In this post, I will show you the top 5 cybersecurity threats that eCommerce websites should watch out for.
The e-commerce industry has always been a bonne bouche for spammers, hackers, and cybercriminals of all shades. With intruders’ methods becoming more complicated, the consequences more destructive, and the number of companies affected growing at an exponential rate, online businesses have to think through actionable strategies to strengthen their security maturity and protect their assets against cyber threats.
From data leaks and financial charges to disrupted customer trust and compromised trade secrets – the slightest security vulnerability can lead to immense damage.
Understanding your enemies is the first step toward building an unbreachable wall around your business. As such, knowing the major security threats that e-commerce websites face will assist entrepreneurs in developing robust strategies to repulse an assault.
READ ALSO: Web Security Guide: Keeping Your Website Safe
Table of Contents
Top 5 Cybersecurity Threats That eCommerce Websites Should Watch Out For
1. DDoS Attacks
Firstly, among the top 5 cybersecurity threats that eCommerce websites owners encounter is DDoS.
DDoS is one of the oldest tricks that is still a concern for IT departments. Distributed Denial of Service attacks are considered “old-fashioned,” but the threat is often underestimated.
In a nutshell, DDoS is a malicious attempt to disrupt servers by overwhelming the targets with tons of traffic so that the servers cannot serve legitimate requests. Hackers leverage such specific apps as LOIC (a network stress-testing tool that is used to launch a DDoS attack from a web browser) to overload targets with UDP, TCP, and HTTP packets.
READ ALSO: Exclusive Interview With Vladimir Fomenko, Founder Infatica
For e-commerce businesses, a successful attempt may result in millions in lost revenue, apart from significant reputational damage caused by ongoing downtime and ruined favorable image.
| For example, Lieferando, the German service that delivers food to more than 15,000 restaurants, became a victim of a massive DDoS attack during the COVID pandemic. Cybercriminals have demanded two bitcoins (about $11,000) to stop the flood of traffic. As the hackers wronged Lieferando’s server, they couldn’t process the orders and had to return money to their clients. |
It is worth mentioning that DDoS attacks can serve as a shield for serious data thefts. While all the efforts of an IT department are focused on handling the traffic flood, cybercriminals can leverage a known vulnerability to steal your data on the sly. According to Kaspersky research, 26% of DDoS attacks lead to data loss.
The most common DDoS protection techniques include:
- Implementing CDN or smart DSN adds an extra layer for resolving DNS queries.
- Placing computation resources behind load balancers minimizes the attack surface and restricts traffic to some parts of the infrastructure.
- Using firewalls or ACLs to get complete control over the traffic that reaches their websites.
2. Ransomware
Among our list of cybersecurity threats that eCommerce websites should watch out for is ransomware. Ransomware is a form of financial fraud that can become a full-scale business model for some criminal elements. Because you don’t have to possess solid coding skills to execute this attack, the number of e-commerce businesses, as well as financial organizations of all shades, affected by the threat is increasing.
With ransomware, a target gets an email with a malicious link embedded or a file attached. Once the victim clicks to the link that leads to an infected website or downloads the file, a cryptoworm is spreading like wildfire, encrypts essential data (photos, documents, databases) and, in some cases, the entire system.
Cybercriminals demand a ransom to restore access upon payment. Since ransom is usually asked for in Bitcoins, the hackers’ personalities are difficult to identify.
READ ALSO: 3 Critical Cybersecurity Questions To Ask Before Buying a Marketing SAAS Product
There are only two ways for this kind of malicious software to penetrate the system:
- Through phishing emails that can look like they are from a trustworthy company or someone you know.
- Through visiting infected Internet resources.
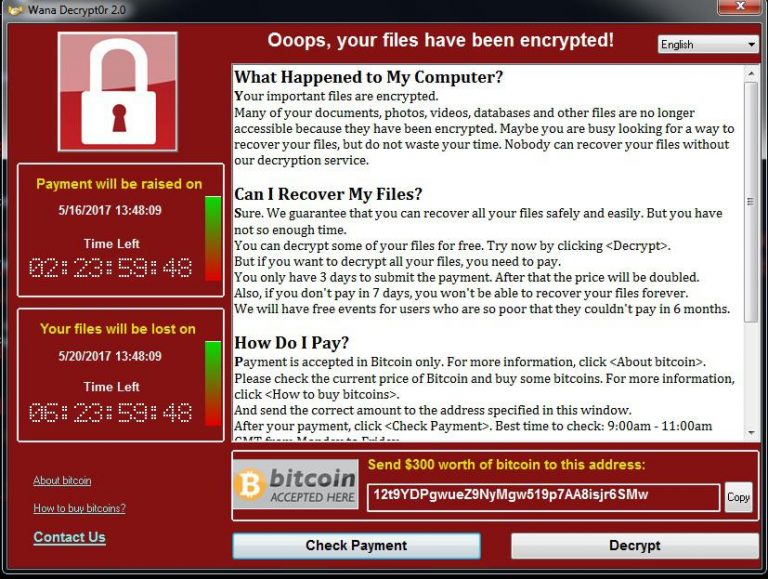
For example, the WannaCry attacks turned out to be a global pandemic 2017. The virus has affected many e-commerce websites, many of which have decided to pay a ransom to the cybercriminals to get a decryption key. Below you can see the WannaCry warning message that has appeared on many screens worldwide.
