In this post, we want to take a look at the PassHulk password manager. Read on for the PassHulk review.
In the digital age, password management is more crucial than ever. With an increasing number of accounts, applications, and devices requiring secure logins, managing passwords has become a daunting task.
Enter PassHulk, a password management solution designed to simplify and secure your digital life. This review aims to provide an in-depth analysis of PassHulk, its features, pricing, pros and cons, and alternatives to help you make an informed decision.
Passwords are annoying due to the stress of creating and remembering passwords for various accounts, ranging from email to Netflix, yet they are needed to secure our digital life, hence the need for a robust password manager.
There are several password managers, but the review will focus on PassHulk, its features, ease of use, compatibility, pricing, and other info you need to know about PassHulk.
Table of Contents
TLDR; Bottom Line
PassHulk is a robust password manager that offers a user-friendly interface, strong security features, and competitive pricing. It's ideal for individuals and businesses looking to enhance their password security without breaking the bank. With its comprehensive feature set, PassHulk stands out in the crowded password management market.
What Is PassHulk?
PassHulk is a password manager that can generate, store, and manage passwords and other digital credentials, thereby allowing you to access them with a single master password.
It eliminates the need to remember multiple passwords, reducing the risk of password fatigue and enhancing your overall security posture. PassHulk offers cross-platform compatibility, ensuring you can access your passwords from any device, whether it's a smartphone, tablet, or desktop computer.
In addition, PassHulk encrypts and safeguards your passwords and other sensitive credentials like credit card details, bank account details, SSN, Licenses, and other Personally Identifiable Information (PII), using the AES encryption protocol (the strongest encryption protocol in use today).
PassHulk users enjoy a user-friendly personalized interface for managing passwords and other stored data. You can choose your password storage location from your dashboard, create and organize your data into separate folders, and do much more.
When signing up, PassHulk suggests robust Passwords and also prompts you to save new passwords, thus saving you the stress of writing down passwords or manually saving your passwords in a notepad.
Quote From Personal Experience
Using PassHulk has significantly simplified my online experience. No more struggling to remember multiple passwords or resetting them frequently. The security features give me peace of mind, knowing that my information is safe.” – A satisfied PassHulk user.
How To Get Started With PassHulk
Getting started with PassHulk is straightforward. Follow these steps to set up your account:
- Visit the PassHulk Website: Go to the official PassHulk website.
- Sign Up: Click on the sign-up button and enter your details.
- Choose a Plan: Select the plan that suits your needs (more on pricing below).
- Download the App: Download the PassHulk app on your devices.
- Set Up Your Master Password: Create a strong master password that will be used to access your account.
- Import Your Passwords: Import your existing passwords or add them manually.
- Start Using PassHulk: Begin managing your passwords securely.
PassHulk Key Features
Security features: AES-256-bit encryption and Secure Remote Password Protocols
PassHulk uses the AES 256-bit military-grade encryption protocol to encrypt and safeguard all users' passwords and online credentials. As a first-time user, PassHulk generates a one-time secret key to access your PassHulk vault the first time you log in. This key will not be required for subsequent logins.
PassHulk uses the Secure Remote Password (SRP) protocol to store passwords, secret keys, and other online credentials and keep them safe from hacking and interception. Hence, there's no way that hackers can intercept passwords sent to PassHulk’s servers.
Multiple Vaults
With PassHulk, you can create multiple folders to manage your online credentials. You can create folders for personal, work, family, banking, and social media credentials for easy organization, storage, and management.
Data Breach Scanner
PassHulk’s data breach scanner notifies you of passwords susceptible to attacks. Such passwords can be weak or used passwords. This feature also monitors the internet and notifies you of any password breaches.
Aside from monitoring passwords, PassHulk’s data breach monitoring also monitors your credit card details and notifies you when your credit card is nearing expiration. I love this feature because it keeps me updated about the state of my credit cards without posing any security risk to my credit cards.
Manage Passwords from multiple devices
Aside from your native device, you can log in to your PassHulk account from other devices, platforms, and OS. Whether you're on the go, you can manage, edit, or store passwords across multiple platforms irrespective of where you're.
