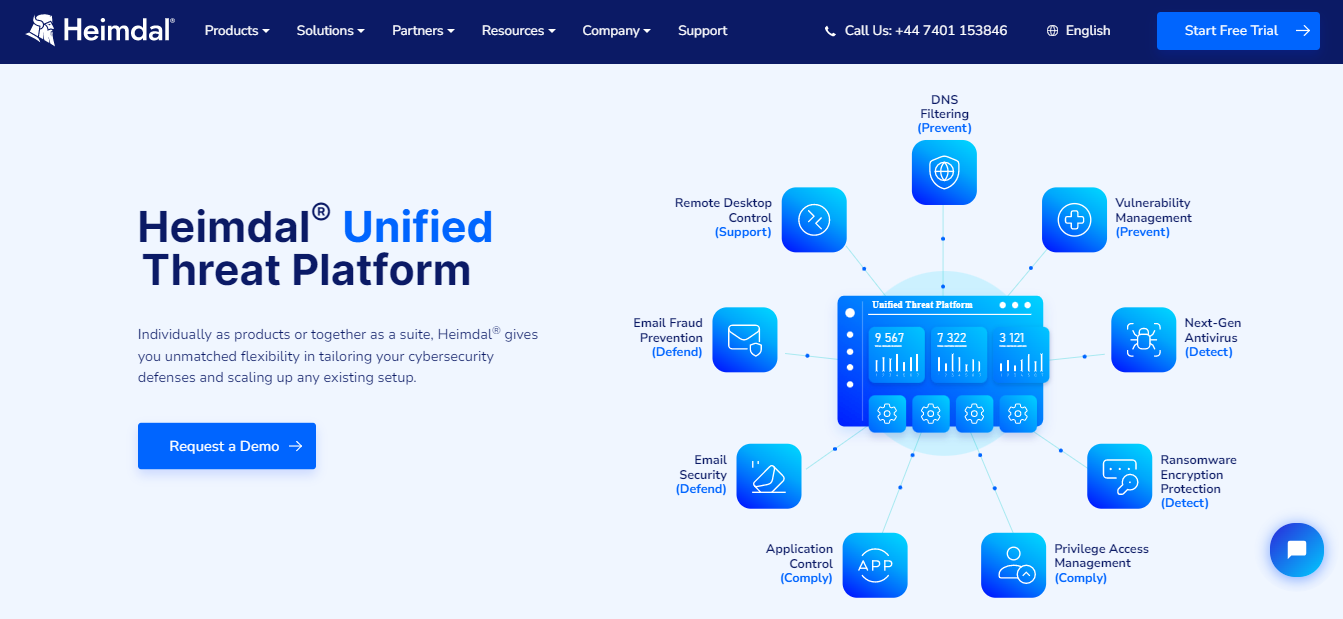
What Is Heimdal Security?
Heimdal Security is a device protection solution. It has a comprehensive, unified threat platform to defend your devices from several cybersecurity harms. In particular, the unified threat platform includes the following:
- Email fraud protection
- DNS filtering
- Remote desktop control
- Next-Gen antivirus
- Ransomware encryption protection
- DNS filtering
We’ll subsequently discuss most of these features and my experience using them in detail. Besides the unified threat protection system, Heimdal includes Patch & Asset Management and Admin Rights Management. These are advanced features you’ll appreciate if you’re an enterprise user.
It’s worth noting that Heimdal boasts more than 10,000 business users. The number of individual users is even higher, which is a testament to the platform’s reliability.
Furthermore, top platforms like Trustpilot, Capterra, G2 Crowd, and even Reddit highly rate Heimdal Security solutions.
All of these were influential in my decision to use Heimdal Security.
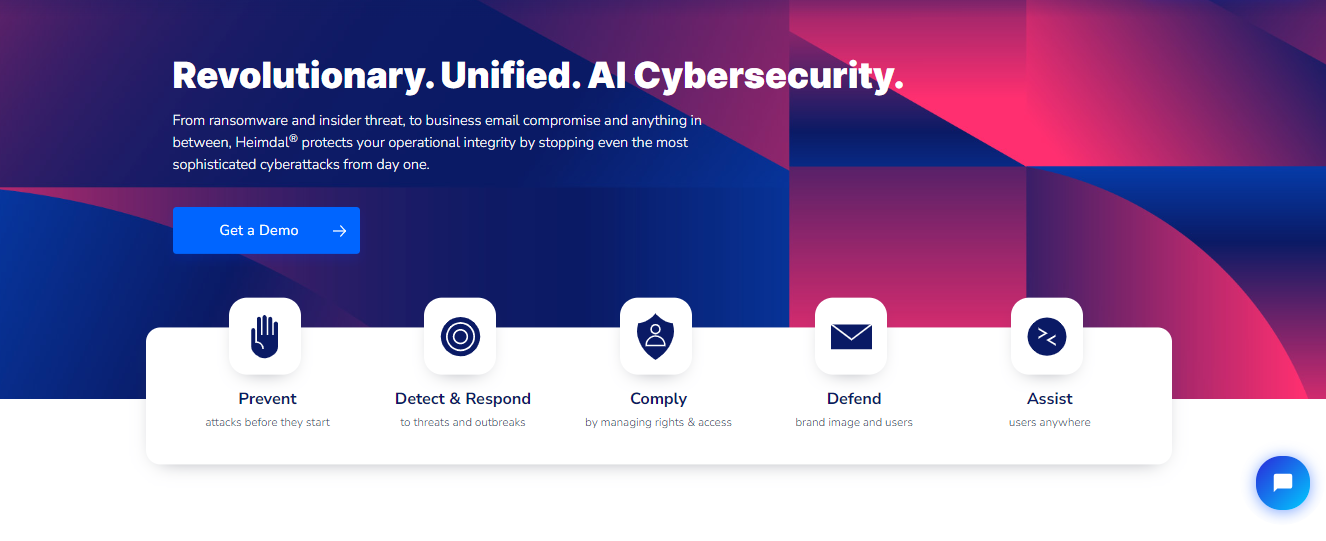
In my experience, the protection software employs a five-step approach to cybersecurity. These include:
- Prevent: First, the software aims to stop attacks before they manifest.
- Detect and Respond: Suppose cyber threats have already penetrated your device. In that case, Heimdal Security will detect and attend to the associated files accordingly.
- Comply: While fighting off digital dangers, Heimdal Security always stays on the good side of the law. The tool ensures your rights and access are handled as they should.
- Defend: The Defend approach primarily targets businesses. If you’re one, you can count on Heimdal Security to protect your brand image and customers.
- Assist: whether you’re a business or individual user, you can get help managing your cybersecurity anytime, anywhere.
Heimdal Security started by developing security add-ons for antivirus software. With the widespread success of its add-ons, Heimdal Security decided to upgrade its services to combat the rising incidence of cybercrimes by launching its Thor series.
A traditional antivirus only has a layer of security, but Heimdal stepped up its game by offering an antivirus and a traffic monitoring application in one package.
Heimdal Security has four significant products, namely:
- Heimdal Thor Free
- Heimdal Thor Vigilance
- Heimdal Thor Foresight
- Heimdal Thor Premium
Heimdall Security has two classes for all products, excluding Thor Free – Home (for individuals) and Enterprise (for organizations). Let’s take a brief look at what these products offer.
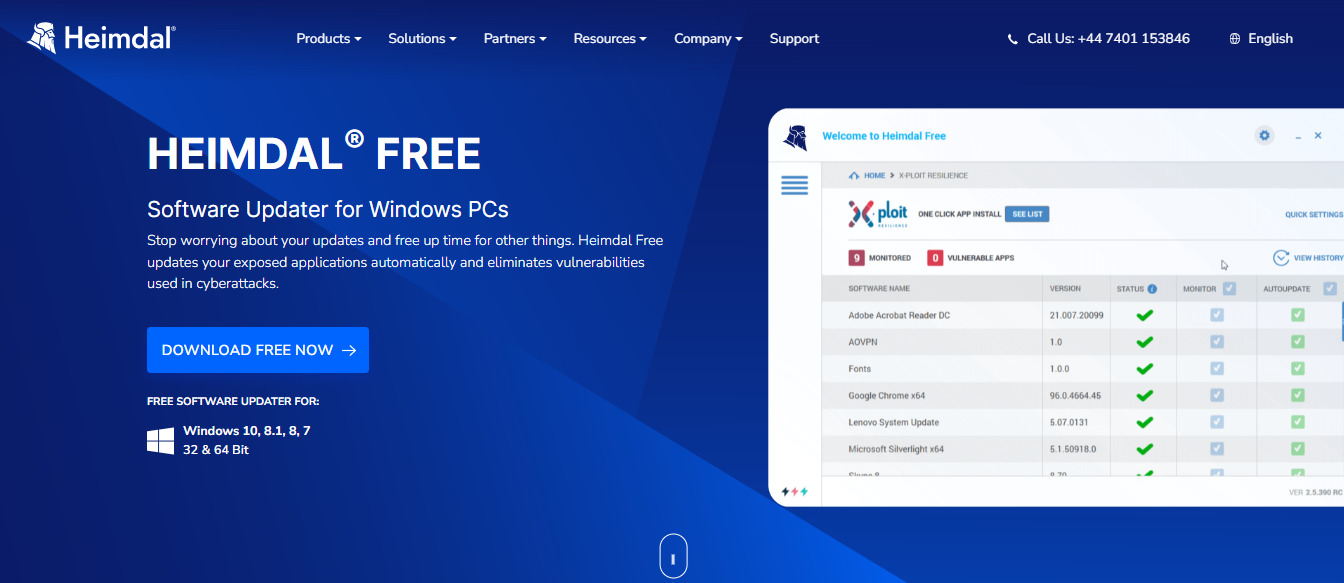
Thor Free
The Thor Free package increases your PC’s security by monitoring and automatically updating outdated applications. Outdated applications are often vulnerable to cyber-attacks; Thor Free helps you update your applications in the background.
