This post will answer the question – what is a certificate authority? Read on.
Safety and Security are the two factors that are vital in the digital world. When any user surfs the Internet, the two questions which arise in their mind are:
Is the site secured? Can they make online transactions safely on the site?
And to get answers to the above questions, they check the Security of the site. Online users who browse the Internet frequently know that HTTPS and padlocks are trust indicators and prove that the site is secure.
These icons are visible on the screen, but:
- Are you aware of how these icons work behind the screen?
- How does a server communicate with the browser?
- How does the server state: “I am secured with an SSL certificate, so trust me?”
- How does the browser know which SSL certificate can be trusted?
- Who issues these SSL certificates?
Before knowing the backend process, let us see what makes trust indicators visible. When installed on the website, SSL certificates show these visual trust icons. SSL (Secure Socket Layers) certificates are digital certificates that encrypt all browser-server communications, making them secure from intruders. These digital certificates are issued by Certificate Authorities (CA). Hence, these Certificate Authorities are responsible for securing the Internet to a large extent.
In this article, we will discuss what a certificate authority is. How does it work? What does it do to secure the Internet?
Table of Contents
What Is Certificate Authority?
Certificate Authority is a trusted entity that verifies websites and, post-verification, issues digital certificates called SSL certificates. Their motto is to ensure the Security of the digital world.
CAs are trusted by third parties, as well as certificate owners. They validate the domain or company that has applied for an SSL certificate and issue SSL certificates that web browsers trust.
An example may clear your doubts.
Example: Let us say this is the SSL2BUY website. Though the domain name is SSL2BUY, are you sure it runs on the same company's server? What if some hacker has mimicked the same server?
So, there is no way to cross-check whether the website is legitimate. Here, Certificate Authorities come into the picture.
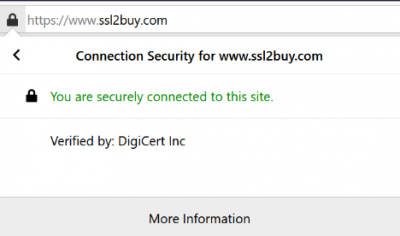
When a CA issues an SSL certificate for a website, the CA details are visible in the SSL certificate. When you click on the padlock, the website shows that the connection is secured by CA (DigiCert Inc.); hence, customers are assured about the website's authenticity.
READ ALSO: 5 Ways To Make Your Company Website More Secure
How Do CA's Work?
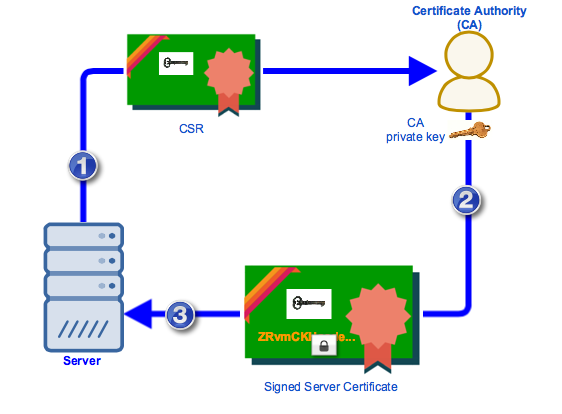
SSL certificates are based on Public Key Infrastructure (PKI), and hence, you need to generate a key pair (private key and public key) and create CSR (Certificate Signing Request). A copy of the public key is handed with the CSR to the CA with all the information.
The CA will then sign the certificate and import it to your server. This signed digital certificate has all the information regarding the site, the validity of the certificate, the issuer name, the public key of your site, and the signature on the certificate with CA's private key.
What Does The Certificate Authority Do?
Certificate Authorities do verifications and authentications before issuing digital security certificates.
Tasks
- CA verifies the identity of the user who has requested an SSL certificate for their website. The process includes vetting domain names, organizations, or individuals by validating their identities with official registrations and records.
- After the validation process, digital certificates are issued to build trust. These certificates authenticate servers, companies, and individuals, thus displaying site security. They are also used for encryption code signing, etc.
- These CAs also keep track of CRL (Certificate Revocation Lists), which hints at invalid or expired certificates, and revoked certificates (invalid before the expiry date).
Validations & Functions of CA
The CA does the validation depending on the SSL certificate requested by the user.
