Learn how to sign up for OmniWatch identity protection plans.
With the rising rate of cyber risks recently, it’s crucial to safeguard your data as an internet user. That’s why services like OmniWatch exist. Registering with OmniWatch gives you access to 24/7 identity theft protection — up to the tune of $2 million in insurance.
As you’d expect, however, OmniWatch is a premium identity protection solution. To access the features, you have to choose and pay for a subscription plan. How exactly do you sign up and subscribe? That’s what we’ll be discussing in this post.
So, if you’re interested in getting OmniWatch protection, read on.
Table of Contents
Why Sign Up for OmniWatch ID Protection?
OmniWatch is a service dedicated to protecting, detecting, and correcting online identity theft issues. The solution comes with numerous notable features that make signing up worthwhile. Check them out below:
- Access to resolution experts: With OmniWatch, you get 24/7 support from ID theft resolution experts in the United States. Particularly, the service will assign you an agent who will assist in any way you need help.
- Credit protection: If you have a TransUnion account, you can leverage OmniWatch to lock your credit file. The advantage here is that you’ll prevent third parties from creating accounts using your details. Notably, OmniWatch offers a similar service for Equifax and Experian.
- Dark web monitoring: To ensure your sensitive details aren’t exposed to the dark web, OmniWatch provides a dedicated monitoring service. You’ll receive instant alerts whenever there’s any change to your credit report or other sensitive details.
- ID risk score: You can regularly check the OmniWatch ID risk score to gauge how safe you are on the web. It’s straightforward, and you get tips on how to mitigate any risk.
- Up to $2 million insurance.
So, you’ll agree that simply referring to OmniWatch as an “identity protection software” doesn’t do justice. The platform has a lot more to offer. As a result, if you’ve decided to sign up, it’s an instructive decision.
OmniWatch Identity Protection Plans
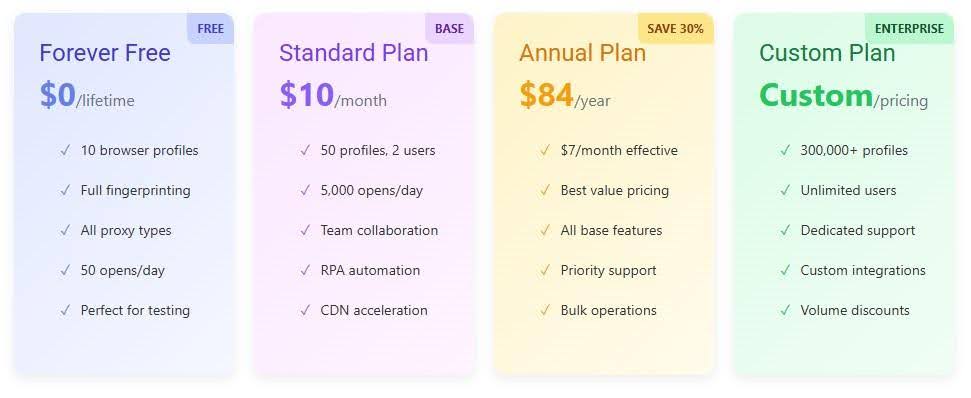
To begin using OmniWatch, you have two main pricing plans to choose from: Basic and Premium. As you’d expect, the Premium plan gives you access to more features compared to the Basic plan.
You can check out the comparison between both two below:
| Basic Plan features | Premium Plan features |
| Dark web monitoring | All features of the basic plan |
| Up to $2 million ID theft insurance | Up to $2 million ID theft insurance |
| Credit report and monitoring | Up to $25,000 in ransomware protection |
| Credit lock | Additional credit monitoring |
| Identity resolution experts | Additional credit reports |
How much do the plans cost? Check out the prices below:
- Basic: $9.99 per month
- Premium: $14.99 per month
Evidently, the difference between the basic and premium plans is only $5, which is minimal. We recommend opting for the premium plan from the outset so you can enjoy the full benefits of using OmnWatch.
Nevertheless, you can start with the basic plan if you want to get familiar with the platform before upgrading to the comprehensive package.
Steps to Subscribe for OmniWatch ID Protection
From first-hand experience, subscribing to OmniWatch ID protection is straightforward. So long as you have your payment details handy, you can complete the process within a few minutes. Below are the steps to take:
Step 1: Visit the website and click Get Started
To start with, you’ll visit the official OmniWatch website. There’s a Get Started button on the homepage. Simply click on it to kickstart the subscription process.
Step 2: Set up your account
The next page will require you to create an OmniWatch account. It’s simple; you only need to enter your name and email address. Then, click Register at the bottom. If you don’t want to type in your details manually, simply choose the option to sign up using your Google account.