It saves you the stress of constantly checking for outdated apps and prevents you from downloading infected updates. Thor Free also provides free and fast installation of popular applications with a single click.
And you guessed right. It’s free to use!
Thor Vigilance
Thor Vigilance is Heimdal’s antivirus system. Thor Vigilance uses some of the most sophisticated malware detection technology to protect you from malware and viruses. It also offers a comprehensive range of scanning options (seven options) that you can find on any antivirus.
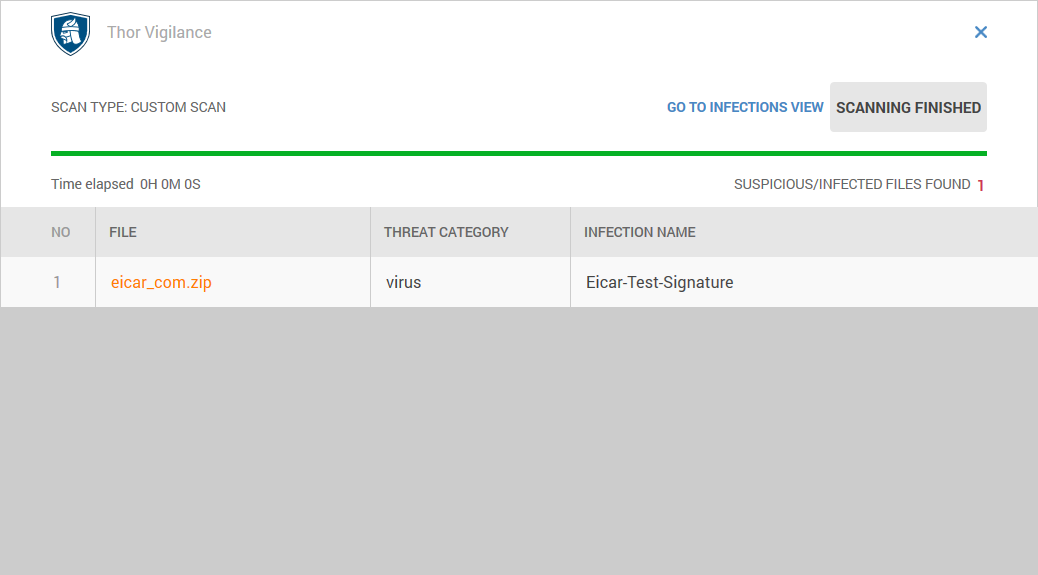
Thor Vigilance utilizes signature code to scan your local files, detecting malware, viruses, data leakage, and other threats. Unknown files are sent to its cloud system for further scanning. It also ensures your firewall is always on to protect you from online threats.
Thanks to Thor Vigilance, home and enterprise users can access next-generation technology absent in regular antivirus applications.
Thor Foresight
Heimdal Security created Thor Foresight as a proactive internet security add-on for antivirus applications. Thor Foresight protects you from cyber-attacks by scanning your internet traffic for malicious content and filtering out cyber threats before they reach your computer.
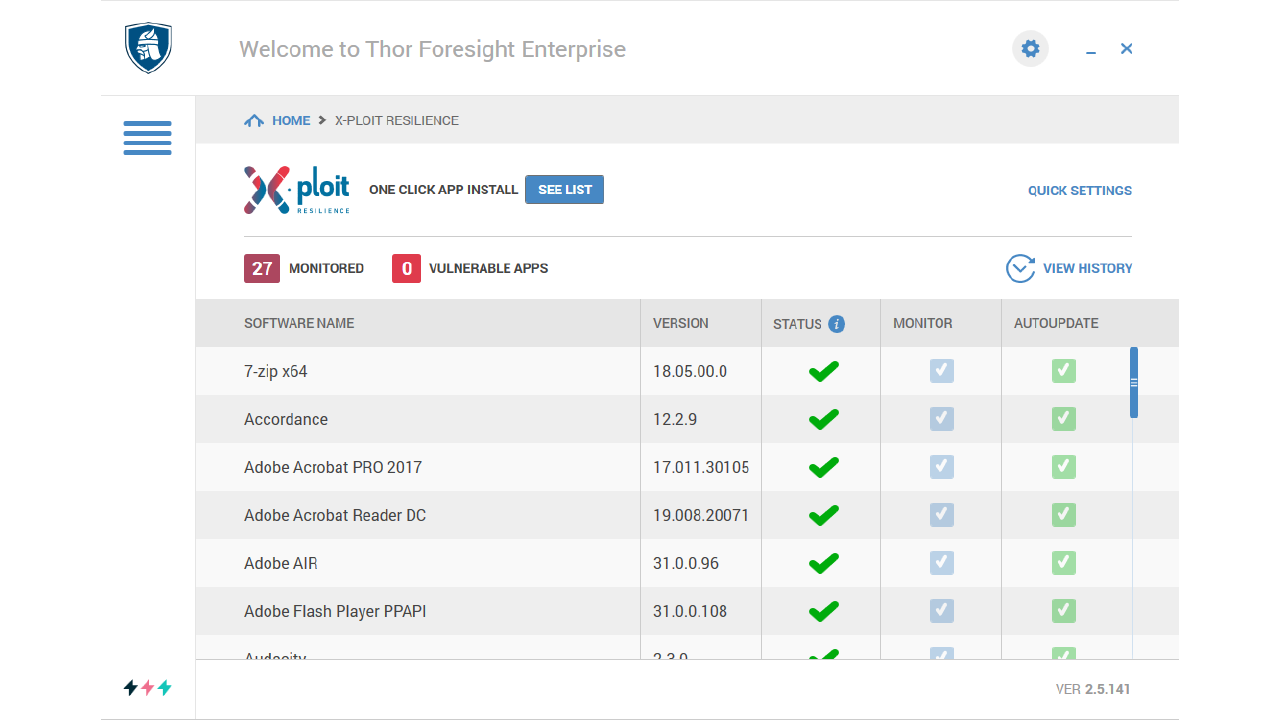
Besides being fully compatible with any antivirus in the market, Thor Foresight provides three layers of protection – Xploit Resilience, VectorN Detection, and Darklayer Guard.
Xploit Resilience is responsible for automatically updating your applications. It also offers Compliance, Vulnerability, and Software Asset Management.
VectorN Detection identifies malware that no Antivirus or Endpoint platform can detect by using Machine Learning Detection.
Darklayer Guard is a two-way traffic filtering engine that blocks network communication at the DNS, HTTP, and HTTPS levels to mitigate Zero-Day exploits, next-generation attacks, Ransomware command-and-control (C&Cs), and data leakages.
This unique product prevents second-generation attacks that no antivirus can detect from reaching your computer. Thor Foresight is available for home and enterprise users.
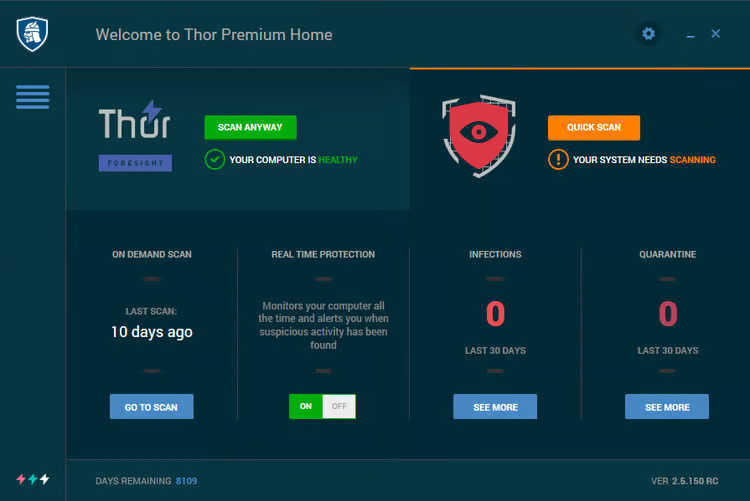
Thor Premium
Thor Premium is the ultimate product in Heimdal Security’s product hierarchy. It’s just as it’s called – Premium. This product contains a combination of Thor Vigilance and Thor Foresight.
Thor Premium is considered one of the best products on the market, providing all-around protection against malware.
While Thor Foresight is a unique product, Thor Vigilance is not the best stand-alone antivirus. However, both products, combined with additional next-generation protection layers in Thor Premium, are highly recommended security solutions you might want to use.
Thor Premium provides you with reactive protection against malware on your local computer, alongside proactive protection to keep threats away from your computer as you browse the internet.
It also patches your installed applications automatically to ensure no window for cyber attacks.
