Here, we will show you what Zero Trust Architecture is all about, its concepts, and why it emerging as a new cybersecurity paradigm.
But, first, let’s start with the history of Zero Trust.
Table of Contents
The History Of Zero Trust
Zero Trust is a strategic effort that aims to eliminate the idea of trust from an organization’s network architecture, therefore reducing the likelihood of successful data breaches like the Pipeline Oil Ransomware attack.
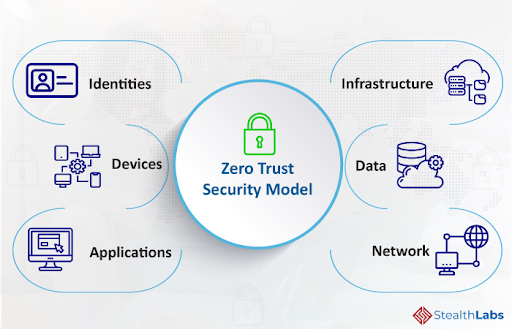
Zero Trust is built on the idea of “never trust, always verify,” and it uses network segmentation, lateral movement prevention, Layer 7 threat prevention, and granular user-access management to secure modern digital environments.
During his time as a vice president and lead analyst at Forrester Research, John Kindervag developed Zero Trust after realizing that existing security approaches are built on the outmoded notion that everything inside a network should be trusted.
It is believed that a user’s identity is not stolen and that all users take responsibility and can be trusted under this broken trust paradigm. Trust is a weakness, according to the Zero Trust paradigm. Users, including threat actors and malevolent insiders, are free to roam about the network and access or exfiltrate any data they want once they’re connected.
The Jericho Forum in 2003 discussed the trend of de-parameterisation and the problems of establishing the perimeter of an organization’s IT systems. BeyondCorp, a zero-trust architecture developed by Google, was launched in 2009.
The reporting and analysis done by Kindervag helped to solidify zero trust principles in the IT community. Zero trust architectures, on the other hand, would take over a decade to become common, owing to the growing usage of mobile and cloud services, among other factors.
READ ALSO: How to Secure Your Mobile Devices: A Comprehensive Guide
The Concepts Of Zero Trust
What Is a Zero-Trust Network, and How Does It Work? Here are the 5 key assumptions within a zero-trust network:
- The network is always assumed to be hostile.
- On the network, external and internal threats are constantly present.
- Network proximity is insufficient for deciding whether to trust a network.
- Every device, user, and network flow requires authentication and permission.
- Policies must be flexible and based on a variety of data sources.
The zero-trust network is a new paradigm that has emerged in the wake of global hacking scandals. It hinges on five key assumptions: that networks are assumed to be hostile, external, and internal dangers exist at all times, choosing whether or not to trust someone means ensuring they have proper authentication and authorization for every device used by them as well as themselves–not just their location–and finally recognizing that it’s essential we continue this mindset even after any attack occurs.
Here is how Microsoft explains their Zero Trust deployment: Rather than trusting that everything inside the company firewall is secure, the Zero Trust model assumes a breach and validates each request as if it came from a public network. Zero Trust teaches us to “never trust, always verify” no matter whence the request comes from or what resource it accesses.
Before giving access, each request is thoroughly verified, approved, and encrypted. To keep lateral movement to a minimum, micro segmentation, and least privileged access are used. To detect and respond to abnormalities in real time, rich intelligence and analytics are employed.
READ ALSO: Zero Trust Architecture: Enhancing Network Security
Outdated Security Models
Today’s security model is outdated, and it needs to modernize in order for organizations to keep up with the ever-changing environment.
Today’s businesses need a new way of thinking about cybersecurity because today’s world has become more complex than before due to smartphones being so prevalent among people these days. Cybersecurity should embrace this mobile workforce by adapting quickly as threats change continuously – which they are constantly doing!
When it comes to cybersecurity, the importance of zero trust cannot be overstated. This is especially important when building a system from scratch or implementing new technologies into an existing workflow.
The security industry has been experiencing a paradigm shift in recent years as we move further away from traditional models that rely on protocols like firewalls and allow more access at once.
Along with this trend, cyberattacks have become increasingly sophisticated–and so too should our solutions for protecting against them!
That’s why it can’t be stressed enough how crucial Zero Trust implementations are to any company looking to protect data by being proactive about their physical protection strategies: only those who bake Zero Trust into every aspect of their business will know what success feels like!
READ ALSO: Responsible Web Intelligence at Scale: An MCP-Driven Architecture
Why Is Zero Trust Emerging As A New Cybersecurity Paradigm? Is It Feasible?
Yes and no. For any organization that has not yet embraced the concept of privileged access and least privilege, as well as still maintaining shared accounts for security purposes, zero trust is simply not going to work.
They are not offering a self-contained solution to solve all the problems—a massive undertaking that requires building an IT architecture from scratch with zero trust as the driving security principle.
