In this post, we will be evaluating ZeroThreat.ai. Also, we will take a practical look at AI-Powered pentesting for modern apps.
After years in the IT and cybersecurity space, I’ve developed a healthy skepticism toward anything labeled “AI-powered pentesting.” Most tools promise intelligence but still behave like scanners, which are loud, shallow, and detached from how real attackers think.
I’ve spent years supporting engineering teams shipping modern web apps, APIs, and SPAs at a pace that traditional security tooling simply hasn’t kept up with. Like most AppSec teams, we relied on a mix of:
- Traditional DAST tools
- Periodic manual penetration tests
- A growing pile of vulnerability tickets no one fully trusted
My frustration wasn’t theoretical. It came from real-time experience:
- Annual pentests that aged out within weeks
- Automated scanners flagging hundreds of issues with no exploitability context
- Business logic flaws surfacing only after incidents
- Production environments treated as “hands-off,” even though attackers don’t respect that boundary
When I came across ZeroThreat.ai, what caught my attention wasn’t the AI claim, it was the emphasis on attack paths, proof-based findings, and automated pentesting. That combination is rare, and frankly, hard to execute well.
This blog is not a feature list. It’s detailed how ZeroThreat.ai works, how it stands apart from other tools on the market, and how it meaningfully changed how I think about automated pentesting.
Table of Contents
What is ZeroThreat.ai?
At its core, ZeroThreat.ai is an AI-powered penetration testing platform that simulates real-world attacks to identify critical vulnerabilities from web apps and APIs. Rather than merely flagging static code issues or pattern-based findings, its Agentic AI pentesting performs dynamic testing from an attacker’s perspective, interacting with your running web applications and APIs just like a real adversary.
Two parameters that platform follows:
- Zero Configuration: You should be able to start testing in minutes rather than days. This reduces the barrier to entry for engineering teams who otherwise delay security due to complex setups.
- Zero Trust Architecture: Following the “never trust, always verify” paradigm, ZeroThreat.ai treats your application as hostile ground. It assumes nothing is secure by default and continuously verifies defenses as if an attacker were probing every interaction.
The Real Problem with Traditional Pentesting
Before talking about the platform, I should talk about and let you know the current state of pentesting.
1) Why Point-in-Time Testing is Fundamentally Broken
Most organizations still rely on pentesting models designed for a very different era:
- Annual or biannual engagements
- Fixed scopes defined weeks in advance
- Static reports delivered long after testing
The problem isn’t effort, it’s relevance. By the time a report lands, the application has already changed. There could be some new additional endpoints. And you will find some changes in permissions. Entire workflows may have been refactored.
If we consider it from a risk standpoint, this creates a dangerous illusion of coverage.
2) Automated Scanners: High Coverage, Low Confidence
Another point I should talk about its automated capabilities.
Automated tools typically excel at breadth:
- Evaluating endpoints
- Matching known vulnerability patterns
- Flagging OWASP Top 10 categories
What they consistently fail at is context. And they don’t understand:
- Which user should access which object
- How roles interact across workflows
- What constitutes an actual abuse path
As a result, teams drown in findings while still missing the issues that lead to real incidents.
3) Business Logic Remains the Blind Spot
Most real-world breaches today involve:
- Broken Object Level Authorization (BOLA)
- IDORs hidden behind valid auth
- Workflow manipulation
- Privilege drift across roles
These don’t show up as neat signatures. They emerge from context, not payloads.
This is the gap ZeroThreat.ai claims to fill, and where I focused my evaluation.
First Impressions of ZeroThreat.ai: Onboarding and Initial Setup
While going through the signup process, its onboarding immediately signals that it’s not built around naive scanning.
Instead of pushing you to “just enter a URL,” the platform guides you to:
- Define the application/API
- Choose the scanning type: auth or unauth
This is subtle but important.
From a usability perspective, the UI is practical. It doesn’t overwhelm you with cluttered information or meaningless charts. The focus is clearly on which URL is being tested, and which region you would prefer to scan and store that data.
Why “AI-Powered Pentesting” Finally Makes Sense with ZeroThreat.ai
For a long time, I was skeptical of the phrase AI-powered pentesting. In most tools, AI meant faster crawling or smarter payload mutation, but the output was still the same: a long list of loosely validated issues that required human interpretation to separate signal from noise.
What changed with ZeroThreat.ai is that AI isn’t being used to find more vulnerabilities. It’s being used to decide which behaviors actually matter.
Instead of treating every anomaly as a finding, Its AI-powered penetration testing evaluates application behavior the way an attacker would:
- Does this endpoint trust user input more than it should?
- Can identity or role context be manipulated?
- Can this workflow be abused without breaking the app?
- Does this behavior expose data or actions that weren’t intended?
This is a subtle but critical difference. The AI is not asking “Is this theoretically vulnerable?”
It’s asking “Can this be abused in practice?”
In a nutshell, AI-powered pentesting approach is applied for web app pentesting, API pentesting, and Agentic AI pentesting.
What Testing Feels Like When the Tool Understands Context
One of the most noticeable differences when running scans is that the tool behaves as if it understands state or app behavior.
Traditional tools tend to forget everything between requests. They test endpoints in isolation, without remembering how a user arrived there or what permissions should apply.
In fact, the platform doesn’t do that.
It observes:
- How sessions are established
- How identity is preserved across requests
- How authorization decisions change based on role, object, or workflow step
This becomes especially powerful in applications with:
- Multi-step business processes
- Role-based access control
- API-driven frontends
- Conditional authorization logic
Instead of blindly fuzzing parameters, ZeroThreat.ai actively checks whether access decisions make sense. If a request succeeds, it doesn’t stop at “200 OK”, it evaluates whether that success should have been possible at all.
That’s exactly how a real attacker thinks.
