Learn how to use a VPN to bypass geo-blocks and unlocking access to restricted content.
In today’s interconnected world, accessing online content from anywhere should be a seamless experience. However, geo-blocking, a practice that restricts access to internet content based on location, often hinders the freedom of internet users.
Whether you’re traveling abroad, seeking to watch your favorite TV shows, or accessing region-specific services, geo-blocks can be a significant inconvenience.
Thankfully, there is a solution: using a Virtual Private Network (VPN) to bypass geo-blocks and unlock access to restricted content. In this comprehensive guide, we will explore the ins and outs of VPNs and provide you with step-by-step instructions on how to use a VPN effectively to bypass geo-blocks and regain control over your online experience.
Table of Contents
Understanding Geo-Blocking
What is Geo-Blocking?
Geo-blocking is a practice employed by online platforms and websites to restrict access to content based on the user’s geographical location.
By analyzing the user’s IP address, which acts as a digital identifier, these platforms determine the user’s location and either grant or deny access to specific content.
Geo-blocking is commonly used by media streaming services, online retailers, and websites to comply with licensing agreements, copyright laws, and regional regulations.
Reasons for Geo-Blocking
Geo-blocking serves various purposes, primarily driven by licensing agreements, copyright protection, and market segmentation.
Media streaming platforms like Netflix and Amazon Prime Video implement geo-blocking to comply with licensing deals that grant access to content in specific countries or regions. This allows them to provide country-specific content libraries tailored to the preferences and legal requirements of each region.
Additionally, geo-blocking can be used to enforce copyright protection. Content creators and copyright holders may limit access to their intellectual property based on geographical boundaries to prevent unauthorized distribution or piracy.