- Domain Validation (DV) SSL:
CA verifies the domain name and matches the same with the name registered in the WHOIS register. It also checks whether the certificate's applicant is the owner of the domain name or not.
- Organisation Validation (OV) SSL:
One step further from DV, the CA verifies whether the organization is legitimate. It also confirms the organization's presence by validating the location, domain name, and name of the organization registered.
- Extended Validation (EV) SSL:
The highest level of validation and preferred by large organizations and corporations is EV SSL. Thorough research about the company and legal verification makes this certificate highly popular. Conversion rates are bound to be high with EV SSL sites.
CA's include multiple certificates for multiple securities.
- Single Domain SSL: Secures the primary domain of the site
- Multi-Domain SSL: Secures multiple domains and multiple sub-domains of all levels
- Wildcard SSL: Secures the primary domain and various sub-domains of the first-level
Analyze your business requirements and buy an SSL certificate accordingly.
Role Of CA In Nurturing Trust
A hierarchical trust model, which all the CA's use for the chain of trust, comprises of:
- Root Certificates:
These certificates are shared by all popular browsers and operating systems and are owned by CAs. The root store of browsers and OS comprises these certificates. CAs control them and belong to the issuing Certificate Authority. They are issued and signed by CA using their private key.
- Intermediate Certificates:
They are the man-in-middle between secured root certificates and website certificates issued to the users. These certificates are issued from root certificates.
- Server Certificates:
This is the primary certificate that a CA issues to secure your domain. When installed on your web server, this certificate also secures your domains and sub-domains (depending on the certificate type).
- Importance of CA:
Let us imagine:
- What will happen if there is no CA's?
- Without any trusted entities and digital certificates, how will you survive cyber-attacks?
- Without CAs securing the web world, how will a user know whether they are connected to a legitimate site server or a malicious server?
All these questions are enough to cause goosebumps. CA's duties are not only restricted to issuing certificates, but they are also the key authorities to sign public keys and authenticate and validate domains, individuals, and organizations.
CA issues SSL certificates after verifying the site's legitimacy; hen,ce, these sites having SSL certificates are termed trustworthy. Even Google has appreciated sites with SSL certificates and ensures that popular browsers flash a warning message stating “Non-Secure” on sites that do not have this digital certificate.
SSL encryption security comes with robust 256-bit encryption, which is a tough nut for hackers to crack. Without these security protocols, the chances of data tampering and malware attacks rise. Hence, CA'CAslp in with authenticity, confidentiality, and data integrity.
Types Of CA's
Region and Globe distribute CA's. There are many global CA's, but only a few make it to the game's top.
There are publicly trusted CAs, called public CAs and private CAs. Let us have a brief about both.
- Public CA:
Public CAs are also called commercial CAs. These third-party entities issue certificates to individuals and organizations who request the same. ThesCAs comply with Baseline Requirements, and most browsers approve their certificates.
Example:
Comodo, DigiCert, GlobalSign, let's Encrypt, etc., are a few big names.
- Private CA:
Private CA or Private PKI (Public Key Infrastructure) works for a single enterprise or company but functions like a public CA. It is also termed Internal CA. It issues the certificates only for the company it works for and has specific features.
- Since these CA's are issued internally, they are trusted by internal clients, users, and IT staff.
- Access is restricted to a limited group of users.
- The setup and hosting of this CA are to be done by the company itself or by hired third-party personnel.
- They best serve internet networks and intranets.
Private CA's are used for:
- Intranet Sites
- VPN (Virtual Private Network)
- Private Email Signing Certificates
- CUG's (Closed User Groups)
Certificate Authority (CA): Your Questions Answered
In the digital world, trust is paramount. Certificate Authorities (CAs) play a vital role in establishing trust online by issuing digital certificates that verify the identities of websites and other entities.
Here's a breakdown of CAs and how they function:
What does a Certificate Authority (CA) do?
CAs act as trusted third parties in the digital world. They perform several key functions:
- Validation: CAs validate the identity of entities requesting digital certificates. This validation process can involve verifying domain ownership, organizational information, or individual identity, depending on the type of certificate.
- Issuing Certificates: Upon successful validation, CAs issue digital certificates containing the validated information and a digital signature from the CA. This signature is a seal of approval, vouching for the entity's legitimacy.
- Maintaining Trust: CAs maintain a repository of issued certificates known as a Certificate Transparency Log (CTL). This log helps ensure accountability and transparency in the certificate issuance process. Additionally, CAs can revoke certificates if they become compromised or outdated.
