The social media landscape witnessed a shocking event on July 15th, 2020. Twitter, a platform boasting over 330 million monthly users at the time, was struck by a cyberattack that compromised the accounts of prominent celebrities and corporations.
This wasn’t a random targeting of a few profiles; verified accounts with millions of followers, including those belonging to Elon Musk, Apple, Joe Biden, Jeff Bezos, and even former presidents like Barack Obama, were hijacked.
Table of Contents
2020 Twitter Hack: A Daring Bitcoin Scam
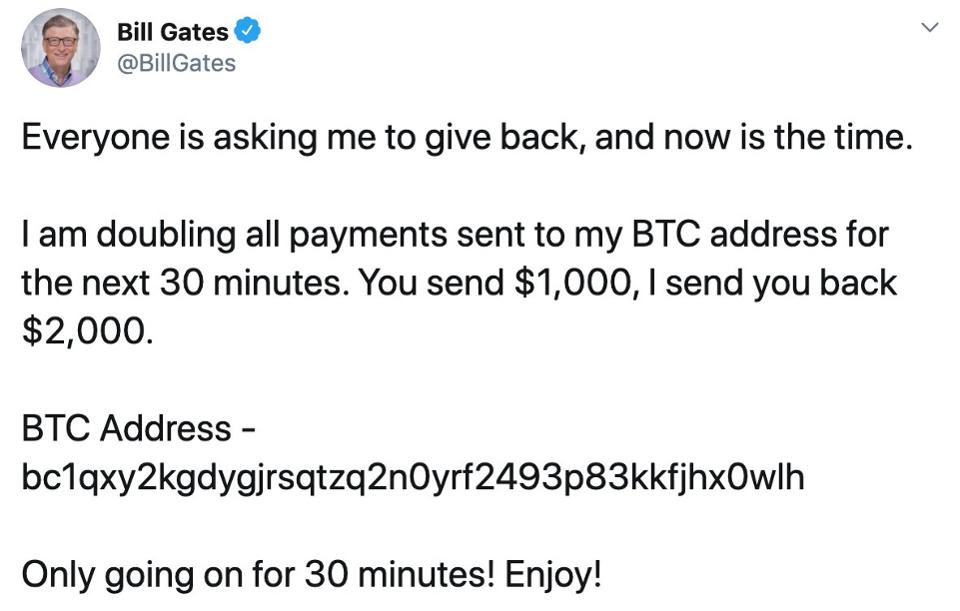
The motive behind the hack was a brazen Bitcoin scam. Hackers gained control of these high-profile accounts and tweeted messages promising to double any Bitcoin sent to specific wallet addresses.
The tweets, often crafted to appear legitimate, enticed unsuspecting users. A common tactic involved requesting $1,000 in Bitcoin with the promise of receiving $2,000 in return.
The allure of doubling their money proved irresistible to some, leading to a reported loss of over $100,000 in stolen Bitcoin.
A Sophisticated Breach Exposes Security Gaps
The scale and sophistication of the attack were unprecedented. Investigators concluded it wasn’t a random attempt but a meticulously planned operation.
Hackers breached Twitter’s internal systems, bypassing security measures to gain control of these highly coveted accounts. The ease with which they navigated Twitter’s defenses pointed towards potential vulnerabilities within the platform itself.
Twitter Reacts and Locks Down Accounts
Hours after the initial breach, Twitter acknowledged the situation through its official support channel.
While details remained scarce, they advised users to reset their passwords and implement additional security measures. Notably, some verified accounts were temporarily restricted from tweeting, presumably to prevent further exploitation.
Social Media’s Vulnerability to High-Profile Scams
The incident highlighted the susceptibility of social media platforms to cyberattacks, particularly those targeting high-profile accounts. Bitcoin scams, although not new on Twitter, were amplified by the sheer number of compromised accounts involved.
Leveraging the trust associated with verified profiles, the hackers effectively bypassed the skepticism users might usually hold towards such financial offers.
READ ALSO: Controlling Data Breach And The Use Of DRM For Document Security
Tracing the Hackers: A Challenge in the Blockchain Age
Unfortunately, the decentralized nature of Bitcoin transactions made tracing the perpetrators a significant challenge.
Publicly available wallet addresses offered little in identifying the hackers, as the blockchain technology behind Bitcoin prioritizes anonymity.