By restricting access to specific regions, they can ensure compliance with licensing agreements and protect their revenue streams.
Moreover, geo-blocking is utilized for market segmentation, enabling companies to tailor their products, services, and pricing based on regional demand and market conditions. Online retailers like Amazon may employ geo-blocking to direct users to their local websites, offering localized pricing and product availability.
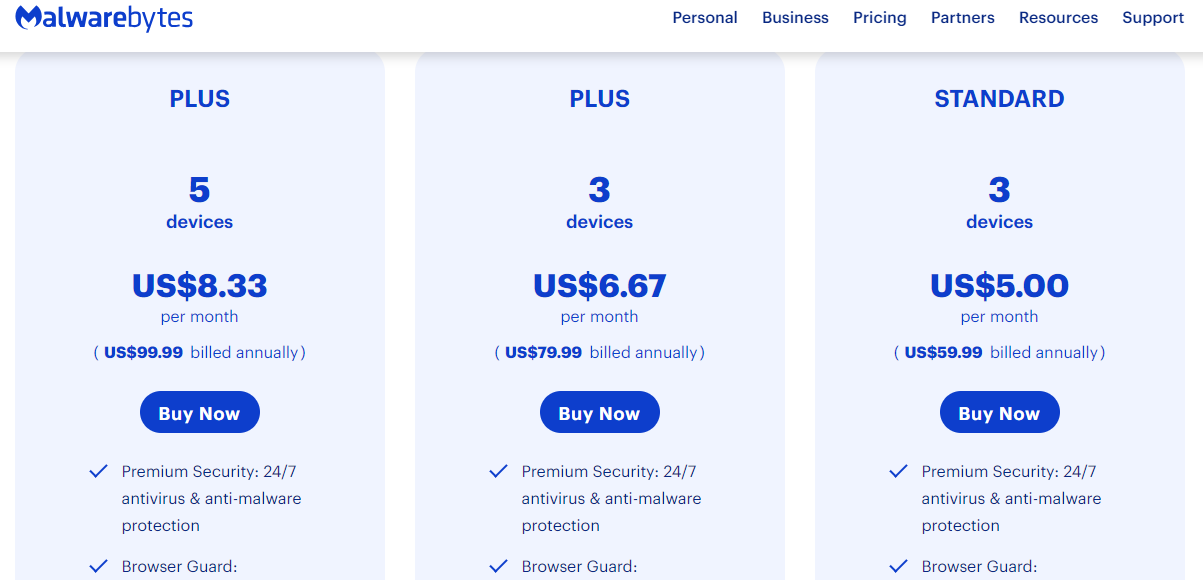
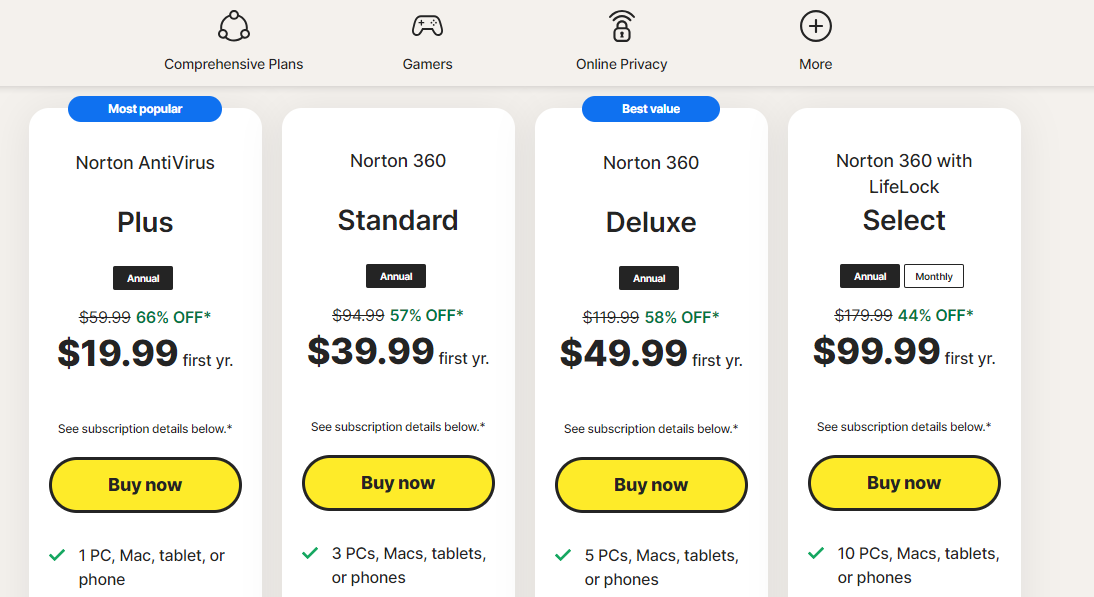
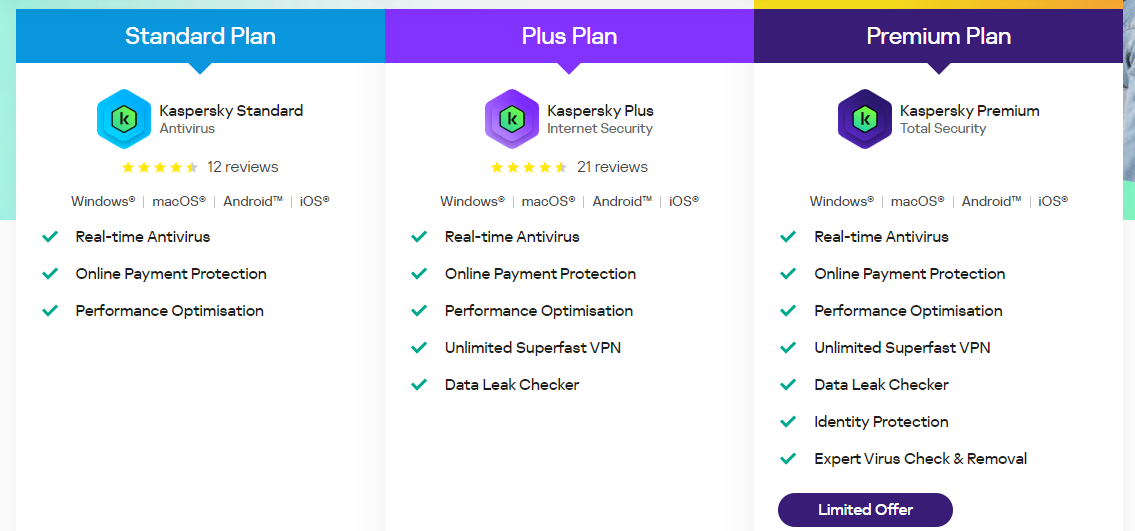
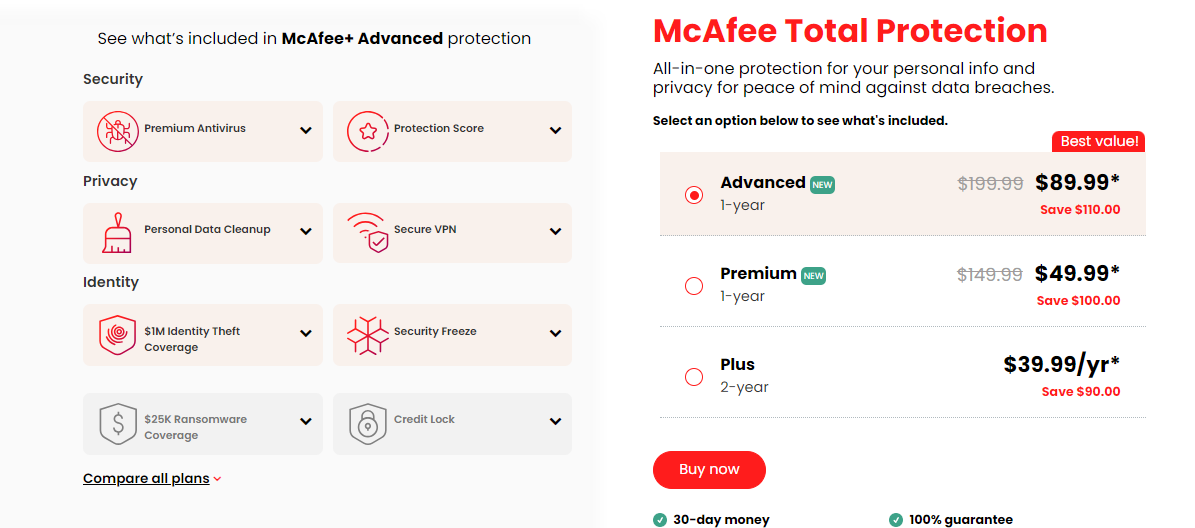
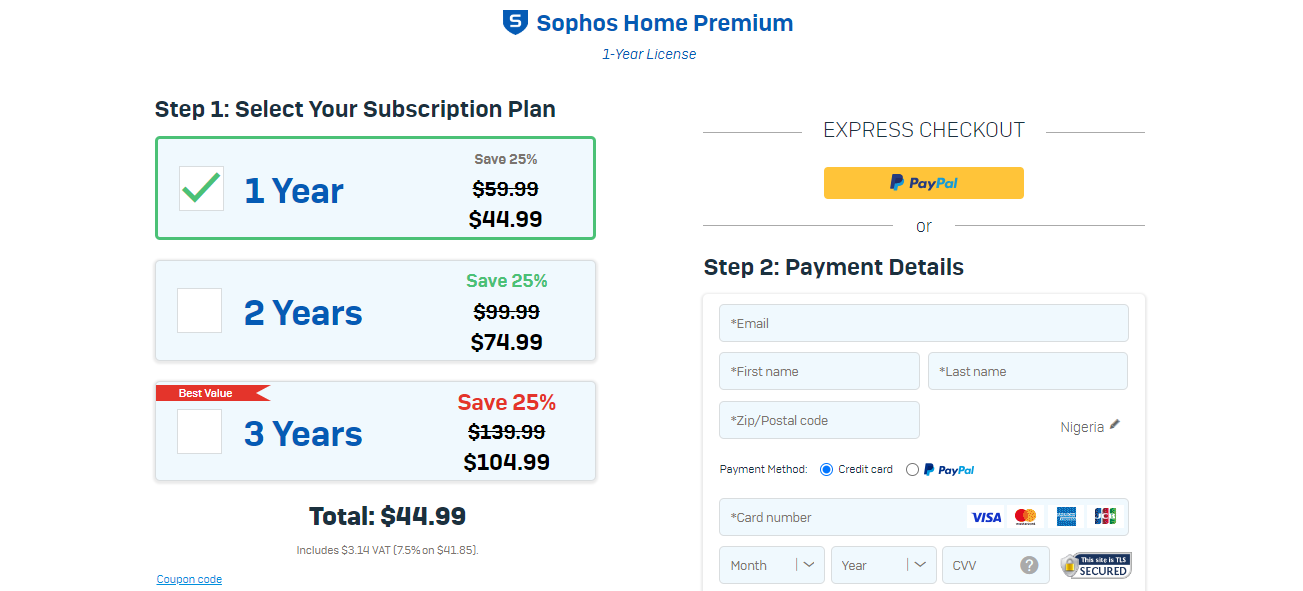
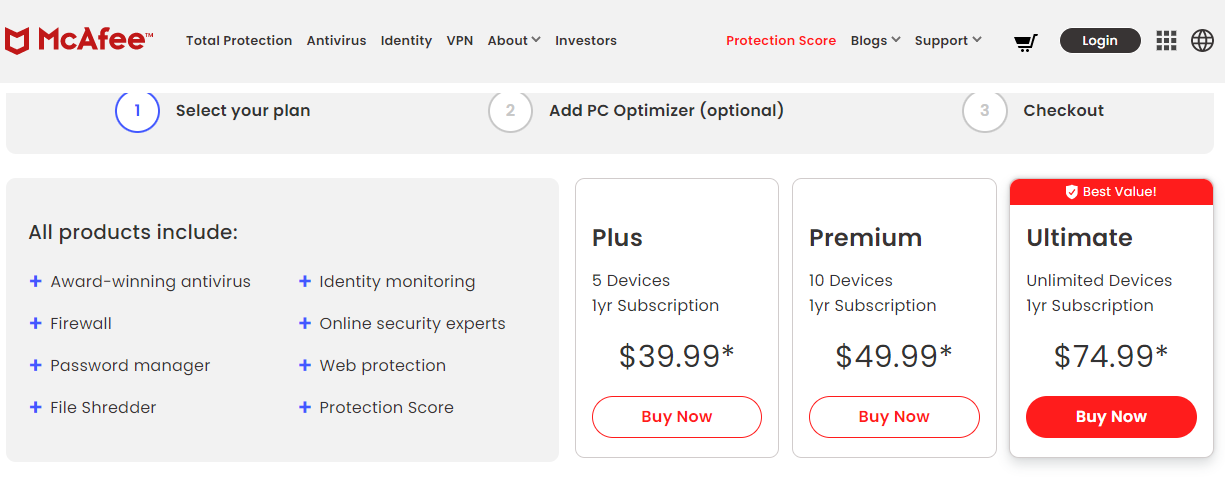
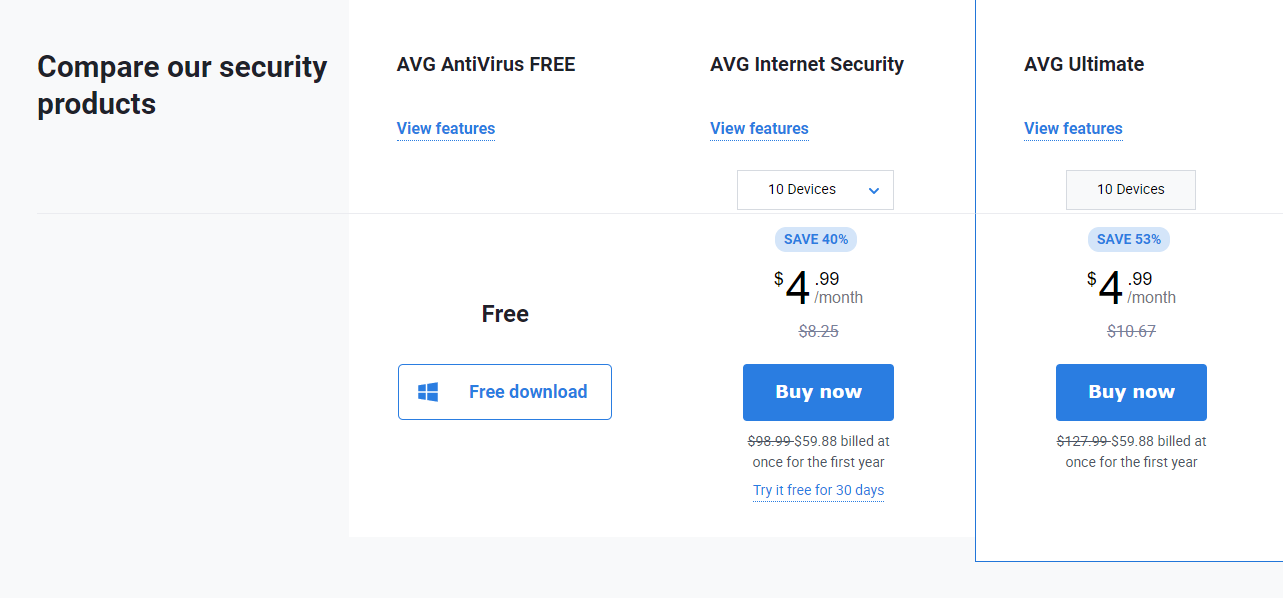