Even though all the products are packed into this supreme product, it is straightforward to use and navigate for beginners.
Let’s now consider how Heimdal Security’s onboarding process weighs up.
Getting Started With Heimdal Security
When you launch the Heimdal website, you can get started by clicking the “Start a free trial” button. Indeed, the platform allows you to open a free account. However, when I registered, the free account version was essentially a demo.
So, if you want to use Heimdal Security, prepare to pay for a complete subscription before you can access most features.
Nevertheless, as a first-time user, you must book a demo with an expert. I recommend it, as it allows you to verify if the solution is right for you. It’s more essential if you’re a business.
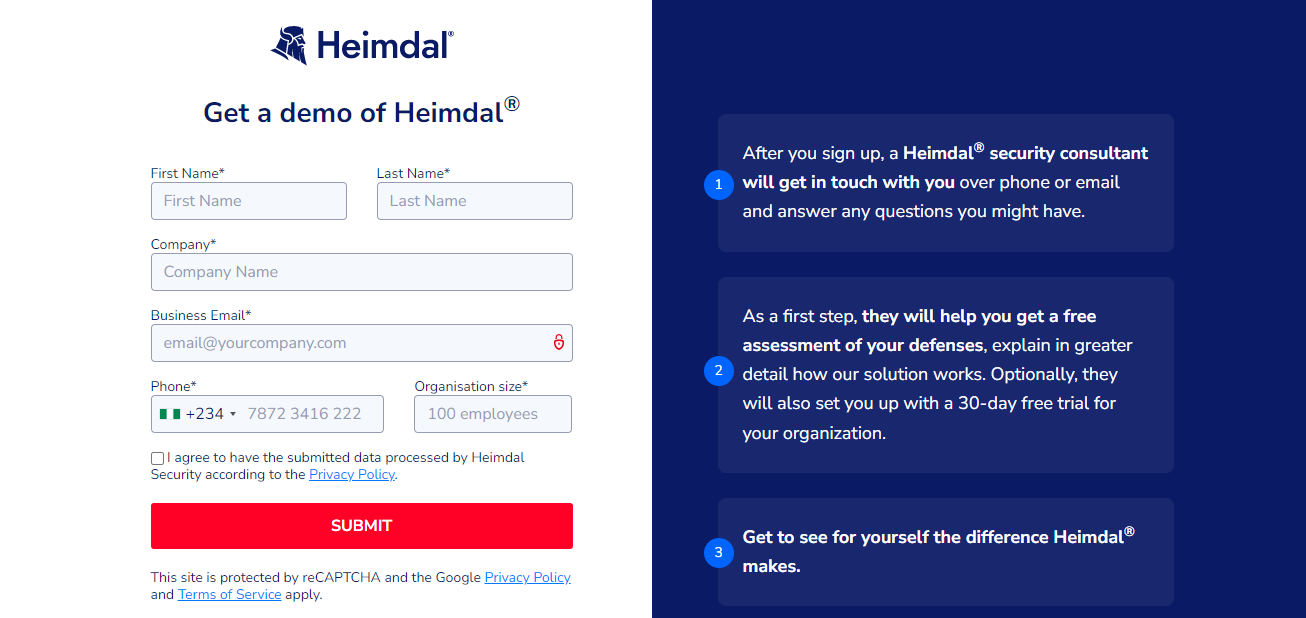
Thankfully, the demo-booking process is as straightforward as I did when writing this Heimdal Security review. You only need to fill out a form, as shown below:
Accordingly, you’ll enter your name, company name, business email, and phone number. You’ll also join the number of workstations with which you aim to use Heimdal Security. This translates to the number of computers you have in your office. Initially, I registered 20 workstations.
After submitting the form, a Heimdal agent will contact you. Subsequently, after the demo, you’ll receive a quote tailored to your business size.
If, from the demo, you recognize that the solution is the best for you, then pay and start using it.
How To Download And Install Heimdal Security
Installing the Heimdal Security app is a straightforward process. Follow the steps below:
- Download the Heimdal Security installer file from the website.
- Run the installer file after downloading. You may get a pop-up if Windows Defender is installed on your PC. If you do, click on “Run anyway” and proceed.
- Accept the installation terms and conditions by clicking on “I agree.”
- Set your preferred language (default is English), and click on “Next.”
- Choose if you want to customize the installation (it’s recommended that you do not), and click “Next.”
- Choose the version of Heimdal Security you want to install: Trial, Free, or Home/Enterprise. If you’ve purchased the tool, select Home/Enterprise, enter your activation key, and click “Activate.”
- Click on “Install” and allow the software to install. Afterward, click on “Finish.”
That’s all; you can start using Heimdal Security on your PC. Ideally, it would be best if you reboot your PC after installation.
Let’s discuss its features to help you understand if Heimdal Security is the solution your business needs.
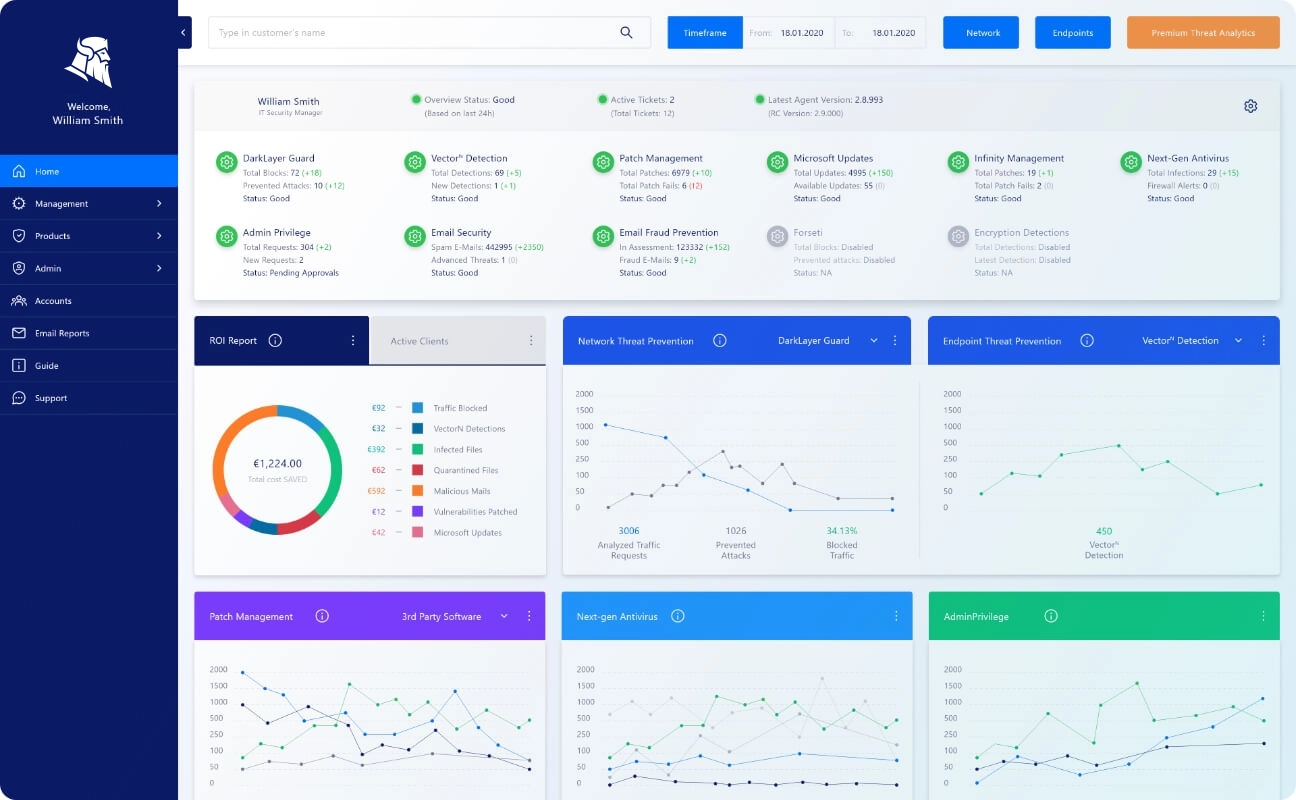
Heimdal Security Features
Check out Heimdal Security’s top features below and what you should expect when you start using the tool:
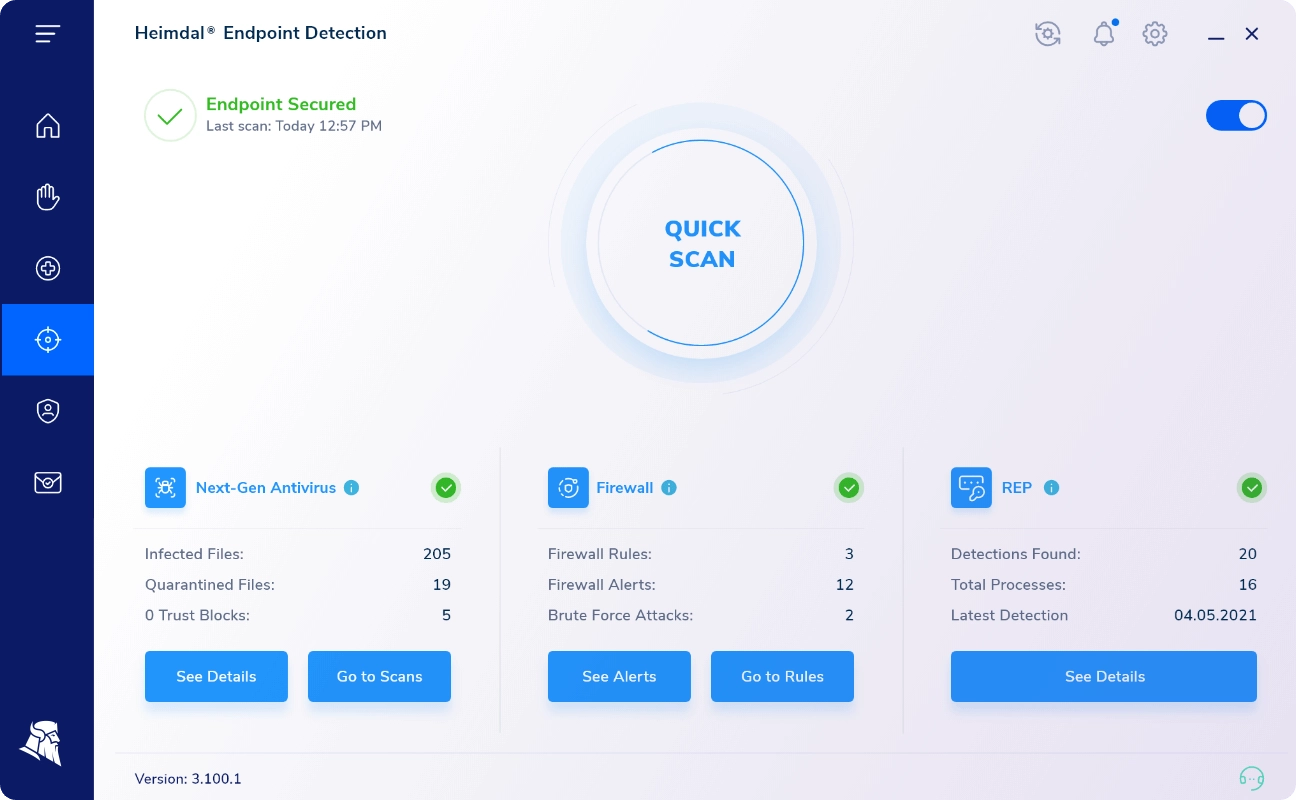
Next-Gen Antivirus
Heimdal Security’s flagship feature is the next-generation antivirus.
