In this post, I will show you the best online proxy checkers.
In today’s digital landscape, where privacy, security, and unrestricted access to online content are increasingly important, proxies have become essential for many internet users.
However, not all proxies are created equal, and using an unreliable or compromised proxy can lead to security risks, poor performance, and frustration.
This is where proxy checkers come into play. In this comprehensive guide, we’ll explore the best online proxy checkers available, their features, and how to use them effectively to ensure your proxies are reliable and secure.
Table of Contents
Introduction to Proxy Checkers
Proxy checkers are tools designed to verify proxy servers’ functionality, performance, and security.
These tools test various aspects of a proxy, including its anonymity level, speed, protocol support, and geographical location.
Using a proxy checker, you can ensure that your proxies work as expected and suit your specific needs.
Why Use a Proxy Checker?
There are several compelling reasons to use a proxy checker:
- Verify Functionality: Ensure that your proxies work and route your traffic successfully.
- Check Anonymity Levels: Determine whether your proxy is truly anonymous or if it’s leaking information about your real IP address.
- Measure Performance: Test the speed and latency of your proxies to ensure they meet your performance requirements.
- Detect Geolocation: Verify that your proxy is located where it claims to be, which is crucial for accessing geo-restricted content.
- Identify Protocol Support: Determine which protocols (HTTP, HTTPS, SOCKS4, SOCKS5) your proxy supports.
- Avoid Blacklisted IPs: Check if major services or spam databases have blacklisted your proxy’s IP address.
- Ensure Compatibility: Verify that your proxy works with specific websites or services you intend to use.
Key Features of Effective Proxy Checkers
When evaluating proxy checkers, look for the following key features:
- Multiple Protocol Support: Should be able to check HTTP, HTTPS, SOCKS4, and SOCKS5 proxies.
- Batch Checking: The ability to check multiple proxies simultaneously saves time for users with large proxy lists.
- Detailed Reports: Provides comprehensive information about each proxy, including anonymity level, speed, and detected location.
- Customizable Tests: Users can specify which checks to perform and set custom parameters.
