Follow me as I review the BullGuard Premium Protection 2021 Edition…
BullGuard announced its latest suite of security solutions – The BullGuard Premium Protection 2021 Edition on the 30th of September, 2020.
The new security suite features an antivirus engine with dynamic machine learning capabilities and enhanced protection to meet the needs of its users. It also includes other privacy and security tools intended to protect users’ data and safety while online.
This review provides detailed information about BullGuard Premium Protection 2021 Edition, its robust suite of security and privacy tools, including a Game Booster, and offers guidance on maximizing the benefits of these features and tools.
- Read Also: Surfshark Antivirus Review
Table of Contents
What Is BullGuard Premium Protection 2021 Edition?
BullGuard Premium Protection 2021 Edition is an enhanced security and privacy tool designed to keep users’ devices and data safe, irrespective of their online or offline activities. The security suite also includes an improved Game Booster feature, ensuring that users enjoy uninterrupted gaming sessions while keeping Gaming devices and data safe and protected.
For the 2021 edition, we see BullGuard introducing enhanced features for its antivirus engine, firewall, parental control, secure browser, and more to make it a next-generation security software. For users staying connected via Wi-Fi networks, it’s an opportunity to enjoy privacy and security protection while connected to unsecured Wi-Fi networks.
BullGuard Premium Protection 2021 Edition Features
User Interface
BullGuard has one of the most intuitive User interfaces with easily navigable features, making it suitable for tech-inclined and less tech-savvy users. Although users would have to get familiar with the Interface to find their way around pretty easily, it does feature a drop-down menu from which users can access every one of BullGuard’s features within a click away.
Antivirus Engine with Dynamic machine learning and multi-layered protection
Testing BullGuard’s antivirus engine against new and existing threats, its Dynamic Machine learning features keep it ahead of the pack in protecting users’ devices. We see BullGuard scoring high in its performance as an antivirus engine in all AV lab tests. Its high-performance features can be attributed to its Dynamic Machine Learning capabilities. This enables its AV engine to continually monitor users’ devices in real-time, enabling it to detect potential threats before they can harm users’ devices.
Aside from Dynamic Learning Capabilities, the signature-based BullGuard AV engine protects users’ devices against threats, even without running a full system scan or requiring updates to its virus signatures. When connected to the internet, BullGuard’s cloud detection can identify new threats in real-time, eliminating the need to manually update its antivirus engine.
Game Booster
Its Game Booster is my favourite BullGuard feature. When playing games like PUBG, Minecraft, or Starcraft 2, BullGuard’s Game Booster prevented pop-ups and other game interrupters while still keeping my device protected. For this enhanced Game Booster feature, I give BullGuard a thumbs up as an antivirus for gamers. The new Game Booster features include an anti-cheat engine and broadcasting support, which makes gaming time something I look forward to.
Built-in Browser
Most users have cause to worry about their browsers’ security. With BullGuard’s built-in browser, users no longer have to worry about browser security. Its custom-built browser establishes a secure connection to protect users’ information and protect them from web-based attacks. Test-running the browser, it requested permissions to load cookies and browser extensions. This implies that users would not have to worry about third-party cookie trackers and malicious websites anymore since the browser can screen them out effectively.
Firewall Protection
BullGuard’s Firewall protection features a range of unique protective capabilities beyond its inbound and outbound traffic monitoring functionality. Its firewall monitors and protects all ports, blocks unauthorized connectivity attempts, keeps track of security updates, and protects the device during downloads, among other functions. I also find this feature quite impressive for its minimal resource usage, which does not interfere with other running applications.
Parental Controls
This feature is ideal for users who want to monitor and protect their kids online. Playing around with this feature, I can set search filters to prevent access to censored web content, limit screen time, block websites and apps not suitable for children’s use, monitor kids’ location, and a host of other features designed to ensure children’s safety.
Vulnerability Scanner
Downloading is part of everyday internet life. There is a need to download various media files, applications, drivers, and other files. BullGuard’s vulnerability scanner automatically scans downloads to verify their sources. As expected, its vulnerability scanner lived up to its expectation of keeping my device safe from malicious downloads. Additionally, I receive alerts for security issues that require updates.
Other BullGuard Premium Protection 2021 Edition features include:
- Optimized performance
- Identity protection
- VPN (separate subscription package)
- Home security scanner
- Multiple device compatibility
- Auto-updates
Technical Details
Supported devices and OS: Windows, Mac, Android, iOS, SP1+
RAM: minimum 1GB
Storage: 850MB minimum free space
Internet connectivity: Needed
Languages: English, Danish, Dutch, French, German, Italian, Norwegian, Portuguese, Spanish, Swedish, Brazilian Portuguese, Chinese, Arabic, Vietnamese
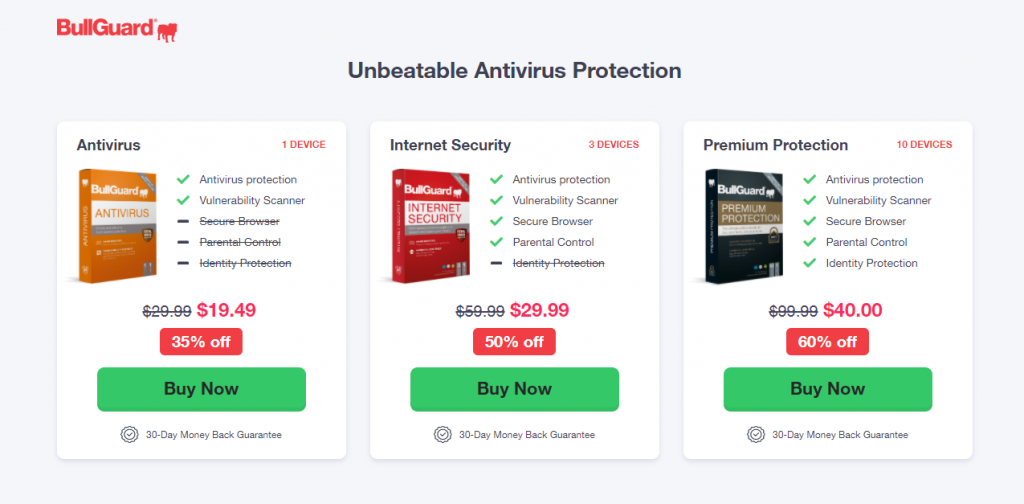
Pricing model: 1-year subscription, 2-year subscription, and 3-year subscription supporting 10-15 devices.