In particular, this is a 4-layer malware-fighting solution that works against both old and new threats. Old threats, such as worms and trojans, and new threats, including ransomware and stealth viruses.
The first stage of the antivirus is to compare suspicious files with Heimdal Security’s virus database. This helps uncover whether a file is infected or not. In my experience using the tool, this feature proved helpful, as it allows you to spot corrupted files before they spread.
The software scans the files in stage two using the native Threat Cloud. This is a relatively fast process that uses AI for maximum effectiveness.
Stages three and four are similar. Both ensure no malicious links exist between the corrupted files and other device controls.
Extended Firewall
Also included in the Heimdal next-gen antivirus is a firewall. The firewall doesn’t stand out as a sub-feature of the antivirus. However, after trying it out, I found some aspects worth highlighting.
Notably, what you get with Heimdal Security is a hybrid firewall. Such a firewall type is typically associated with antivirus software or other inspection systems. And it’s comprehensive enough to check every aspect of your network.
The above is possible thanks to support for deep packet analysis. Also known as deep packet inspection (DPI), this feature automatically implements critical actions to protect a computer’s network. These actions include blocking, alerting, re-routing, or logging.
Notably, it saves you time, as you won’t necessarily need to configure the firewall yourself. Furthermore, based on first-hand observations, the firewall is dependable for fending off brute force attacks.
READ ALSO: Your Essential Ransomware Guide: Prevention, Detection, and Recovery
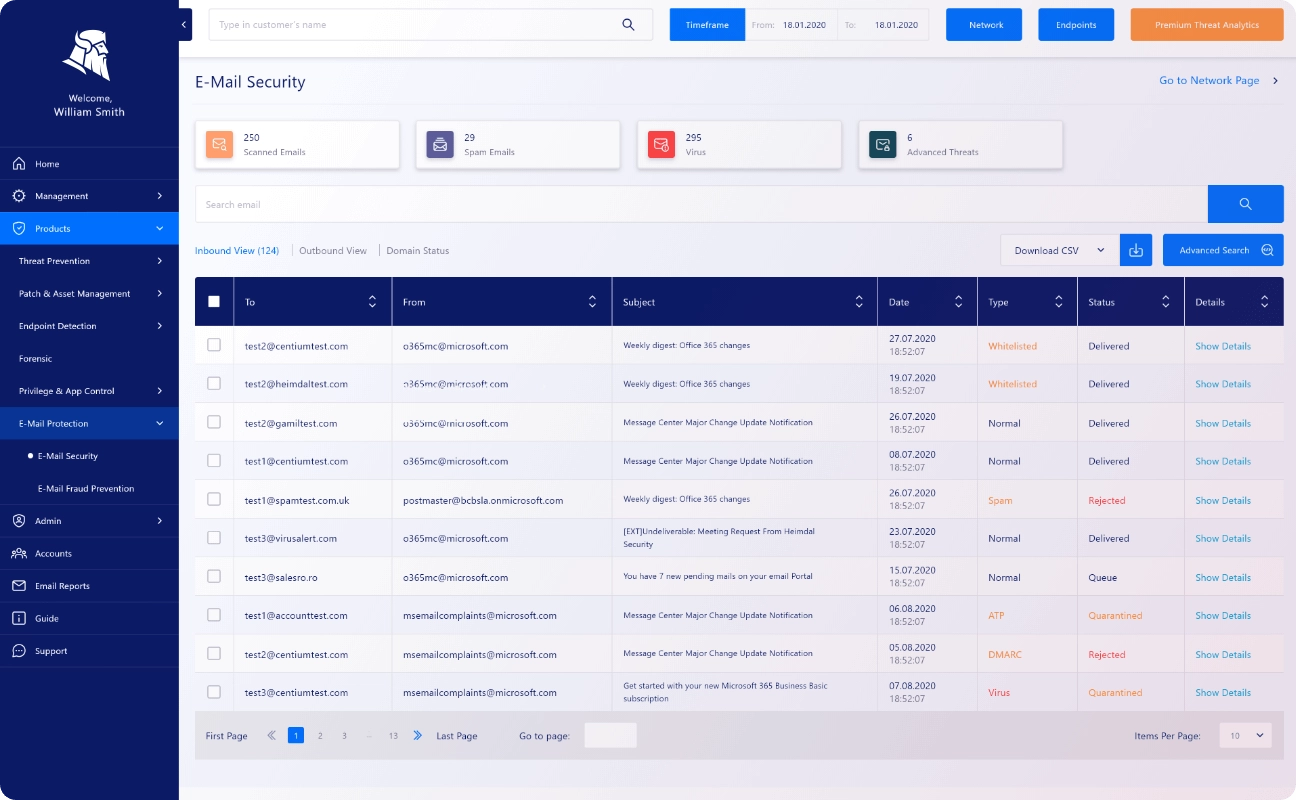
Email Security
Email Security is one of Heimdal Security’s best features for businesses. It stops mail-delivered threats, including malware, malicious URLs, ransomware, and phishing.
Phishing and scam emails remain prevalent among the most common cyber threats. Heimdal Premium Security Home tackles these with a dependable email protection system. It employs live threat intelligence and over 125 vectors of analysis to identify and block malicious emails of any kind.
Drawing from my experience, the feature works in three ways. First, it applies more rigorous spam filters – much more reliable than your email’s default ones. As a result, you’ll hardly get junk mail in your inbox.
The following approach is Full Email Protection. Heimdal Security monitors emails you send and receives any red flags via this medium. If any, it immediately identifies them for you to take action.
The third approach focuses on email attachments. It involves deep-scanning attachments for any malicious content.
With the three-approach protection, you can rest assured that this software gives you prime email security.