It’s an interesting time to be in the cybersecurity industry. Therefore, it is ideal to utilize a reliable cloud backup and disaster recovery company like Assurance IT. Zero trust is now a common practice among organizations, but there are limitations with this approach that we need to acknowledge as IT professionals, like myself, Luigi Tiano.
Regardless of whether your organization has one person or thousands, zero trust can only manage what falls within its scope – and when it comes outside of those bounds (i.e., remote employees), it struggles mightily regardless how long you’ve been practicing zero trusts policies internally!
A hot topic of conversation coming into 2021 is how feasible Zero Trust really is. The idea has been around since 2018, but only a handful of organizations have adopted it at large scale so far.
It seems that more and more companies are considering the risk involved with trusting any user on their network to remain authentic for long periods or even permanently- which may be why there’s still an ongoing debate about its feasibility 3 years in?
Organizations should start preparing for quantum computers now, as they are still years away. While a hacker may not be able to decrypt information immediately with today’s technology, it is possible that an attack could happen in the future when hackers have access to advanced forms of encryption or decryption methods through their own devices.
This would cause organizations and governments alike great harm if sensitive data were compromised and released into public networks during this time period without being encrypted properly beforehand due either human error or user negligence at some point beforehand.
READ ALSO: 5 Adoption Strategies For Zero Trust
Zero Trust Architecture: Frequently Asked Questions
What are the pillars of zero trust architecture?
Zero Trust is built on three core principles:
- Least Privilege Access: This principle dictates that users and devices are granted only the minimum level of access required to perform their tasks. This minimizes the potential damage if a security breach occurs.
- Continuous Verification: Zero Trust doesn’t rely on implicit trust based on network location. Users and devices must be continuously verified throughout a session, even if they are already inside the network perimeter.
- Never Trust, Always Verify: This principle emphasizes the importance of constant verification. Identity, device posture (security status), and access requests are continuously checked to ensure authorized access.
What are the three main concepts of zero trust?
These three concepts essentially boil down to the core principles mentioned above:
- Assume Breach: Security posture assumes a breach has already occurred or could happen at any time. This eliminates the concept of a trusted network perimeter.
- Micro-Segmentation: Networks are divided into smaller segments with specific access controls. This limits the potential damage if a breach occurs within one segment.
- Identity and Device Access Management: Strong identity and device access management solutions are central to Zero Trust. They ensure only authorized users and devices can access resources, and their access is continuously monitored.
READ ALSO: 4 Cybersecurity Risks Emerging From Cross-Border Online Services
What is an example of zero trust?
Imagine a company using a Zero Trust approach. An employee working from home needs to access a confidential document on a company server. Here’s how Zero Trust might work:
- The employee logs in using strong Multi-Factor Authentication (MFA).
- The employee’s device posture (security software updates, etc.) is verified.
- The system only grants access to the specific document the employee needs, not the entire server.
- Even after gaining access, the employee’s activity might be monitored for suspicious behavior.
What are the pillars of Zero Trust?
As mentioned earlier, the core principles (Least Privilege Access, Continuous Verification, Never Trust, Always Verify) form the pillars of Zero Trust Architecture.
READ ALSO: The End of Passwords? Summer 2025 Digest on Cybersecurity Reset
What is the main goal of Zero Trust?
The main goal of Zero Trust is to significantly reduce the risk of unauthorized access to data and resources within a network. It achieves this by eliminating implicit trust and implementing continuous verification throughout a session. By minimizing access privileges and constantly monitoring activity, Zero Trust helps organizations better protect their sensitive information from cyberattacks.
INTERESTING POSTS
- Best Antivirus For 2022
- What Is Zero Day Exploit? Risks And Why Is It Called Zero Day?
- Should I Trust VPN Review Sites?
- Cybersecurity Strategies To Protect Your Critical SaaS Data
- 5 Best Browsers for Online Gaming
- The Best Art Apps You Can Use For Handheld Devices
- What Is A Certificate Authority (CA) And What Do They Do?
- The Gaming Industry Must Be Proactive About DDoS Attacks
About the Author:
Daniel Segun is the Founder and CEO of SecureBlitz Cybersecurity Media, with a background in Computer Science and Digital Marketing. When not writing, he's probably busy designing graphics or developing websites.
Meet Angela Daniel, an esteemed cybersecurity expert and the Associate Editor at SecureBlitz. With a profound understanding of the digital security landscape, Angela is dedicated to sharing her wealth of knowledge with readers. Her insightful articles delve into the intricacies of cybersecurity, offering a beacon of understanding in the ever-evolving realm of online safety.
Angela's expertise is grounded in a passion for staying at the forefront of emerging threats and protective measures. Her commitment to empowering individuals and organizations with the tools and insights to safeguard their digital presence is unwavering.