This post will show you how to secure your WordPress website from hackers.
In today’s digital landscape, securing your WordPress website is paramount. WordPress’s popularity as a content management system (CMS) has become a prime target for hackers and malicious actors.
In this post, I will show you the essential steps and best practices to protect your WordPress website from potential security vulnerabilities and keep it safe from unauthorized access.
By implementing these measures, you can enhance the security of your website and mitigate the risk of potential attacks.
Table of Contents
How To Secure Your WordPress Website From Hackers
Here are tips on how to secure your WordPress website from hackers.
1. Keep your computer and network protected
First, you should ensure that your computer is clean and free from viruses and malware.
Perform occasional scanning to locate and eliminate viruses, as they can be anywhere in your system.
Here are some antivirus programs that you can use:
Your network should also be protected; try to avoid visiting websites that are not secure, and do not share your site admin details on any site other than WordPress.
If you use a Windows PC, ensure that the Firewall is active and running whenever you go online.
2. Keep WordPress Core, Themes, and Plugins Updated
Regularly updating your WordPress core installation, themes, and plugins is crucial for maintaining a secure website. Outdated software can have known vulnerabilities that hackers can exploit. Follow these steps:
- Enable automatic updates for the WordPress core, themes, and plugins.
- Regularly check for updates manually and install them promptly.
- Remove unused themes and plugins to minimize potential risks.
READ ALSO: Website Security Check: How Secure Is Your Website?
3. Use Strong and Unique Login Credentials
Weak or easily guessable login credentials make your WordPress website vulnerable to brute-force attacks.
Whenever you want to access the dashboard of your WordPress website, you are to visit the admin login page and log in using a username and password. These details are set by you and you alone should know them.
First, change the default “admin” username to something unique and choose a secure password.
Most WordPress websites get hacked because their owners use weak passwords that are easy for hackers to guess. Implement the following measures:
- Use strong, complex passwords that combine uppercase and lowercase letters, numbers, and special characters.
- Avoid using common passwords or personal information in your login credentials.
- Consider using a password manager to generate and securely store unique passwords for each account.
4. Limit Login Attempts and Enforce Two-Factor Authentication (2FA)
You should know what 2-factor authentication is all about; it is a security process whereby 2 different authentication processes must be completed before access will be granted.
If you are concerned about your WordPress website’s security, then you should be using 2FA. That way, even if hackers manage to get your password, they will find it difficult to bypass the 2FA process.
You can install several 2FA WordPress plugins, but I recommend installing the Google Authenticator plugin. It is a free plugin with a 4.5 out of 5 stars rating by WordPress users.
Limiting the number of login attempts and implementing two-factor authentication adds an extra layer of security to your WordPress website:
- Install a plugin that limits failed login attempts, such as Login Lockdown or Limit Login Attempts.
- Enforce two-factor authentication using a plugin like Google Authenticator or Authy, which requires a second verification step, such as a unique code sent to your mobile device.
READ ALSO: Top 8 WordPress LMS Plugins to Use in 2026
5. Secure Your WordPress Admin Area
The WordPress admin area is a critical access point that requires special attention. Apply the following measures:
- Change the default login URL (/wp-admin/) to a custom one to avoid easy identification.
- Restrict access to the admin area by IP address using plugins like Limit Login Attempts Reloaded or WPS Hide Login.
- Implement a web application firewall (WAF) to filter out malicious traffic and protect against common attacks.
6. Add Security Questions
As with the 2FA Authentication, you can add security questions to your login page. Login will only be accepted if the answer to your security question is entered correctly. This is a very efficient way of securing your WordPress website, as hackers will have difficulty figuring out the answer.
You can use multiple plugins to implement this security process, and you can go for any of them. When setting your questions, avoid very easy ones; even if it’s easy, make sure the answer you provide is not simple.
For example, you can set “What is the name of your Pet?” That’s a relatively easy question, and guess answers would be a dog, cat, etc. Your answer should be something like “A brown hairy dog”; that would be difficult to decipher.
7. Use Reliable Themes and Plugins
Using reputable and regularly updated themes and plugins significantly reduces the risk of vulnerabilities. Follow these guidelines:
- Download themes and plugins from trusted sources, such as the official WordPress repository or reputable third-party marketplaces.
- Read user reviews and ratings before installing any theme or plugin.
- Don’t use nulled themes or plugins, irrespective of how legit they may appear.
- Regularly update themes and plugins to benefit from security patches and bug fixes.
8. Scan your WordPress site
Your WordPress software can become infected by a virus, so you should scan it once in a while to be on the safe side. This can be done using related WordPress plugins or online URL scanners.
Some trusted websites you can use to scan include virustotal.com, siteguarding.com, Wpsec.com and many more.
You are not at risk using these websites as all you supply is just your website’s URL. At the end of a scan, you will get results to know if malware is present or other vulnerabilities in your WordPress site. You will also get insights on how to get rid of them.