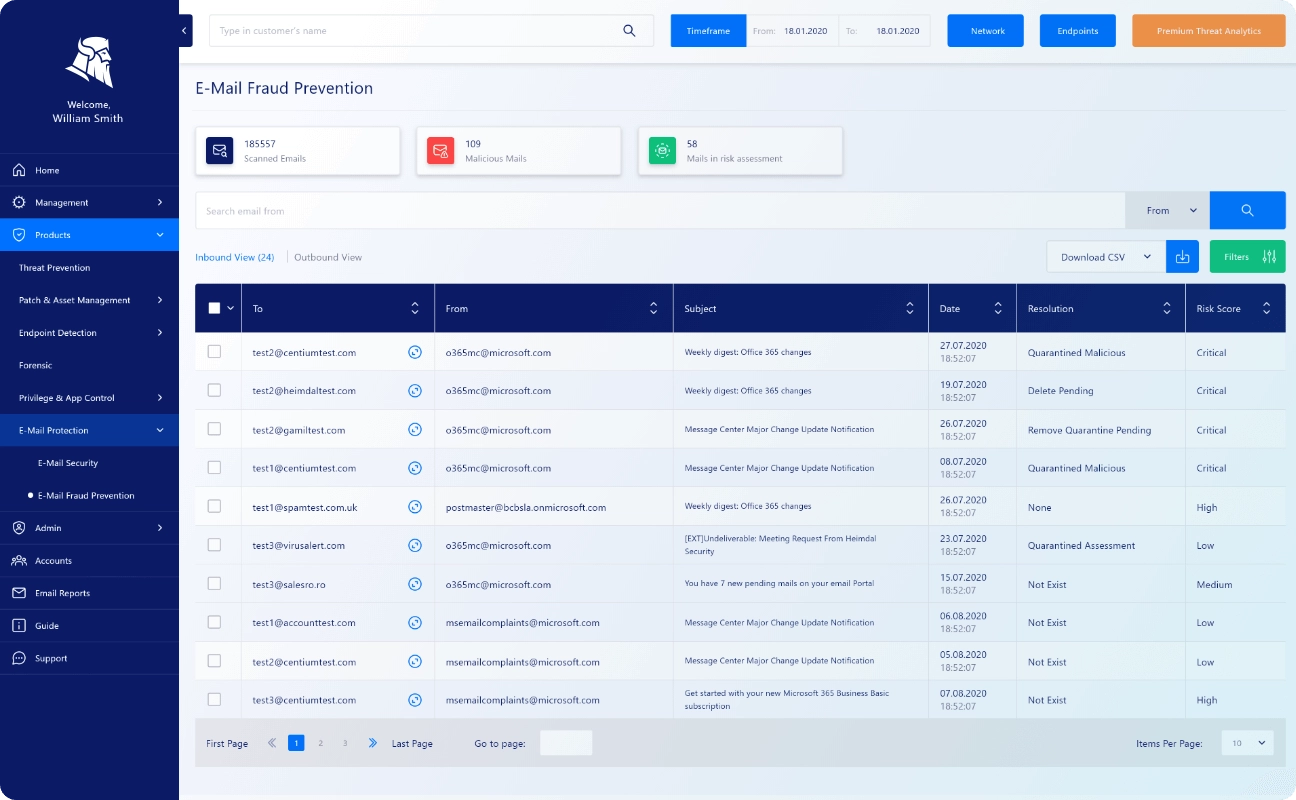
Email Fraud Prevention
In addition to email security, Heimdal offers an exclusive email fraud prevention solution. The option focuses on stopping business email compromise and phishing. It works with the live platform threat intelligence, using data from over 125 analysis vectors.
You get advanced email scanning technology with Heimdal Security’s email fraud prevention. It also supports multiple languages. So, it doesn’t matter how hackers attack; it’ll stop their efforts.
One popular method of email fraud is CEO imposter or impersonation. This is a scenario where a hacker impersonates a company’s CEO and contacts you.
Using Heimdal Security, we confirm that preventing such fraud is straightforward. All in all, it’ll save your business from suffering negative brand impact.
Ransomware Encryption Protection
Ransomware encryption protection forms a core part of Heimdal Security’s endpoint protection. The software includes an antivirus feature that prevents ransomware. However, this option is a more targeted solution for dealing with the specific malware type.
Heimdal Premium Security transcends just virus, malware, and ransomware attacks. With ransomware encryption protection, the software safeguards you against malicious encryption attempts commonly associated with ransomware attacks.
It functions as a high-grade defense system against advanced persistent threats, such as exfiltration and data loss. With incident reports, you can review the full details of every attack.
Based on firsthand observations, this feature effectively counters any ransomware attack. It integrates seamlessly with the antivirus, so both solutions work in harmony.
However, what’s more interesting is that the feature is universally compatible. Universally compatible, it will work with any antivirus, not just that of Heimdal Security.
Furthermore, you get insightful reports occasionally to stay on top of the software’s performance. The report is accessible from the dashboard, and you can filter the metrics or export them as needed.
READ ALSO: How to Protect Your Computer from Ransomware: Essential Security Measures
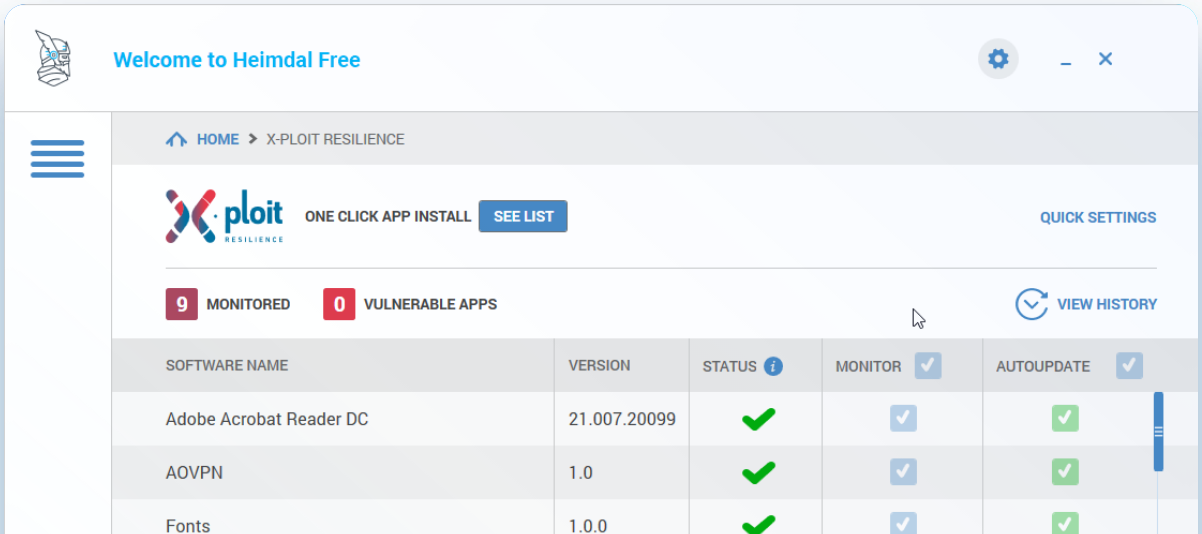
Software Updater
When your installed programs and applications become obsolete, you don’t have to stress about updating them. Heimdal Security includes a software updater you can use at no cost. The updater will monitor your apps and automatically update them the moment a new version is available.
However, please note that this feature is only compatible with Windows PCs. In particular, you can install it using Windows 7 or recent versions. There are also versions for 32-bit and 64-bit variants.
When you install the software updater, you can specify which apps you want it to work on. The software will check each program version every two hours and update accordingly. As you’d expect, for this to work, you must be online.
Remote Desktop
Heimdal Security Remote Desktop is handy for enterprise and business users. It allows you to access and secure devices remotely from anywhere.
This state-of-the-art feature is compatible with Windows, macOS, iOS, and Android devices. Aside from security, Heimdal Security Remote Desktop also works for content sharing and collaboration.
As an enterprise user, you can leverage Heimdal Security’s remote desktop software to manage your devices from anywhere. This feature allows you to transfer files without trouble and record sessions.
Heimdal Security’s remote desktop supports multiple operating systems. When we tested the tool, we used it on Windows and macOS. However, it’ll also work on Android, iOS, and Windows Server.
Furthermore, the feature is ideal for leveraging collaboration. As you remotely manage your devices and files, you can invite others to support you. And when it comes to file sharing, the solution supports all file types.
It’s worth mentioning that the remote security feature is highly secure. It supports multiple encryption methods, including RSA 2048/4096 and AES-256, as well as multi-factor authentication (MFA).
