Here is a beginner’s guide to using a product video maker like a Pro.
Creating compelling video content is essential for capturing audience attention and boosting product visibility.
Table of Contents
Step-by-step guide: Using Pippit AI’s product video maker
In today’s fast-paced digital world, high-quality video content is key to capturing attention and boosting product visibility. Pippit AI is an innovative product video maker that allows anyone—from beginners to marketers—to create professional-grade product videos quickly and easily.
With its AI-powered features, you can generate videos from simple product links, images, or text, and customize them with voiceovers, avatars, and brand elements.
Whether you’re promoting a product on social media or creating content for your website, Pippit streamlines the entire video creation process. This guide will walk you through each step to help you make the most of Pippit AI.
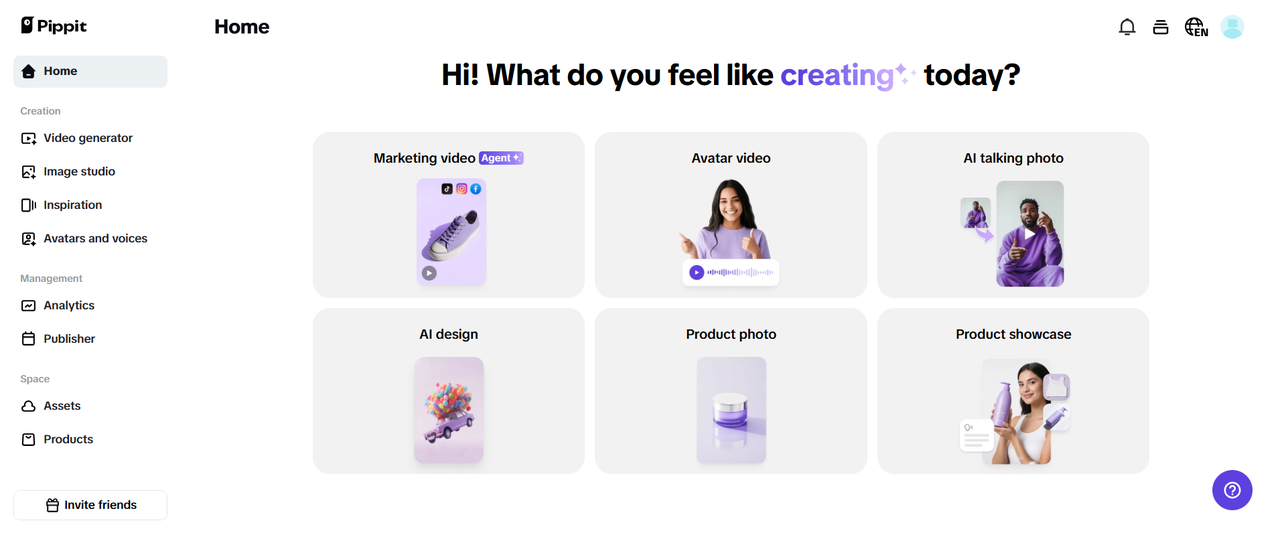
Step 1: Navigate to the “Video generator” section
Begin your video creation journey by first signing up for Pippit, using the weblink provided above. Once done, head over to Pippit’s homepage and then click on the “Video generator” option.