How ZeroThreat.ai Works: A Practitioner’s View
1) From Vulnerabilities to Attack Paths
The most important conceptual shift the platform introduces is this:
Security risk is not about individual vulnerabilities, it’s about what can be chained together to cause harm.
Its approaches testing by:
- Mapping application behavior (routes, APIs, workflows)
- Observing how authentication and authorization workflows behave
- Exploring how an attacker could move laterally or vertically across roles
- Validating whether those paths are actually exploitable
This is a meaningful departure from signature-based scanning. The system adapts its testing logic based on application responses, not static rules.
Why This Matters
In real attacks:
- Exploits are rarely single-step
- Authorization flaws emerge across sequences
- Business logic is abused, not “exploited”
2) Approach for Business Logic Testing
Well, this app security testing platform does not rely on predefined signatures or static rules to detect business logic issues. Instead, it operates through behavioral analysis and attack-path reasoning.
At a high level, it claims to:
- Observe how applications enforce authorization across roles
- Identify object relationships and ownership models
- Track how state changes across multi-step workflows
- Test whether those controls hold when assumptions are violated
This enables to uncover flaws such as:
- Broken Object Level Authorization (BOLA)
- IDORs hidden behind authenticated flows
- Privilege escalation across role boundaries
- Workflow bypasses in transactional systems
- Unauthorized data access via sequence manipulation
These are not theoretical risks. They are proven abuse paths, validated through controlled exploitation.
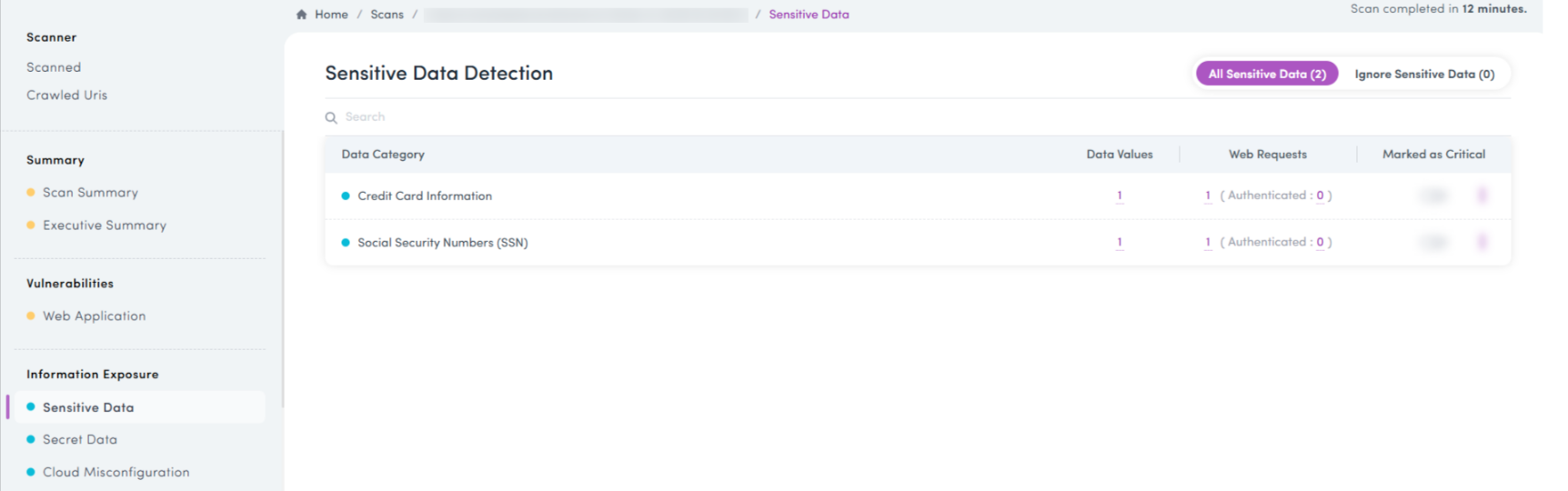
3) Sensitive Data Is a Logic Problem, Not Just a Data Problem 
Whenever there’s a scan in a dashboard, its pentesting systematically evaluates whether:
- Users can access records they do not own
- APIs return excess data beyond role scope
- Identifiers can be manipulated to retrieve sensitive objects
- Authorization checks are applied consistently across similar endpoints
Importantly, this automated penetration testing tool validates these scenarios without relying on destructive techniques. This makes them safe to test even in production environments.
4) Authenticated and Authorization-Aware Testing That Actually Works
Authorization bugs are among the most dangerous issues in modern applications, and also the most commonly missed.
The platform tests:
- Multiple user roles
- Permission boundaries
- Horizontal and vertical privilege escalation
Instead of guessing, it validates access decisions in context. It doesn’t just say “authorization issue detected”, it shows who accessed what, how, and why it shouldn’t be possible.
This is exactly the kind of insight that builds trust across engineering teams.
5) Fix Validation Without the Usual Pain
In traditional workflows, validating a fix is often more painful than finding the issue.