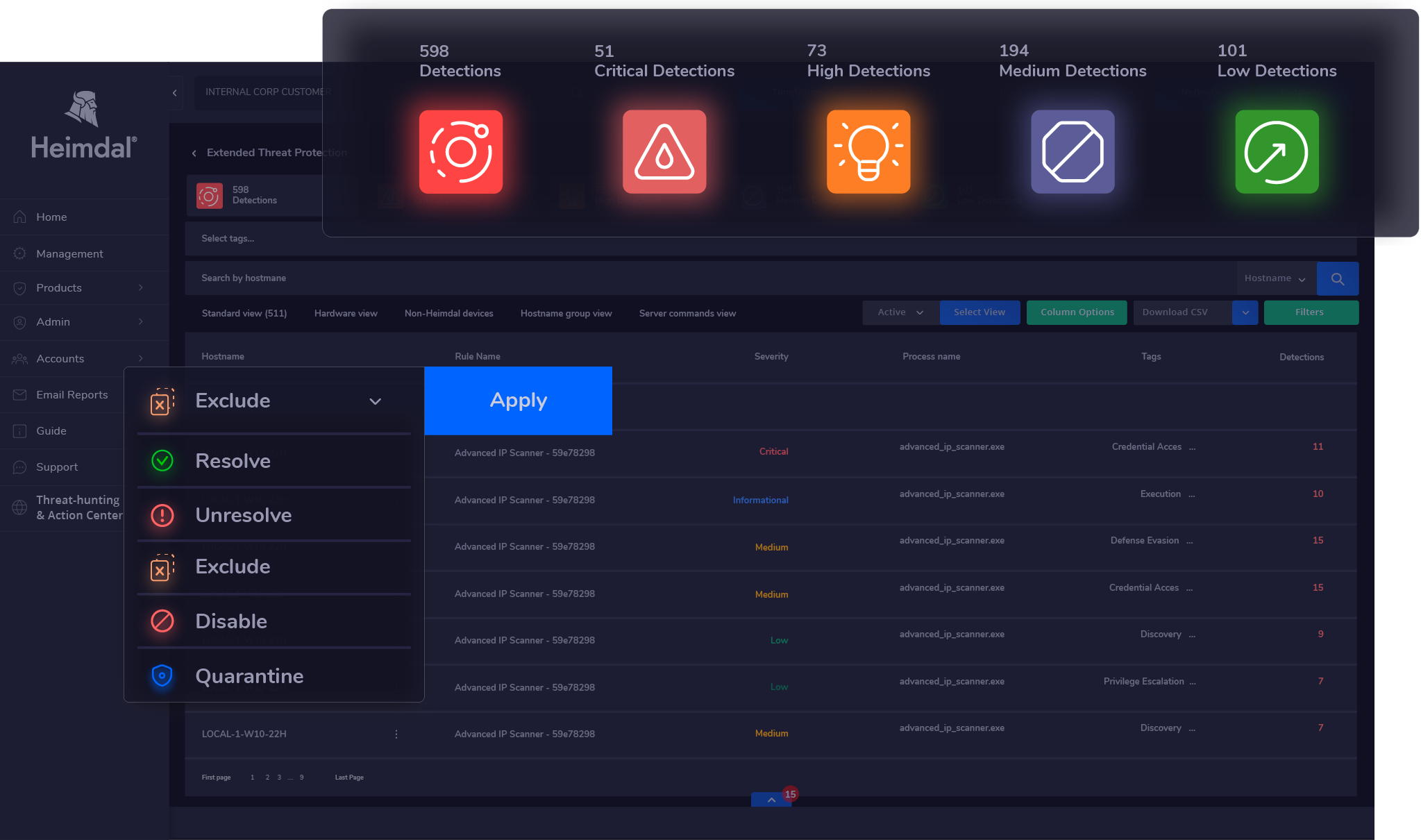
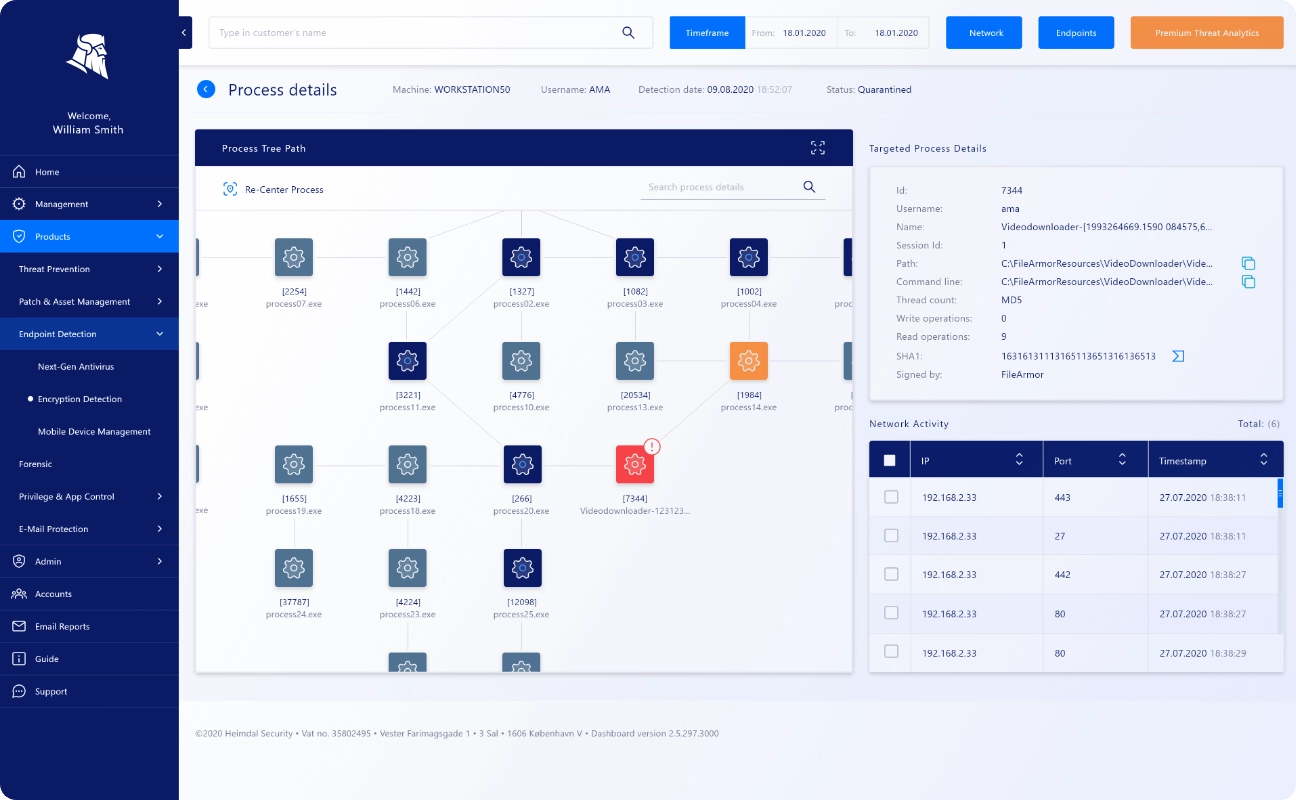
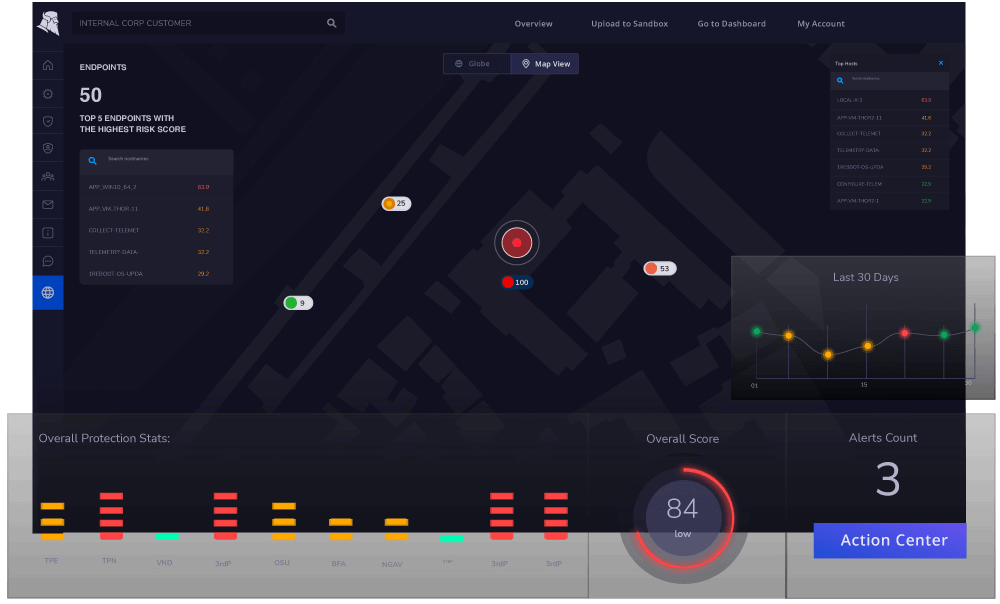
Threat Hunting
Heimdal Security doesn’t sit and wait for viruses and malware to come. According to our findings, you can leverage the software to find and finish malware in its earliest stages. This is possible with the threat-hunting feature.
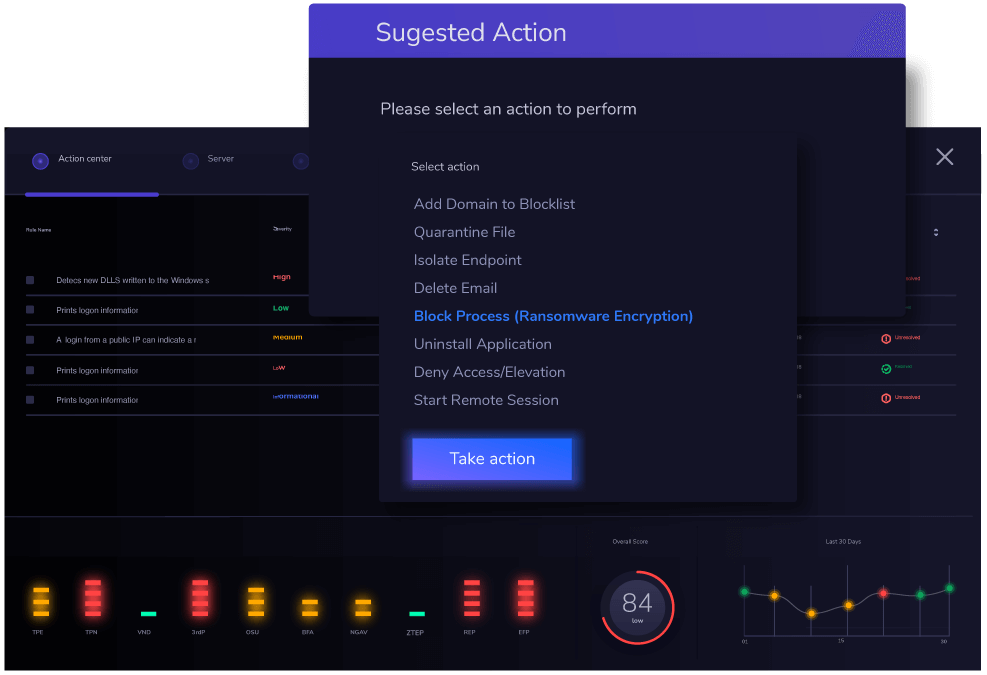
You’ll appreciate using threat hunting as it’s relatively straightforward. You get a single, unified interface, which isn’t complex to navigate. And from there, you can issue any action to combat malware.