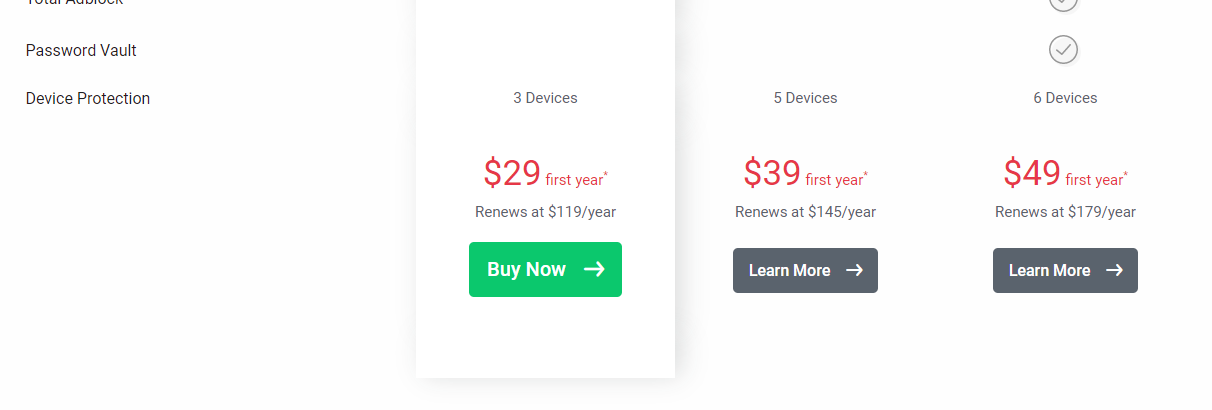
TOP DEALS
How Geo-Blocking Works
Geo-blocking works by analyzing the user’s IP address, a unique identifier assigned by their Internet Service Provider (ISP). Your IP address provides information about your geographic location, allowing websites and platforms to determine your eligibility to access specific content.
When you attempt to access geo-blocked content, the website or platform checks your IP address against a database of blocked or allowed regions. If your IP address falls within a blocked region, access is denied.
It’s important to note that your IP address can change depending on various factors, such as your physical location or the use of a VPN.