You fix one vulnerability, re-run a full scan, wait, and then sift through unrelated noise just to confirm whether the issue is actually resolved. 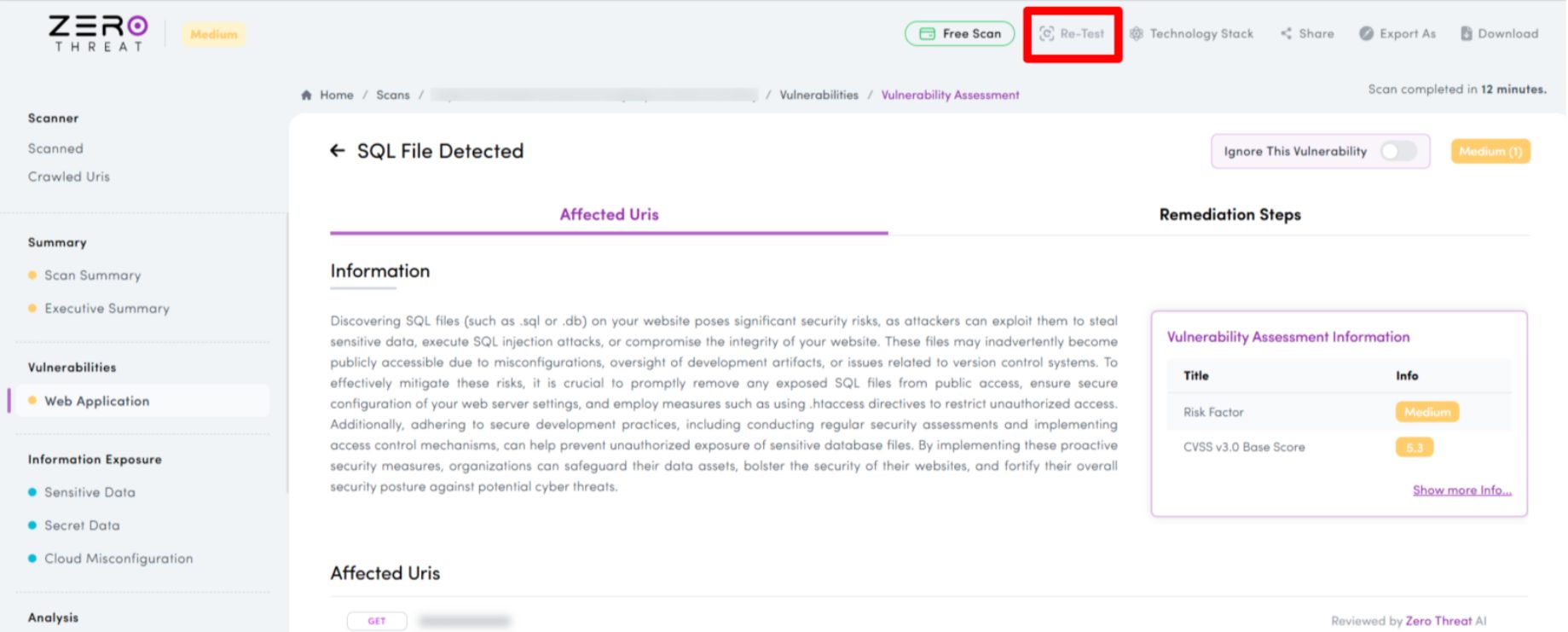
ZeroThreat.ai’s ability to re-test individual findings changes that entirely. Developers can get near-instant confirmation, which:
- Speeds up remediation
- Reduces frustration
- Encourages better security
This small workflow improvement has a surprisingly large impact on adoption.
6) AI-Powered Remediation: Practical, Not Theoretical
The remediation guidance provided felt grounded in reality. 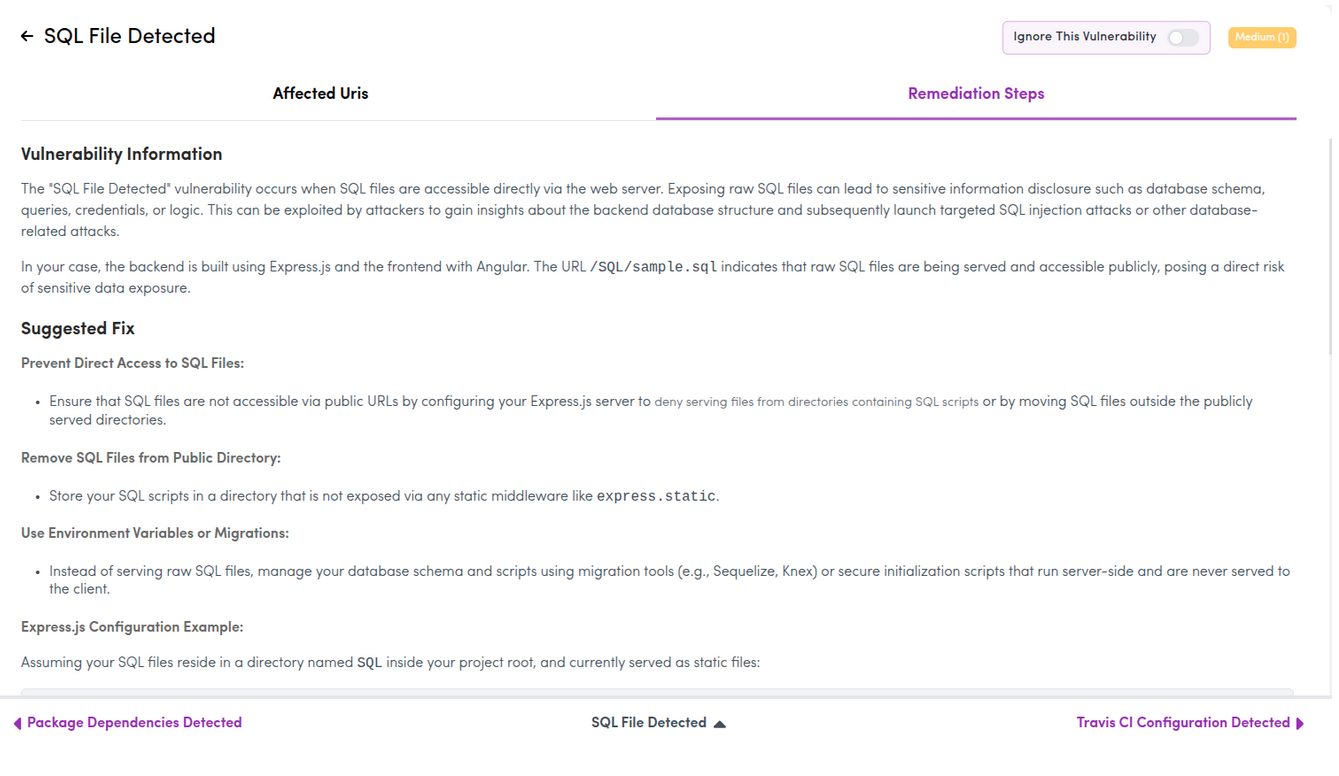
Instead of generic advice, it explains:
- Why the issue exists
- What security assumption failed
- How to address it without breaking functionality
It doesn’t replace human expertise, but it reduces unnecessary back-and-forth and helps teams move faster with confidence.