One mention-worthy aspect of this feature is enhanced visibility. You get a clear picture of your entire digital landscape as an enterprise. With this, you can easily spot the areas the feature should target.
It’s up to you to specify what action follows when threats are identified. Nevertheless, Heimdal Security offers expert action tips to guide you.
Extended Detection & Response (XDR)
You can’t leave out Extended Detection Response (XDR) when discussing Heimdal Security features. This feature is next-level and revolutionary in the cybersecurity space.
With XDR, you gain more accurate threat detection and faster response times. The feature utilizes artificial intelligence and machine learning to identify and mitigate threats. It’s also less complex to use, yet it uses powerful technologies.
The reports you receive from XDR are well-presented in graphs and charts. Consequently, using the insights to make data-driven decisions becomes easy.
Customer Support
Most Heimdal Security users attest that the company has a staunch, quick-to-respond support team. The support will handle any issues you encounter while using the security solution.
From first-hand experience crafting this Heimdal Security review, we can confirm that the platform has a prompt support service.
You can initiate a quick help session by clicking the live chat button on our website. The live chat is available 24/7, allowing you to use it at any time.
Besides the live chat, you can also call Heimdal Security’s helpline. Another option is to send an email; a third is to submit a support ticket.
However, you can quickly get help from the Heimdal Knowledge Base for most inquiries. The knowledge base is well-detailed, with guides for home, enterprise, and free users. There are FAQs and a troubleshooting guide.
Furthermore, you can get exclusive VIP support as a premium user.
Heimdal Security Pricing
Heimdal Security offers a comprehensive range of cybersecurity solutions. When preparing for his Heimdal Security review, I can say that Heimdal costs around $35 annually.
Heimdal Security has different pricing plans to suit your needs. However, you can try out any of their products for free for 30 days.
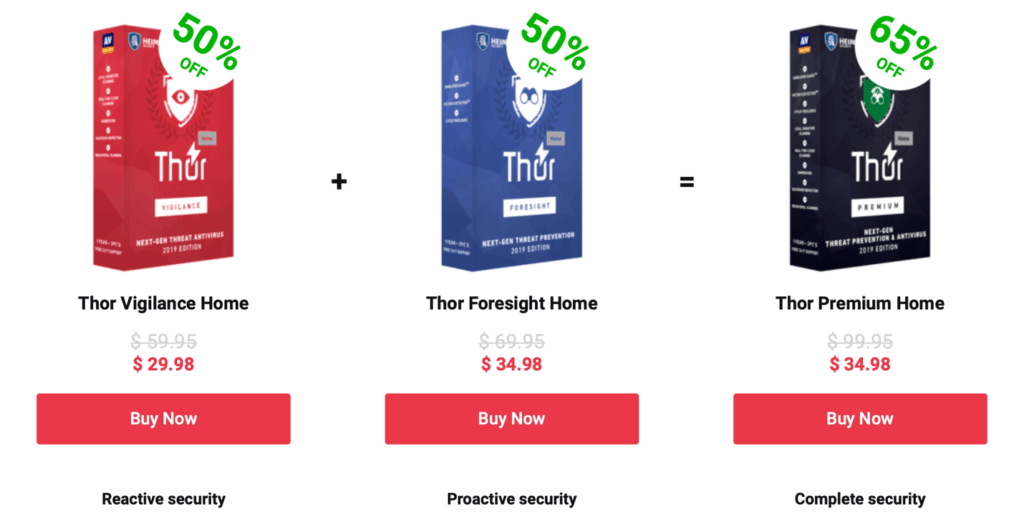
Thor Vigilance: This next-generation antivirus is the cheapest product in the Heimdal Security suite. You can download Thor Vigilance for $49.95 annually if you only need a traditional antivirus.
Thor Foresight: This is a required add-on that complements your antivirus work. If you have viable antivirus software, you can obtain this proactive security add-on for $59.95 per year.
Thor Premium: This ultimate plan offers proactive security from Thor Foresight and reactive security from Thor Vigilance for just $89.95 per year. If you are starting or need a complete security package, this is the plan for you.
Note: These prices are for home users. As a business user, you must register or contact our support team for pricing information.
Please note that you receive a 30-day money-back guarantee with each subscription you purchase. This is ideal as it means your payment is safe. I never needed to request my money back anyway. And if the software works for you as it did for me, you won’t need to either.
Furthermore, in my experience, Heimdal Security supports multiple currency payments. Euro, Dollars, British Pounds, Danish Krone, and Swedish Krona.
Irrespective of your currency, the price stays the same as Heimdal Security, which uses international exchange rates.
Heimdal Pros
- Free tools
- Malware and ransomware protection
- Reliable antivirus
- Relatively fast
- Agile Internet security solutions
- 24/7 prompt support
- Advanced threat protection
- Software updater
- Email Protection
- Threat hunting and action center
Heimdal Cons
- Some features are limited to Windows
- Pricing isn’t transparent
Heimdal Security Review Ratings
Features
Heimdal Security offers a range of cybersecurity solutions to keep you safe. Most importantly, these features are regularly updated to keep up with the dynamic nature of the internet.
Score: 5/5.
Apps
Heimdal Security is primarily a security solution for businesses, mainly targeting desktop users. Only a few of the software’s solutions are available as apps for mobile users.
Score: 3.5/5.
Pricing
Most Heimdal Security users say the price is high, which is true. However, it’s the industry standard as other alternative solutions cost just as much. The good thing is that from time to time, you get price discounts.
Score: 4/5.
Customer Service
Quality customer service is one of the best aspects of using Heimdal Security. They quickly respond across all support channels and are skilled in resolving issues.
Score: 5/5.
Heimdal Security Review: Frequently Asked Questions
Who owns Heimdal Security?
Marlin Equity Partners owns the Heimdal Security company. Marlin Equity Partners wasn’t the company behind the conception of the platform. However, the company acquired the cybersecurity solution several years later. Note that Marlin Equity Partners is a UK-based company operating out of buildings in London.
Who is the CEO of Heimdal Security?
The current CEO of Heimdal Security is Morten Kjaersgaard. Morten has years of experience in cybersecurity, reflecting his position as a leader in critical cybersecurity solutions. In one interview, the CEO confirmed that the focus of Heimdal Security is to remain proactive in the correct approaches to tackling cyber threats.
Where is Heimdal Security headquarters?
Heimdal Security has its headquarters in Copenhagen, Hovedstaden, Denmark. From Denmark, the company can offer cybersecurity services to Europe and other continents. Notably, Heimdal Security’s parent company is based in London. So, it’s safe to say the company also has a strong presence in the United Kingdom.
What Does Heimdal Security Do?
Heimdal Security ensures 360 cybersecurity protection. The software features an antivirus that prevents malware and a firewall that safeguards your network against hackers. Furthermore, it also includes email protection to secure your email messages and prevent phishing and other types of fraud. Another thing Heimdal Security does is automatically update your installed programs.
Is Heimdal Free?
Heimdal Security Thor is just one part of the Heimdal Security package. It’s the antivirus part of the package and is not free. You must pay the annual subscription fee to use it.
The only free tool Heimdal Security features is the free software updater for Windows. It ensures that your installed apps and programs are up to date, helping to avoid vulnerabilities.
How much is Heimdal Security?
Heimdal Security doesn’t have explicit pricing plans. The amount you pay will depend on the size of your business. And you’ll discuss with a sales agent to settle on an ideal price. However, based on my experience with the cybersecurity solution, pricing typically starts at around $35 per year.
Is Heimdal Security Safe?
Heimdal Security is a verified company on TrustPilot with 4.6 stars out of 5 ratings. The company has received 77 percent excellent ratings and 15 percent great ratings from nearly one thousand reviews. That’s a total of 92 percent positive Heimdal Security reviews. As a result, it’s clear that Heimdal Security is a safe and reliable software you can count on to keep your devices secure.
Is Heimdal Security Legit?
With all the positive reviews and features, it’s evident that Heimdal Security is a legitimate security solution. According to customers who have used and are currently using the platform, it’s easy to implement and lightweight. In other words, it won’t affect the performance of your device. As mentioned before, people only complain about the price, but reliable products aren’t always low-cost. Ultimately, you get the worth of your money with Heimdal.
READ ALSO: Best Antivirus For 2023: Windows, Mac, Linux, iOS & Android
Benefits of Using Heimdal Security
Listed below are a few benefits of Heimdal Security.
- Security from all forms of cyber attack: Heimdal Security Suite protects you from malware hidden in emails, instant messages, online ads, and malicious links. It also provides different layers of security between your computer and infected content.