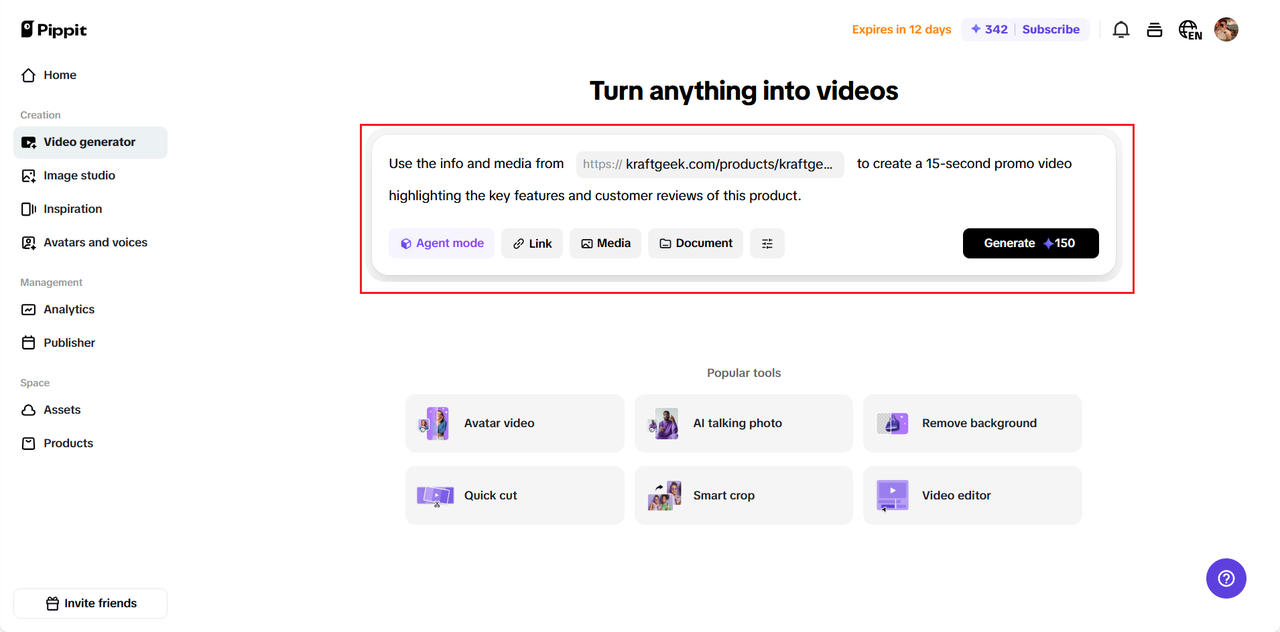
After that, you will be asked to either provide a product link, upload a picture of the product, enter a text prompt, or upload a relevant document, for which you are creating the desired content.
After providing your input, choose between Agent mode (more intelligent, for all video types) or Lite mode (faster, mainly for marketing videos) to start generating your video.
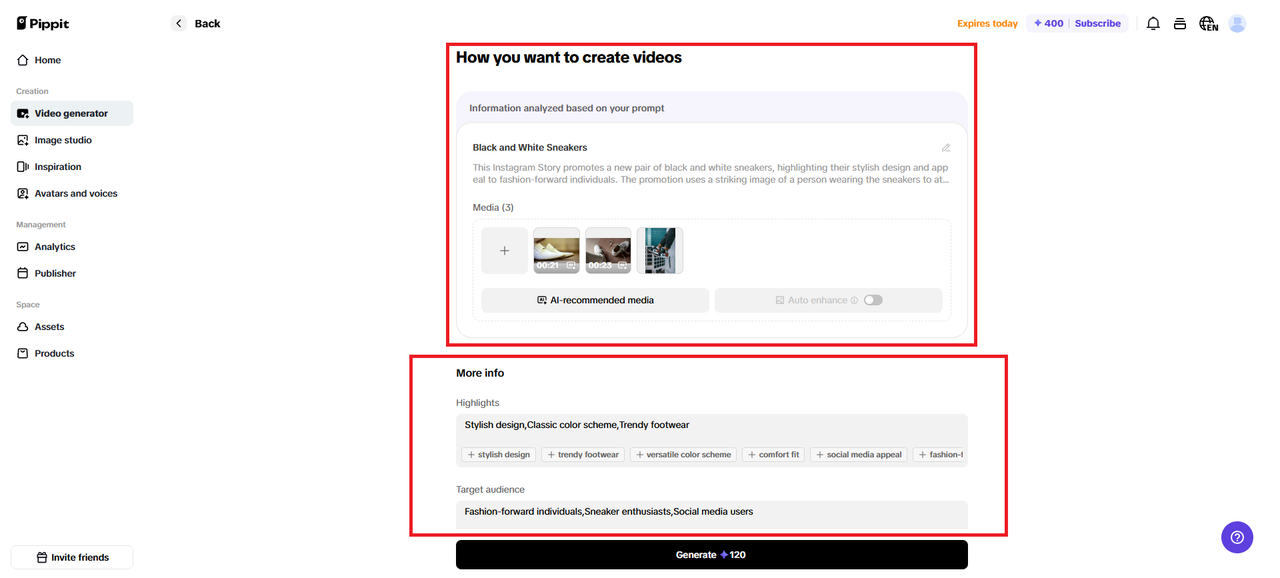
Once you do that, a new page “How you want to create video” will appear, where you will need to provide the name of the topic/theme as well as state additional details, such as the topic highlights, target audience, etc.