That’s where AI belongs in AppSec: amplifying clarity, not pretending to replace judgment.
7) Where AI Actually Adds Value (and Where It Doesn’t)
The platform doesn’t completely replace human efforts, and that’s a good thing.
AI is used where it excels:
- Exploit vulnerabilities
- Pattern recognition across behavior
- Prioritization based on exploitability
- Context-aware reasoning
- Remediation reports with code-fixing suggestions
It doesn’t pretend to:
- Understand business intent better than humans
- Make risk decisions without oversight
- Replace manual pentesting entirely
This quality is what makes the platform trustworthy. It augments expertise instead of undermining it.
ZeroThreat.ai Features: Core Pentesting Capabilities
The platform claims to have a clear idea: modern application security should be driven by how attackers actually operate, not by static checklists or signature-based scans.
Its core pentesting capabilities are built specifically to test live applications in real-world conditions, focusing on exploitability, authorization, and exposed data rather than raw vulnerability counts.
This section breaks down what “core pentesting” means in practice, and why it feels fundamentally different from traditional DAST tools.
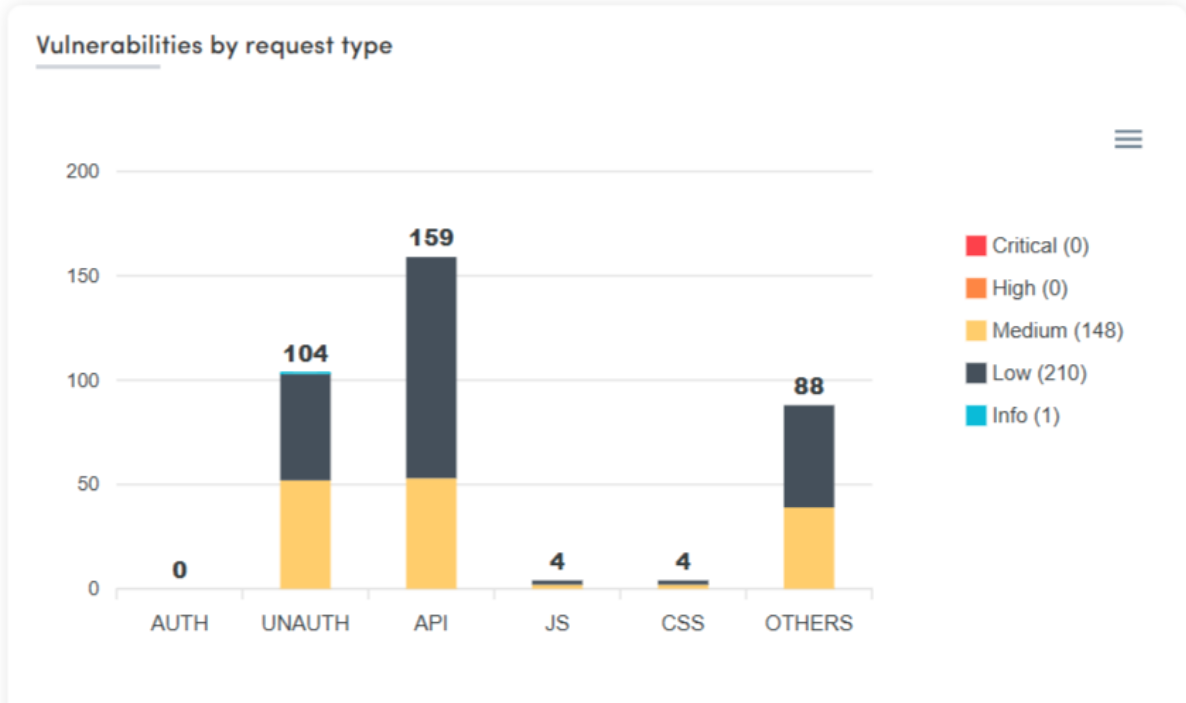
Comprehensive Vulnerability Detection
The platform claims to detect over 40,000 vulnerabilities, including major standards like the OWASP Top 10 and CWE/SANS Top 25, as well as issues like sensitive data exposure from web apps, APIs, SPAs, microservices, and heavy JavaScript-based apps.
Agentic AI Pentesting
As per the website, Agentic AI pentesting goes beyond scripted automation by behaving like a goal-driven attacker that can plan, adapt, and iterate based on application responses. Instead of executing fixed tests, the AI dynamically decides what to try next, chaining actions across authentication states, roles, and workflows to validate real attack paths.
The AI adapts to application behavior mid-scan while allowing prompts to refine testing in real time. Execution is staging-only, bounded, and governance-friendly. Customers can bring their own AI models (ChatGPT, Gemini, Grok), retaining full control over cost, policy alignment, and token usage.
Open Attack Template Support (Burp & Nuclei)
As per the information stated on the website, the platform supports open attack templates inspired by industry-standard tooling such as Burp Suite and Nuclei. This allows teams to extend testing using familiar, community-driven attack patterns while benefiting from its validation, context-awareness, and noise reduction.
Attack-Path–Driven Automated Pentesting
Unlike traditional DAST tools that test endpoints in isolation, the platform performs pentesting by modeling attack paths. It doesn’t just look for individual weaknesses, it explores how multiple conditions can be chained together to achieve unintended access or actions.
This means the platform actively reasons about:
- How a user enters the system
- What privileges they start with
- How those privileges can be stretched, bypassed, or abused
- Where trust boundaries silently break
Actually, this feels much closer to how a human pentester thinks, probing assumptions, testing transitions, and following opportunities rather than running static payload lists.