One-click Logins
With PassHulk, you can log in to multiple accounts with a single click; hence, you do not have to go through the pains of remembering password credentials for various websites or platforms.
PassHulk Apps
As at the time of writing this PassHulk review, I observed that PassHulk has an app for Android device users only.
However, other users can enjoy PassHulk’s web-based version; although this is disappointing, I would like to see PassHulk support other device types and platforms, including Windows, Mac, iOS, and Linux.
Nevertheless, PassHulk integrates with most websites, apps, and platforms, including Google, MailChimp, Amazon, Spotify, PayPal, Facebook, and Airbnb, to save and manage passwords and fill up forms.
PassHulk Customer Service and Resources
Overall, for this PassHulk Password Manager review, I will say that I am impressed with PassHulk’s customer service. I got an instant response when I contacted PassHulk’s customer support via their LiveChat feature; also, the customer support staff was friendly and professional, taking his time to answer my questions and inquiries.
Although support via PassHulk’s email channel is not instant like the LiveChat feature, I got a satisfactory reply within 4 hours, which is an impressive response time via email considering the number of email-based inquiries pouring in.
PassHulk Review: Features And Testing Results
PassHulk boasts a comprehensive suite of features designed to enhance your password management experience.
Here’s a detailed look at some of its standout features and our testing results:
| Feature | Description | Testing Results |
| Password Generator | Generates strong, unique passwords for all your accounts. | Easy to use, highly customizable. |
| Auto-Fill | Automatically fills in login details for websites and apps. | Smooth performance, accurate auto-fills. |
| Secure Sharing | Share passwords securely with trusted contacts. | Secure and efficient sharing options. |
| Cross-Platform Sync | Syncs passwords across multiple devices seamlessly. | Fast sync, no noticeable delays. |
| Security Dashboard | Monitors your accounts for security breaches and weak passwords. | Comprehensive, easy to understand. |
| Two-Factor Authentication (2FA) | Adds an extra layer of security by requiring a second form of authentication. | Reliable and enhances security. |
| Dark Web Monitoring | Scans the dark web for compromised credentials. | Timely alerts, useful for proactive security. |
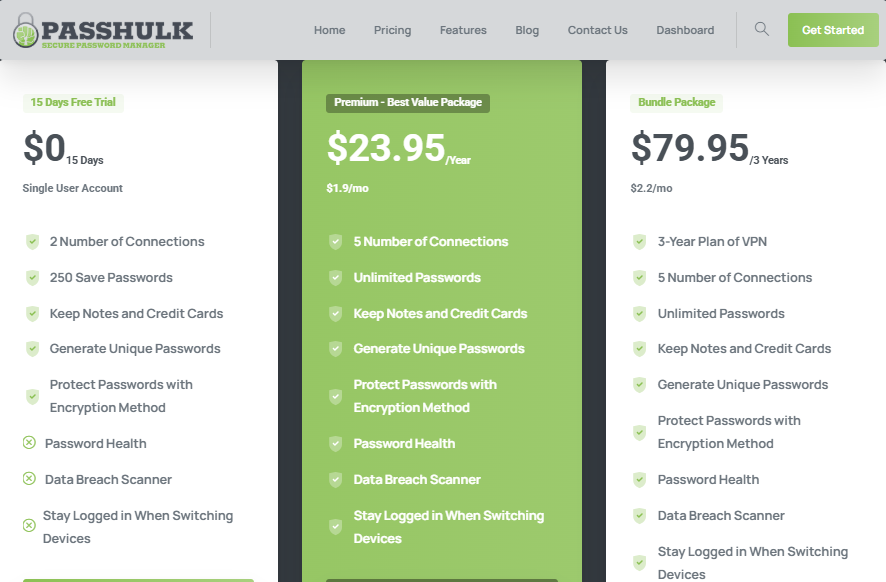
PassHulk Pricing: How Much Does It Cost?
PassHulk offers several pricing tiers to accommodate different needs:
- Free Trial: Users can try out PassHulk for free for 15 days. This free plan offers users 2 Numbers of connections, 250 password storage, password encryption, data breach monitor, and much more.
- Yearly Plan: for $23.95 per year, users can enjoy access to 5 connections, unlimited password storage, notes, credit card storage, password health, and other features.