- API Access: Offers programmatic access for integration with other tools or automated workflows.
- Regular Updates: Frequently updated to detect new types of leaks and adapt to changing proxy technologies.
- User-Friendly Interface: Easy to use, with clear presentation of results.
- Export Options: Ability to export results in various formats (CSV, JSON, etc.) for further analysis.
Best Proxy Service Deals
Best Featured Proxy Service Providers
When it comes to premium proxy solutions, some providers stand out for their innovative offerings, high reliability, and competitive pricing. Below, we highlight three top-tier proxy services, each excelling in different categories to cater to various user needs.
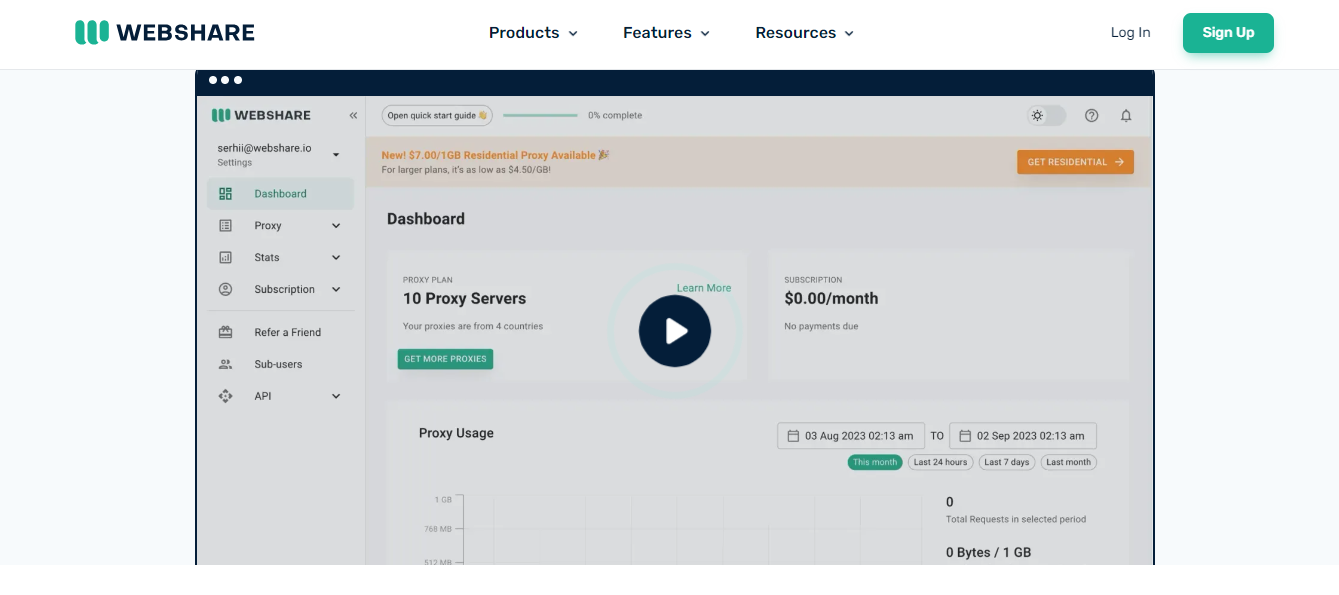
1. Webshare – Best for Affordable and Customizable Proxy Solutions
Webshare offers an exceptional balance of affordability and flexibility, making it a great choice for businesses and individuals looking for cost-effective proxy services. With a variety of proxy types, including residential, datacenter, and mobile proxies, Webshare ensures seamless online anonymity and web scraping capabilities.
Key Features:
- Highly customizable proxy plans
- Free proxy options available for testing
- Secure HTTPS and SOCKS5 support
- Instant setup and user-friendly dashboard
Best For:
- Budget-conscious users looking for high-quality proxies
- Developers and businesses requiring scalable proxy solutions
- Web scraping, SEO monitoring, and automation tasks
2. Oxylabs – Best for Enterprise-Grade Proxy Solutions
Oxylabs is a powerhouse in the proxy industry, known for its enterprise-level solutions designed to handle high-volume data extraction and large-scale web scraping. With a vast proxy pool and AI-driven technology, Oxylabs is the go-to choice for businesses that demand reliability and efficiency.
Key Features:
- Over 175 million residential proxies worldwide
- Dedicated datacenter proxies for high-speed operations
- Ethical web scraping solutions with AI-powered tools
- 24/7 customer support and account management
Best For:
- Enterprises requiring high-quality, large-scale proxy networks
- E-commerce intelligence, market research, and data collection
- Users seeking industry-leading security and uptime
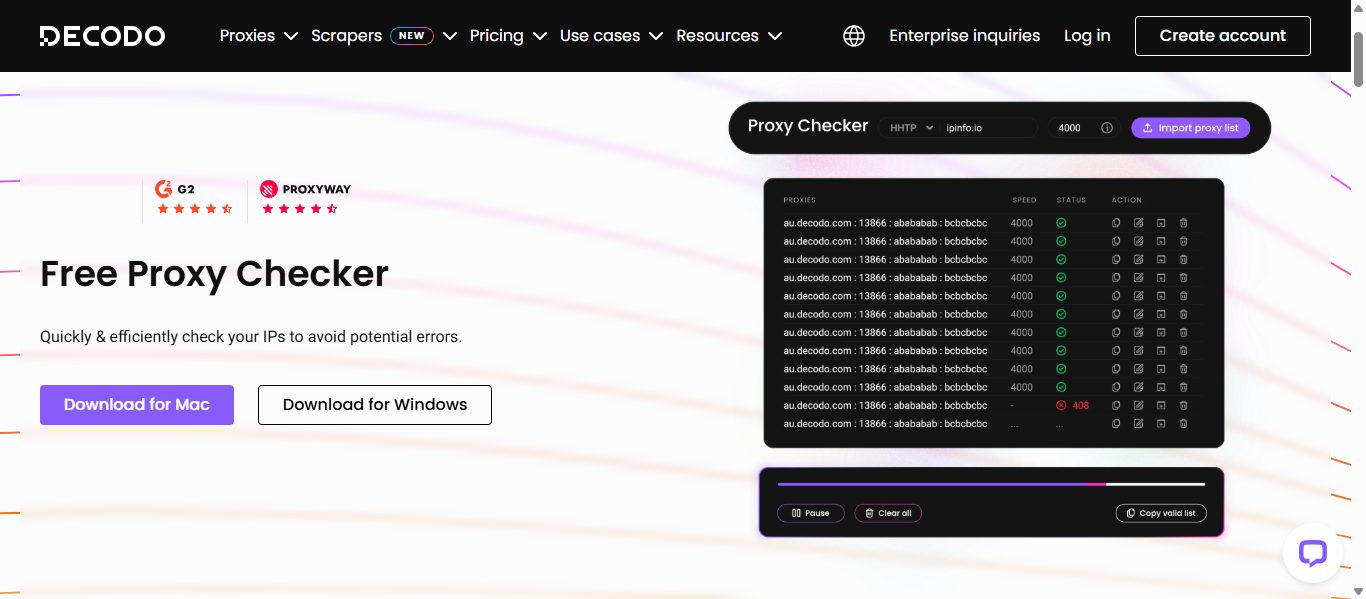
3. Decodo – Best for Fast and Reliable Residential Proxies
Decodo (formerly Smartproxy) is a well-rounded proxy provider offering a seamless user experience and high-performance features.