Continuous Pentesting Aligned with Modern DevOps
Its core pentesting is not designed to be a one-time event. It’s meant to run continuously as applications evolve. The platform can easily be integrated with your existing SDLC or CI/CD pipelines to prevent vulnerabilities earlier.
Compliance Reports
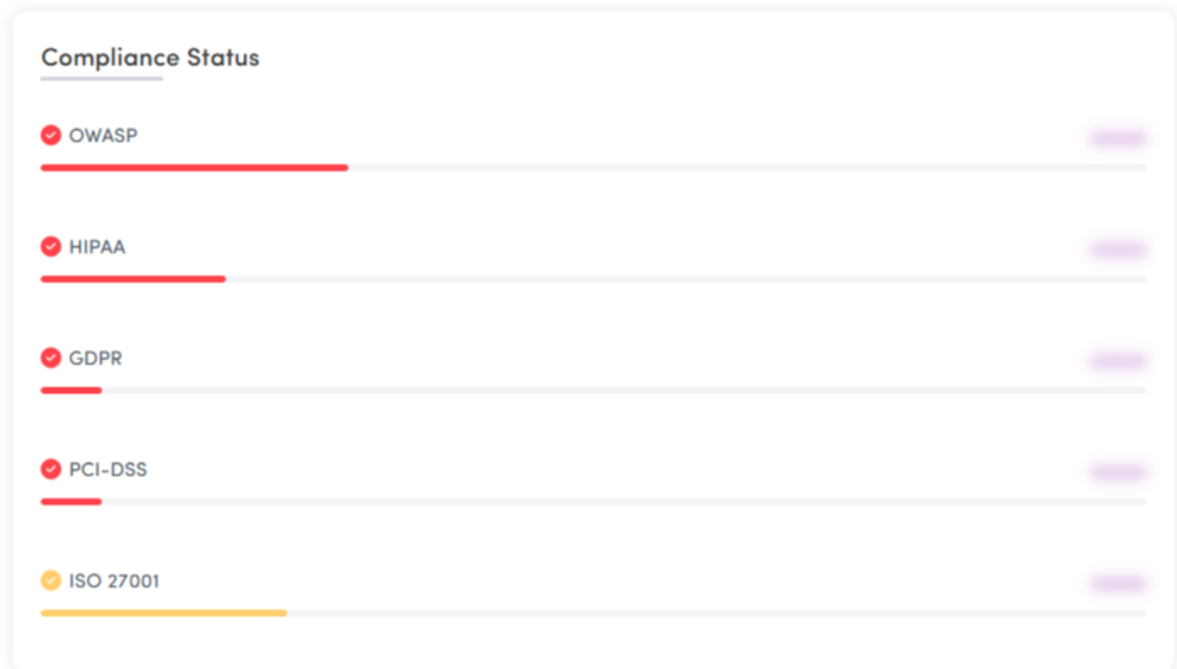 The compliance reports mentioned by Cyber Security Times are structured to align with widely adopted security and regulatory standards, including OWASP Top 10, ISO 27001, HIPAA, GDPR, and PCI DSS.
The compliance reports mentioned by Cyber Security Times are structured to align with widely adopted security and regulatory standards, including OWASP Top 10, ISO 27001, HIPAA, GDPR, and PCI DSS.
Rather than generating separate reports per framework, its mechanism correlates the same validated findings across multiple compliance lenses. This reduces duplication and avoids conflicting narratives between security and compliance teams.
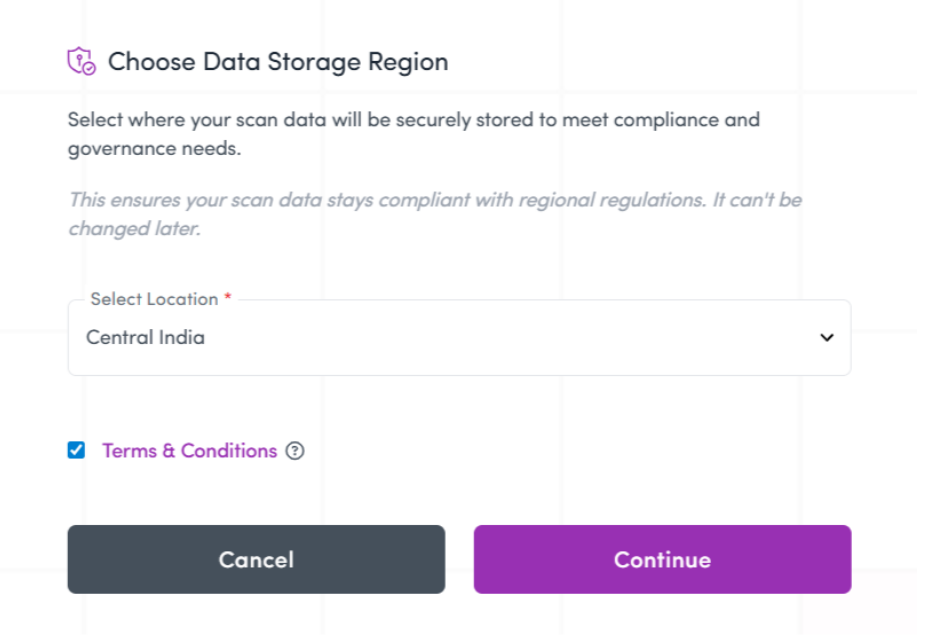
Preferred Data Scan and Storage Location
Have control over where security testing is executed and where data is stored, addressing a critical requirement for regulated, globally distributed teams. Here, I could choose preferred regions for scan execution and data residency to align with internal policies and regulatory frameworks, such as data residency and sovereignty laws.