After that, scroll down on the same page till you reach the “Video types” and “Video settings” options.
This is where you can select the type of product video you want Pippit to create, as well as choose the video avatar and voice, the aspect ratio for the video, the video’s language, and the approximate length. Once you select your preferred options, click on “Generate”.
Step 2: Let AI create & edit your video
Pippit will start generating your videos and take just a few seconds to complete the process.
Once finished, you’ll see several AI-generated video options to choose from. Take your time to browse through them and pick the one that best fits your needs. When you find a video you like, hover your mouse over it to reveal options like “Change video,” “Quick edit,” or “Export.”
If none of the videos meet your expectations, simply select “Create new” to generate a fresh batch.
For quick adjustments, click “Quick edit” to easily modify your video’s script, avatar, voice, media, and text inserts. You can also customize caption styles, perfect for Instagram Story videos.
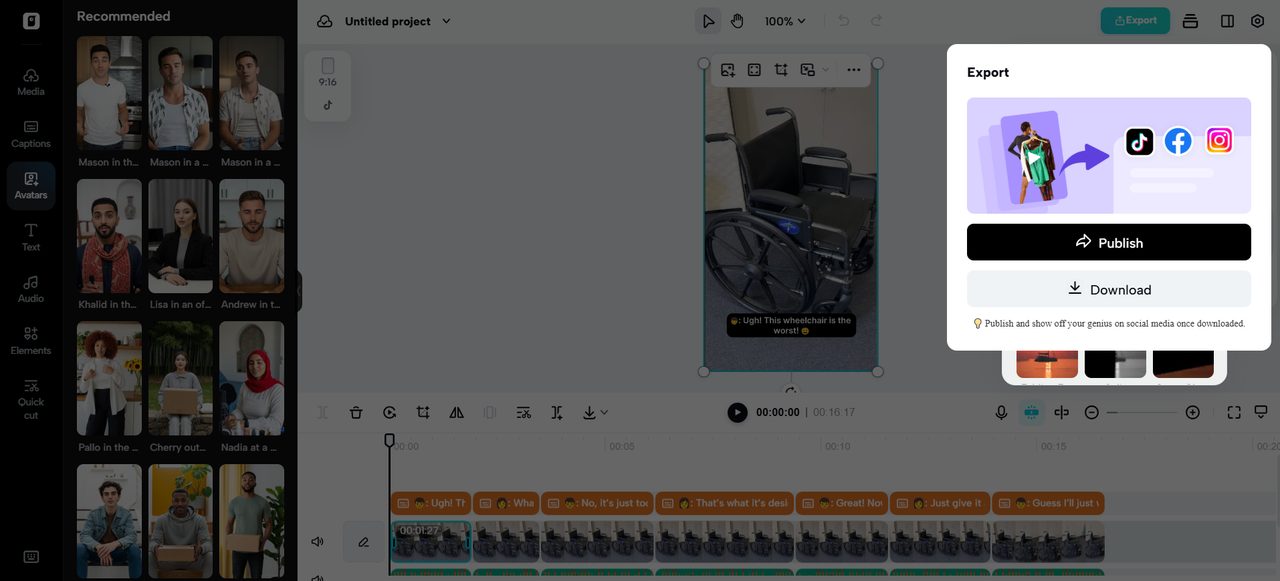
Step 3: Preview and export your video
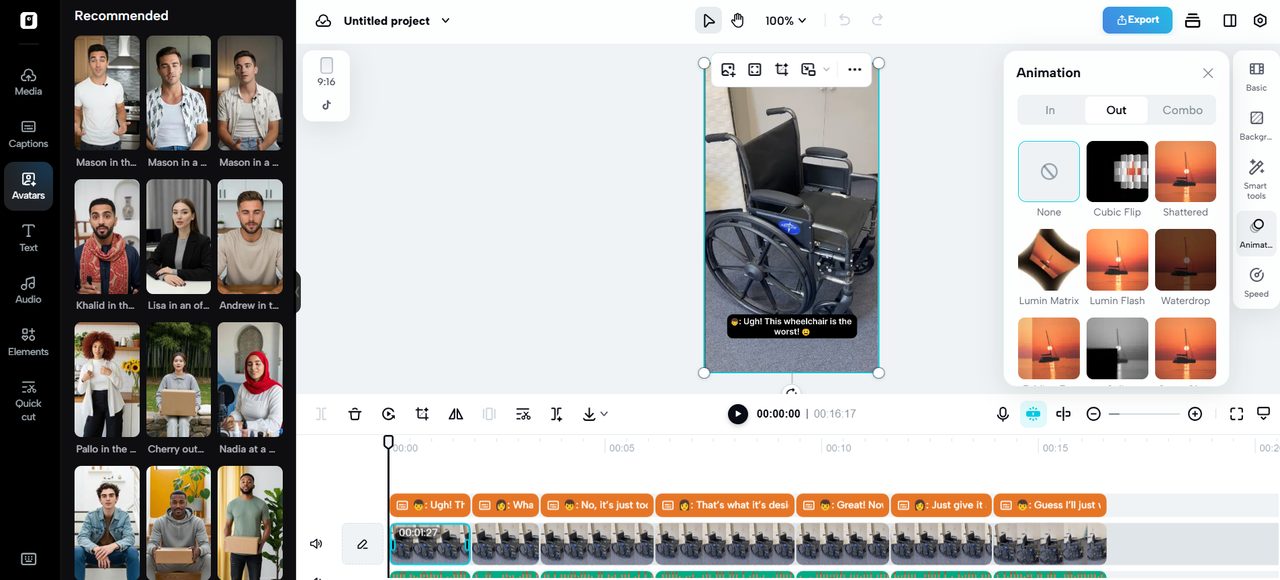
If you want more control over your video editing, select the “Edit more” option to access an advanced timeline editor.
Here, you can fine-tune color balance, use powerful Smart tools, remove backgrounds, reduce audio noise, adjust video speed, add effects and animations, and incorporate stock photos and videos—plus many other exciting features.
Once you’re satisfied with your edits, click “Export” to download the video to your device. From there, you can share it across your social media platforms, especially Instagram.