- Optimal Performance: Heimdal Security utilizes minimal memory while running scans in the background. It doesn’t eat into your RAM as it scans files, allowing your computer to run smoothly. This is beneficial because you can continue using your laptop while Heimdal Security runs.
- Automatic patching of third-party apps: Heimdal automatically updates your outdated and vulnerable third-party applications. It checks for new updates every two hours. Heimdal Security also patches vulnerabilities in your operating system.
- Ease of Use: The Heimdal Security suite is straightforward for beginners. It also doesn’t require any tech knowledge to install, as I did for this Heimdal Security review. Its user interface is vibrant and user-centric.
- Multiple Computers: Heimdal allows you to use a single subscription across multiple computers, depending on the number you pay for during the subscription period.
- Flexible Payment Options: Heimdal Security offers flexible payment plans. You can opt for the monthly pay-as-you-go license. It also offers a 30-day free trial period for all products.
Heimdal Security Alternatives
Before concluding the Heimdal Security review, let’s compare it with other cybersecurity solutions.
Here, we compare the software with popular alternatives like Surfshark Antivirus, Malwarebytes, and Trend Micro.
1. Heimdal vs Surfshark Antivirus
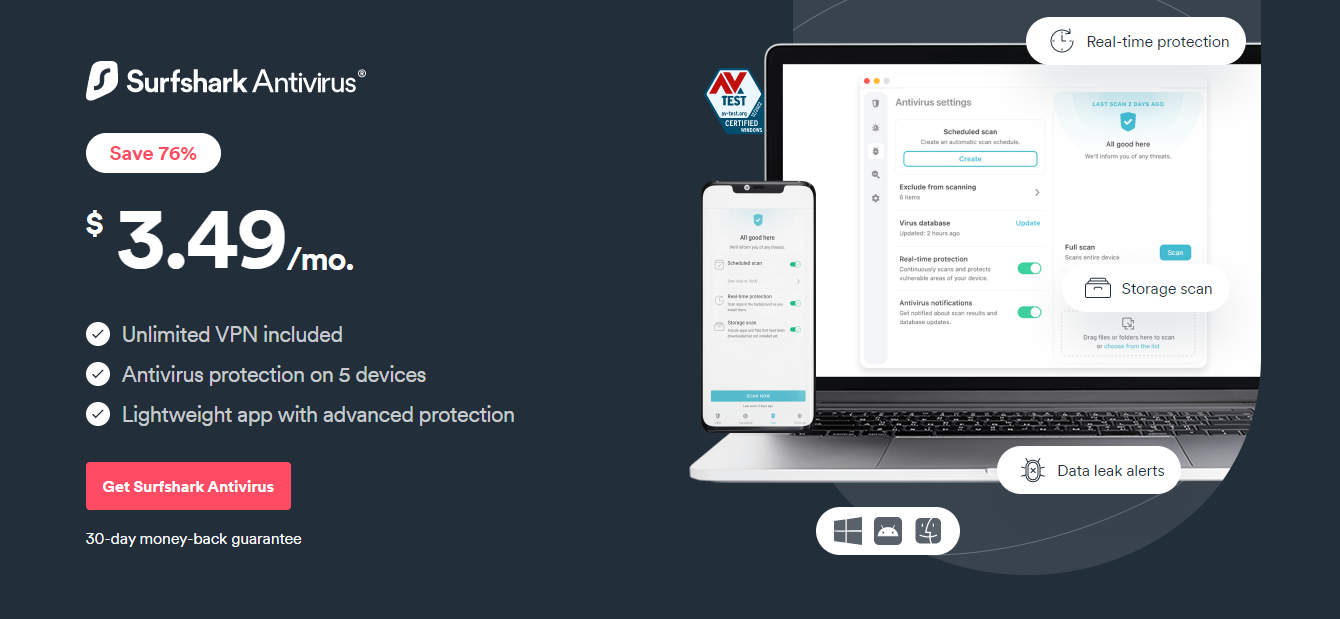
Surfshark Antivirus is an affordable solution to free your devices from viruses and zero-day threats. It’s a relatively simple solution with an intuitive interface, making it easy for anyone to use.
While the antivirus is at the forefront, that’s not all you get with Surfshark. You can purchase the Surfshark One package and get a VPN, a secure search tool, and an alerts tool.
To use Surfshark, your pricing options start at $12.95 per month. This differs from Heimdal Security, which does not disclose public pricing. In addition, you can reduce the rate to $2.39 per month when you pay for 24 months.
However, Surfshark Antivirus doesn’t have as many advanced features as Heimdal Security. For instance, the software lacks solutions such as email protection, threat hunting, and extended detection response.
You can opt for Surfshark Antivirus over Heimdal Security if you need a lightweight, low-cost solution. However, Heimdal Security is the better tool for advanced features and business applications.
==>> Get Surfshark Antivirus
2. Heimdal vs. Malwarebytes
Like Heimdal Security, Malwarebytes offers a cybersecurity solution for homes and businesses. Home users get an antivirus for Windows, Mac, iOS, and Android.
The home solution also comes with a VPN connection and an Ad Blocker. These tools help ensure a better browsing experience.
For businesses, you can use Malwarebytes as an SME or enterprise. Available solutions include endpoint protection, detection, and response. Malwarebytes also comes with managed detection and response. Accordingly, millions use the software.
From first-hand observations, it’s easy to say Heimdal Security and Malwarebytes are equal solutions. However, Heimdal Security offers more to IT security teams than Malwarebytes.
You can use Heimdal Security or Malwarebytes as an individual business or enterprise. But if you’re an IT security firm, you get more versatility with Heimdal Security.
This is thanks to exclusive features such as ransomware encryption protection, email fraud protection, and threat hunting, as outlined in this Heimdal Security review.
==>> Get Malwarebytes
3. Heimdal vs. Trend Micro
Trend Micro is a renowned cloud security solution patronized by many enterprises. The company has been in operation since 1988, making it easy to understand why it has such a strong cybersecurity stance.
Trend Micro products include cloud security, network security, endpoint and email security, security operations, and SME security. These are the same features Heimdal Security offers.
So, which should you pick? Heimdal or Trend Micro? It’s worth noting that Heimdal Security has the upper hand in some areas, as depicted in this Heimdal Security review.
An example is Managed Detection and Response (MDR). Heimdal Security is more reliable for MDR than Trend Micro, although the latter offers an advantage in cloud security.
Like Heimdal Security, Trend Micro doesn’t have public pricing plans. You first need to contact the sales team and discuss a quote. But you can request a demo or free trial.
Then, it depends on your business needs. However, you won’t go wrong with either Heimdal Security or Trend Micro.
==>> Get Trend Micro
4. Heimdal vs. McAfee
McAfee is an award-winning security solution offering two key products: antivirus and VPN. Other security products you get from McAfee include identity monitoring and personal info removal tools.
Using McAfee is simple, as you can personalize all the solutions to suit your needs. You can use McAfee on all major devices, including Windows, macOS, Android, and iOS.
McAfee is a premium solution, similar to Heimdal Security. Pricing starts from $29.99 for the first year with the basic plan.
The highest is the advanced plan, which costs $84.99 per month. Notably, this comprehensive plan includes identity theft coverage worth $1 million.
You can also opt for the exclusive antivirus plan, which provides access to all antivirus features for $29.99 per year.
==>> Get McAfee
5. Heimdal vs. Kaspersky
Kaspersky is a globally renowned company in the cybersecurity industry. It offers both home and business solutions.
The primary product is Kaspersky antivirus, which utilizes advanced technology and AI to combat malware, spyware, ransomware, and fileless attacks.
Additionally, it offers phishing protection by automatically blacklisting fake sites and emails.
Kaspersky also features a VPN, like the other Heimdal alternatives on this list. The VPN is bright and fast, and will keep you safe from cyberattacks.
Other security solutions from Kaspersky include an ad blocker, a private browser, webcam protection, a GPS locator, a password manager, and file protection.
Kaspersky pricing starts from $22.99 per month for the essential plan. It’s slightly cheaper than the starting price of other platforms.
The highest plan, Kaspersky Total Security, begins at $42.99 per month. It’s much cheaper than that of other platforms.
Notably, Kaspersky supports Windows, macOS, iOS, and Android devices.
==>> Get Kaspersky Total Security
A Final Word On The Heimdal Security Review
To conclude this Heimdal Security review, I will say that Heimdal is dependable if you need an extensive security solution to keep you and your device safe.
Heimdal is renowned by businesses and individuals as a reliable solution to stop cybersecurity threats. I can attest to that, having used the tool myself. And this is why I recommend it.
This review clearly demonstrates that the software is indeed robust in terms of cybersecurity. The next-gen antivirus, hybrid firewall, endpoint protection, email security, and software updater all stand out. The only major con is that there aren’t detailed pricing plans.
Leave a comment below regarding this Heimdal Security review.
INTERESTING POSTS
- 12 Best Free Antivirus Software for your Windows PC [Not Free Trial]
- Is Windows Defender Enough?
- What is the difference between a Virus, Malware, Adware, Trojans, and Ransomware?
- Surfshark Antivirus Review
- Best Paid Antivirus According To Reddit Users
- Ultimate List Of The Best Antivirus Blogs [MUST READ]
- Best Anti-Pharming Software
- Here Are The Best Windows 7 Antivirus After Support Ends