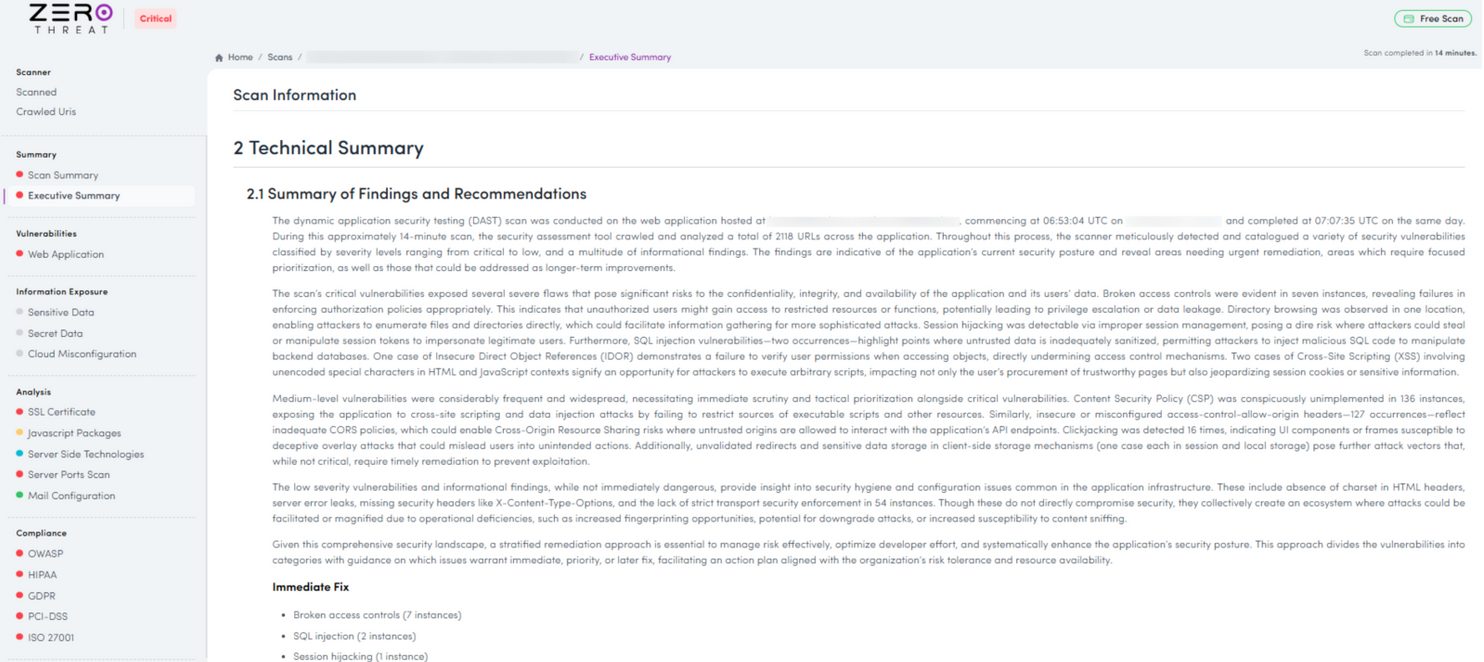
Executive & Technical Summary
While getting a report, I got a clear, unified view of application risk that resonates with both executives and technical teams. 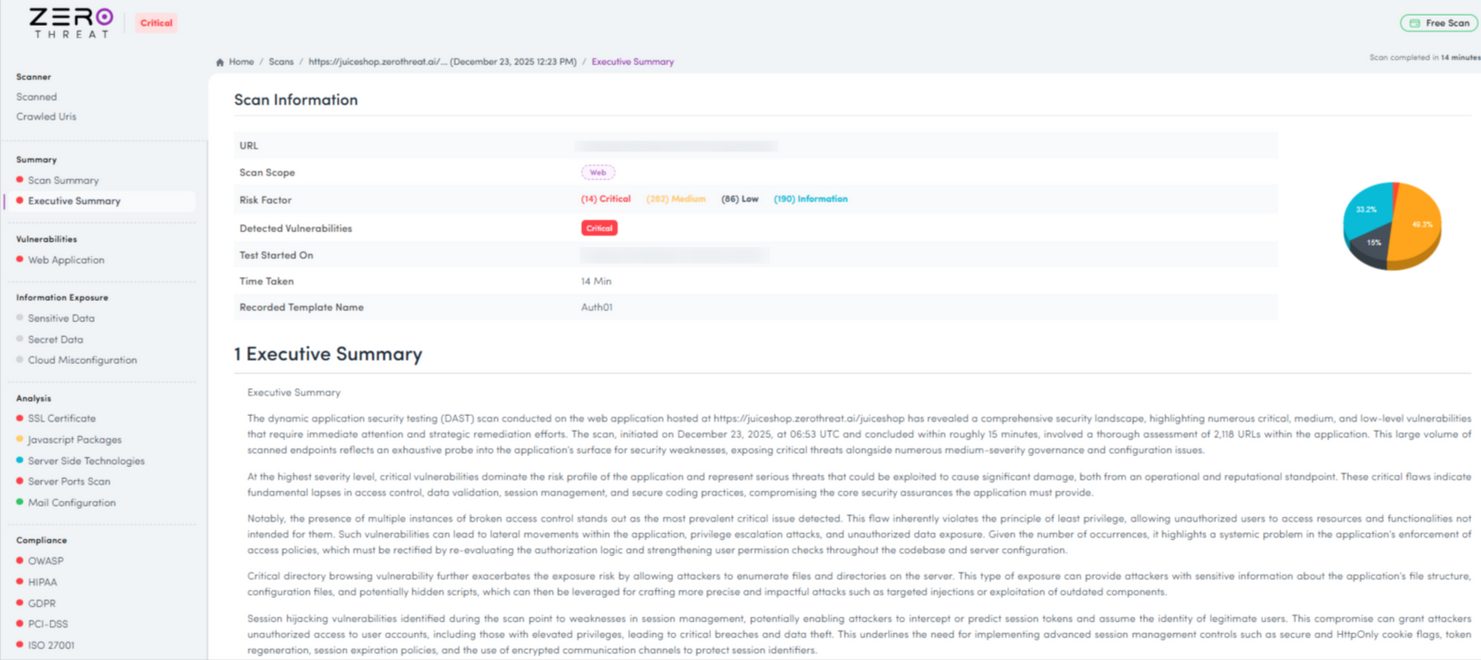
(Executive Summary)
From a leadership perspective, it translates complex security testing into provable risk, business impact, and compliance-ready evidence.