Customer types: individuals, businesses, and corporate organizations
Mobile applications: Android, iOS
BullGuard Premium Edition 2021 Pricing
BullGuard Premium Edition 2021 is a next-generation privacy and security suite designed to offer comprehensive protection for all users.
BullGuard offers its subscribers a one-month trial and a 30-day money-back guarantee. Thus, users have the privilege of enjoying BullGuard’s premium features free for a whole month. Additionally, for users who may feel BullGuard does not meet their needs, they can call for a money-back guarantee within 30days.
Available plans
1-year subscription
- 10 Devices: $99.99
- 15 Devices: $139.99
2-year subscription
- 10 Devices: $159.99
- 15 Devices: $223.99
3-year subscription
- 10 Devices: $199.99
- 15 Devices: $279.99
Is BullGuard Safe?
BullGuard is 100% safe for use by individuals, families, and organizations. Users enjoy a variety of protection features, including anti-phishing, anti-malware, Wi-Fi protection, etc. Gamers also appreciate using BullGuard due to its Game Booster feature, which enables uninterrupted gaming sessions.
Its Dynamic Machine Language feature enables it to keep users’ devices safe and protected by continually scanning for new and existing threats.
Wrapping Up The BullGuard Premium Protection 2021 Edition Review
BullGuard’s 2021 edition takes privacy and security protection to the next level. It is built to protect users from existing and emerging malware threats. Hence, users enjoy a wide range of protective features with BullGuard.
In terms of price comparison, BullGuard may be on the high side, but it does make it up by offering subscribers protection for 10-15 devices, depending on the subscribers’ choice. Hence, this makes BullGuard Premium 2021 edition a recommended choice of antivirus for individuals, families, and organizations.
Get BullGuard Premium Edition 2021
Note: This post was originally published in 2020 but has been updated for grammatical accuracy.



![Unbiased Lookout App Review 2026 [Reliable Mobile Security] Unbiased Lookout App Review 2026 [Reliable Mobile Security]](https://secureblitz.com/wp-content/uploads/2022/01/Lookout-App-Review-768x402.png)
 Lookout works like you would expect a mobile security and antivirus application to work. In fact, in this Lookout app review, we purchased its premium plan to see how it works.
Lookout works like you would expect a mobile security and antivirus application to work. In fact, in this Lookout app review, we purchased its premium plan to see how it works.
 Lookout claims to have the best mobile security support team in the world that helps users and answers all their questions regarding the application. So, for this Lookout app review, we also tested their customer support process.
Lookout claims to have the best mobile security support team in the world that helps users and answers all their questions regarding the application. So, for this Lookout app review, we also tested their customer support process.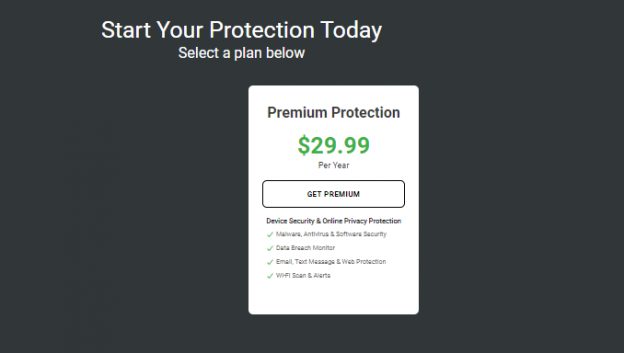 Lookout has three plans: Basic, Premium, and Premium Plus. The Basic plan offers all the essential security, privacy, and device theft protection features, while the Premium Plus and Premium plans offer additional and advanced security, privacy, device theft protection, and even identity theft protection features.
Lookout has three plans: Basic, Premium, and Premium Plus. The Basic plan offers all the essential security, privacy, and device theft protection features, while the Premium Plus and Premium plans offer additional and advanced security, privacy, device theft protection, and even identity theft protection features.








![Dos And Don’ts Of Using A Public Wi-Fi [Ultimate Guide] Dos And Don’ts Of Using A Public Wi-Fi [Ultimate Guide]](https://secureblitz.com/wp-content/uploads/2019/08/dos-and-donts-public-wi-fi-768x512.jpg)