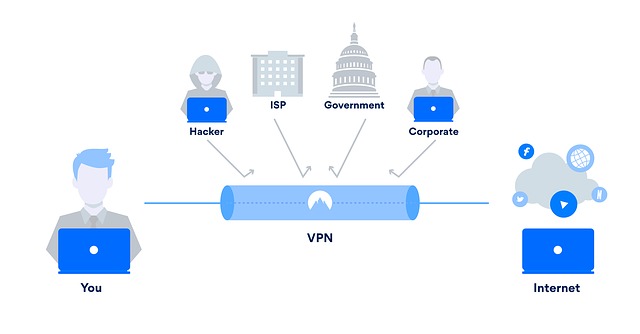
By utilizing a VPN, you can mask your IP address and make it appear as if you are accessing the internet from a different location, effectively bypassing geo-blocks and gaining access to restricted content.
Popular Examples of Geo-Blocking
Geo-blocking is prevalent across various online platforms and services. Let’s explore some common examples of geo-blocking:
- Streaming Services: Streaming giants like Netflix and Amazon Prime Video employ geo-blocking to enforce licensing agreements and restrict access to their content libraries based on the user’s location. This results in different content availability across countries and regions, with some shows or movies being exclusive to specific countries.
- Social Media Platforms: Some social media platforms, like Facebook and Twitter, may be blocked or restricted in certain countries due to government regulations or censorship policies. This can limit users’ ability to access and engage with these platforms while in those regions.
- E-commerce Websites: Online retailers, such as Amazon, may employ geo-blocking to direct users to their local websites based on their IP address. This allows them to provide localized pricing, product availability, and shipping options.
- Live Sports Streaming: Sports streaming platforms often use geo-blocking to enforce regional broadcasting rights. For example, the MLB TV app restricts streaming of baseball games based on the user’s location within a team’s cable broadcast region.
- News Websites: Some news websites may employ geo-blocking to comply with local regulations or licensing agreements. This can result in certain articles or content being inaccessible to users outside of specific regions.
Legal Aspects of Geo-Blocking
Geo-blocking, while sometimes frustrating for users, is generally legal and serves various legitimate purposes. It allows companies to comply with licensing agreements, copyright laws, and regional regulations.
For example, streaming services like Netflix are bound by licensing contracts that dictate content availability in specific regions. By implementing geo-blocking, they ensure compliance with these agreements and avoid legal repercussions.
However, legal frameworks differ across countries, and some jurisdictions may have specific regulations or restrictions on geo-blocking practices. The European Union (EU), for instance, has taken steps to address unjustified geo-blocking within its member states.
The EU’s Geo-Blocking Regulation aims to promote a Digital Single Market by prohibiting unjustified geo-blocking and discrimination based on customers’ nationality or location within the EU.
The Benefits of Bypassing Geo-Blocks
Bypassing geo-blocks using a VPN offers several benefits for internet users:
Access to Restricted Content: By using a VPN, you can bypass geo-blocks and gain access to content that would otherwise be restricted based on your location. This includes streaming services, social media platforms, news websites, and other region-specific content.
Enhanced Privacy and Security: VPNs encrypt your internet traffic and protect your online activities from prying eyes, including your ISP, government surveillance, and potential hackers. By masking your IP address, VPNs provide an additional layer of privacy and security.
Online Anonymity: When you use a VPN, your online activities are associated with the IP address of the VPN server, not your actual IP address. This helps maintain your anonymity and prevents websites, advertisers, and other entities from tracking your online behavior.
Protection on Public Wi-Fi: Public Wi-Fi networks pose security risks, as they are often unencrypted and vulnerable to attacks. When connected to a VPN, your data is encrypted, making it significantly more secure while using public Wi-Fi hotspots.
Overcoming Censorship: In countries with strict internet censorship or content restrictions, a VPN can help bypass these limitations and provide access to blocked websites and services. By connecting to a VPN server located in a different country, you can bypass censorship and enjoy unrestricted internet access.
