Do you want to encrypt your Windows PC with a Pen drive or USB drive?
Ever wished you could add a touch of secret agent flair to your PC security? Imagine locking your computer simply by removing a pen drive and unlocking it with its swift insertion – just like a high-tech key.
Well, with the help of readily available software, you can turn this fantasy into reality! This guide explores two popular methods for locking and unlocking your Windows PC using a pen drive:
In this post, I will show you how to use your flash drive to lock and unlock your PC. This tutorial will guide you through the process.
READ ALSO: 5 Do’s and Don’ts For Using USB Flash Drives
Table of Contents
How To Lock And Unlock Your PC With A Pen Drive
Method 1: Using Predator
Predator is a free and user-friendly software that transforms your pen drive into a physical security key. Here’s how to use it:
Download and Installation
Head to the Source: Download Predator from a reputable source. A quick Google search for “Predator USB Lock software” should lead you to the developer’s website. Avoid downloading from untrusted sources to ensure the legitimacy of software and prevent potential malware.
Installation Simplicity: Once downloaded, run the installation file. The installation process is typically straightforward – just follow the on-screen instructions. The Predator will likely request administrative privileges during installation. Granting these permissions is necessary for the software to function correctly.
READ ALSO: What Programming Skills Do Pen Testers Need?
Setting Up Your Pen Drive Key
Launch Predator: Once installed, locate and launch the Predator program on your PC. The interface should be reasonably intuitive, even for non-technical users.
Choose Your Guardian: Predator refers to your pen drive as the “Guardian Key.” Locate the option to “Create Guardian Key” or similar wording within the software’s interface.
Insert and Select: With Predator running, insert your desired pen drive into a USB port on your computer. The software should automatically detect the pen drive. Select the detected pen drive from the options presented within Predator.
Password Backup (Optional): While Predator relies on the physical presence of the pen drive for access, creating a backup password is a wise precaution. This password can be used if you lose your pen drive or encounter technical issues. Look for an option to “Set Backup Password” and select a robust, unique password that you can easily remember.
Activation: After selecting your pen drive and choosing a password (if desired), follow the on-screen prompts to activate your pen drive as the guardian key. This might involve a brief formatting process on the pen drive, so ensure it doesn’t contain any critical data.
Locking and Unlocking with Your Pen Drive
Automatic Lock: With the Predator set up, your PC automatically locks whenever you remove the pen drive from the USB port. This is ideal for situations where you need to step away from your computer for a short while and want to ensure instant security.
Unlocking with the Key: Simply insert the designated pen drive back into the USB port to unlock your PC. Predator will detect the pen drive and automatically unlock your computer, granting you access.
Backup Password (if set): In case you lose your pen drive or encounter issues with automatic unlocking, you can use the backup password you created earlier. Look for Predator’s “Unlock with Password” option and enter your backup password to regain access.
READ ALSO: Is Windows Defender Enough for 2024?
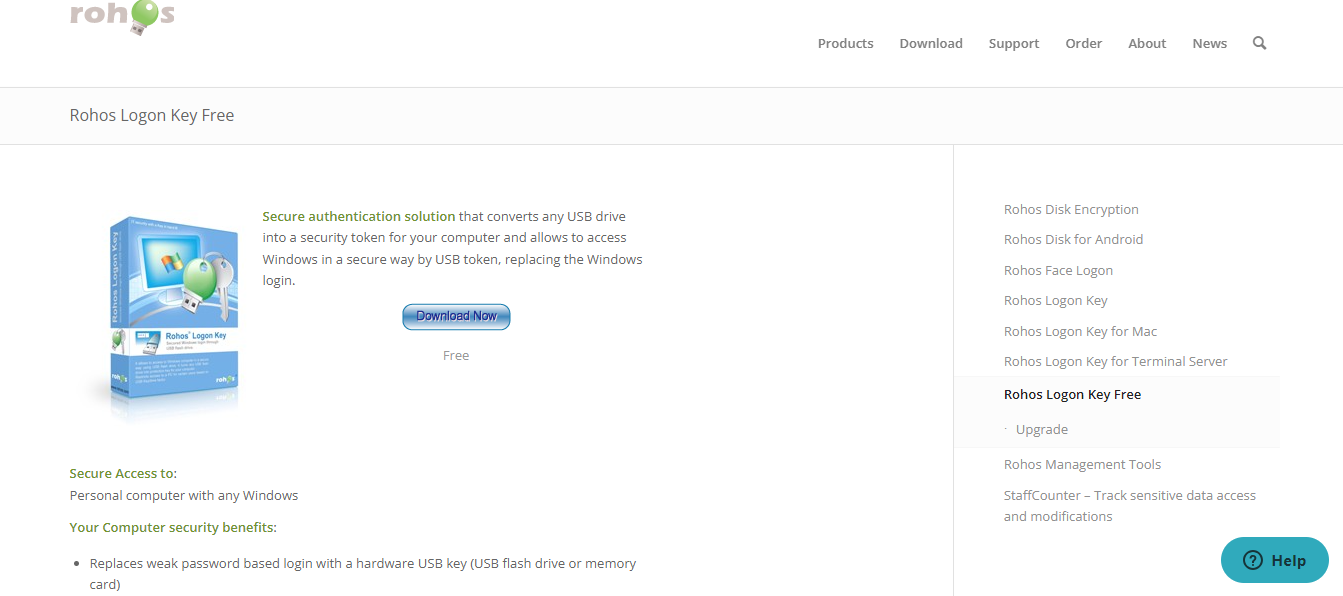
Method 2: Using Rohos Logon Key
Rohos Logon Key offers a more feature-rich solution than Predator. Most importantly, it allows you to lock the PC effortlessly. Although it offers a free trial, unlocking its full potential requires a paid license.