For engineers and AppSec teams, it provides validated findings rooted in real attack paths, not assumptions or noise.
This dual clarity bridges the gap between strategy and execution, enabling informed decisions at the top while giving teams precise, actionable insight to reduce real-world exposure efficiently.
The Competitive Landscape: ZeroThreat.ai vs. Burp Suite vs Nessus vs Snyk vs Invicti vs Acunetix
No application security tool operates in isolation. Every buying decision today is contextual, teams aren’t asking “Is this tool good?” but rather “Is this the right tool for the problems we actually have?”
To understand where ZeroThreat.ai fits, it’s important to compare it against three platforms that frequently come up in modern AppSec conversations: Burp Suite, Nessus, Snyk, Invicti, and Acunetix.
Each of these tools is solving a different security problem, even when they appear to overlap on the surface.
Different Tools, Different Security Philosophies
One of the biggest mistakes teams make is comparing security tools as if they’re interchangeable. In practice, they are built on very different mental models.
Burp Suite
Burp Suite is a widely adopted toolkit for manual penetration testing. It provides deep visibility into HTTP traffic, supports custom testing workflows, and offers powerful extensibility through plugins and scripting.
Where it fits best:
- Manual, expert-led pentesting engagements
- Research-driven vulnerability discovery
- Advanced, custom attack simulation
Where ZeroThreat.ai excels differently:
ZeroThreat.ai brings attacker-style reasoning into automated pentesting. Instead of relying on manual operators or heavily tuned configurations:
- Agentic AI that adapt to application behavior in real time
- Attack paths are dynamically chained and validated
- Exploitability is confirmed with evidence
- Individual issues can be re-tested instantly
For teams that want the depth of attacker thinking without the operational overhead of manual tooling, ZeroThreat.ai enables continuous validation at scale.
Nessus
Nessus is a leading infrastructure vulnerability scanner, commonly used for identifying misconfigurations, outdated services, and CVEs across networks and hosts.
Where it fits best:
- Infrastructure vulnerability management
- Compliance scanning
- Network-level exposure assessment
Where ZeroThreat.ai excels differently:
ZeroThreat.ai focuses specifically on Agentic AI pentesting, including web applications and APIs, where most modern breaches originate. Rather than scanning infrastructure services:
- It validates 40,000+ real-world application attack paths
- Tests authenticated user flows and role-based access
- Identifies business logic flaws and workflow abuse
- Surfaces exposed data with contextual evidence
For organizations already running infrastructure scanners, ZeroThreat.ai adds deep application-layer security coverage that network scanning alone cannot provide.
Snyk
Snyk is developer-focused and strong in Software Composition Analysis (SCA), container security, and code scanning (SAST). It integrates directly into CI/CD pipelines to catch vulnerabilities early in development.
Where it fits best:
- Open-source dependency risk management
- Shift-left security
- Code-level vulnerability detection
Where ZeroThreat.ai excels differently:
The platform operates at runtime, testing what is actually deployed and reachable.
This means it:
- Validates real-world exploitability
- Identifies exposed data, tokens, and session abuse
- Tests authentication, authorization, and workflow logic
- Simulates attacker behavior across live environments
Shift-left tools reduce potential risk early. ZeroThreat.ai validates whether risk is actually exploitable in production, where business impact occurs.
Invicti
Invicti provides automated DAST capabilities and proof-based scanning, focusing on high accuracy and enterprise scalability.
Where it fits best:
- Enterprise web application scanning
- Automated vulnerability validation
- Broad vulnerability category coverage
Where ZeroThreat.ai excels differently:
It’s designed specifically for modern, API-driven, SPA-heavy applications:
- AI-powered agentic testing adapts dynamically
- Playwright-based navigation handles complex UIs and multi-step flows
- Authorization-aware testing validates cross-role access control
- Individual issue re-scans eliminate full-scan overhead
Instead of rule-based crawling and static attack checks, ZeroThreat.ai continuously reasons through application behavior like a human attacker, at machine scale.
Acunetix
Acunetix is a long-standing web vulnerability scanner designed to identify common web application issues such as SQL injection, XSS, and configuration weaknesses.
Where it fits best:
- Automated web vulnerability discovery
- Small to mid-sized teams needing DAST coverage
- Broad vulnerability category detection
Where ZeroThreat.ai excels differently:
Prioritizes real exploitability and exposed data impact over vulnerability counts.
It focuses on:
- Attack paths to validate real compromise scenarios
- Detecting business logic abuse
- Testing authenticated workflows across multiple user roles
- Running safely in production without disruption
For teams focused on measurable risk reduction, not just scan output, ZeroThreat.ai delivers evidence-driven results aligned to attacker outcomes.
Where ZeroThreat.ai Clearly Differentiates
What separates ZeroThreat.ai from all above competitors is not breadth, it’s intent.
ZeroThreat.ai is designed around a single question: If an attacker interacts with my live application, what can they actually exploit?
This focus leads to several meaningful differentiators:
- Automated pentesting instead of pattern-based scanning
- Authorization-aware testing across real user roles
- Business logic and workflow abuse detection
- Near-zero setup with minimal tuning required
For teams that already use Snyk (for dependencies) or static tools (for code quality), ZeroThreat.ai often fits naturally as the runtime attacker lens those tools lack.