Methods to Bypass Geo-Blocking
Several methods can be used to bypass geo-blocking and regain access to restricted content. Let’s explore some popular methods:
Using a VPN
A VPN (Virtual Private Network) is the most effective and widely-used method to bypass geo-blocks. VPNs redirect your internet traffic through a server located in a different country, thereby masking your IP address and making it appear as if you are accessing the internet from that country. This allows you to bypass geo-restrictions and access region-specific content.
To use a VPN to bypass geo-blocks, follow these steps:
- Choose a reputable VPN provider that offers servers in the desired location(s) for accessing the blocked content. Consider factors such as server network size, encryption protocols, and user reviews to make an informed decision.
- Sign up for a VPN subscription plan that suits your needs, and download and install the VPN app on your device(s).
- Launch the VPN app and log in using your credentials.
- Connect to a server located in a country where the desired content is accessible. For example, if you want to access US-based streaming services, connect to a server in the United States.
- Once connected, your IP address will be masked, and your internet traffic will be routed through the selected server. You can now access the previously blocked content as if you were physically located in the chosen country.
By using a VPN, you can bypass geo-blocks and enjoy unrestricted access to a wide range of online content.
BEST VPNs
Proxy Servers
Proxy servers act as intermediaries between your device and the websites you want to access. When you connect to a proxy server, your requests are routed through the server, and the server’s IP address is used to access the requested content.
By choosing a proxy server located in a different country, you can bypass geo-blocks and access region-restricted content.
However, it’s important to note that proxy servers may not provide the same level of security and privacy as VPNs. Your internet traffic may not be encrypted, and your IP address may still be exposed to the websites you visit.
Additionally, some websites and services may detect and block proxy server IP addresses, limiting their effectiveness in bypassing geo-blocks.
Best Proxy Services
Tor Browser
The Tor browser is a privacy-focused web browser that allows users to access the internet anonymously.
It works by routing your internet traffic through a network of volunteer-operated servers, known as Tor nodes or relays, which encrypt and redirect your connection multiple times. This process helps mask your IP address and provides a high level of anonymity.
While the Tor browser can help bypass geo-blocks, it’s important to note that the browsing experience may be slower compared to traditional browsers due to the multiple encryption layers and routing process.
Additionally, not all websites and services are accessible through the Tor network, as some may block connections from Tor exit nodes.
Smart DNS and DNS Changers
Smart DNS and DNS changers are alternative methods to bypass geo-blocking. These methods involve changing the DNS (Domain Name System) settings on your device to redirect DNS requests through servers located in different countries.
By using a smart DNS or DNS changer service, you can mask your IP address and access region-specific content.
It’s worth noting that smart DNS and DNS changers primarily focus on masking your location for the purpose of bypassing geo-blocks.
They do not provide the same level of encryption and privacy as VPNs, and your online activities may still be visible to your ISP and other entities.
How to Choose the Best VPN for Bypassing Geo-Blocks
When selecting a VPN for bypassing geo-blocks, consider the following factors:
- Server Network: Ensure that the VPN provider offers a wide range of servers in various countries and regions. This will allow you to access content from different locations and bypass geo-restrictions effectively.
- Speed and Performance: Look for VPNs that provide fast and reliable connections, as slow speeds can impact your streaming and browsing experience. Read reviews and consider conducting speed tests to assess a VPN’s performance.
- Security and Privacy Features: Choose a VPN that offers robust encryption protocols, such as OpenVPN or IKEv2, to ensure the security of your internet traffic. Look for additional privacy features, such as a strict no-logs policy and DNS leak protection, to safeguard your online activities.
- User-Friendly Interface: Opt for a VPN with an intuitive and user-friendly interface that makes it easy to connect to servers and navigate the VPN settings. A well-designed VPN app can enhance your overall user experience.
- Customer Support: Consider the availability and quality of customer support provided by the VPN provider. Look for options such as live chat, email support, and comprehensive knowledge bases to address any concerns or issues that may arise.