With an extensive proxy network of over 65 million IPs, including 55+ million residential proxies, Decodo is an excellent choice for users who need reliable, high-speed connections at competitive prices.
Its proxies are easy to set up, work flawlessly, and come with a free trial for all products, while residential proxies include a limited-time 40% discount with the code RESI40.
Key Features:
- 65+ million IPs across 195+ locations
- <0.3s average speed with 99.99% uptime
- Residential Proxies: 55+ million IPs with 40% off (RESI40)
- All other products include a free trial
- Supports both HTTPs and SOCKS5
- Fast customer support—40s average response time
- No need for long-term contracts—flexible, pay-as-you-go plans
- Intuitive dashboard with easy API integration
Best For:
- Digital marketers, social media managers, and sneaker resellers
- Businesses and freelancers needing fast, easy-to-use proxy solutions
- Users looking for a balance between affordability and performance
These top proxy service providers each bring unique strengths to the table, ensuring that whether you’re looking for affordability, enterprise solutions, or high-speed residential proxies, there’s an ideal choice for you.
Explore their offerings today and elevate your online activities with a reliable proxy provider!
The Top Online Proxy Checkers
Let’s explore some of the best online proxy checkers available:
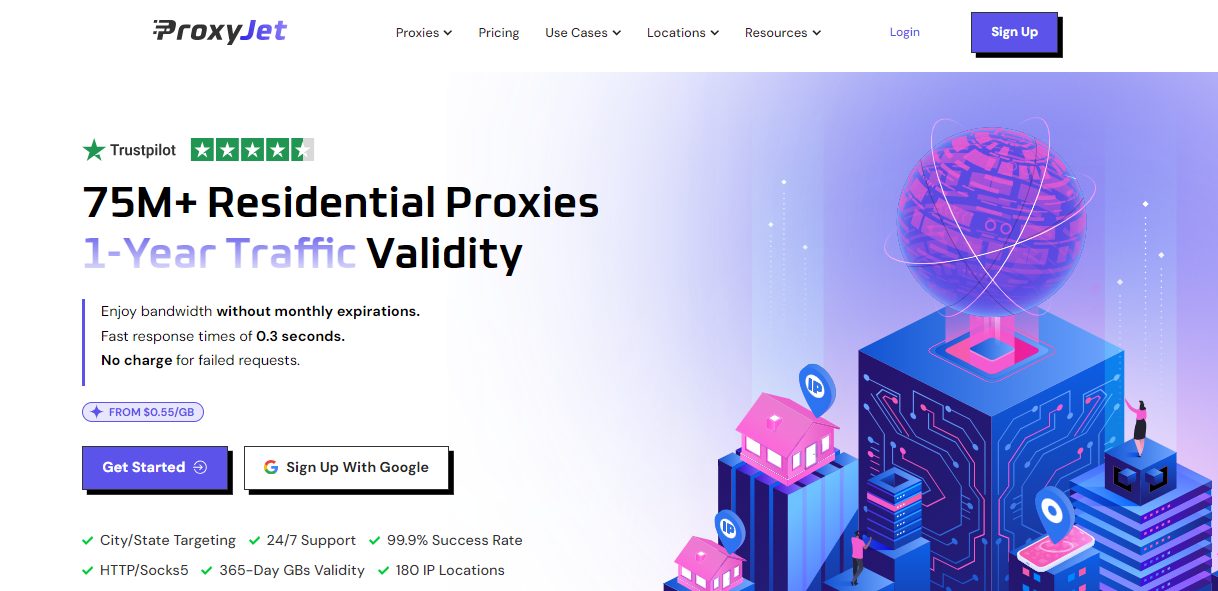
1. ProxyJet
When it comes to ensuring that your proxies are both reliable and secure, ProxyJet is an industry-leading service that excels in delivering high-quality proxy solutions.