- 3-year Plan: for $79.95 for three years, users enjoy all the benefits available to other PassHulk plans in addition to a free, 3-year FastestVPN plan
For all plans, users enjoy a 15-day trial and a 30-day money-back guarantee. This is a fair deal considering that you have 15 days to try out PassHulk, and also get your money back within 30 days if you feel PassHulk is not for you.
Is PassHulk Safe?
PassHulk is absolutely safe; it uses a range of robust security features like military-grade encryption and Secure Remote Password Protocols to secure, protect, and manage your passwords and online credentials.
✅ Frequently Asked Questions (FAQs) about PassHulk Password Manager
What is PassHulk Password Manager?
PassHulk is a secure and user-friendly password manager that helps you store, manage, and autofill your passwords across multiple platforms. It’s designed for individuals and teams who want a simple yet powerful way to protect their digital identities. With PassHulk, you no longer have to remember complex passwords or reuse weak ones.
Is PassHulk Password Manager free?
Yes, PassHulk offers a free version with core features like password storage, autofill, and secure notes. The premium plans provide additional benefits such as cloud backup, device sync, and enhanced security tools. It's a great option for budget-conscious users looking for strong password protection.
How secure is PassHulk?
PassHulk uses AES-256 bit encryption, which is the industry standard for military-grade protection. It also supports zero-knowledge architecture, meaning your data is encrypted on your device before it reaches PassHulk’s servers. Even the company cannot view or access your stored credentials.
Can I use PassHulk on multiple devices?
Yes, PassHulk supports cross-platform compatibility including Windows, macOS, Android, iOS, and major browsers like Chrome and Firefox. With a premium plan, you can sync your passwords and notes seamlessly across all your devices using encrypted cloud storage.
Does PassHulk offer a password generator?
Absolutely. PassHulk includes a built-in strong password generator that lets you create long, random, and secure passwords with just one click. You can customize the length and complexity to suit different websites’ requirements—making it easier to maintain security best practices.
What happens if I forget my master password?
PassHulk emphasizes privacy and doesn’t store or reset your master password due to its zero-knowledge policy. However, during setup, users are provided with a recovery key or backup options to regain access. It’s highly recommended to store this key securely in an offline location.
Can PassHulk autofill passwords on websites and apps?
Yes, PassHulk’s browser extension and mobile apps can autofill login forms, credit card information, and other saved data. This feature not only saves time but also helps prevent phishing attacks by ensuring you’re logging into legitimate sites.
Is PassHulk better than LastPass or 1Password?
PassHulk is a strong competitor in the password management space, especially for users looking for a more cost-effective and straightforward alternative. While LastPass and 1Password have advanced features, PassHulk offers an excellent balance of simplicity, security, and performance for everyday users.
Does PassHulk store other types of data besides passwords?
Yes, in addition to passwords, you can securely store credit card details, secure notes, Wi-Fi credentials, and identity documents. All entries are encrypted and organized in a clean, easy-to-use interface, giving you one safe place for all your sensitive information.
Is PassHulk suitable for teams or business use?
Yes, PassHulk offers business plans that include features like role-based access control, secure team sharing, activity logs, and admin dashboards. It’s ideal for small teams or businesses that want to enforce strong password policies and minimize cyber risks.
A Final Thought On The PassHulk Review
It will be ideal to conclude this review by mentioning some of the PassHulk password manager features that make it an outstanding password manager; such features include:
- Unlimited password storage
- Military-grade encryption and Secure Remote Password protocols
- One-click login
- Notes and credit card storage
- Auto-filling
- Multiple vaults
- Save password Auto-prompts
- Online shopping support
- 24/7 live support
In concluding this PassHulk review, I will give PassHulk a 5-star rating and recommend it as a secure password manager for storing and managing passwords, banking credentials, credit card details, notes, and other online credentials.
INTERESTING POSTS
- Large scale attack campaign targets WordPress sites’ database credentials
- The new Firefox password manager now alert users with leaked passwords
- How To Choose The Best Password Manager | 2022
- Unbiased CyberGhost Password Manager Review
- 7 Business Credit Card Tips For Small Businesses
- Full 1Password Review – Reliable Password Manager