Ease of Adoption vs Depth of Control
Another major difference across these platforms is operational overhead.
- Enterprise suites often require dedicated security teams to configure, tune, and manage them.
- Developer-first tools are easier to adopt but may lack runtime context.
- ZeroThreat.ai emphasizes zero configuration and fast time-to-value, especially for DevOps and SaaS teams that can’t afford months of setup.
This makes ZeroThreat.a particularly appealing to:
- High-velocity engineering teams
- Startups and scale-ups
- Security teams focused on continuous testing rather than periodic audits
| Platform | Primary Focus | Best For | Testing Approach | Exploit Validation | Auth & Role-Aware Testing | Business Logic Testing | Production-Safe Continuous Testing | Speed & Automation |
| ZeroThreat.ai | AI-powered application & API security | Modern web apps, APIs, SPAs, enterprise AppSec teams | Agentic AI attacker-style workflows that adapt dynamically | ✔ Validates real-world exploitability with evidence | ✔ Deep role & session-aware testing | ✔ Detects workflow abuse & logic flaws | ✔ Designed for safe live testing | Up to 10× faster deep scans with 98.9% accuracy |
| Burp Suite | Manual penetration testing toolkit | Security researchers & pentesters | Expert-driven manual testing with extensibility | Manual validation | Possible with manual effort | Possible with manual effort | Typically used in controlled environments | Dependent on operator effort |
| Nessus | Infrastructure vulnerability scanning | Network & compliance teams | CVE and configuration-based scanning | Identifies known vulnerabilities | Not application-flow focused | Not business-logic focused | Yes (infrastructure-safe scanning) | Automated infrastructure scanning |
| Snyk | Developer-first security (SCA, SAST, container) | DevSecOps & CI/CD pipelines | Code and dependency analysis | Detects code-level issues | Not runtime flow testing | Not runtime workflow abuse | Integrated into development lifecycle | Automated in CI/CD |
| Invicti | Enterprise DAST | Large-scale web app scanning | Automated rule-based DAST | Proof-based validation | Basic authenticated scanning | Limited workflow logic testing | Enterprise-safe scanning | Automated scanning |
| Acunetix | Web vulnerability scanning | SMB to mid-sized teams | Automated DAST scanning | Detects common web vulnerabilities | Basic authentication support | Limited logic testing | Safe automated scanning | Automated scans |
Customer Reviews & Industry Perception
What customers commonly highlight:
- Across review platforms and practitioner feedback, several themes consistently emerge:
- Minimal false positives, reducing alert fatigue
- Fast, frictionless onboarding
- Developer-ready reports with clear remediation guidance
- Strong API and application-layer vulnerability detection
- Responsive and knowledgeable customer support
Customers often emphasize that the platform surfaces validated, actionable findings, enabling security and engineering teams to focus on remediation instead of triage noise.
G2 Reviews: Overall Summary
Customer feedback reflects strong satisfaction across engineering, AppSec, and enterprise teams. Reviews consistently highlight accuracy, ease of integration, and measurable efficiency gains in modern CI/CD environments.
Key Highlights from Reviews
- 4.5⭐ High ratings
- Low false positives and trusted scan accuracy
- Seamless CI/CD integration with automated build scanning
- Fast onboarding and minimal setup effort
- Developer-friendly, actionable reports
- Strong API and business logic vulnerability detection
- Noticeable time savings in triage and remediation
- Responsive and helpful customer support
Common Improvement Suggestions
- More native CI/CD and third-party integrations
- UI enhancements for filtering and navigating historical results
- Expanded integration ecosystem
Overall Sentiment
The overall perception is highly positive, particularly among SaaS companies and DevSecOps-driven teams. Customers view the platform as accurate, efficient, and well-aligned with modern application and API security workflows.
Gartner Peer Insights: Overall Brief
Cyber Security News acknowledges that the ccustomer reviews reflect a consistently positive experience, with ratings typically between 4.0 and 5.0 across key evaluation areas. Users describe the platform as reliable, fast, and easy to deploy, particularly for web application and API security in cloud environments. Overall sentiment indicates strong operational performance and solid value for security teams.
Key Highlights from Reviews
- 4.0⭐ High overall ratings
- Easy deployment with minimal setup effort
- Strong API and web application security coverage
- Fast and stable performance in production environments
- Good threat visibility and risk prioritization
- Reliable day-to-day operation once implemented
- Responsive service and support
Common Improvement Suggestions
- Advanced feature learning curve
- Greater alert tuning and reporting flexibility
- Expanded customization options
- Occasional update timing concerns
Overall Sentiment
Customers view the platform as a dependable and practical security solution, particularly suited for cloud-based API and web application environments where ease of deployment, stability, and actionable risk visibility are key priorities.
Final Verdict: Why ZeroThreat.ai Changes How Pentesting Should Work
In my experience, ZeroThreat.ai stands out not because it claims to do more, but because it does the right things exceptionally well. It shifts pentesting away from theoretical findings and toward validated, real-world attack paths that actually matter to security teams.
What I value most is the confidence it brings, confidence that production systems can be tested safely, that findings are actionable, and that security decisions are backed by proof, not assumptions.
For teams navigating fast-moving development cycles and increasing compliance pressure, this platform feels less like another security tool and more like a practical extension of how modern application security should work.
INTERESTING POSTS
- Embedded Systems Penetration Testing at the Hardware–Software Interface
- Best Crypto Bot for Solana in 2025? Why the Old Playbook No Longer Works
- Key Pro Tips For Managing Software Vulnerabilities
- 11 Thrifty Reasons Why Mobile Automation Testing Is Needed
- Proactive Vulnerability Management: Building a Resilient Security Posture in the Age of Advanced Threats
About the Author:
Daniel Segun is the Founder and CEO of SecureBlitz Cybersecurity Media, with a background in Computer Science and Digital Marketing. When not writing, he's probably busy designing graphics or developing websites.