Let’s talk about implementing threat modeling in a DevOps workflow.
In today’s digital-first world, security isn’t just important, it’s non-negotiable. Nowhere is this more evident than in DevOps environments, where development and operations teams work together to accelerate innovation.
While DevOps dramatically speeds up software delivery, it often bypasses critical security checkpoints in the race to release. That’s why integrating threat modeling directly into the DevOps workflow is no longer optional; it’s essential.
According to IBM’s 2024 Cost of a Data Breach report, the global average cost of a data breach has reached $4.88 million, a 10% increase from the previous year and the highest on record. These figures reinforce a pressing truth: embedding security into DevOps pipelines isn’t just about risk mitigation it’s a business imperative. Moreover, adopting DevSecOps practices can accelerate release cycles, reduce costs, and improve product quality by catching vulnerabilities early.
Table of Contents
What Is Threat Modeling in DevOps?
Threat modeling is not just another security checklist, it’s your first line of defense in a DevSecOps strategy. It’s a proactive, structured approach to identifying, analyzing, and mitigating potential threats across systems and applications.
Think of it as adopting the mindset of a malicious actor to identify vulnerabilities before they are exploited. Instead of waiting until the end of development to address security concerns, threat modeling integrates security thinking throughout the software development lifecycle from design to deployment and beyond.
By mapping out system components, valuable assets, data flows, and potential attack vectors, teams embed security into their development DNA, reducing risk without slowing innovation.
The Case for Threat Modeling: Statistics & Insights
- Gartner reports that DevSecOps adoption is accelerating, with organizations reporting fewer security incidents and improved management of risks related to open-source libraries and third-party components.
- CISA (Cybersecurity and Infrastructure Security Agency) emphasizes the importance of “secure by design” and “secure by default” principles. It advocates using customized threat models during product development to address system-specific risks.
- According to SNS Insider Research, the global DevSecOps market is projected to grow from $6.3 billion in 2023 to $45.93 billion by 2032, at a CAGR of 24.7%. This growth is fueled by escalating cyber threats and the need for rapid, secure software delivery.
Real-World Case Studies
Let’s take a look at some of the real world cases where a threat modeling exercise could have saves some significant incidents:
Bybit (2025)
In February 2025, cryptocurrency exchange Bybit experienced a $1.5 billion breach the largest in crypto history. The root cause wasn’t flawed code, but operational security gaps that allowed attackers to manipulate transaction data. Traditional code audits could not detect such flaws, but comprehensive threat modeling could have revealed the systemic weaknesses in operational security.
Capital One (2019)
Capital One suffered a major data breach when a former AWS employee exploited a misconfigured cloud infrastructure, affecting over 100 million customers. A robust threat model could have helped identify these vulnerabilities during design, avoiding the breach altogether.
Equifax (2017)
The Equifax breach exposed sensitive data of nearly 147 million individuals due to an unpatched software vulnerability. This incident underscores the need for proactive threat modeling to catch and remediate known risks before they escalate into crises.
Key Steps in the Threat Modeling Process
- Scoping: Define the full scope of your system. Document all components, data flows, and external dependencies.
- Asset Identification: Identify valuable assets that may be targeted by attackers.
- Threat and Vulnerability Identification: Assess how vulnerabilities could be exploited across the system.
- Mitigation Planning: Develop and implement controls to eliminate or reduce risk.
- Validation: Continuously test and validate that implemented controls are effective.
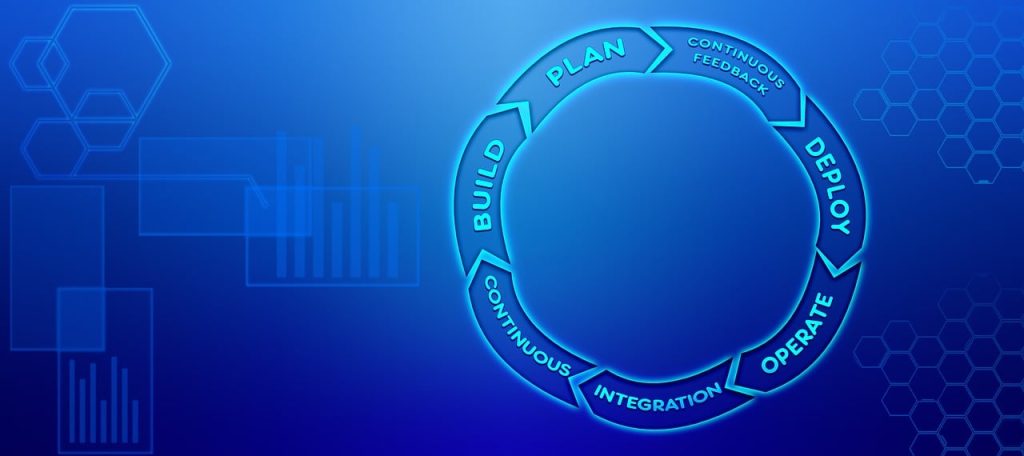
Integrating Threat Modeling Into the DevOps Workflow
1. Shift Left
Start early to integrate threat modeling during design and planning stages. Early detection of vulnerabilities reduces remediation costs and avoids delays in later stages. Embed threat modeling as a recurring step in your CI/CD pipelines.
2. Automation and Tools
Automate security checks using tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing). Automation ensures security isn’t a bottleneck but a seamless part of the development lifecycle.
3. Collaboration and Culture
Security is a team sport. Foster cross-functional collaboration between developers, operations, and security teams. Assign security champions within development squads to promote awareness and drive best practices. Encourage knowledge sharing around threats and mitigation strategies.
4. Continuous Monitoring
Threat modeling isn’t a one-time task it must evolve with your application. Implement continuous monitoring to detect emerging threats. Reassess your threat models regularly to maintain resilience as your infrastructure changes.
Threat Modeling Framework: STRIDE
A popular framework for threat modeling is STRIDE, developed by Microsoft. It breaks down threats into six categories:
- Spoofing – Impersonating users or systems
- Tampering – Unauthorized modification of data or code
- Repudiation – Denying actions or transactions
- Information Disclosure – Unauthorized data exposure
- Denial of Service (DoS) – Disrupting system availability
- Elevation of Privilege – Gaining unauthorized access rights
Using STRIDE within DevOps allows teams to systematically assess threats during each stage of development. It guides teams to ask the right questions early and often: What can go wrong? What are we missing? How can we stop it?
Conclusion
Threat modeling acts as a security compass in your DevOps journey helping you navigate evolving risks and adjust course as your software grows. Integrating it into your workflow isn’t just smart, it’s a strategic imperative.
By embracing automation, fostering a security-first culture, and aligning cross-functional teams, organizations can move fast without compromising on security. But remember: threat modeling is one layer of a comprehensive security strategy. It must align with broader initiatives like risk management, secure coding, and incident response to be truly effective.
In a world of increasingly sophisticated cyber threats, baking security into every development stage isn’t a luxury, it’s your best defense.
INTERESTING POSTS
About the Author:
Meet Angela Daniel, an esteemed cybersecurity expert and the Associate Editor at SecureBlitz. With a profound understanding of the digital security landscape, Angela is dedicated to sharing her wealth of knowledge with readers. Her insightful articles delve into the intricacies of cybersecurity, offering a beacon of understanding in the ever-evolving realm of online safety.
Angela's expertise is grounded in a passion for staying at the forefront of emerging threats and protective measures. Her commitment to empowering individuals and organizations with the tools and insights to safeguard their digital presence is unwavering.