Unfortunately, in most cases, once the ransomware has been released into your device, there is little you can do unless you have ongoing security software or backup. Some companies pay a ransom to regain access to the locked files.
However, this does not guarantee that the criminals will give you the key as promised. Besides, paying a ransom doesn’t protect your site against repetitive attacks, with higher demand than the previous one. Data recovery is both a sophisticated and expensive process that sometimes requires the help of experienced professionals.
A piece of good news is that there are some ways for e-commerce business owners to prevent this form of cyber threat:
- Installing the Microsoft patches to prevent the virus from spreading within your network
- proper employee education and technoliteracy increasing
- updating antivirus and antimalware software regularly
- visit nomoreransome.org if your files have been encrypted
- regular backups
3. SQL-injections
Preventing SQL injections should be an inherent part of your security checklist. With this attack, hackers leverage loopholes in the back end to insert malicious code in a query and make it executed.
As a result of unsanitized user input, a hacker gains full control over the infected store. This allows them to modify the store’s content, delete the entire database, steal credit card details, and expose admin credentials to open the door for further attacks.
READ ALSO: Could A Keylogger Be Spying On You? – All You Need To Know
The malicious query has only three rooms to reach your website database:
- known loopholes in modules and plugins
- security vulnerabilities in custom code
- bugs in the e-commerce platforms the site runs on.
| In 2019, a critical Magento vulnerability – PRODSECBUG-2198 – was discovered. Being one of the most popular e-commerce platforms, Magento powers more than 300,000 online stores that were at risk of credit card skimming with the vulnerability. |
So, to contradict SQL injections, you need to close the doors for those three routes. Keep your system updated, install proper security patches, and regularly conduct security checks with automated testing tools to identify and correct these bugs ASAP. Thus, you may need the help of experienced developers who know how to make your website secure.
4. Malicious Bots
Malicious bots pose a severe concern for e-commerce business owners. This self-propagating software is developed to scan websites for security vulnerabilities and leverage them to carry out fraudulent activity and report this information to the botmaster.
As such, bad bots can steal your pricing data, scrape your inventories, spam, perform checkout fraud, overload a server infrastructure, and slow down the website speed. Therefore, protecting your business against bad bots should be integral to your security checklist.
READ ALSO: Importance of CAPTCHA in Web Security
However, bot activity is not easy to identify. The latest generation can mimic human behavior in a very natural way so that it is hard to distinguish a bot from a real user.
Make sure you run to cover by implementing the following strategies:
- Install a server firewall that blocks the illegitimate traffic.
- Set up firewall rules for a web server. The filters will let the server determine which packets can go through the firewall and which are not. Let’s assume that you’ve discovered that some strange traffic was coming from a particular location, say, India or China. Thus, you may restrict all the traffic from these locations by a single firewall rule.
- Use Cloudflare or another reverse proxy with built-in bot management tools.
5. Cross-Site Scripting (XSS)
Protecting your website against Cross-Site Scripting is essential. Even Google has launched the reward program where it promises to pay $10, 000 to the developer or cybersecurity expert who can detect an XSS vulnerability in its network.
READ ALSO: How To Secure And Protect A Website [We Asked 38 Experts]
XSS targets authentication information: names, tokens, passwords, and email addresses. Once a cybercriminal gains access to this data, they can exploit the user’s account whatever they want.
For example, if a hacker gets to know, say, the user’s credit card number connected to the store, they can use this data to make fraudulent orders or change the shipping destination.
| Cross-site scripting threatens e-commerce stores of all sizes. As such, auction giant eBay was spotted at missing out a critical XSS vulnerability that made the site tempting to hackers’ attacks. The cybercriminals have exploited the loophole in the site to inject malicious code into several listings for cheap iPhones and redirect users to a phishing page designed to harvest user log-ins for the hackers. |
Summarizing
Apart from these top 5 cybersecurity threats that eCommerce websites owners encounter, there are others as well. With the rise of artificial intelligence and modern technologies, attacks on online stores and websites are becoming increasingly sophisticated.
READ ALSO: Summer Sales: Top Cybersecurity Products Special Offers And Deals
Some experts believe we are on the threshold of the cyber arms race. To build an impenetrable wall around the business and win in this wrecking war, entrepreneurs have to know their enemies and invest in this scope as much as they spend on the other fields.
Note: This was initially published in October 2020, but has been updated for freshness and accuracy.
INTERESTING POSTS
- Top 6 Hacks To Secure Your eCommerce Site Against Cyber Threats
- Macropay Scam Alert: Fake E-Commerce Sites
- 3 Easy Steps To Boost Security For Your eCommerce Business
- Payment Challenges: How E-Commerce Businesses Can Deal With Payment Errors
- E-Commerce Fraud: Navigating the Challenges in Online Retail
- The State of Romanian E-Commerce Security 2026: A Case Study of the Children’s Goods Sector
About the Author:
Daniel Segun is the Founder and CEO of SecureBlitz Cybersecurity Media, with a background in Computer Science and Digital Marketing. When not writing, he's probably busy designing graphics or developing websites.