What sets ProxyJet apart is its robust infrastructure, designed to offer consistent uptime, low-latency connections, and exceptional anonymity.
Whether you’re using proxies for web scraping, streaming, or bypassing geo-restrictions, ProxyJet ensures a seamless experience by providing a diverse range of IPs, including residential, datacenter, and mobile proxies.
This diversity reduces the risk of IP bans and helps maintain uninterrupted access, making ProxyJet an essential tool for professionals and casual users alike.
In addition to offering excellent proxy services, ProxyJet is also fully compatible with most online proxy checkers, which is a crucial aspect when testing the effectiveness of your proxies.
Its IPs perform well across numerous platforms, consistently passing speed, anonymity, and reliability tests. The company’s commitment to security, combined with excellent customer support, ensures that users have peace of mind when managing their proxies.
If you’re serious about enhancing your online privacy or boosting the efficiency of your operations, ProxyJet is a provider you can trust to deliver top-tier performance.
==>> Get ProxyJet
2. ProxyChecker.net
Key Features:
- Supports HTTP, HTTPS, SOCKS4, and SOCKS5 proxies
- Batch checking capability
- Detailed anonymity analysis
- Speed testing
- Geolocation verification
- Export options (CSV, TXT)
Pros:
- User-friendly interface
- Fast checking speed
- Comprehensive anonymity checks
Cons:
- Limited free checks per day
3. Live Proxies
Live Proxies provides a powerful proxy testing tool designed to verify the speed, anonymity, and reliability of proxies. Whether you are a data scraper, social media marketer, or cybersecurity professional, this tool ensures that your proxies meet performance and security standards before use.
Key Features:
- Real-Time Proxy Testing – Quickly assesses proxy speed, geolocation accuracy, and anonymity levels.
- Bulk Proxy Checking – Allows users to test multiple proxies simultaneously for efficiency.
- Detailed Reports – Displays key metrics, including response time, IP reputation, and security status.
- Supports Multiple Protocols – Compatible with HTTP, HTTPS proxies.
- User-Friendly Interface – Simple dashboard for easy proxy input and analysis.
Pros:
- Supports various proxy types (residential, mobile, static).
- Offers detailed performance reports to help users choose the best proxies.
- Fast and accurate proxy testing with real-time results.
Cons:
- No free plan is available, testing requires a paid proxy subscription.
- Limited advanced filtering options compared to some competitors.
==>> Get Live Proxies
4. HideMyAss Proxy Checker
Key Features:
- Supports HTTP and HTTPS proxies
- Anonymity level detection
- Speed testing
- Country detection
Pros:
- Simple and easy to use
- No registration required
- Provided by a well-known VPN service
Cons:
- Limited to HTTP and HTTPS proxies
- Basic features compared to some other checkers
5. GitHub – Proxy Checker
Key Features:
- Open-source options available
- Various implementations with different features
- Customizable and extendable
Pros:
- Free and open-source
- Can be modified to suit specific needs
- Often updated by the community
Cons:
- Requires some technical knowledge to set up and use
- May lack user-friendly interfaces
6. Hidester Proxy Checker
Key Features:
- Supports HTTP, HTTPS, and SOCKS proxies
- Anonymity level detection
- Speed testing
- Geolocation verification
- Blacklist checking
Pros:
- Clean, user-friendly interface
- Comprehensive checks
- No registration required
Cons:
- Limited to checking one proxy at a time
7. IPHub Proxy Detection
Key Features:
- Detects various types of proxies (including VPNs and Tor)
- API available for integration
- Detailed information about detected proxies
Pros:
- Specialized in proxy detection
- Offers both free and paid API access
- Regularly updated database
Cons:
- Focused more on detection than checking functionality
8. CheckerProxy.net
Key Features:
- Supports HTTP, HTTPS, SOCKS4, and SOCKS5 proxies
- Batch checking
- Anonymity level detection
- Speed testing
- Country detection
Pros:
- Fast checking speed
- Regular updates of proxy lists
- Simple interface
Cons:
- Ads can be intrusive
- Limited customization options
How to Use Proxy Checkers Effectively
To get the most out of proxy checkers, follow these steps:
- Prepare Your Proxy List: Compile a list of proxies you want to check. You can opt for a free proxies list or a premium proxies list. Most checkers accept lists in IP: Port format.