By carefully evaluating these factors, you can choose the best VPN for bypassing geo-blocks and enjoy seamless access to restricted content.
Step-by-Step Guide: How to Use a VPN to Bypass Geo-Blocks
Now that you understand the benefits and methods of bypassing geo-blocks using a VPN, here’s a step-by-step guide on how to use a VPN effectively:
- Research and Choose a VPN: Explore different VPN providers and compare their features, server networks, and user reviews. Select a VPN that meets your specific needs for bypassing geo-blocks.
- Sign up and Install the VPN: Subscribe to a VPN plan and download the VPN app for your device(s). Follow the installation instructions provided by the VPN provider.
- Launch the VPN App: Open the VPN app on your device and log in using your credentials.
- Choose a Server Location: Select a server location in a country where the desired content is accessible. For example, if you want to access US-based streaming services, choose a server located in the United States.
- Connect to the VPN Server: Click on the “Connect” button within the VPN app to establish a connection to the selected server. Wait for the app to establish a secure connection.
- Verify Your New IP Address: After connecting to the VPN server, verify that your IP address has changed to the location of the server. You can use online tools or visit websites that display your IP address to confirm the change.
- Access Geo-Blocked Content: With the VPN connection established, you can now access geo-blocked content as if you were located in the chosen server’s country. Enjoy unrestricted access to streaming services, websites, and other region-specific content.
By following these steps, you can effectively use a VPN to bypass geo-blocks and unlock access to a wide range of online content.
Best Practices for Bypassing Geo-Blocks
To ensure a smooth and effective experience when bypassing geo-blocks using a VPN, consider the following best practices:
- Choose Reliable VPN Servers: Select VPN servers that are known to work effectively for bypassing geo-blocks. Research user reviews and recommendations to identify reliable servers for accessing specific content.
- Regularly Update the VPN App: Keep your VPN app up to date by installing the latest updates and patches provided by the VPN provider. This ensures optimal performance and compatibility with the latest technologies and geo-blocking measures.
- Clear Browser Cookies and Cache: Clear your browser’s cookies and cache regularly to avoid potential conflicts or issues when accessing geo-blocked content. This helps ensure a clean browsing session and minimizes the risk of encountering errors or restrictions.
- Test Different Server Locations: If you encounter difficulties accessing certain geo-blocked content, try connecting to different server locations within the same country. Some content may be limited to specific regions within a country, and switching servers can help you bypass these restrictions.
- Contact VPN Support for Assistance: If you experience persistent issues when bypassing geo-blocks, reach out to the VPN provider’s customer support for assistance. They can provide guidance, recommend alternative server locations, or troubleshoot any technical issues you may encounter.
By following these best practices, you can optimize your VPN bypassing experience and enjoy seamless access to geo-blocked content.
Conclusion
Geo-blocking can be a frustrating hurdle when trying to access online content from different locations. However, by utilizing a VPN, you can bypass geo-blocks and regain control over your online experience.
VPNs provide a secure and private connection that masks your IP address and routes your internet traffic through servers located in different countries, effectively bypassing geo-restrictions and allowing access to region-specific content.
Whether you’re traveling abroad, seeking to watch your favorite shows, or accessing region-specific services, a VPN is an essential tool to unlock the world of geo-blocked content and enjoy seamless internet access from anywhere in the world.
Choose the best VPN, follow our step-by-step guide, and embrace a truly unrestricted online experience.
INTERESTING POSTS
























































































![Can VPNs Help Prevent Cyberattacks? [We Have The Answer] Can VPNs Help Prevent Cyberattacks? [We Have The Answer]](https://secureblitz.com/wp-content/uploads/2020/08/Can-VPNs-Help-Prevent-Cyberattacks-768x433.jpg)