9. Secure Your Hosting Environment
The security of your WordPress website is not solely dependent on the CMS itself; your hosting environment also plays a crucial role.
Take the following precautions:
- Choose a reputable hosting provider that prioritizes security and offers features like SSL certificates and firewalls.
- Keep your hosting environment up to date, including the server software, PHP version, and other dependencies.
- Regularly monitor server logs and set up intrusion detection systems to identify potential security breaches.
10. Update your software, themes, and plugins
You must run the latest versions of the themes and plugins you use, as they often carry new security patches.
It would be easier for a hacker to hack old WordPress versions than the new ones, and your site would be at risk if you do not update it.
Also, stay away from unofficial sources of WordPress themes and plugins. Purchase and download from trusted ones only.
11. Back-Up Your Website Regularly
Backing up your website regularly is essential, and it is another tip to secure a WordPress website from hackers that I’ll be talking about.
You should back up your website regularly because if it eventually gets hacked, it would be a lot easier to recover posts, pages, and other things.
Even if your site is not hacked, it can happen to your hosting service provider (Yeah! They get hacked too) and will affect your site.
Backups are easy to perform on WordPress, and the XML files are very low-sized. You can use WordPress plugins to perform site backups at scheduled intervals.
Creating regular WordPress website backups is crucial for recovering from potential security incidents or data loss. Consider the following:
- A reliable backup plugin, such as UpdraftPlus or BackupBuddy, schedules automated backups.
- Store backups in secure, off-site locations like cloud storage or a separate server.
- Test the backup restoration process periodically to ensure its integrity and functionality.
12. Install a Security Plugin
Adding a security plugin can provide additional layers of protection and simplify the implementation of various security measures. Consider the following:
- Install a reputable security plugin like Sucuri, Wordfence, or iThemes Security.
- Configure the security plugin to perform regular scans for malware, monitor file integrity, and block suspicious IP addresses.
- Enable features like firewall protection, brute force attack prevention, and login lockdown options provided by the security plugin.
13. Protect Against Malware and Vulnerabilities
Malware and vulnerabilities can compromise the security of your WordPress website. Take the necessary steps to protect against them:
- Regularly scan your website for malware using security plugins or online tools like VirusTotal.
- Remove any malicious code or infected files identified during the scanning process.
- Update your security plugin’s malware signature database to protect against the latest threats.
14. Educate Yourself and Your Users
Security is a shared responsibility. Educate yourself and any users who have access to your WordPress website about best security practices:
- Stay informed about the latest security threats and vulnerabilities related to WordPress.
- Train users on the importance of using strong passwords, identifying phishing attempts, and avoiding suspicious links or downloads.
- Encourage users to report any suspicious activities or potential security breaches immediately.
15. Disable File Editing within the WordPress Dashboard
WordPress allows administrators to edit theme and plugin files directly from the dashboard by default. However, disabling this feature can prevent unauthorized access and minimize the risk of accidental code modifications. To disable file editing:
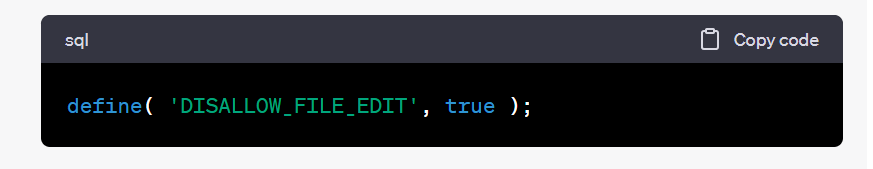
- Open the
wp-config.phpfile of your WordPress installation. - Add the following line of code before the “That’s all, stop editing!” comment
- Save and upload the modified
wp-config.phpfile back to your server.
Disabling file editing adds an extra layer of security, as even if an attacker gains access to your WordPress admin area, they won’t be able to modify your theme or plugin files directly.
Remember to always take a backup of your wp-config.php file before making any modifications for safety purposes.
By implementing this additional security measure, you further reduce the potential attack surface and enhance the overall security of your WordPress website.
Conclusion
Securing your WordPress website from hackers requires a proactive approach and a combination of technical measures, regular updates, and user awareness.
Implementing the steps outlined in this comprehensive guide can significantly reduce the risk of unauthorized access, malware infections, and other security breaches.
Maintaining a secure website is an ongoing process, so stay vigilant, keep up with the latest security practices, and regularly review and update your security measures to protect your valuable online presence.
By following the security tips listed in this article, you should be able to secure your WordPress website from hackers.
INTERESTING POSTS
- 10 Best Antivirus for a Basic Laptop [Must Read]
- Use Utopia P2P Ecosystem! Keep Your Eyes Open!
- The Ultimate WordPress Security Guide
- Nulled WordPress Themes And Plugins: Why using them is a security risk
- 5 Ways To Improve The Security Of Your Magento eCommerce Store
- 5 Most Common WordPress Attacks
- How To Secure Your Magento Website
- How to Choose the Best AI App for Safe and Anonymous Chatting