- Choose the Right Checker: Select a proxy checker that supports the types of proxies you’re using and offers the features you need.
- Set Check Parameters: If the checker allows customization, set parameters like timeout limits, target websites for testing, and specific checks to perform.
- Run the Check: Input your proxy list and start the checking process.
- Analyze Results: Carefully review the results, paying attention to anonymity levels, speeds, and any flags or warnings.
- Filter and Sort: Use the checker’s filtering and sorting options to identify the best proxies for your needs.
- Export and Save: Export the results for future reference or to use with other tools.
- Regularly Recheck: Proxy status can change over time, so regularly recheck your proxies to ensure they’re still performing well.
Interpreting Proxy Checker Results
Understanding the results provided by proxy checkers is crucial. Here’s what to look for:
- Anonymity Level:
- Elite/High Anonymous: Your real IP is not detectable
- Anonymous: Proxy is detectable, but real IP is hidden
- Transparent: Your real IP is visible
- Speed:
- Look for low latency and high download/upload speeds
- Compare speeds to your direct connection to assess the proxy’s impact
- Protocol Support:
- Confirm that the proxy supports the protocols you need (HTTP, HTTPS, SOCKS4, SOCKS5)
- Geolocation:
- Verify that the proxy’s location matches what you expect or need
- Blacklist Status:
- Check if the proxy’s IP is on any blacklists, which could impact its usability
- Uptime/Reliability:
- Some checkers provide historical data on proxy reliability
- SSL/TLS Support:
- For HTTPS proxies, verify proper SSL/TLS handling
Common Issues Detected by Proxy Checkers
Proxy checkers can identify various issues, including:
- DNS Leaks: The proxy may use your local DNS servers, potentially revealing your real location.
- WebRTC Leaks: WebRTC can bypass browser proxy settings, revealing your real IP.
- Slow Speeds: High latency or low bandwidth can make the proxy impractical for many uses.
- Blacklisted IPs: The proxy’s IP may be blocked by certain services due to abuse by other users.
- Incorrect Geolocation: The proxy may not be located where it claims to be.
- Protocol Mismatch: The proxy may not support the protocols it advertises.
- Unreliable Uptime: The proxy may frequently go offline or have intermittent connectivity issues.
- SSL Stripping: Some proxies may downgrade HTTPS connections to HTTP, compromising security.
Proxy Checkers vs. Proxy Managers
While proxy checkers focus on verifying and testing proxies, proxy managers offer broader functionality:
Proxy Checkers:
- Primarily for testing and verifying proxies
- Often, web-based or simple applications
- Focus on providing detailed information about proxy status and performance
Proxy Managers:
- Comprehensive tools for managing and using proxies
- Often, desktop or browser-based applications
- Features may include:
- Proxy rotation
- Automatic failover
- Browser integration
- Traffic routing rules
- Built-in proxy checking functionality
For advanced users or those managing large numbers of proxies, a proxy manager with built-in checking capabilities might be more efficient than using standalone proxy checkers.
Building Your Own Proxy Checker
Building a custom proxy checker can offer maximum flexibility and control for those with programming skills.
Here’s a basic outline of how you might approach this:
- Choose a Programming Language: Python is popular for this task due to its rich libraries for network programming.
- Design the Checker:
- Implement functions to test different proxy types (HTTP, SOCKS, etc.)