Here’s a breakdown of using Rohos Logon Key:
Download and Installation
Official Source: Download the Rohos Logon Key from the official website (a quick web search for “Rohos Logon Key” should get you there). Downloading software directly from the developer’s homepage ensures authenticity and helps avoid potential security risks.
Installation: Run the downloaded installation file and follow the on-screen instructions. The installation process might request administrative privileges necessary for the software to function correctly.
Setting Up Your Pen Drive Key
Launch Rohos: Once installed, locate and launch the Rohos Logon Key program on your PC. The interface may be slightly more complex than Predator’s, but it still prioritizes user-friendliness.
Wizard Guidance: Rohos will likely guide you through a setup wizard. Follow the on-screen instructions carefully.
Choose Your Guardian: Similar to Predator, Rohos uses the term “USB Key” to refer to your pen drive. Look for the option to “Create USB Key” or similar wording within the wizard.
Insert and Select: With Rohos running, insert your desired pen drive into a USB port on your computer. The software should automatically detect the pen drive. Select the detected pen drive from the options presented within Rohos.
Password Options: Rohos offers more flexibility than Predator in terms of password options. You can choose to:
- Enable Automatic Login with USB Key: This option functions similarly to Predator, where the PC unlocks automatically upon inserting a USB drive.
- Set a Login Password: In addition to the pen drive, you can create a traditional password for login redundancy. This allows you to access your PC even if you lose your pen drive, provided you remember the password.
- Two-Factor Authentication (2FA): For enhanced security, Rohos allows you to enable two-factor authentication. This requires the pen drive and a unique code from your smartphone app to unlock the PC, offering an extra layer of protection.
- Encryption (Optional): Rohos offers the option to encrypt a hidden partition on your pen drive. This encrypted partition can be used to store sensitive data that is only accessible when you unlock your PC with the pen drive.
Activation: After selecting your pen drive, password options (if applicable), and any encryption settings (optional), follow the on-screen prompts to complete the setup process. This might involve a brief formatting process on the pen drive, so ensure it doesn’t contain any critical data.
READ ALSO: How To Download And Install CyberGhost VPN On Your PC [Windows & Mac]
Locking and Unlocking with Your Pen Drive
Locking Options: Rohos offers more control over locking behaviour. You can choose to:
- Automatic Lock on System Idle: The PC will lock automatically after a period of inactivity that you define.
- Manual Lock via Hotkey: You can assign a keyboard shortcut to lock your PC manually whenever needed.
Unlocking with the Key: Depending on your chosen settings:
- Automatic Unlock: If you opt for automatic login with the pen drive, your PC will unlock automatically when the pen drive is inserted.
- Manual Unlock with Password: If you set a login password, you can unlock the PC by entering the password after inserting the pen drive.
- Two-Factor Authentication: For enhanced security, you’ll need the pen drive and the unique code from your smartphone app to unlock the PC.
READ ALSO: iPhone Can’t Unlock? Easiest iPhone Unlock Workaround Here
Essential Considerations Before You Begin
- Data Backup: Always back up any critical data stored on the pen drive you plan to use, as it might be formatted during setup.
- Losing the Key: While convenient, consider the implications of losing your pen drive. Ensure you have a backup password or recovery method (if applicable) to avoid getting locked out of your PC.
- Software Choice: Predator offers a free and straightforward solution, while Rohos provides more features but requires a paid license for full functionality. Choose the option that best suits your needs and comfort level.
- Technical Knowledge: Although both methods are user-friendly, having some basic computer knowledge may be helpful during setup, especially with Rohos Logon Key.
READ ALSO: How To Secure Your USB Flash Drive
Beyond the Pen Drive: Additional Security Measures
Locking your PC with a pen drive adds a layer of physical security. However, consider these additional measures for a comprehensive security posture:
- Strong Passwords: Create strong and unique passwords for your Windows account and other online services.
- Automatic Updates: Enable automatic updates for your Windows operating system and software to ensure you have the latest security patches.
- Antivirus and Anti-malware Software: Install a reputable antivirus and anti-malware program to protect your PC from malicious software and online threats.
- Two-Factor Authentication (2FA): Enable two-factor authentication wherever possible for added security beyond just passwords.
Conclusion
Locking your PC with a pen drive offers a convenient and unique way to enhance physical security.
By following the steps outlined above and considering the additional security measures, you can create a more robust defence against unauthorized access to your computer.
I want you to know that security is an ongoing process. Stay informed about evolving threats and maintain reasonable security practices to protect your digital life.
Were you able to unlock your Windows PC with a pen drive? Let us know by commenting below.
Note: This was initially published in October 2019 but has been updated for freshness and accuracy.
RELATED POSTS
- How to set up a new Computer
- Best System Optimization Tools
- 4 of the Best Cloud Backup Services for personal use
- Firefox Lockwise: What is it? Benefits, Features, & How to Download?
- 8 Best Cybersecurity Practices for Website Owners
- 5 Security Hacks To Ensure Your Telemedicine Apps Are Safe To Use
- What is Penetration Testing? Importance, Types and Process
About the Author:
Daniel Segun is the Founder and CEO of SecureBlitz Cybersecurity Media, with a background in Computer Science and Digital Marketing. When not writing, he's probably busy designing graphics or developing websites.