Unconfirmed Rumors and Questions of an Insider Job

Amidst the chaos, unconfirmed reports on Twitter emerged, pointing the finger at a former Twitter developer, Samuel Hyde (@inteldotwav). However, Twitter never officially addressed this claim, leaving the true identity of the hackers shrouded in mystery.
The possibility of an “inside job” raised crucial questions about Twitter’s internal security protocols. If the breach originated from within the company, it indicated a significant vulnerability in access control and employee vetting procedures.
Individual Responsibility: Securing Your Accounts
However, focusing solely on the attacker diminishes the importance of individual account security. Regardless of the hack’s origin, Twitter users have a responsibility to safeguard their accounts.
Fortunately, Twitter offers robust security features like two-factor authentication (2FA), which adds an extra layer of protection during login attempts. Implementing 2FA significantly strengthens your account’s resilience against unauthorized access.
Read Also: The Must Dos And Don’ts For Protecting Your Password And Personal Data
Beyond 2FA: The Importance of Strong Passwords
Beyond 2FA, the importance of strong passwords cannot be overstated. Complex passwords incorporating a mix of uppercase and lowercase letters, numbers, and symbols are significantly harder to crack than simple, predictable phrases. Regularly changing your password further enhances security.
2020 Twitter Hack: Frequently Asked Questions
How did Twitter get hacked?
The attackers used social engineering, a tactic where they manipulated people into giving away information. They likely targeted Twitter employees with phishing emails or phone calls, tricking them into revealing login credentials or access to internal systems. This gave the hackers a foothold within Twitter, allowing them to hijack high-profile accounts.
READ ALSO: Identity Protection Explained in Fewer than 140 Characters
What was the Twitter phishing case in July 2020?
The July 2020 Twitter hack involved a social engineering attack that compromised numerous verified accounts. Hackers gained access and used them to promote a Bitcoin scam, defrauding unsuspecting users.
When was Twitter last hacked?
There have been other hacking incidents on Twitter besides the July 2020 event. However, it’s important to note that successful large-scale hacks like this one are uncommon.
How many accounts were hacked on Twitter?
Twitter has undisclosed the exact number of hacked accounts in July 2020. However, reports suggest it involved over 130 accounts, including many high-profile verified users.
How do your accounts get hacked?
There are various ways your accounts can be hacked. Phishing emails and fake websites are common methods. Here are some tips to protect yourself:
- Be cautious of suspicious emails and links. Don’t click on links or attachments from unknown senders.
- Use strong, unique passwords for each account. Consider a password manager to help you create and manage complex passwords.
- Enable two-factor authentication (2FA) on all your accounts whenever possible. This adds an extra layer of security during login attempts.
- Beware of social media scams. If an offer seems too good to be true, it probably is. Don’t send money or personal information based on unsolicited messages.
A Lasting Impact: Lessons Learned
The 2020 Twitter hack served as a stark reminder of the ever-evolving cyber threat landscape. It exposed vulnerabilities within the platform and highlighted the importance of user vigilance.
By implementing robust security measures like 2FA and strong passwords, users can take control of their online safety. Social media platforms are also responsible for continually strengthening their defenses and prioritizing user account security.
This Twitter hack incident serves as a cautionary tale, urging users and platforms to remain vigilant and proactive in the face of evolving cyber threats. The digital landscape is constantly changing, and both individual and collective efforts are crucial to maintaining a secure online environment.
Note: This was initially published in July 2020, but has been updated for freshness and accuracy.
INTERESTING POSTS
About the Author:
John Raymond is a cybersecurity content writer, with over 5 years of experience in the technology industry. He is passionate about staying up-to-date with the latest trends and developments in the field of cybersecurity, and is an avid researcher and writer. He has written numerous articles on topics of cybersecurity, privacy, and digital security, and is committed to providing valuable and helpful information to the public.
Christian Schmitz is a professional journalist and editor at SecureBlitz.com. He has a keen eye for the ever-changing cybersecurity industry and is passionate about spreading awareness of the industry's latest trends. Before joining SecureBlitz, Christian worked as a journalist for a local community newspaper in Nuremberg. Through his years of experience, Christian has developed a sharp eye for detail, an acute understanding of the cybersecurity industry, and an unwavering commitment to delivering accurate and up-to-date information.





Why on earth would Twitter remain mute and verifying the alleged person.
Well, thanks for this news