Step 3: Select your subscription
OmniWatch will present a checkout page featuring the two pricing plans discussed earlier. For this step, simply click on your preferred package.
Step 4: Make the payment
As you scroll down the checkout page, you’ll find the option to Choose Payment Method. Below are the featured options on the OmniWatch website:
- Visa
- AMEX
- MasterCard
- PayPal
Essentially, you can use either a credit/debit card or PayPal. Select the option you prefer and provide the required details to complete the payment.
Step 5: Start protecting your identity
If your payment is successful, you’ve completed the subscription procedure. Now, OmniWatch will redirect you to your account dashboard, where you can access features based on your plan. You can then provide your details and allow the tool to do its work – protect you.
READ ALSO: 3 Simple Tricks to Verify a Site Is Secure Before Signing Up
Who Can Subscribe to OmniWatch?
To be straightforward, only persons within the United States can subscribe to and use OmniWatch. Currently, the service is limited to the US, which you’ll confirm during the sign-up process.
Additionally, to monitor and protect your online identity, you’ll need to provide a valid Social Security Number and home address, in addition to regular details such as date of birth and email address.
Notably, the fact that OmniWatch is only available in the United States is one of the platform’s main drawbacks. If you reside outside the US, you’ll need to use an alternative identity security tool.
Nevertheless, there are other reliable options to go for, which you’ll find on our list of the best data removal services in 2024.
Can You Cancel Your OmniWatch Subscription?
One thing to note about OmniWatch subscriptions is that they automatically renew every month. If you’re wondering if you can cancel your subscription when needed, the answer is yes. However, you must do it before the start date of your payment.
The good thing is that cancelling your OmniWatch subscription isn’t complicated. When you sign into your account, you can access the option from your Account page. You’ll find a Cancel button; click on it, and you’re done.
If you are unable to access your account, you can cancel your subscription by contacting our support team. You can reach the customer service via the channels below:
- Email: support@omniwatch.com
- Toll-free number: (877) 892-8249
The only drawback here is that you can only contact the agents during working hours. Particularly, the OmniWatch customer support team is available Monday to Friday from 7 am to 4 pm PT (10 am – 7 pm ET).
Is There an OmniWatch Free Trial?
No, OmniWatch doesn’t currently offer a free trial. Previously, the service offered a 30-day free trial, allowing you to test the features before making a payment. However, it appears the option was removed in 2024.
However, while a free trial is not available, OmniWatch does offer a refund if you wish to cancel your plan after subscribing.
Pros and Cons of OmniWatch Subscription
Now that you know OmniWatch subscription plans and how to pay, the big question is, “Is OmniWatch worth it?”
Well, based on our OmniWatch review of the subscription plans, the options are relatively affordable. You can begin using the service for only $9.99 per month, and the complete package costs an additional $5.
However, there are both upsides and downsides to consider. To keep things balanced, check out the pros and cons below to decide if subscribing to OmniWatch is worth it:
Pros
- Relatively affordable plans starting at $9.99 monthly
- Straightforward registration and subscription procedure
- Up to $2 million insurance coverage
- Simple subscription cancellation process
Cons
- No free trial
- Only available in the United States
Frequently Asked Questions About OmniWatch Identity Protection Plans
How much does OmniWatch Identity Protection cost?
OmniWatch Identity Protection costs $9.99 per month for the Basic plan and $14.99 per month for the Premium plan. You can pay for any one when you sign up, but the Premium plan accommodates all features.
How do I get OmniWatch free trial?
Unfortunately, you can’t get an OmniWatch free trial at the moment. The service previously featured a 30-day free trial for its pricing plans, but the option is no longer available.
Which country does OmniWatch support?
OmniWatch supports only the United States. If you reside outside the US, you will not be able to access the identity protection features of the platform.
Can I download the OmniWatch app?
No, you can’t download the OmniWatch app at the moment, as it is not available. You can only access OmniWatch and employ the service to protect your online identity by using the website. Nevertheless, the mobile site is responsive, allowing you to use your smartphone’s browser.
Is OmniWatch legit?
Yes, OmniWatch is a legit identity theft solution. The platform is permitted to operate in the United States, as it complies with strict US regulations regarding data privacy.
Bottom Line
To summarize, you’ll agree that signing up for an OmniWatch subscription is easy. It takes only five steps, where you provide your details and make a payment. The service has some drawbacks, including the absence of a free trial and its limited availability in the US.
However, the benefits, including the affordable plans and up to $2 million, have more weight. Ultimately, we recommend OmniWatch to anyone seeking a reliable identity protection solution.
Please leave a comment below regarding OmniWatch Identity Protection plans.
INTERESTING POSTS