Alternatively, you can directly “Publish” the video to Instagram or cross-post it to TikTok, Facebook, and other channels.
Tips for creating stunning product videos
Start with high-quality product images
Add a voiceover for clear messaging
Keep your branding consistent
Incorporate your brand’s colors, logo, and fonts throughout the video for a cohesive look. Consistent branding helps build trust and makes your content instantly recognizable. Even subtle touches can leave a lasting impression and strengthen your overall brand identity.
Conclusion
Creating professional product videos doesn’t have to be complex or time-consuming—especially with tools like Pippit AI. From generating videos using product links to customizing with voiceovers, avatars, and branding, Pippit simplifies the entire process for beginners and pros alike.
By starting with high-quality visuals, using AI-powered voiceovers, and maintaining consistent branding, you can produce engaging, polished videos that resonate with your audience.
Whether you’re promoting on Instagram, TikTok, or your website, these videos can significantly boost visibility and conversions. With the right tools and a bit of creativity, you’ll be creating stunning product videos that truly showcase your brand.
INTERESTING POSTS
- 12 Companies For Outsourcing Web Development [MUST READ]
- Image to Video AI: What It Is and How to Use It Effectively
- How To Streamline The Customer Journey With Omnichannel Integration
- AI Transforming Manufacturing Innovation, Branding, and Customer Interactions
- The Best ISP Proxies [Tested, Reviewed & Ranked]
- Demystifying Cryptocurrency: A Beginner’s Guide to Playing at Crypto Casinos
- Photography Supplies: What You Need to Take Great Photos