- Create methods for checking anonymity, speed, and geolocation
- Develop a system for batch checking and result storage
- Use Appropriate Libraries:
- requests for HTTP requests
- socket for low-level network operations
- geolite2 or similar for IP geolocation
- Implement Checking Logic:
- Test connection establishment
- Verify anonymity by checking headers and comparing IPs
- Measure latency and download speeds
- Check against IP blacklists
- Create a User Interface:
- Command-line interface for scripts
- Web interface for broader accessibility
- Add Advanced Features:
- API support for integration with other tools
- Scheduled checking and alerts
- Custom test targets
Building your own proxy checker allows you to tailor the tool to your needs and potentially integrate it directly into your workflow or applications.
Best Practices for Proxy Usage
While using proxy checkers is important, it’s just one part of responsible proxy usage. Here are some best practices to follow:
- Regularly Check Your Proxies: Proxy status can change quickly, so frequent checking is essential.
- Use Reputable Proxy Providers: Choose well-known, reliable proxy services to minimize the risk of using compromised proxies.
- Implement Proxy Rotation: Regularly rotate your proxies to avoid detection and improve reliability.
- Encrypt Sensitive Data: Use HTTPS when sending sensitive information through proxies.
- Be Aware of Legal and Ethical Considerations: Ensure your proxy usage complies with relevant laws and terms of service.
- Monitor Proxy Performance: Monitor speed and reliability trends over time.
- Use Different Proxies for Different Tasks: Separate proxies for sensitive operations from those used for general browsing.
- Combine with Other Security Measures: Use proxies alongside VPNs, firewalls, and other security tools for comprehensive protection.
Future Trends in Proxy Checking
As proxy technologies evolve, proxy checking tools will, too. Here are some trends to watch:
- AI-Powered Analysis: Machine learning algorithms may predict proxy reliability and detect sophisticated cloaking techniques.
- Integration with Threat Intelligence: Proxy checkers may incorporate real-time threat data to identify potentially malicious proxies.
- Blockchain-Based Verification: Decentralized systems could be used to verify proxy authenticity and performance.
- IoT-Specific Checks: As IoT devices increasingly use proxies, checkers may develop specialized tests for these scenarios.
- Enhanced Privacy Checks: More sophisticated methods for detecting information leaks and ensuring true anonymity.
- 5G and Edge Computing Considerations: Proxy checkers may adapt to test performance in new network paradigms.
- Regulatory Compliance Checks: Tools may evolve to help users ensure their proxy usage complies with data protection regulations.
Conclusion
Listed above are the best online proxy checkers.
Proxy checkers are indispensable tools for anyone relying on proxies for privacy, security, or access to geo-restricted content. Regularly using these tools ensures that your proxies are functioning as expected, maintaining your anonymity, and providing the performance you need.
From simple web-based checkers to advanced, customizable tools, there’s a proxy checker suitable for every level of user and every use case. Whether managing a handful of proxies for personal use or overseeing large proxy pools for business applications, incorporating proxy checking into your routine is crucial for maintaining a robust and reliable proxy infrastructure.
As the digital landscape continues to evolve, with new challenges to privacy and access emerging regularly, proxy checkers will undoubtedly adapt and improve. Staying informed about the latest developments in proxy technologies and checking tools will help you make the most of these powerful networking resources.
Remember, while proxies can be powerful tools for enhancing your online experience and protecting your privacy, they’re just one part of a comprehensive approach to online security. Use them wisely, check them regularly, and always stay informed about best practices in online privacy and security.
By leveraging the best online proxy checkers and following the guidelines outlined in this post, you’ll be well-equipped to maintain a high-performance, secure proxy setup that meets your specific needs. Whether bypassing geo-restrictions, enhancing your online privacy, or managing complex web scraping operations, reliable proxies—verified by robust checking tools—will be key to your success.
INTERESTING POSTS
About the Author:
Meet Angela Daniel, an esteemed cybersecurity expert and the Associate Editor at SecureBlitz. With a profound understanding of the digital security landscape, Angela is dedicated to sharing her wealth of knowledge with readers. Her insightful articles delve into the intricacies of cybersecurity, offering a beacon of understanding in the ever-evolving realm of online safety.
Angela's expertise is grounded in a passion for staying at the forefront of emerging threats and protective measures. Her commitment to empowering individuals and organizations with the tools and insights to safeguard their digital presence is unwavering.