What is an example of a Certificate Authority (CA)?
There are numerous commercial and non-profit CAs operating worldwide. Some well-known examples include:
- DigiCert
- Entrust
- Let's Encrypt (non-profit)
- Comodo
- GlobalSign
How do I get a CA certificate?
The process for obtaining a CA certificate varies depending on the CA and the type of certificate you need. Here's a general outline:
- Choose a CA: Select a reputable CA that meets your needs and budget. Consider factors like the level of validation required, certificate types offered, and customer support.
- Apply for a Certificate: Initiate the application process on the CA's website. This typically involves providing relevant information and documentation for validation.
- Validation Process: The CA will validate your identity based on the chosen certificate type. This might involve domain ownership verification, business registration checks, or individual identity verification.
- Issuing the Certificate: The CA will issue your digital certificate upon successful validation. You can then install this certificate on your server or device.
What is the difference between a certificate and a CA certificate?
All CA certificates are digital certificates, but not all digital certificates are CA certificates. Here's the key distinction:
- Digital Certificate: A broader term encompassing any electronic document that binds a public key to an entity (website, organization, or individual). It can be self-signed (created by yourself) or issued by a CA.
- CA Certificate: A specific digital certificate issued by a trusted Certificate Authority. It carries the weight of the CA's validation and is a more reliable indicator of trust and authenticity.
What is the difference between TLS and CA?
TLS (Transport Layer Security) is a cryptographic protocol secures communication between websites and web browsers. It relies on digital certificates issued by CAs to establish trust and encrypt data transmission. Here's the analogy:
- TLS: The secure communication channel (like a locked padlock)
- CA Certificate: The key that unlocks the channel (issued by a trusted authority)
READ ALSO: How To Invest In Cryptocurrency
Do I need a Certificate Authority for my domain?
For most websites, having a CA certificate is essential. It provides several benefits:
- Enhanced Security: Encrypts data transmission between your website and visitors, protecting sensitive information like login credentials or credit card details.
- Increased Trust: The presence of a CA certificate assures users that your website is legitimate and takes security seriously. This can lead to higher conversion rates and improved brand reputation.
- Improved SEO Ranking: Search engines like Google prioritize websites with valid SSL/TLS certificates (which rely on CA certificates) in their search results.
While there are self-signed certificates, they come with a significant trust warning in most browsers. This can deter visitors and hurt your website's credibility. Using a CA certificate provides visitors a more trusted and secure online experience.
Wrapping Up
The Internet is like 2 sides of a coin. One side indicates that vast global information is accessible within seconds, whereas the other shows the insecurities of accessing the same.
Data breaches, Cyber-attacks, Phishing attacks, Identity thefts, and many more dangers come with internet benefits.
CAs are trusted entities that create a barrier between these dangers, thus creating a secure environment for their users. Hence, website owners should install SSL/TLS certificates from trusted CAs and secure their digital data.
SUGGESTED READINGS
- How To Secure And Protect A Website [We Asked 38 Experts]
- Why SSL Certificate Is An Essential Cybersecurity Tool?
- The Must-Dos And Don'ts For Protecting Your Password And Personal Data
- Session Hijacking: Everything You Need To Know
- What Is An SSL Certificate?[MUST READ]
- How To Measure SEO Success: KPIs You Need To Track
- Why Is A CompTIA Certificate Important?
About the Author:
Marie Beaujolie is a computer network engineer and content writer from Paris. She is passionate about technology and exploring new ways to make people’s lives easier. Marie has been working in the IT industry for many years and has a wealth of knowledge about computer security and best practices. She is a regular contributor for SecureBlitz.com, where she writes about the latest trends and news in the cyber security industry. Marie is committed to helping people stay safe online and encouraging them to take the necessary steps to protect their data.
Meet Angela Daniel, an esteemed cybersecurity expert and the Associate Editor at SecureBlitz. With a profound understanding of the digital security landscape, Angela is dedicated to sharing her wealth of knowledge with readers. Her insightful articles delve into the intricacies of cybersecurity, offering a beacon of understanding in the ever-evolving realm of online safety.
Angela's expertise is grounded in a passion for staying at the forefront of emerging threats and protective measures. Her commitment to empowering individuals and organizations with the tools and insights to safeguard their digital presence is unwavering.